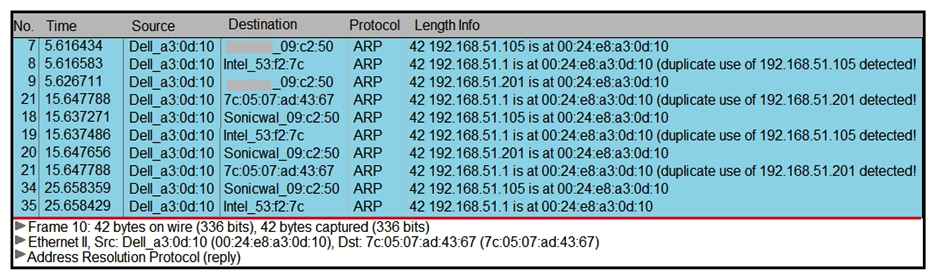
 Refer to the exhibit. A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
Refer to the exhibit. A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
A) DNS spoofing; encrypt communication protocols
B) SYN flooding, block malicious packets
C) ARP spoofing; configure port security
D) MAC flooding; assign static entries
Correct Answer:
Verified
Q6: Q7: A security team received an alert of Q8: Which scripts will search a log file Q9: A security team is discussing lessons learned Q10: Q12: Q13: Which tool conducts memory analysis? Q14: Which technique is used to evade detection Q15: A security team receives reports of multiple Q16: Unlock this Answer For Free Now! View this answer and more for free by performing one of the following actions Scan the QR code to install the App and get 2 free unlocks Unlock quizzes for free by uploading documents![]()
![]()
![]()
A) MemDump
B) Sysinternals![]()

