Deck 10: Fraud and Internal Control
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/100
Play
Full screen (f)
Deck 10: Fraud and Internal Control
1
What three things must a perpetrator have to commit fraud? Include a brief description of each.
The perpetrator must have motive - reason for committing the fraud, such as financial difficulties.
The perpetrator must have opportunity - access to the asset or financial statements in order to carry out the fraud.
The perpetrator must have the means to carry out the fraud - knowledge or skills that permit the perpetrator to commit the crime.
The perpetrator must have opportunity - access to the asset or financial statements in order to carry out the fraud.
The perpetrator must have the means to carry out the fraud - knowledge or skills that permit the perpetrator to commit the crime.
2
List the three fraud and abuse categories. Provide examples.
1. Corruption, such as bribery
2. Misappropriation of assets, including theft of cash, fraudulent disbursements, or stealing merchandise
3. Fraudulent financial reporting, such as misstating financial statements in order to meet earnings targets (acfe.com, 2009)
2. Misappropriation of assets, including theft of cash, fraudulent disbursements, or stealing merchandise
3. Fraudulent financial reporting, such as misstating financial statements in order to meet earnings targets (acfe.com, 2009)
3
Earnings management focuses on managing when revenues and expenses are recorded in order to favorably reflect a company's financial performance in a(n)________.
A)Illegal manner
B)Legal manner
C)Questionable manner
D)Vague manner
A)Illegal manner
B)Legal manner
C)Questionable manner
D)Vague manner
B
4
What percentage of occupational fraud is committed by upper management?
A)19%
B)15%
C)25%
D)30%
A)19%
B)15%
C)25%
D)30%

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
5
What percentage of occupational fraud is committed by the accounting department?
A)16%
B)29%
C)35%
D)38%
A)16%
B)29%
C)35%
D)38%

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
6
Tips are the most likely means of detecting fraud.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
7
What are the elements required to prove fraud?

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
8
The typical fraud lasts three years before it is detected.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
9
The Sarbanes-Oxley Act of 2002, which would become known as SOX, created the ________ to oversee and regulate public companies and their auditors.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
10
List and describe the principles for establishing an environment to effectively manage fraud risk.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
11
The SOX legislation basically requires management of privately held companies must assess and report on the effectiveness of internal controls for financial reporting using a recognized framework.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
12
Accounting professionals often refer to the fraud triangle as incentive/opportunity/rationalization.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
13
Most occupational frauds are committed by the accounting department or upper management.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
14
If the internal audit revealed any significant deficiencies, it is not required to be disclosed by the signing officers of the company.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
15
Substantive procedures collect evidence regarding the accuracy, completeness, and validity of data produced by the accounting system.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
16
What percentage for frauds are detected by tips?
A)33%
B)36%
C)46%
D)56%
A)33%
B)36%
C)46%
D)56%

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
17
How long does the typical fraud last before being detected?
A)Six months
B)One year
C)Two years
D)Three years
A)Six months
B)One year
C)Two years
D)Three years

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
18
________ techniques to avoid potential key fraud risk events should be established, where feasible, to mitigate possible impacts on the organization.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
19
________ focuses on managing when revenues and expenses are recorded in order to favorably reflect a company's financial performance in a legal manner.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
20
________ techniques should be established to uncover fraud events when preventive measures fail or unmitigated risks are realized.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
21
In a(n)________, the auditor performs tests of controls and substantive procedures.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
22
Which SOX section requires the public accounting firm that audits the financial statements of the company to issue an attestation report regarding the effectiveness of the company's internal controls?
A)
A)

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
23
It is not possible for a material weakness in internal control over financial reporting to exist even though the financial statements are not materially misstated.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
24
Which COSO Internal Control-Integrated Framework essential component of an effective internal control system involves identifying, analyzing, and managing risks that affect a company's ability to record, process, summarize, and report financial data properly?
A)Risk Assessment
B)Control Environment
C)Control Activities
D)Monitoring
A)Risk Assessment
B)Control Environment
C)Control Activities
D)Monitoring

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
25
To comply with SOX, companies must use a framework for evaluating internal control.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
26
A(n)________ over financial reporting requires the auditor to conduct tests of controls to obtain evidence that internal control over financial reporting has operated effectively.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
27
Which organization was created by the Sarbanes-Oxley Act of 2002?
A)Public Company Accounting Oversight Board (PCAOB)
B)Institute of Management Accountants (IMA)
C)American Accounting Association (AAA)
D)Committee of Sponsoring Organizations of the Treadway Commission (COSO)
A)Public Company Accounting Oversight Board (PCAOB)
B)Institute of Management Accountants (IMA)
C)American Accounting Association (AAA)
D)Committee of Sponsoring Organizations of the Treadway Commission (COSO)

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
28
In control activities, ________ ensure appropriate information processing, authorization, and data integrity.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
29
Which SOX section requires the chief executive officer and the chief financial officer to disclose to the auditors and the audit committee of the board of directors all significant deficiencies in internal controls, which could adversely affect the ability to record, process, summarize, and report financial data and any material weaknesses in internal controls?
A)
A)

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
30
Which of the following is not the purpose of internal controls?
A)Compliance with laws and regulations
B)Effectiveness and efficiency of operations
C)Public examine of private data
D)Reliability of financial reporting
A)Compliance with laws and regulations
B)Effectiveness and efficiency of operations
C)Public examine of private data
D)Reliability of financial reporting

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
31
In the COSO Internal Control-Integrated Framework, control activities do not include
A)Independent reconciliations of assets and accounting records
B)Physical controls
C)Segregation of duties
D)Management controls
A)Independent reconciliations of assets and accounting records
B)Physical controls
C)Segregation of duties
D)Management controls

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
32
When investigating fraud, ________ enables auditors to extract, analyze, and interpret evidence to detect unusual patterns and irregularities.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
33
What does Auditing Standard No. 5, an Audit of Internal Control Over Financial Reporting That Is Integrated with An Audit of Financial Statements, require the auditor to understand about IT?

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
34
The COSO ________ provides a blueprint for implementing an internal control system to assist in ensuring the reliability of financial statements and compliance with Sarbanes-Oxley legislation.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
35
In control activities, ________ divide authorization, recording, and asset custody among different individuals.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
36
What are the objectives of internal control?

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
37
Increasingly, the PCAOB is expecting auditors to understand how IT affects the audit and integrating IT into the audit.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
38
Physical controls ensure appropriate information processing, authorization, and data integrity.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
39
Which COSO Internal Control-Integrated Framework essential component of an effective internal control system includes the accounting system for identifying, recording, processing, and reporting transactions and financial data?
A)Monitoring
B)Information and Communication
C)Control Activities
D)Control Environment
A)Monitoring
B)Information and Communication
C)Control Activities
D)Control Environment

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
40
A(n)________, as required by Auditing Standard No. 5, integrates an audit of internal control with an audit of financial statements.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
41
What factors are part of the control environment?

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
42
Increasingly the expectation is that the auditor and the IT professional learn more about the other's field.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
43
Which IT process domain, as defined by COBIT, encompasses IT operations, security, and training?
A)Plan and Organize (PO)Domain
B)Deliver and Support (DS)Domain
C)Acquire and Implement (AI)Domain
D)Monitor and Evaluate (ME)Domain
A)Plan and Organize (PO)Domain
B)Deliver and Support (DS)Domain
C)Acquire and Implement (AI)Domain
D)Monitor and Evaluate (ME)Domain

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
44
Internal controls for the accounting system are incomplete without IT controls.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
45
Application controls ensure completeness and accuracy of transaction processing, authorization, and validity.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
46
IT general controls have a pervasive effect on all internal controls.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
47
In the COBIT framework, which IT resource category consists of manual and programmed procedures to process information?
A)Infrastructure
B)Applications
C)People
D)Information
A)Infrastructure
B)Applications
C)People
D)Information

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
48
While COSO is a broad framework for internal control in general, COBIT provides the detailed IT processes necessary to provide IT controls for monitoring and evaluating the IT environment.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
49
The COSO internal control component Information and Communication usually maps to which COBIT domain for IT processes?
A)PO2 Define the information architecture
B)PO1 Define a strategic IT plan
C)PO4 Define the IT processes, organization, and relationships
D)PO9 Assess and manage IT risks
A)PO2 Define the information architecture
B)PO1 Define a strategic IT plan
C)PO4 Define the IT processes, organization, and relationships
D)PO9 Assess and manage IT risks

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
50
List and describe the IT resources categories as defined by COBIT.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
51
________ controls include IT governance at top management levels where strategic business objectives are set and policies are established.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
52
Which of the following is not part of the information criteria as defined by COBIT?
A)Integrity
B)Scalability
C)Availability
D)Confidentiality
A)Integrity
B)Scalability
C)Availability
D)Confidentiality

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
53
COBIT provides high-level strategic guidance for meeting overall internal control objectives.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
54
Which IT process domain, as defined by COBIT, relates to IT strategy and tactics to contribute to attaining business goals?
A)Plan and Organize (PO)Domain
B)Deliver and Support (DS)Domain
C)Acquire and Implement (AI)Domain
D)Monitor and Evaluate (ME)Domain
A)Plan and Organize (PO)Domain
B)Deliver and Support (DS)Domain
C)Acquire and Implement (AI)Domain
D)Monitor and Evaluate (ME)Domain

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
55
The COSO internal control component Control Activities usually maps to which COBIT domain for IT processes?
A)PO9 Assess and manage IT risks
B)ME4 Provide IT governance
C)AI5 Procure IT resources
D)PO1 Define a strategic IT plan
A)PO9 Assess and manage IT risks
B)ME4 Provide IT governance
C)AI5 Procure IT resources
D)PO1 Define a strategic IT plan

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
56
What are the five essential components of an effective internal control system listed in COSO Internal Control-Integrated Framework?

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
57
List and describe the control activities for mitigating financial, operational, and compliance controls risks.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
58
________ controls support application controls to provide a reliable operating environment.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
59
Input controls ensure data is processed properly.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
60
List and describe the 10 generally accepted privacy principles.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
61
Match the DFD symbol to the name.
A)Agent
B)Dataflow
C)Datastore
D)Process

A)Agent
B)Dataflow
C)Datastore
D)Process


Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
62
In a HotSpot DFD, which color indicates the least risk?
A)Yellow
B)Orange
C)Red
D)Green
A)Yellow
B)Orange
C)Red
D)Green

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
63
Which of the following is not part of the audit committee's responsibilities?
A)The organization's compliance with legal and regulatory requirements
B)The integrity of the organization's financial statements and reports
C)The organization's policies regarding ethical conduct
D)The organization's ability to process data efficiently and effectively
A)The organization's compliance with legal and regulatory requirements
B)The integrity of the organization's financial statements and reports
C)The organization's policies regarding ethical conduct
D)The organization's ability to process data efficiently and effectively

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
64
Match the DFD symbol to the name.
A)Agent
B)Dataflow
C)Datastore
D)Process

A)Agent
B)Dataflow
C)Datastore
D)Process


Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
65
Control ________ are control weaknesses.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
66
What are the three major objectives of an IT audit?

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
67
When documenting HotSpots on DFDs, what types of controls are documented?
A)Detective controls
B)Preventative controls
C)Corrective controls
D)A and B
A)Detective controls
B)Preventative controls
C)Corrective controls
D)A and B

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
68
Internal controls are an integral part of business processes and the accompanying accounting transaction cycles.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
69
What are the three phases for documenting control HotSpots?

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
70
Match the DFD symbol to the name.
A)Agent
B)Dataflow
C)Datastore
D)Process

A)Agent
B)Dataflow
C)Datastore
D)Process


Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
71
What are the steps for building a HotSpot DFD?

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
72
Application controls for business processes cannot be documented using DFDs.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
73
What do the audit committee's responsibilities include?

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
74
Which level in the company corresponds to the Entity-Level IT Controls?
A)Top management
B)Information management
C)Business processes
D)IT services
A)Top management
B)Information management
C)Business processes
D)IT services

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
75
Match the DFD symbol to the name.
A)Agent
B)Dataflow
C)Datastore
D)Process

A)Agent
B)Dataflow
C)Datastore
D)Process


Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
76
Which general IT control includes control over SDLC phases for software upgrades and modifications?
A)Program development controls
B)Access security controls
C)Computer operations controls
D)Program change controls
A)Program development controls
B)Access security controls
C)Computer operations controls
D)Program change controls

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
77
Document the preventive and detective controls on the Books Ga'Lore! shipping DFD.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
78
Which general IT control covers acquisition, implementation, and maintenance of system software including the operating system, DBMS, network software, and security software?
A)Access security controls
B)Computer operations controls
C)Program change controls
D)Program development controls
A)Access security controls
B)Computer operations controls
C)Program change controls
D)Program development controls

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
79
Books Ga'Lore! Shipping DFD 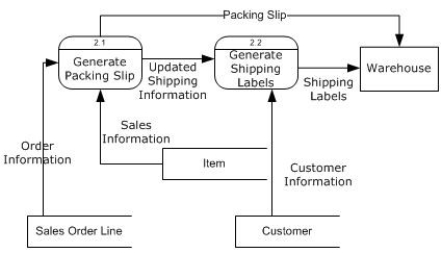
Using the Books Ga'Lore! shipping DFD, create an event-agent-datastore-control table.

Using the Books Ga'Lore! shipping DFD, create an event-agent-datastore-control table.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
80
In a HotSpot DFD, which color indicates the most risk?
A)Yellow
B)Orange
C)Red
D)Green
A)Yellow
B)Orange
C)Red
D)Green

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck



