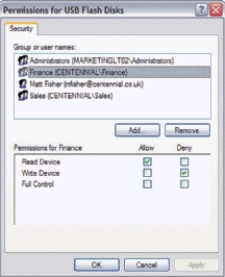
-____ software,such as that shown in the accompanying figure,can control which devices can be connected to an employee's computer.
A) Data-leakage prevention
B) Device authentication
C) Professional firewall
D) Network quarantine
Correct Answer:
Verified
Q42: _ identify users by a particular unique
Q49: The term _ refers to accessing someone
Q50: A booming area of computer crime involves
Q57: A _ provides a secure private tunnel
Q58: _ are acts of malicious destruction to
Q64: _ includes any illegal act involving a
Q65: Phishing schemes may use a technique called
Q72: A(n) _ access system is an identification
Q79: _ can be extremely distressing for victims,
Q80: ![]()
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents