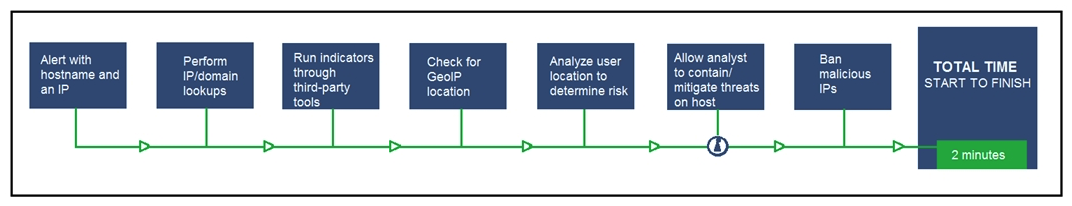
 Refer to the exhibit. An engineer configured this SOAR solution workflow to identify account theft threats and privilege escalation, evaluate risk, and respond by resolving the threat. This solution is handling more threats than Security analysts have time to analyze. Without this analysis, the team cannot be proactive and anticipate attacks. Which action will accomplish this goal?
Refer to the exhibit. An engineer configured this SOAR solution workflow to identify account theft threats and privilege escalation, evaluate risk, and respond by resolving the threat. This solution is handling more threats than Security analysts have time to analyze. Without this analysis, the team cannot be proactive and anticipate attacks. Which action will accomplish this goal?
A) Exclude the step "BAN malicious IP" to allow analysts to conduct and track the remediation
B) Include a step "Take a Snapshot" to capture the endpoint state to contain the threat for analysis
C) Exclude the step "Check for GeoIP location" to allow analysts to analyze the location and the associated risk based on asset criticality
D) Include a step "Reporting" to alert the security department of threats identified by the SOAR reporting engine
Correct Answer:
Verified
Q96: Q97: How does Wireshark decrypt TLS network traffic? Q98: A patient views information that is not Q99: Refer to the exhibit. Which command was![]()
A)

