FIGURE 30-2 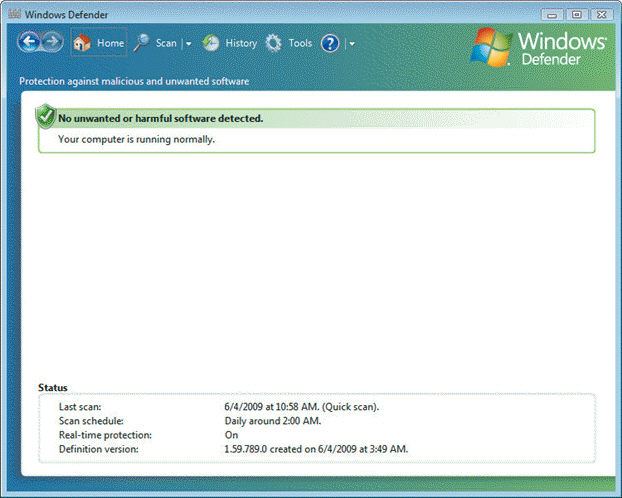 You could use the program shown in Figure 30-2 above to ____.
You could use the program shown in Figure 30-2 above to ____.
A) protect your system against spyware
B) back up files
C) configure a hardware firewall
D) password protect your wireless network
Correct Answer:
Verified
Q34: To make sure your e-commerce transactions are
Q35: Which of the following is not true
Q36: Often, you can inadvertently run a virus
Q37: What is another term for brute force
Q38: When you use a computer in a
Q40: What should you do before donating a
Q41: A(n) _ is a malicious program that
Q42: Identify the letter of the choice that
Q43: Why are passwords important? How do you
Q44: _ are small files that are created
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents