Deck 5: Local Area Networks
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/150
Play
Full screen (f)
Deck 5: Local Area Networks
1
In the early years of personal computers,networks were plentiful.
False
2
A transceiver is a combination of a transmitter and a receiver.
True
3
Most routers supply a WAN port designed for an Internet connection.
True
4
A WAN provides connectivity within a limited geographical area,often within a single building.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
5
A cryptographic algorithm is a word,number,or phrase that must be known to encrypt or decrypt a message.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
6
A process called handshaking allows two communications devices on a network to negotiate their communications protocols.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
7
Microwaves cannot be aimed in a single direction and they have less carrying capacity than radio waves.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
8
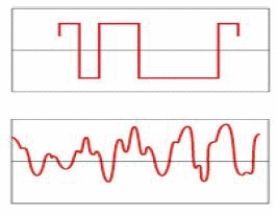
The wave on the top in the accompanying figure depicts an analog signal.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
9
A packet always travels from the source directly to the destination,never traveling through intermediate routing devices.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
10

The wave on the bottom in the accompanying figure depicts a digital signal.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
11
Windows automatically senses nearby networks and displays their SSIDs.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
12
MAC addresses are used for some low-level network functions and can also be employed to establish network security.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
13
Bluetooth is often used to connect workstations to a LAN.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
14
WPA2 makes sure that packets have not been intercepted or tampered with in any way.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
15

In the accompanying figure,the item on the right can be installed in an expansion slot inside the system unit of a desktop computer.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
16
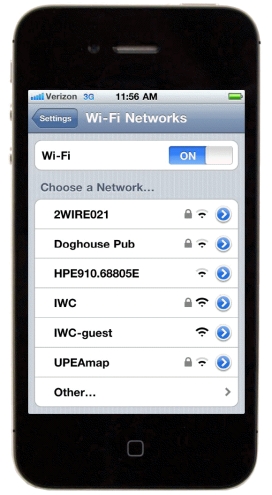
In the accompanying figure,the networks that don't have an icon of a lock next to them aren't secured,and are open targets for hackers to steal data,spread viruses,and create a launching pad for spam.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
17
A gateway joins two different types of networks.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
18

In the accompanying figure,the item on the left simply plugs into a serial port on the outside of the system unit.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
19
IP addresses can be assigned by ISPs or system managers.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
20

In the accompanying figure,the item on the left can be used with a laptop or desktop computer.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
21
If you are using a file server without its own keyboard or monitor,server configuration software is accessible using a(n) (browser)._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
22
A ____ is NOT a type of network device.
A) hub
B) switch
C) workstation
D) router
A) hub
B) switch
C) workstation
D) router

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
23
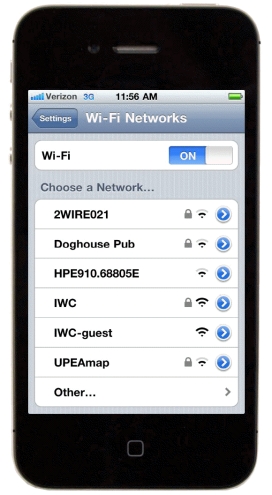
In the accompanying figure,IWC-guest is a(n) (secure) network._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
24
(Public key) encryption uses one key to encrypt a message and another key to decrypt it._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
25
A wireless (ad hoc) network uses a centralized broadcasting device,such as a wireless access point or router._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
26
The Internet is the world's largest example of a(n) (LAN)._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
27
A ____ is a public high-speed network capable of voice and data transmission within a range of about 50 miles.
A) LAN
B) PAN
C) MAN
D) WAN
A) LAN
B) PAN
C) MAN
D) WAN

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
28
Data in a(n) (wired) network travels without the use of network cables._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
29
If networked,____ can be accessed by an authorized LAN user.
A) scanners
B) high-capacity storage devices
C) photo printers
D) all of the above
A) scanners
B) high-capacity storage devices
C) photo printers
D) all of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
30
The best-known communications protocol is probably (SMTP),which regulates Internet data transport._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
31

When network discovery is turned on in a wireless network,any Wi-Fi enabled device within range of your network,such as the one shown in the accompanying figure,can see its (URL)._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
32
A LAN would be used to ____.
A) connect personal computers within a very limited geographical area,such as a single building
B) connect several smaller networks together
C) provide high-speed connectivity for a metropolitan area
D) connect devices over a large geographical area
A) connect personal computers within a very limited geographical area,such as a single building
B) connect several smaller networks together
C) provide high-speed connectivity for a metropolitan area
D) connect devices over a large geographical area

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
33
A ____ is a term sometimes used to refer to the interconnection of personal digital devices or consumer electronics within a range of about 30 feet and without the use of wires or cables.
A) LAN
B) WAN
C) MAN
D) PAN
A) LAN
B) WAN
C) MAN
D) PAN

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
34
A storage device that directly connects to a network is called network (peripheral storage)._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
35
(Microwaves) are electromagnetic signals that can be aimed in a single direction and have more carrying capacity than radio waves._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
36
The process of converting ciphertext into plaintext is called (encryption)._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
37
High-bandwidth communications systems,such as cable TV and DSL,are sometimes referred to as (peakband)._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
38
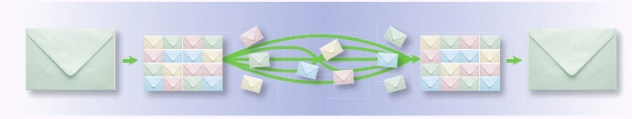
A more efficient alternative to (packet) switching is shown in the accompanying figure._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
39
Wi-Fi signals (cannot) be disrupted by interference from devices such as microwave ovens,cordless telephones,and baby monitors._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
40

In the accompanying figure,the lock icon indicates a network secured with (wired) encryption._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
41
Two devices on a network might have to negotiate their communications protocols through a process called ____.
A) handshaking
B) synchronization
C) realization
D) introduction
A) handshaking
B) synchronization
C) realization
D) introduction

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
42
____ is a disadvantage of using a wireless network when compared to a wired network.
A) Speed
B) Range
C) Security
D) all of the above
A) Speed
B) Range
C) Security
D) all of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
43
Dial-up Internet access is an example of a(n)____ communications system.
A) broadband
B) fireband
C) narrowband
D) Internet 2
A) broadband
B) fireband
C) narrowband
D) Internet 2

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
44
The original Ethernet standard carried data over a coaxial cable bus topology at ____.
A) 10 Mbps
B) 100 Mbps
C) 10 Gbps
D) 100 Gbps
A) 10 Mbps
B) 100 Mbps
C) 10 Gbps
D) 100 Gbps

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
45
To connect to a LAN,a computer requires ____.
A) a peer-to-peer network
B) network attached storage
C) a network interface card
D) a client
A) a peer-to-peer network
B) network attached storage
C) a network interface card
D) a client

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
46
Most wireless networks transport data as ____ signals.
A) infrared
B) satellite
C) microwave
D) RF (radio frequency)
A) infrared
B) satellite
C) microwave
D) RF (radio frequency)

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
47
High-bandwidth communications systems are sometimes referred to as ____.
A) quickband
B) broadband
C) fireband
D) Internet 2
A) quickband
B) broadband
C) fireband
D) Internet 2

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
48
On an Ethernet,a ____ is broadcast to every device but is accepted only by the device to which it is addressed.
A) code
B) packet
C) band
D) node
A) code
B) packet
C) band
D) node

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
49
A wired network is one that uses ____ to connect network devices.
A) NICs
B) radio frequency waves
C) cables
D) infrared light
A) NICs
B) radio frequency waves
C) cables
D) infrared light

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
50
A protocol known as ____ is designed to automatically distribute IP addresses.
A) DHCP
B) packet switching
C) CSMA/CD
D) a piconet
A) DHCP
B) packet switching
C) CSMA/CD
D) a piconet

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
51
Which of the following is NOT an advantage of using a wired network?
A) Increased security
B) Fast access
C) Simple to configure
D) Unlimited mobility
A) Increased security
B) Fast access
C) Simple to configure
D) Unlimited mobility

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
52
Ethernet networks ____.
A) are difficult to implement,manage,and maintain
B) use a nonproprietary technology,making Ethernet equipment available from a variety of vendors
C) do not offer much flexibility in network design
D) are not compatible with Wi-Fi wireless networks
A) are difficult to implement,manage,and maintain
B) use a nonproprietary technology,making Ethernet equipment available from a variety of vendors
C) do not offer much flexibility in network design
D) are not compatible with Wi-Fi wireless networks

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
53
Ethernet is a wired technology that is defined by ____ standards.
A) IEEE 802.2
B) IEEE 802.3
C) IEEE 802.7
D) IEEE 802.11
A) IEEE 802.2
B) IEEE 802.3
C) IEEE 802.7
D) IEEE 802.11

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
54
In the technology referred to as ____,a message is divided into several parcels that can be routed independently to their destination.
A) packet switching
B) handshaking
C) circuit switching
D) protocol
A) packet switching
B) handshaking
C) circuit switching
D) protocol

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
55
A network ____ usually contains a computer,networked peripheral,or network device.
A) node
B) file
C) application
D) index
A) node
B) file
C) application
D) index

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
56
The IEEE designation for the Gigabit Ethernet standard is ____.
A) IEEE 802.3
B) IEEE 802.3ae
C) IEEE 802.3u
D) IEEE 802.3z
A) IEEE 802.3
B) IEEE 802.3ae
C) IEEE 802.3u
D) IEEE 802.3z

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
57
The most important network device is a ____.
A) router
B) switch
C) hub
D) wireless access point
A) router
B) switch
C) hub
D) wireless access point

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
58
Ethernet is easy to ____.
A) implement
B) maintain
C) manage
D) All of the above
A) implement
B) maintain
C) manage
D) All of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
59
The telephone system uses a technology called ____,which establishes a dedicated,private link between telephones for the duration of a call.
A) packet switching
B) circuit switching
C) bus switching
D) ring switching
A) packet switching
B) circuit switching
C) bus switching
D) ring switching

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
60
A ____ is a physical path or a frequency used for signal transmissions.
A) logical channel
B) communications channel
C) connecting link
D) node link
A) logical channel
B) communications channel
C) connecting link
D) node link

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
61
Most routers ship with a(n)____ predefined by the manufacturer.
A) gateway
B) ISP
C) SSID
D) topology
A) gateway
B) ISP
C) SSID
D) topology

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
62
In a wireless ____ network,devices broadcast directly to each other.
A) ad-hoc
B) infrastructure
C) embedded
D) SSID
A) ad-hoc
B) infrastructure
C) embedded
D) SSID

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
63
Wireless signal range can be limited by ____.
A) the type of signal
B) the physical environment
C) transmitter strength
D) all of the above
A) the type of signal
B) the physical environment
C) transmitter strength
D) all of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
64
____ is NOT true.
A) When lots of computer game players compete against each other over a LAN,a fast,wired network is desirable.
B) Speed increases as signal strength decreases.
C) On wireless connections,signal strength varies depending on distance from the transmitter and obstacles that might interfere with the signal.
D) Despite interference,wireless networks are fast enough for most applications.
A) When lots of computer game players compete against each other over a LAN,a fast,wired network is desirable.
B) Speed increases as signal strength decreases.
C) On wireless connections,signal strength varies depending on distance from the transmitter and obstacles that might interfere with the signal.
D) Despite interference,wireless networks are fast enough for most applications.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
65
Legacy equipment without Wi-Fi can be outfitted with a Wi-Fi adapter that plugs into a(n)____.
A) USB port
B) internal expansion slot
C) either a.or b.
D) neither a.nor b.
A) USB port
B) internal expansion slot
C) either a.or b.
D) neither a.nor b.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
66
A ____ is a network device that extends the range of a network by restoring signals to maximum strength and retransmitting them.
A) bridge
B) hub
C) switch
D) repeater
A) bridge
B) hub
C) switch
D) repeater

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
67
To stay with the current Wi-Fi standard,make sure your device is compatible with ____.
A) 802.11b
B) 802.11g
C) 802.11n
D) 802.11p
A) 802.11b
B) 802.11g
C) 802.11n
D) 802.11p

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
68
The configuration settings are stored in the router's ____ memory.
A) EEPRAM
B) EEPROM
C) IEEROM
D) IEERAM
A) EEPRAM
B) EEPROM
C) IEEROM
D) IEERAM

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
69
____ is a wireless MAN or WAN technology commonly used for fixed Internet access.
A) FCC
B) WiMAX
C) Bluetooth
D) Ethernet
A) FCC
B) WiMAX
C) Bluetooth
D) Ethernet

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
70
A ____ is a network device that extends a wired network by adding additional ports.
A) bridge
B) hub
C) switch
D) repeater
A) bridge
B) hub
C) switch
D) repeater

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
71
Before using your network,you should adjust the configuration settings of the ____ to make sure your network is secure.
A) gateway
B) router
C) bridge
D) repeater
A) gateway
B) router
C) bridge
D) repeater

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
72
Legacy equipment without Wi-Fi can be upgraded using a Wi-Fi ____.
A) FireWire
B) adapter
C) port
D) cable
A) FireWire
B) adapter
C) port
D) cable

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
73
Devices with one or more antennas use ____ technology to boost signals and spread them more evenly over the signal range.
A) WiMAX
B) MIMO
C) Zigbee
D) MAN
A) WiMAX
B) MIMO
C) Zigbee
D) MAN

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
74
A Wi-Fi device ____.
A) transmits data as radio waves
B) is compatible with Ethernet
C) both a.and b.
D) neither a.nor b.
A) transmits data as radio waves
B) is compatible with Ethernet
C) both a.and b.
D) neither a.nor b.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
75
A ____ is a network device that intelligently facilitates communication among multiple devices on a network.
A) bridge
B) hub
C) switch
D) repeater
A) bridge
B) hub
C) switch
D) repeater

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
76
In areas where there are overlapping wireless networks,such as in a city or on a college campus,____ help you log in to the right network,rather than a network run by a hacker who will try to suck important information off your computer as soon as you connect.
A) topographical maps
B) routers
C) ISPs
D) SSIDs
A) topographical maps
B) routers
C) ISPs
D) SSIDs

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
77
A true statement about Bluetooth is ____.
A) It requires cables to connect electronic devices.
B) It has a very long transmission range of over 500 feet.
C) It is used exclusively to connect workstations to a LAN.
D) It forms networks automatically when two or more devices in discovery mode are within range.
A) It requires cables to connect electronic devices.
B) It has a very long transmission range of over 500 feet.
C) It is used exclusively to connect workstations to a LAN.
D) It forms networks automatically when two or more devices in discovery mode are within range.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
78
To access your router's configuration utility,open a browser and enter the router ____.
A) encryption key
B) serial number
C) address
D) password
A) encryption key
B) serial number
C) address
D) password

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
79
The most popular wireless LAN technology is ____.
A) WUSB (Wireless USB)
B) Wi-Fi
C) Bluetooth
D) WiMAX
A) WUSB (Wireless USB)
B) Wi-Fi
C) Bluetooth
D) WiMAX

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
80
In ____ mode two Bluetooth devices can find each other and exchange passkeys.
A) distance
B) locational
C) transmission
D) discovery
A) distance
B) locational
C) transmission
D) discovery

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck



