Related Questions
Q23: You can purchase stolen credit cards on
Q25: If you receive an email from your
Q29: What security and controls should a company
Q29: In the Target breach, the HVAC systems
Q30: The deep web is a part of
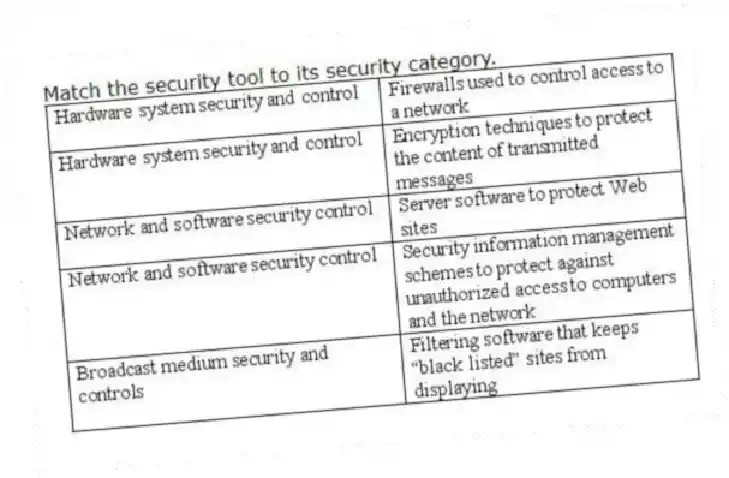
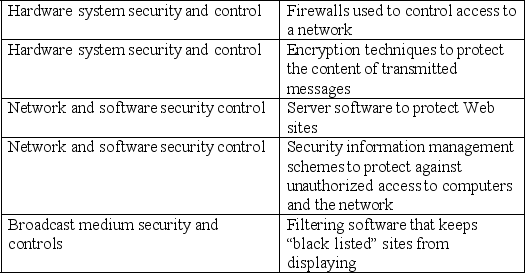
Q31: Of the seven security policies noted in
Q33: A hacker who buys credit card information
Q36: Firewalls can be either in hardware or
Q38: Two factor authentication is when you use
Q49: What are the shortcomings of passwords?
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents