The accompanying figure shows the working of a _____.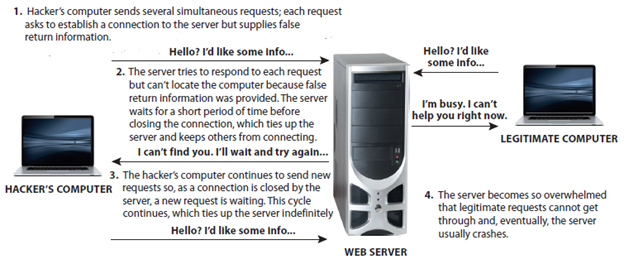
A) brute force attack
B) denial of service attack
C) quick attack
D) phishing attack
Correct Answer:
Verified
Q23: _ steal credit card or debit card
Q24: A user has to provide a
Q25: A sender's private key is used to
Q26: Two of the most common ways individuals
Q27: Leslie, a computer hacker, creates a game
Q29: Abby writes a program that redirects users
Q30: _ typically begins with online harassment, such
Q31: A _ is a software program that
Q32: Sara , the chief finance officer of
Q33: _ is the use of an email
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents