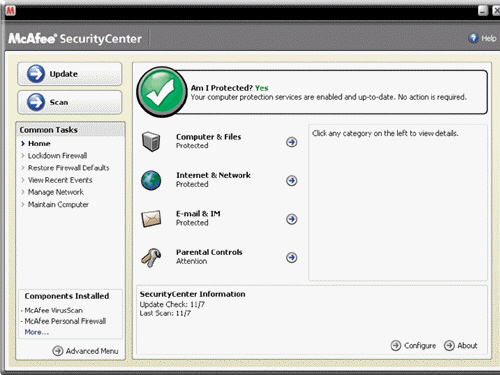
 A program, like the one in the accompanying figure, scans for programs that attempt to modify the boot program, the operating system, and other programs that normally are read from but not modified.
A program, like the one in the accompanying figure, scans for programs that attempt to modify the boot program, the operating system, and other programs that normally are read from but not modified.
Correct Answer:
Verified
Q88: Identification verifies that an individual is the
Q93: A cyberextortionist uses the Internet or network
Q95: Many companies use access controls to minimize
Q96: COGNITIVE ASSESSMENT Which of the following terms
Q97: COGNITIVE ASSESSMENT What is a power surge?
A)
Q98: COGNITIVE ASSESSMENT Which of the following statements
Q99: COGNITIVE ASSESSMENT Which of the following statements
Q100: COGNITIVE ASSESSMENT Which of the following terms
Q102: To utilize intrusion detection software requires little
Q115: The best preventive measures against hardware theft
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents