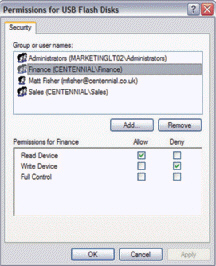
 ____ software, such as that shown in the accompanying figure, can control which devices can be connected to an employee's computer.
____ software, such as that shown in the accompanying figure, can control which devices can be connected to an employee's computer.
A) Data-leakage prevention
B) Device authentication
C) Professional firewall
D) Network quarantine
Correct Answer:
Verified
Q26: In spoofing, terrorists launch attacks via the
Q45: _, the most commonly used type of
Q49: The term _ refers to accessing someone
Q50: A booming area of computer crime involves
Q53: _ access systems use physical objects for
Q55: Increasingly, USB security keys, also called USB
Q57: A _ provides a secure private tunnel
Q58: _ are acts of malicious destruction to
Q59: A _ is a malicious program that
Q60: A computer _ is a software program
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents