Deck 7: Defining the System Architecture
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/86
Play
Full screen (f)
Deck 7: Defining the System Architecture
1
Although in common usage we refer to the Internet and the Web interchangeably,in reality they mean different things.
True
2
The Internet and the WWW are synonyms.
False
3
Describing the environment is one of the detailed activities of core process 4: Design system components.
True
4
In a client/server configuration the term "server" refers to the central computer equipment that houses the core resources.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
5
In a client/server configuration,it is possible for a single software component to be both client and server.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
6
The Web is the highway over which messages and information travel from network to network.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
7
A three-layer architecture requires at least three computers to be implemented correctly.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
8
A network diagram and a location diagram show basically the same information but in a different format.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
9
For a large company such as RMO,external hosting of part or all of the system is not usually a cost effective technique.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
10
Computer users are the primary beneficiaries of Web services since they can find new functions and interesting applications by searching the Web for new Web services.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
11
Application software that usually executes with a browser is often just called an "app".

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
12
A network diagram is a useful model to show three/layer architecture.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
13
The Internet can be thought of as the network of networks.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
14
The Amazon.com application can be considered a client/server architecture.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
15
Another term for a network diagram is a deployment diagram.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
16
The primary benefit of a network diagram,is to show the network cabling and the network routers.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
17
A location diagram can be used to indicate the locations of the client computers and the server computers in a client/server environment.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
18
A network diagram and a deployment diagram show basically the same information,just in a different format.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
19
In three-layer architecture,the three layers consist of the view layer,the business logic layer,and the domain layer.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
20
Computing devices include all of the following: a server computer,a laptop,a smartphone,Kindle reader,and Apple Watch.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
21
What does HTTP stand for?
A)Hypertext Timeline Process
B)Hypertext Translation Protocol
C)Hypertext Transfer Protocol
D)Hyperlink Text Transfer Process
A)Hypertext Timeline Process
B)Hypertext Translation Protocol
C)Hypertext Transfer Protocol
D)Hyperlink Text Transfer Process

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
22
System software usually refers to what kind of software?
A)Software that runs on servers but not on personal devices
B)Operating systems and web servers
C)All the software in an information system
D)Software that runs on a specific system
A)Software that runs on servers but not on personal devices
B)Operating systems and web servers
C)All the software in an information system
D)Software that runs on a specific system

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
23
What is the latest version of HTML?
A)HTML4
B)HTML5
C)HTML6
D)HTMLS
A)HTML4
B)HTML5
C)HTML6
D)HTMLS

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
24
Given the following URL,what is the correct description of the portion shown in bold?
Http://www.barnesandnoble.com/u/books-best selling-books/379003057
A)The protocol
B)The resource name
C)The server name
D)The company name
Http://www.barnesandnoble.com/u/books-best selling-books/379003057
A)The protocol
B)The resource name
C)The server name
D)The company name

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
25
A personal computing device includes all of the following except ______.
A)a laptop
B)a smartphone
C)a Kindle Reader
D)a router
A)a laptop
B)a smartphone
C)a Kindle Reader
D)a router

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
26
What is a computer that manages shared resources for access across a network called?
A)A hosted server
B)Software as a Service (SaaS)
C)A server computer
D)A mainframe computer
A)A hosted server
B)Software as a Service (SaaS)
C)A server computer
D)A mainframe computer

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
27
When a URL of a Web resource is embedded within a Web page,it is called a(n)________.
A)hyperlink
B)hot spot
C)embedded URL
D)mouse over
A)hyperlink
B)hot spot
C)embedded URL
D)mouse over

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
28
A method of organizing software applications so that the data and core processing is in a central location and access to that core is distributed on user's computing devices is called ________.
A)application architecture
B)client/server architecture
C)technology architecture
D)three-layer architecture
A)application architecture
B)client/server architecture
C)technology architecture
D)three-layer architecture

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
29
A toolbar might be considered an example of what?
A)An App
B)Browser Software
C)System Software
D)Embedded Software
A)An App
B)Browser Software
C)System Software
D)Embedded Software

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
30
An approach to implementing a software application where little or no software is installed and local computers,where the data is isolated between organizations a service computer is called _______.
A)a software service
B)a Web service
C)a remote application
D)software as a service
A)a software service
B)a Web service
C)a remote application
D)software as a service

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
31
What does XML stand for?
A)Extra modified language
B)Extreme modeling links
C)Extended modeling language
D)Extensible markup language
A)Extra modified language
B)Extreme modeling links
C)Extended modeling language
D)Extensible markup language

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
32
Which of the following is NOT one of the activities of Core Process 4: Design system components?
A)Describe the environment
B)Design the user interface
C)Design application components
D)Design security and integrity controls
A)Describe the environment
B)Design the user interface
C)Design application components
D)Design security and integrity controls

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
33
A set of languages,rules and procedures to facilitate data exchange between among hardware and software components is called a(n)_______.
A)uniform resource locator
B)hypertext markup language
C)protocol
D)standard
A)uniform resource locator
B)hypertext markup language
C)protocol
D)standard

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
34
Which of the following diagrams is correct?
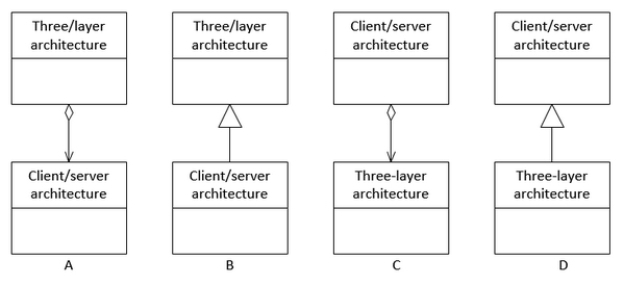
A)A
B)B
C)C
D)D

A)A
B)B
C)C
D)D

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
35
What is the difference between HTTP and HTTPS?
A)No difference, just different names.
B)HTTP is more secure than HTTPS
C)HTTP is old technology, while HTTPS is the new standard
D)Amazon uses HTTPS for credit card information
A)No difference, just different names.
B)HTTP is more secure than HTTPS
C)HTTP is old technology, while HTTPS is the new standard
D)Amazon uses HTTPS for credit card information

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
36
When we use the term the Web what is the correct definition?
A)The set of interconnected networks that cover the world
B)The set of world wide resources that are available over the Internet
C)The set of server computers that connect to the Internet
D)The set of networks and computers that support the Internet
A)The set of interconnected networks that cover the world
B)The set of world wide resources that are available over the Internet
C)The set of server computers that connect to the Internet
D)The set of networks and computers that support the Internet

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
37
A function or service that is called from a Web application to another Web application is called a(n)________.
A)hyperlink
B)Web service
C)remote procedure call
D)software as a service
A)hyperlink
B)Web service
C)remote procedure call
D)software as a service

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
38
The set of computing hardware,network hardware and system software used by an organization is called the _________.
A)application architecture
B)technology architecture
C)system architecture
D)client/server architecture
A)application architecture
B)technology architecture
C)system architecture
D)client/server architecture

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
39
Which of the following is not a valid Web protocol?
A)VPN
B)HTTPS
C)HTML
D)XML
A)VPN
B)HTTPS
C)HTML
D)XML

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
40
Web-based application is software with the following characteristics:
A)Executes only on a Web server
B)Is written with html
C)Is installed on a personal computing device
D)Uses a browser and web-server
A)Executes only on a Web server
B)Is written with html
C)Is installed on a personal computing device
D)Uses a browser and web-server

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
41
Which of the following are key questions that may be used to describe the environment? (choose all that apply)
A)Where will the users be located?
B)What data conversion techniques will be used?
C)What software applications need to be deployed?
D)Who are the key system engineers?
E)What operating systems are being used?
F)What are the data bases that will be used?
A)Where will the users be located?
B)What data conversion techniques will be used?
C)What software applications need to be deployed?
D)Who are the key system engineers?
E)What operating systems are being used?
F)What are the data bases that will be used?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
42
Amazon.com is a good example of what kind of architecture?
A)Web based architecture
B)three-layer architecture
C)server based architecture
D)server farm architecture
A)Web based architecture
B)three-layer architecture
C)server based architecture
D)server farm architecture

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
43
In a three-layer architecture,what are the three layers?
A)view layer, business logic layer, and data layer
B)view, service layer, domain layer
C)client layer, view layer, and data layer
D)client layer, domain layer, and server layer
A)view layer, business logic layer, and data layer
B)view, service layer, domain layer
C)client layer, view layer, and data layer
D)client layer, domain layer, and server layer

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
44
What does LAN stand for?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
45
When Designing Application Components,which characteristics of use cases are helpful to define component boundaries? (choose all that apply)
A)Must be installed concurrently
B)Require the same security level
C)Sharing common data
D)Similarities in actors
E)Have the same pre-conditions
F)Triggered by same events
A)Must be installed concurrently
B)Require the same security level
C)Sharing common data
D)Similarities in actors
E)Have the same pre-conditions
F)Triggered by same events

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
46
In the activity Designing Application Components which of the following tasks should be considered? (choose all that apply)
A)Determine integration requirements between components
B)Determine which user interface technique will be used for the components
C)Determine which DBMS will be utilized
D)Determine the test cases for integrating the application components
E)Determine the classes and methods in each component
F)Determine the boundaries of the various application components
A)Determine integration requirements between components
B)Determine which user interface technique will be used for the components
C)Determine which DBMS will be utilized
D)Determine the test cases for integrating the application components
E)Determine the classes and methods in each component
F)Determine the boundaries of the various application components

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
47
What are the layers of a three-layer architecture? (choose all that apply)
A)data layer
B)domain layer
C)client layer
D)server layer
E)application layer
F)user interface layer
A)data layer
B)domain layer
C)client layer
D)server layer
E)application layer
F)user interface layer

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
48
What are the characteristics of SAAS? (Choose all that apply)
A)Costs are calculated on a "use" basis
B)Software is installed remotely with no local involvement
C)User data is stored and isolated on central computers
D)Services are usually available during specified time periods
E)Little, if any, software is installed on the user's computer
F) SAAS company often deploys an on sight employee to assist the client
A)Costs are calculated on a "use" basis
B)Software is installed remotely with no local involvement
C)User data is stored and isolated on central computers
D)Services are usually available during specified time periods
E)Little, if any, software is installed on the user's computer
F) SAAS company often deploys an on sight employee to assist the client

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
49
In a three-layer architecture,the application server would be part of which layer?
A)view layer
B)business logic layer
C)data layer
D)server layer
A)view layer
B)business logic layer
C)data layer
D)server layer

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
50
Which of the following are examples of embedded software? (choose all that apply)
A)Toolbars
B)POS systems
C)User interfaces
D)DBMSs
E)Operating systems
F)Widgets
A)Toolbars
B)POS systems
C)User interfaces
D)DBMSs
E)Operating systems
F)Widgets

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
51
The model that best shows how software components are distributed across hardware components is the ________.
A)client/server diagram
B)location diagram
C)network diagram
D)deployment diagram
A)client/server diagram
B)location diagram
C)network diagram
D)deployment diagram

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
52
A software architecture that divides an application into view,business logic,and data is called a(n)________.
A)distributed architecture
B)two-layer architecture
C)three-layer architecture
D)client/server architecture
A)distributed architecture
B)two-layer architecture
C)three-layer architecture
D)client/server architecture

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
53
A computer that manages shared resources and allows users to access those resources over a network is called a(n)______.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
54
The high-speed,high capacity network that interconnects regions,countries,and continents is called the _____ _____ _____.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
55
The activity of Describing the Environment consists of what two key elements?
A)Internal systems and application architecture
B)External systems and technology architecture
C)External systems and internal applications
D)Software applications and database technology
A)Internal systems and application architecture
B)External systems and technology architecture
C)External systems and internal applications
D)Software applications and database technology

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
56
Which of the following activities are included in the core process of Design System Components? (choose all that apply)
A)Describe the environment
B)Describe the network
C)Design the software classes
D)Design the database
E)Design the security elements
F)Design the graphics
A)Describe the environment
B)Describe the network
C)Design the software classes
D)Design the database
E)Design the security elements
F)Design the graphics

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
57
A small computer network that is deployed in a single building or small office is called a(n)______ ______ ______.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
58
The set of resources that can be accessed over the Internet is referred to was the ______ _____ ______.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
59
What are the characteristics of a Web service? (choose all that apply)
A)Does not execute on the calling applications computer
B)Input data is sent via an attachment
C)Has a charge or cost associated with it each time it is used
D)Returns results encoded as a Web page
E)Client data is stored on a central server
F)Is called via a URL
A)Does not execute on the calling applications computer
B)Input data is sent via an attachment
C)Has a charge or cost associated with it each time it is used
D)Returns results encoded as a Web page
E)Client data is stored on a central server
F)Is called via a URL

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
60
Which of the following are examples of distributed architectures? (choose all that apply)
A)technology architecture
B)three-layer architecture
C)application architecture
D)client/server architecture
E) browser based architecture
F)LAN architecture
A)technology architecture
B)three-layer architecture
C)application architecture
D)client/server architecture
E) browser based architecture
F)LAN architecture

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
61
What does SaaS stand for?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
62
What does HTML stand for?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
63
A language that is an extension of HTML that allows the user to define new tags is called ______ ______ ______.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
64
A secure communications scheme that utilizes the Internet but with very secure technologies so that it appears as a dedicated network is called a(n)_____ _____ _____.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
65
The identifier of a Web resource and which defines a protocol,a server or domain name,and a resource identifier is called a(n)______ ______ ______.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
66
What does XML stand for?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
67
A client/server architecture that divides an application into view,business logic and data layers is called _____ _____ ______.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
68
Software that performs user- or business-specific tasks is called ______ ______.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
69
When a URL of Web resource is embedded within a Web page,it is called a(n)______.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
70
The set of computing hardware,network hardware and system software in an organization is usually referred to as the ______ ______.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
71
A protocol that defines the structure and content of a web page is called _____ _____ _____.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
72
A software function or set of functions or services that can be executed via Web protocols is called a(n)______ ______.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
73
A ______ is a set of languages,rules,and procedures to facilitate accurate data exchange.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
74
The set of information systems the organization needs to support its operations is often called the ______ ______.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
75
An application that uses a browser for the user interface is usually called a(n)______ ______.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
76
Software,such as Web server software,and works behind the scenes is called ______ ______.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
77
A protocol that defines the format and content of Web requests and data communication is called _____ _____ _____.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
78
What does HTTP stand for?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
79
What does HTTPS stand for?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
80
What does URL stand for?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck



