Deck 41: Implementing Cisco Collaboration Core Technologies (CLCOR)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/213
Play
Full screen (f)
Deck 41: Implementing Cisco Collaboration Core Technologies (CLCOR)
1
What are two DDoS attack categories? (Choose two.)
A) protocol
B) source-based
C) database
D) sequential
E) volume-based
A) protocol
B) source-based
C) database
D) sequential
E) volume-based
protocol
volume-based
volume-based
2
Which two capabilities does TAXII support? (Choose two.)
A) exchange
B) pull messaging
C) binding
D) correlation
E) mitigating
A) exchange
B) pull messaging
C) binding
D) correlation
E) mitigating
pull messaging
binding
binding
3
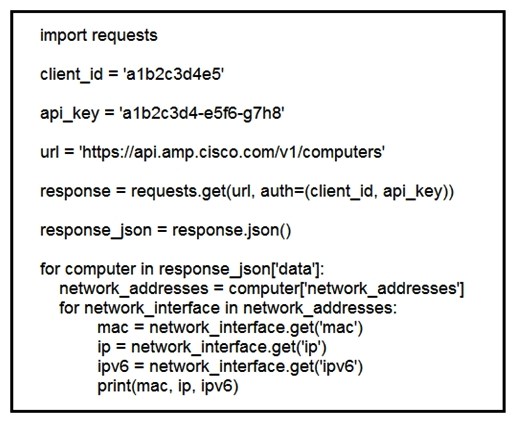 Refer to the exhibit. What does the API do when connected to a Cisco security appliance?
Refer to the exhibit. What does the API do when connected to a Cisco security appliance?A) create an SNMP pull mechanism for managing AMP
B) gather network telemetry information from AMP for endpoints
C) get the process and PID information from the computers in the network
D) gather the network interface information about the computers AMP sees
gather the network interface information about the computers AMP sees
4
How does DNS Tunneling exfiltrate data?
A) An attacker registers a domain that a client connects to based on DNS records and sends malware through that connection.
B) An attacker opens a reverse DNS shell to get into the client's system and install malware on it.
C) An attacker sends an email to the target with hidden DNS resolvers in it to redirect them to a malicious domain.
D) An attacker uses a non-standard DNS port to gain access to the organization's DNS servers in order to poison the resolutions.
A) An attacker registers a domain that a client connects to based on DNS records and sends malware through that connection.
B) An attacker opens a reverse DNS shell to get into the client's system and install malware on it.
C) An attacker sends an email to the target with hidden DNS resolvers in it to redirect them to a malicious domain.
D) An attacker uses a non-standard DNS port to gain access to the organization's DNS servers in order to poison the resolutions.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
5
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed?
A) smurf
B) distributed denial of service
C) cross-site scripting
D) rootkit exploit
A) smurf
B) distributed denial of service
C) cross-site scripting
D) rootkit exploit

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
6
Which two kinds of attacks are prevented by multifactor authentication? (Choose two.)
A) phishing
B) brute force
C) man-in-the-middle
D) DDOS
E) tear drop
A) phishing
B) brute force
C) man-in-the-middle
D) DDOS
E) tear drop

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
7
How does Cisco Advanced Phishing Protection protect users?
A) It utilizes sensors that send messages securely.
B) It uses machine learning and real-time behavior analytics.
C) It validates the sender by using DKIM.
D) It determines which identities are perceived by the sender.
A) It utilizes sensors that send messages securely.
B) It uses machine learning and real-time behavior analytics.
C) It validates the sender by using DKIM.
D) It determines which identities are perceived by the sender.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
8
What are two rootkit types? (Choose two.)
A) registry
B) buffer mode
C) user mode
D) bootloader
E) virtual
A) registry
B) buffer mode
C) user mode
D) bootloader
E) virtual

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
9
Which two behavioral patterns characterize a ping of death attack? (Choose two.)
A) The attack is fragmented into groups of 16 octets before transmission.
B) The attack is fragmented into groups of 8 octets before transmission.
C) Short synchronized bursts of traffic are used to disrupt TCP connections.
D) Malformed packets are used to crash systems.
E) Publicly accessible DNS servers are typically used to execute the attack.
A) The attack is fragmented into groups of 16 octets before transmission.
B) The attack is fragmented into groups of 8 octets before transmission.
C) Short synchronized bursts of traffic are used to disrupt TCP connections.
D) Malformed packets are used to crash systems.
E) Publicly accessible DNS servers are typically used to execute the attack.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
10
Which two conditions are prerequisites for stateful failover for IPsec? (Choose two.)
A) Only the IKE configuration that is set up on the active device must be duplicated on the standby device; the IPsec configuration is copied automatically.
B) The active and standby devices can run different versions of the Cisco IOS software but must be the same type of device.
C) The IPsec configuration that is set up on the active device must be duplicated on the standby device.
D) Only the IPsec configuration that is set up on the active device must be duplicated on the standby device; the IKE configuration is copied automatically.
E) The active and standby devices must run the same version of the Cisco IOS software and must be the same type of device.
A) Only the IKE configuration that is set up on the active device must be duplicated on the standby device; the IPsec configuration is copied automatically.
B) The active and standby devices can run different versions of the Cisco IOS software but must be the same type of device.
C) The IPsec configuration that is set up on the active device must be duplicated on the standby device.
D) Only the IPsec configuration that is set up on the active device must be duplicated on the standby device; the IKE configuration is copied automatically.
E) The active and standby devices must run the same version of the Cisco IOS software and must be the same type of device.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
11
Which form of attack is launched using botnets?
A) TCP flood
B) DDOS
C) DOS
D) virus
A) TCP flood
B) DDOS
C) DOS
D) virus

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
12
The main function of northbound APIs in the SDN architecture is to enable communication between which two areas of a network?
A) SDN controller and the cloud
B) management console and the SDN controller
C) management console and the cloud
D) SDN controller and the management solution
A) SDN controller and the cloud
B) management console and the SDN controller
C) management console and the cloud
D) SDN controller and the management solution

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
13
A user has a device in the network that is receiving too many connection requests from multiple machines. Which type of attack is the device undergoing?
A) SYN flood
B) slowloris
C) phishing
D) pharming
A) SYN flood
B) slowloris
C) phishing
D) pharming

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
14
Which threat involves software being used to gain unauthorized access to a computer system?
A) ping of death
B) HTTP flood
C) NTP amplification
D) virus
A) ping of death
B) HTTP flood
C) NTP amplification
D) virus

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
15
Which two request methods of REST API are valid on the Cisco ASA Platform? (Choose two.)
A) put
B) options
C) get
D) push
E) connect
A) put
B) options
C) get
D) push
E) connect

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
16
What is a feature of the open platform capabilities of Cisco DNA Center?
A) application adapters
B) domain integration
C) intent-based APIs
D) automation adapters
A) application adapters
B) domain integration
C) intent-based APIs
D) automation adapters

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
17
An attacker needs to perform reconnaissance on a target system to help gain access to it. The system has weak passwords, no encryption on the VPN links, and software bugs on the system's applications. Which vulnerability allows the attacker to see the passwords being transmitted in clear text?
A) unencrypted links for traffic
B) weak passwords for authentication
C) improper file security
D) software bugs on applications
A) unencrypted links for traffic
B) weak passwords for authentication
C) improper file security
D) software bugs on applications

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
18
In which type of attach does the attacker insert their machine between two hosts that are communicating with each other?
A) man-in-the-middle
B) LDAP injection
C) insecure API
D) cross-site scripting
A) man-in-the-middle
B) LDAP injection
C) insecure API
D) cross-site scripting

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
19
Which functions of an SDN architecture require southbound APIs to enable communication?
A) SDN controller and the network elements
B) management console and the SDN controller
C) management console and the cloud
D) SDN controller and the cloud
A) SDN controller and the network elements
B) management console and the SDN controller
C) management console and the cloud
D) SDN controller and the cloud

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
20
Which type of attack is social engineering?
A) trojan
B) MITM
C) phishing
D) malware
A) trojan
B) MITM
C) phishing
D) malware

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
21
An organization has two machines hosting web applications. Machine 1 is vulnerable to SQL injection while machine 2 is vulnerable to buffer overflows. What action would allow the attacker to gain access to machine 1 but not machine 2?
A) sniffing the packets between the two hosts
B) sending continuous pings
C) overflowing the buffer's memory
D) inserting malicious commands into the database
A) sniffing the packets between the two hosts
B) sending continuous pings
C) overflowing the buffer's memory
D) inserting malicious commands into the database

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
22
Which algorithm provides encryption and authentication for data plane communication?
A) AES-GCM
B) SHA-96
C) AES-256
D) SHA-384
A) AES-GCM
B) SHA-96
C) AES-256
D) SHA-384

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
23
Which command enables 802.1X globally on a Cisco switch?
A) dot1x system-auth-control
B) dot1x pae authenticator
C) authentication port-control auto
D) aaa new-model
A) dot1x system-auth-control
B) dot1x pae authenticator
C) authentication port-control auto
D) aaa new-model

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
24
Which feature requires a network discovery policy on the Cisco Firepower Next Generation Intrusion Prevention System?
A) security intelligence
B) impact flags
C) health monitoring
D) URL filtering
A) security intelligence
B) impact flags
C) health monitoring
D) URL filtering

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
25
Which protocol provides the strongest throughput performance when using Cisco AnyConnect VPN?
A) DTLSv1
B) TLSv1
C) TLSv1.1
D) TLSv1.2
A) DTLSv1
B) TLSv1
C) TLSv1.1
D) TLSv1.2

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
26
A network engineer has entered the snmp-server user andy myv3 auth sha cisco priv aes 256 cisc0383320506 command and needs to send SNMP information to a host at 10.255.254.1. Which command achieves this goal?
A) snmp-server host inside 10.255.254.1 snmpv3 andy
B) snmp-server host inside 10.255.254.1 version 3 myv3
C) snmp-server host inside 10.255.254.1 snmpv3 myv3
D) snmp-server host inside 10.255.254.1 version 3 andy
A) snmp-server host inside 10.255.254.1 snmpv3 andy
B) snmp-server host inside 10.255.254.1 version 3 myv3
C) snmp-server host inside 10.255.254.1 snmpv3 myv3
D) snmp-server host inside 10.255.254.1 version 3 andy

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
27
Under which two circumstances is a CoA issued? (Choose two.)
A) A new authentication rule was added to the policy on the Policy Service node.
B) An endpoint is deleted on the Identity Service Engine server.
C) A new Identity Source Sequence is created and referenced in the authentication policy.
D) An endpoint is profiled for the first time.
E) A new Identity Service Engine server is added to the deployment with the Administration persona.
A) A new authentication rule was added to the policy on the Policy Service node.
B) An endpoint is deleted on the Identity Service Engine server.
C) A new Identity Source Sequence is created and referenced in the authentication policy.
D) An endpoint is profiled for the first time.
E) A new Identity Service Engine server is added to the deployment with the Administration persona.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
28
What is a language format designed to exchange threat intelligence that can be transported over the TAXII protocol?
A) STIX
B) XMPP
C) pxGrid
D) SMTP
A) STIX
B) XMPP
C) pxGrid
D) SMTP

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
29
Which technology must be used to implement secure VPN connectivity among company branches over a private IP cloud with any-to-any scalable connectivity?
A) DMVPN
B) FlexVPN
C) IPsec DVTI
D) GET VPN
A) DMVPN
B) FlexVPN
C) IPsec DVTI
D) GET VPN

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
30
What is a characteristic of traffic storm control behavior?
A) Traffic storm control drops all broadcast and multicast traffic if the combined traffic exceeds the level within the interval.
B) Traffic storm control cannot determine if the packet is unicast or broadcast.
C) Traffic storm control monitors incoming traffic levels over a 10-second traffic storm control interval.
D) Traffic storm control uses the Individual/Group bit in the packet source address to determine if the packet is unicast or broadcast.
A) Traffic storm control drops all broadcast and multicast traffic if the combined traffic exceeds the level within the interval.
B) Traffic storm control cannot determine if the packet is unicast or broadcast.
C) Traffic storm control monitors incoming traffic levels over a 10-second traffic storm control interval.
D) Traffic storm control uses the Individual/Group bit in the packet source address to determine if the packet is unicast or broadcast.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
31
What is a function of 3DES in reference to cryptography?
A) It encrypts traffic.
B) It creates one-time use passwords.
C) It hashes files.
D) It generates private keys.
A) It encrypts traffic.
B) It creates one-time use passwords.
C) It hashes files.
D) It generates private keys.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
32
Which two tasks allow NetFlow on a Cisco ASA 5500 Series firewall? (Choose two.)
A) Define a NetFlow collector by using the flow-export command
B) Create a class map to match interesting traffic
C) Create an ACL to allow UDP traffic on port 9996
D) Enable NetFlow Version 9
E) Apply NetFlow Exporter to the outside interface in the inbound direction
A) Define a NetFlow collector by using the flow-export command
B) Create a class map to match interesting traffic
C) Create an ACL to allow UDP traffic on port 9996
D) Enable NetFlow Version 9
E) Apply NetFlow Exporter to the outside interface in the inbound direction

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
33
When wired 802.1X authentication is implemented, which two components are required? (Choose two.)
A) authentication server: Cisco Identity Service Engine
B) supplicant: Cisco AnyConnect ISE Posture module
C) authenticator: Cisco Catalyst switch
D) authenticator: Cisco Identity Services Engine
E) authentication server: Cisco Prime Infrastructure
A) authentication server: Cisco Identity Service Engine
B) supplicant: Cisco AnyConnect ISE Posture module
C) authenticator: Cisco Catalyst switch
D) authenticator: Cisco Identity Services Engine
E) authentication server: Cisco Prime Infrastructure

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
34
Which type of API is being used when a security application notifies a controller within a software-defined network architecture about a specific security threat?
A) southbound API
B) westbound API
C) eastbound API
D) northbound API
A) southbound API
B) westbound API
C) eastbound API
D) northbound API

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
35
Which group within Cisco writes and publishes a weekly newsletter to help cybersecurity professionals remain aware of the ongoing and most prevalent threats?
A) Talos
B) PSIRT
C) SCIRT
D) DEVNET
A) Talos
B) PSIRT
C) SCIRT
D) DEVNET

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
36
Which statement about IOS zone-based firewalls is true?
A) An unassigned interface can communicate with assigned interfaces
B) Only one interface can be assigned to a zone.
C) An interface can be assigned to multiple zones.
D) An interface can be assigned only to one zone.
A) An unassigned interface can communicate with assigned interfaces
B) Only one interface can be assigned to a zone.
C) An interface can be assigned to multiple zones.
D) An interface can be assigned only to one zone.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
37
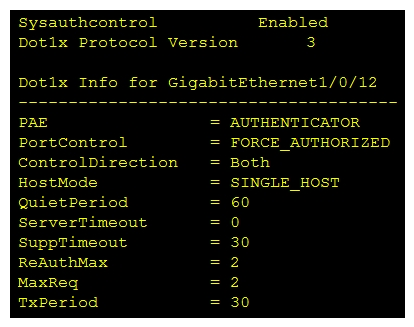 Refer to the exhibit. Which command was used to display this output?
Refer to the exhibit. Which command was used to display this output?A) show dot1x all
B) show dot1x
C) show dot1x all summary
D) show dot1x interface gi1/0/12

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
38
Which two activities can be done using Cisco DNA Center? (Choose two.)
A) DHCP
B) design
C) accounting
D) DNS
E) provision
A) DHCP
B) design
C) accounting
D) DNS
E) provision

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
39
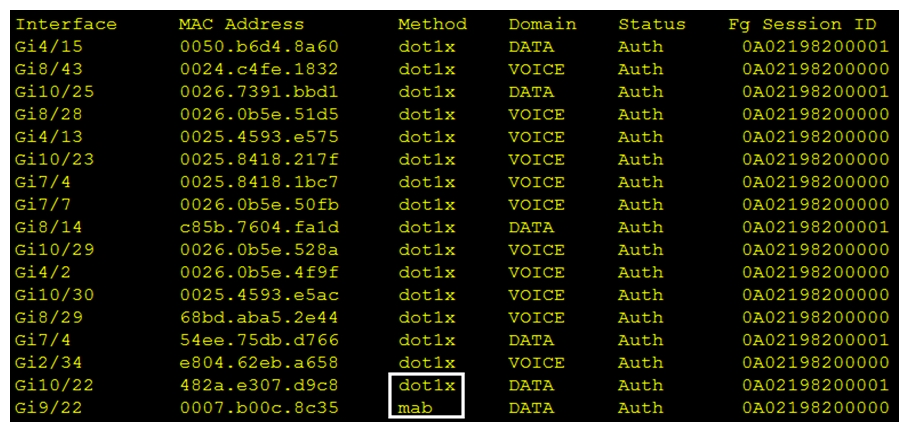 Refer to the exhibit. Which command was used to generate this output and to show which ports are authenticating with dot1x or mab?
Refer to the exhibit. Which command was used to generate this output and to show which ports are authenticating with dot1x or mab?A) show authentication registrations
B) show authentication method
C) show dot1x all
D) show authentication sessions

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
40
Which two features of Cisco DNA Center are used in a Software Defined Network solution? (Choose two.)
A) accounting
B) assurance
C) automation
D) authentication
E) encryption
A) accounting
B) assurance
C) automation
D) authentication
E) encryption

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
41
Which information is required when adding a device to Firepower Management Center?
A) username and password
B) encryption method
C) device serial number
D) registration key
A) username and password
B) encryption method
C) device serial number
D) registration key

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
42
A mall provides security services to customers with a shared appliance. The mall wants separation of management on the shared appliance. Which ASA deployment mode meets these needs?
A) routed mode
B) multiple zone mode
C) multiple context mode
D) transparent mode
A) routed mode
B) multiple zone mode
C) multiple context mode
D) transparent mode

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
43
 Refer to the exhibit. Traffic is not passing through IPsec site-to-site VPN on the Firepower Threat Defense appliance. What is causing this issue?
Refer to the exhibit. Traffic is not passing through IPsec site-to-site VPN on the Firepower Threat Defense appliance. What is causing this issue?A) Site-to-site VPN preshared keys are mismatched.
B) Site-to-site VPN peers are using different encryption algorithms.
C) No split-tunnel policy is defined on the Firepower Threat Defense appliance.
D) The access control policy is not allowing VPN traffic in.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
44
An engineer notices traffic interruptions on the network. Upon further investigation, it is learned that broadcast packets have been flooding the network. What must be configured, based on a predefined threshold, to address this issue?
A) Storm Control
B) embedded event monitoring
C) access control lists
D) Bridge Protocol Data Unit guard
A) Storm Control
B) embedded event monitoring
C) access control lists
D) Bridge Protocol Data Unit guard

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
45
Which exfiltration method does an attacker use to hide and encode data inside DNS requests and queries?
A) DNS tunneling
B) DNSCrypt
C) DNS security
D) DNSSEC
A) DNS tunneling
B) DNSCrypt
C) DNS security
D) DNSSEC

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
46
An engineer is trying to securely connect to a router and wants to prevent insecure algorithms from being used. However, the connection is failing. Which action should be taken to accomplish this goal?
A) Generate the RSA key using the crypto key generate rsa command. Generate the RSA key using the crypto key generate rsa command.
B) Configure the port using the ip ssh port 22 command. Configure the port using the ip ssh port 22
C) Enable the SSH server using the ip ssh server command. Enable the SSH server using the ip ssh server
D) Disable telnet using the no ip telnet command. Disable telnet using the no ip telnet
A) Generate the RSA key using the crypto key generate rsa command. Generate the RSA key using the crypto key generate rsa command.
B) Configure the port using the ip ssh port 22 command. Configure the port using the ip ssh port 22
C) Enable the SSH server using the ip ssh server command. Enable the SSH server using the ip ssh server
D) Disable telnet using the no ip telnet command. Disable telnet using the no ip telnet

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
47
Which feature is configured for managed devices in the device platform settings of the Firepower Management Center?
A) quality of service
B) time synchronization
C) network address translations
D) intrusion policy
A) quality of service
B) time synchronization
C) network address translations
D) intrusion policy

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
48
An engineer needs behavioral analysis to detect malicious activity on the hosts, and is configuring the organization's public cloud to send telemetry using the cloud provider's mechanisms to a security device. Which mechanism should the engineer configure to accomplish this goal?
A) sFlow
B) NetFlow
C) mirror port
D) VPC flow logs
A) sFlow
B) NetFlow
C) mirror port
D) VPC flow logs

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
49
What can be integrated with Cisco Threat Intelligence Director to provide information about security threats, which allows the SOC to proactively automate responses to those threats?
A) Cisco Umbrella
B) External Threat Feeds
C) Cisco Threat Grid
D) Cisco Stealthwatch
A) Cisco Umbrella
B) External Threat Feeds
C) Cisco Threat Grid
D) Cisco Stealthwatch

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
50
A network engineer is configuring DMVPN and entered the crypto isakmp key cisc0383320506 address 0.0.0.0 command on host A. The tunnel is not being established to host B. What action is needed to authenticate the VPN?
A) Change the password on host A to the default password
B) Enter the command with a different password on host B
C) Enter the same command on host B
D) Change isakmp to ikev2 in the command on host A Change isakmp to ikev2 in the command on host A
A) Change the password on host A to the default password
B) Enter the command with a different password on host B
C) Enter the same command on host B
D) Change isakmp to ikev2 in the command on host A Change isakmp to ikev2 in the command on host A

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
51
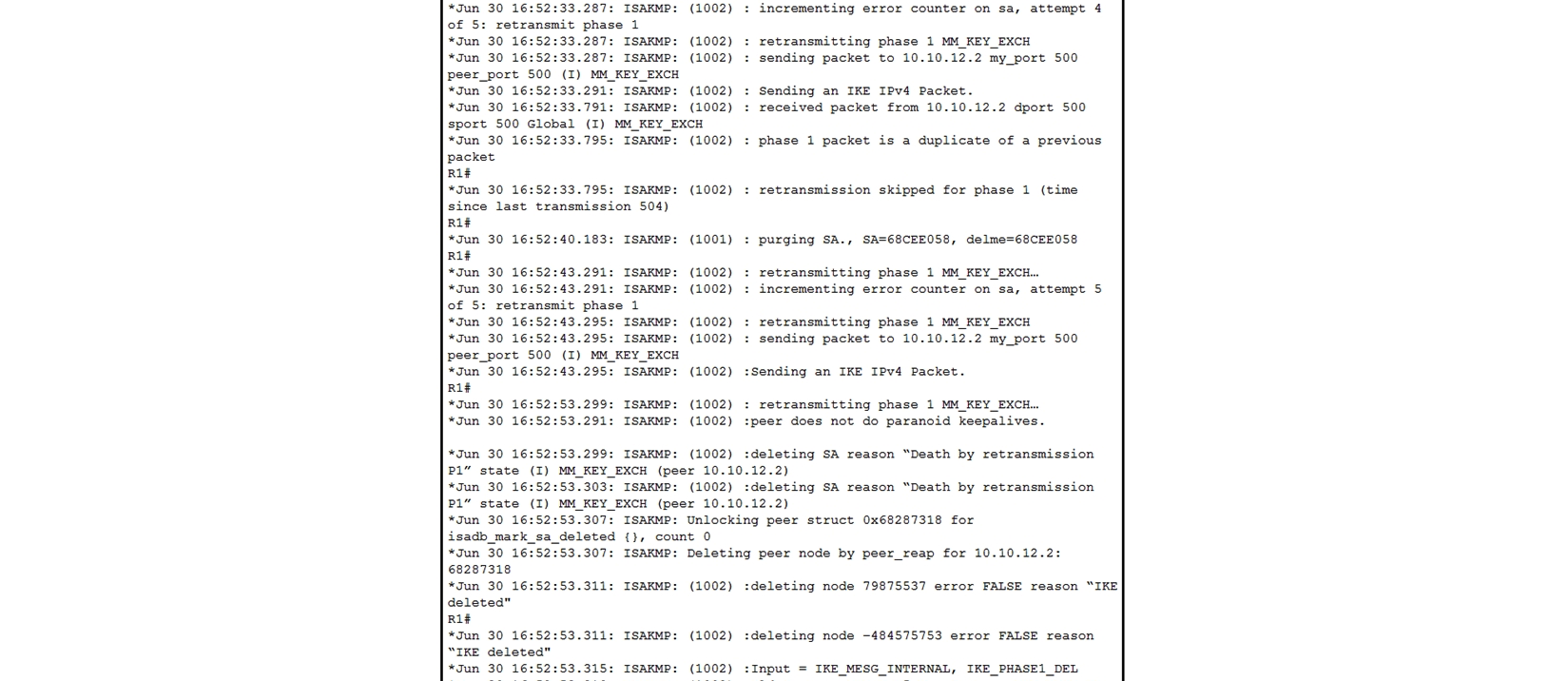 Refer to the exhibit. A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status. What is the problem according to this command output?
Refer to the exhibit. A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status. What is the problem according to this command output?A) interesting traffic was not applied
B) encryption algorithm mismatch
C) authentication key mismatch
D) hashing algorithm mismatch

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
52
What is a key difference between Cisco Firepower and Cisco ASA?
A) Cisco Firepower provides identity based access control while Cisco ASA does not.
B) Cisco AS provides access control while Cisco Firepower does not.
C) Cisco ASA provides SSL inspection while Cisco Firepower does not.
D) Cisco Firepower natively provides intrusion prevention capabilities while Cisco ASA does not.
A) Cisco Firepower provides identity based access control while Cisco ASA does not.
B) Cisco AS provides access control while Cisco Firepower does not.
C) Cisco ASA provides SSL inspection while Cisco Firepower does not.
D) Cisco Firepower natively provides intrusion prevention capabilities while Cisco ASA does not.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
53
A Cisco FirePower administrator needs to configure a rule to allow a new application that has never been seen on the network. Which two actions should be selected to allow the traffic to pass without inspection? (Choose two.)
A) permit
B) allow
C) reset
D) trust
E) monitor
A) permit
B) allow
C) reset
D) trust
E) monitor

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
54
The Cisco ASA must support TLS proxy for encrypted Cisco Unified Communications traffic. Where must the ASA be added on the Cisco UC Manager platform?
A) Certificate Trust List
B) Endpoint Trust List
C) Enterprise Proxy Service
D) Secured Collaboration Proxy
A) Certificate Trust List
B) Endpoint Trust List
C) Enterprise Proxy Service
D) Secured Collaboration Proxy

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
55
Which two application layer preprocessors are used by Firepower Next Generation Intrusion Prevention System? (Choose two.)
A) SIP
B) inline normalization
C) SSL
D) packet decoder
E) modbus
A) SIP
B) inline normalization
C) SSL
D) packet decoder
E) modbus

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
56
What does the Cloudlock Apps Firewall do to mitigate security concerns from an application perspective?
A) It allows the administrator to quarantine malicious files so that the application can function, just not maliciously.
B) It discovers and controls cloud apps that are connected to a company's corporate environment.
C) It deletes any application that does not belong in the network.
D) It sends the application information to an administrator to act on.
A) It allows the administrator to quarantine malicious files so that the application can function, just not maliciously.
B) It discovers and controls cloud apps that are connected to a company's corporate environment.
C) It deletes any application that does not belong in the network.
D) It sends the application information to an administrator to act on.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
57
What is a feature of Cisco NetFlow Secure Event Logging for Cisco ASAs?
A) Multiple NetFlow collectors are supported.
B) Advanced NetFlow v9 templates and legacy v5 formatting are supported.
C) Secure NetFlow connectors are optimized for Cisco Prime Infrastructure
D) Flow-create events are delayed.
A) Multiple NetFlow collectors are supported.
B) Advanced NetFlow v9 templates and legacy v5 formatting are supported.
C) Secure NetFlow connectors are optimized for Cisco Prime Infrastructure
D) Flow-create events are delayed.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
58
Which product allows Cisco FMC to push security intelligence observable to its sensors from other products?
A) Threat Intelligence Director
B) Encrypted Traffic Analytics.
C) Cognitive Threat Analytics.
D) Cisco Talos Intelligence
A) Threat Intelligence Director
B) Encrypted Traffic Analytics.
C) Cognitive Threat Analytics.
D) Cisco Talos Intelligence

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
59
What is a characteristic of a bridge group in ASA Firewall transparent mode?
A) It has an IP address on its BVI interface and is used for management traffic.
B) It allows ARP traffic with a single access rule.
C) It includes multiple interfaces and access rules between interfaces are customizable.
D) It is a Layer 3 segment and includes one port and customizable access rules.
A) It has an IP address on its BVI interface and is used for management traffic.
B) It allows ARP traffic with a single access rule.
C) It includes multiple interfaces and access rules between interfaces are customizable.
D) It is a Layer 3 segment and includes one port and customizable access rules.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
60
Which technology reduces data loss by identifying sensitive information stored in public computing environments?
A) Cisco SDA
B) Cisco Firepower
C) Cisco HyperFlex
D) Cisco Cloudlock
A) Cisco SDA
B) Cisco Firepower
C) Cisco HyperFlex
D) Cisco Cloudlock

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
61
Which feature is supported when deploying Cisco ASAv within AWS public cloud?
A) multiple context mode
B) user deployment of Layer 3 networks
C) IPv6
D) clustering
A) multiple context mode
B) user deployment of Layer 3 networks
C) IPv6
D) clustering

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
62
What are the two types of managed Intercloud Fabric deployment models? (Choose two.)
A) Service Provider managed
B) User managed
C) Public managed
D) Hybrid managed
E) Enterprise managed
A) Service Provider managed
B) User managed
C) Public managed
D) Hybrid managed
E) Enterprise managed

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
63
Which API is used for Content Security?
A) NX-OS API
B) IOS XR API
C) OpenVuln API
D) AsyncOS API
A) NX-OS API
B) IOS XR API
C) OpenVuln API
D) AsyncOS API

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
64
In a PaaS model, which layer is the tenant responsible for maintaining and patching?
A) hypervisor
B) virtual machine
C) network
D) application
A) hypervisor
B) virtual machine
C) network
D) application

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
65
An organization is receiving SPAM emails from a known malicious domain. What must be configured in order to prevent the session during the initial TCP communication?
A) Configure the Cisco ESA to reset the TCP connection.
B) Configure policies to stop and reject communication.
C) Configure the Cisco ESA to drop the malicious emails.
D) Configure policies to quarantine malicious emails.
A) Configure the Cisco ESA to reset the TCP connection.
B) Configure policies to stop and reject communication.
C) Configure the Cisco ESA to drop the malicious emails.
D) Configure policies to quarantine malicious emails.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
66
Which Cisco solution does Cisco Umbrella integrate with to determine if a URL is malicious?
A) AMP
B) AnyConnect
C) DynDNS
D) Talos
A) AMP
B) AnyConnect
C) DynDNS
D) Talos

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
67
What is the function of Cisco Cloudlock for data security?
A) data loss prevention
B) controls malicious cloud apps
C) detects anomalies
D) user and entity behavior analytics
A) data loss prevention
B) controls malicious cloud apps
C) detects anomalies
D) user and entity behavior analytics

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
68
How does Cisco Umbrella archive logs to an enterprise-owned storage?
A) by using the Application Programming Interface to fetch the logs
B) by sending logs via syslog to an on-premises or cloud-based syslog server
C) by the system administrator downloading the logs from the Cisco Umbrella web portal
D) by being configured to send logs to a self-managed AWS S3 bucket
A) by using the Application Programming Interface to fetch the logs
B) by sending logs via syslog to an on-premises or cloud-based syslog server
C) by the system administrator downloading the logs from the Cisco Umbrella web portal
D) by being configured to send logs to a self-managed AWS S3 bucket

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
69
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway?
A) Enable IP Layer enforcement.
B) Activate the Advanced Malware Protection license
C) Activate SSL decryption.
D) Enable Intelligent Proxy.
A) Enable IP Layer enforcement.
B) Activate the Advanced Malware Protection license
C) Activate SSL decryption.
D) Enable Intelligent Proxy.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
70
Which two aspects of the cloud PaaS model are managed by the customer but not the provider? (Choose two.)
A) middleware
B) applications
C) virtualization
D) operating systems
E) data
A) middleware
B) applications
C) virtualization
D) operating systems
E) data

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
71
In which cloud services model is the tenant responsible for virtual machine OS patching?
A) IaaS
B) UCaaS
C) PaaS
D) SaaS
A) IaaS
B) UCaaS
C) PaaS
D) SaaS

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
72
When web policies are configured in Cisco Umbrella, what provides the ability to ensure that domains are blocked when they host malware, command and control, phishing, and more threats?
A) Application Control
B) Security Category Blocking
C) Content Category Blocking
D) File Analysis
A) Application Control
B) Security Category Blocking
C) Content Category Blocking
D) File Analysis

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
73
Which feature within Cisco Umbrella allows for the ability to inspect secure HTTP traffic?
A) File Analysis
B) SafeSearch
C) SSL Decryption
D) Destination Lists
A) File Analysis
B) SafeSearch
C) SSL Decryption
D) Destination Lists

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
74
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two.)
A) DDoS
B) antispam
C) antivirus
D) encryption
E) DLP
A) DDoS
B) antispam
C) antivirus
D) encryption
E) DLP

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
75
Which Talos reputation center allows you to track the reputation of IP addresses for email and web traffic?
A) IP Blacklist Center
B) File Reputation Center
C) AMP Reputation Center
D) IP and Domain Reputation Center
A) IP Blacklist Center
B) File Reputation Center
C) AMP Reputation Center
D) IP and Domain Reputation Center

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
76
An engineer configured a new network identity in Cisco Umbrella but must verify that traffic is being routed through the Cisco Umbrella network. Which action tests the routing?
A) Ensure that the client computers are pointing to the on-premises DNS servers.
B) Enable the Intelligent Proxy to validate that traffic is being routed correctly.
C) Add the public IP address that the client computers are behind to a Core Identity.
D) Browse to http://welcome.umbrella.com/ to validate that the new identity is working.
A) Ensure that the client computers are pointing to the on-premises DNS servers.
B) Enable the Intelligent Proxy to validate that traffic is being routed correctly.
C) Add the public IP address that the client computers are behind to a Core Identity.
D) Browse to http://welcome.umbrella.com/ to validate that the new identity is working.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
77
What is an attribute of the DevSecOps process?
A) security scanning and theoretical vulnerabilities
B) development security
C) isolated security team
D) mandated security controls and check lists
A) security scanning and theoretical vulnerabilities
B) development security
C) isolated security team
D) mandated security controls and check lists

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
78
An organization is implementing URL blocking using Cisco Umbrella. The users are able to go to some sites but other sites are not accessible due to an error. Why is the error occurring?
A) Client computers do not have an SSL certificate deployed from an internal CA server.
B) Client computers do not have the Cisco Umbrella Root CA certificate installed.
C) IP-Layer Enforcement is not configured.
D) Intelligent proxy and SSL decryption is disabled in the policy.
A) Client computers do not have an SSL certificate deployed from an internal CA server.
B) Client computers do not have the Cisco Umbrella Root CA certificate installed.
C) IP-Layer Enforcement is not configured.
D) Intelligent proxy and SSL decryption is disabled in the policy.

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
79
Which cloud service model offers an environment for cloud consumers to develop and deploy applications without needing to manage or maintain the underlying cloud infrastructure?
A) PaaS
B) XaaS
C) IaaS
D) SaaS
A) PaaS
B) XaaS
C) IaaS
D) SaaS

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck
80
Where are individual sites specified to be blacklisted in Cisco Umbrella?
A) application settings
B) content categories
C) security settings
D) destination lists
A) application settings
B) content categories
C) security settings
D) destination lists

Unlock Deck
Unlock for access to all 213 flashcards in this deck.
Unlock Deck
k this deck



