A systems administrator is reviewing the following information from a compromised server: 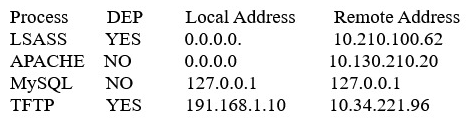 Given the above information, which of the following processes was MOST likely exploited via a remote buffer overflow attack?
Given the above information, which of the following processes was MOST likely exploited via a remote buffer overflow attack?
A) Apache
B) LSASS
C) MySQL
D) TFTP
Correct Answer:
Verified
Q65: Which of the following are methods to
Q66: A security analyst is hardening a web
Q67: A new firewall has been places into
Q68: Joe, a security administrator, needs to extend
Q69: A dumpster diver recovers several hard drives
Q71: Which of the following cryptography algorithms will
Q72: An application developer is designing an application
Q73: After an identified security breach, an analyst
Q74: A security analyst is testing both Windows
Q75: An organization's file server has been virtualized
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents