Related Questions
Q50: _ are proofs of identity.
A) Certifications
B) Credentials
C)
Q51: When a hashing algorithm is applied, the
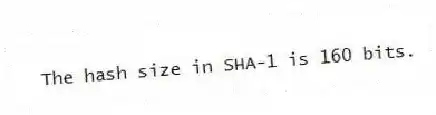
Q52: The hash size in MD-5 is 160
Q53: The most popular public key encryption cipher
Q54: When Emma sends a message to Lucy,
Q56: MS-CHAP is used for _ authentication.
A) initial
B)
Q57: Hashing is a reversible process.
Q58: Hashing is _.
A) reversible
B) repeatable
C) Both A
Q59: To be strong, _ keys need to
Q60: In mutual authentication between two parties, _.
A)
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents