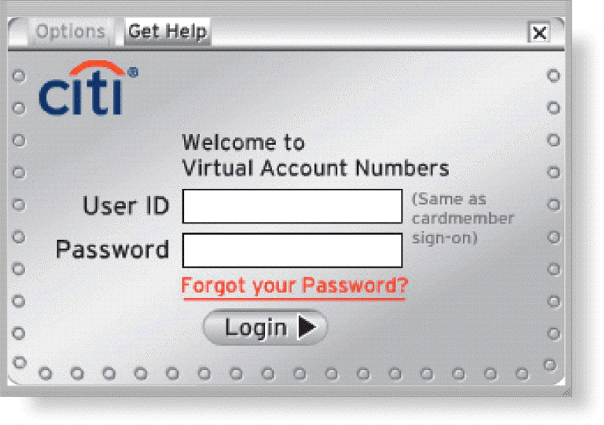
As shown in the accompanying figure, most operating systems require that users correctly enter a user name and password before they can access the data, information, and programs stored on a computer, mobile device, or network.
Correct Answer:
Verified
Q88: COGNITIVE ASSESSMENT What term is used to
Q89: COGNITIVE ASSESSMENT Which of the following terms
Q92: COGNITIVE ASSESSMENT What is an EULA intended
Q102: Personal firewalls constantly monitor all transmissions to
Q104: Perpetrators of back doors trick their victims
Q105: PINs are not the same as passwords.
Q106: Both Windows and Mac operating systems include
Q111: A rootkit can be a back door.
Q114: Audit trails only record unsuccessful access attempts.
Q120: Biometric objects are entirely foolproof.
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents