Deck 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/33
Play
Full screen (f)
Deck 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)
1
A DevOps engineer has built a container to host a web-server and it must run as an executable. Which command must be configured in a Dockerfile to accomplish this goal?
A) ENTRYPOINT
B) ENTRYPOINT ["/usr/sbin/apache2ctl", "-D", "FOREGROUND"]
C) ENTRYPOINT ["BACKGROUND", "-D", "/usr/sbin/apache2ctl"]
D) ENTRYPOINT {usr/sbin/apache2ctl}
A) ENTRYPOINT
B) ENTRYPOINT ["/usr/sbin/apache2ctl", "-D", "FOREGROUND"]
C) ENTRYPOINT ["BACKGROUND", "-D", "/usr/sbin/apache2ctl"]
D) ENTRYPOINT {usr/sbin/apache2ctl}
ENTRYPOINT ["/usr/sbin/apache2ctl", "-D", "FOREGROUND"]
2
Which two characteristics of a build tool that is used in an automated build pipeline? (Choose two.)
A) It runs unit tests against code that is committed.
B) It builds your software on the production environment.
C) It builds your software when changes are committed.
D) It builds your software every 500 milliseconds.
E) It must have a plug-in for Puppet and Maven.
A) It runs unit tests against code that is committed.
B) It builds your software on the production environment.
C) It builds your software when changes are committed.
D) It builds your software every 500 milliseconds.
E) It must have a plug-in for Puppet and Maven.
It runs unit tests against code that is committed.
It builds your software when changes are committed.
It builds your software when changes are committed.
3
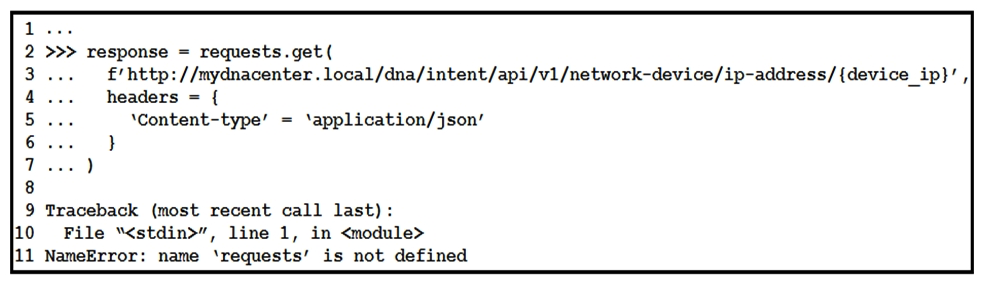 Refer to the exhibit. What is causing the requests code to fail?
Refer to the exhibit. What is causing the requests code to fail?A) Rython3 is not compatible with requests.
B) The requests library is not imported.
C) The requests library is not installed.
D) The requests coming into stdin fail because device_ip cannot be parsed.
The requests library is not imported.
4
A DevOps engineer has built a new container and must open port 8080 for intercontainer communication. Which command must be added in a Dockerfile to accomplish this goal?
A) EXPOSE 8080
B) FIREWALL ADD-PORT 8080
C) PORT 8080
D) OPEN PORT 8080
A) EXPOSE 8080
B) FIREWALL ADD-PORT 8080
C) PORT 8080
D) OPEN PORT 8080

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
5
A new version of an application is being released by creating a separate instance of the application that is running the new code. Only a small portion of the user base will be directed to the new instance until that version has been proven stable. Which deployment strategy is this example of?
A) recreate
B) blue/green
C) rolling
D) canary
A) recreate
B) blue/green
C) rolling
D) canary

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
6
![<strong> Refer to the exhibit. The exhibit shows the output of an Ansible task that prints the contents of the show_ip_int_brief variable that was registered in a different task in the playbook. Which expression is used to print the output of the command without its header row?</strong> A) show_ip_int_brief['stdout_lines'][0] B) show_ip_int_brief['stdout_lines'][1:] C) show_ip_int_brief['stdout_lines'][0][1:] D) show_ip_int_brief['stdout_lines']](https://d2lvgg3v3hfg70.cloudfront.net/C1178/11ec5360_db1b_2e27_8515_5b952b684e00_C1178_00.jpg) Refer to the exhibit. The exhibit shows the output of an Ansible task that prints the contents of the show_ip_int_brief variable that was registered in a different task in the playbook. Which expression is used to print the output of the command without its header row?
Refer to the exhibit. The exhibit shows the output of an Ansible task that prints the contents of the show_ip_int_brief variable that was registered in a different task in the playbook. Which expression is used to print the output of the command without its header row?A) show_ip_int_brief['stdout_lines'][0]
B) show_ip_int_brief['stdout_lines'][1:]
C) show_ip_int_brief['stdout_lines'][0][1:]
D) show_ip_int_brief['stdout_lines']

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
7
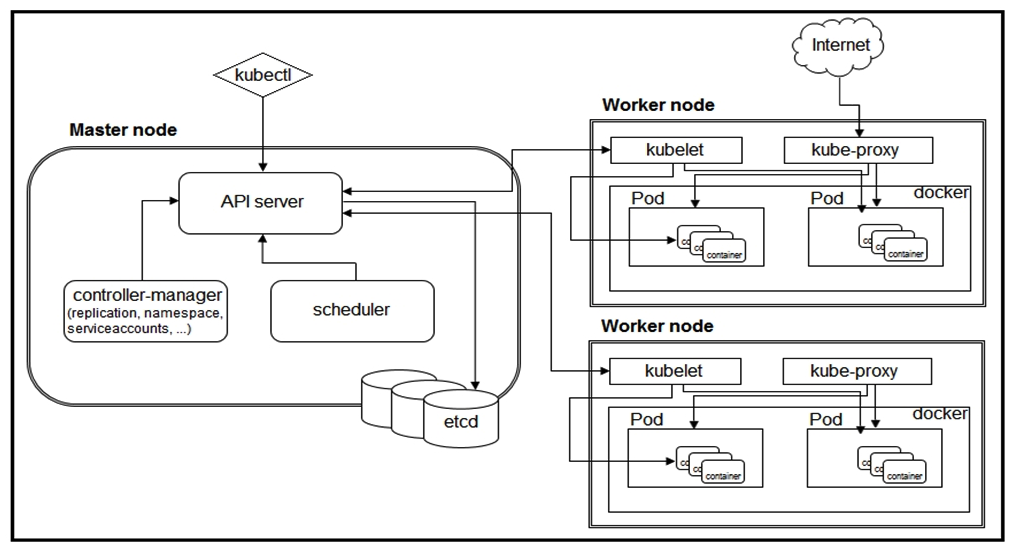 Refer to the exhibit. A developer needs to scale the existing pods within the worked nodes. Which object should be edited to achieve this goal?
Refer to the exhibit. A developer needs to scale the existing pods within the worked nodes. Which object should be edited to achieve this goal?A) ReplicaSet
B) PriorityClass
C) Deployment
D) Pod

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
8
A DevOps engineering wants to build an application implementation based on the CI/CD pipeline model. Which service should be used to provide hosted continuous service for open and private projects?
A) Ansible
B) pyATS
C) Genie CLI
D) Travis CI
A) Ansible
B) pyATS
C) Genie CLI
D) Travis CI

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
9
When static routes are added to a router in a network using a CI/CD pipeline, an Ansible playbook is used to make these changes. Which steps must be added to the pipeline to validate that the changes have the intended effect on the traffic flow?
A) Add a step to run the debug ip routing command before the change, and add a step after the change to issue the no debug ip routing command. Add a step to run the debug ip routing command before the change, and add a step after the change to issue the no debug ip routing command.
B) Add a step to capture the routing table before the change, and add a step after the change to capture it again. Calculate the difference between the two for review.
C) Add a step to ping a host on each of the static routes before the change, and a step after to repeat the same check. Calculate the difference between the two checks for review.
D) Add a step to run the same playbook again with the debug option enabled and use grep on the log output to ensure that the commands are not applied again. Add a step to run the same playbook again with the debug option enabled and use grep on the log output to ensure that the commands are not applied again.
A) Add a step to run the debug ip routing command before the change, and add a step after the change to issue the no debug ip routing command. Add a step to run the debug ip routing command before the change, and add a step after the change to issue the no debug ip routing command.
B) Add a step to capture the routing table before the change, and add a step after the change to capture it again. Calculate the difference between the two for review.
C) Add a step to ping a host on each of the static routes before the change, and a step after to repeat the same check. Calculate the difference between the two checks for review.
D) Add a step to run the same playbook again with the debug option enabled and use grep on the log output to ensure that the commands are not applied again. Add a step to run the same playbook again with the debug option enabled and use grep on the log output to ensure that the commands are not applied again.

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
10
Which Kubernetes object is used to create a ClusterIP or NodePort?
A) service
B) pod
C) deployment
D) loadbalancer
A) service
B) pod
C) deployment
D) loadbalancer

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
11
A CI/CD pipeline that builds infrastructure components using Terraform must be designed. A step in the pipeline is needed that checks for errors in any of the .tf files in the working directory. It also checks the existing state of the defined infrastructure. Which command does the pipeline run to accomplish this goal?
A) terraform plan
B) terraform check
C) terraform fmt
D) terraform validate
A) terraform plan
B) terraform check
C) terraform fmt
D) terraform validate

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
12
Which description of a canary deployment is true?
A) deployment by accident
B) deployment that is rolled back automatically after a configurable amount of minutes
C) deployment relating to data mining development
D) deployment to a limited set of servers or users
A) deployment by accident
B) deployment that is rolled back automatically after a configurable amount of minutes
C) deployment relating to data mining development
D) deployment to a limited set of servers or users

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
13
A DevOps engineer is supporting a containerized application with multiple components running across the Kubernetes cluster. Metrics from the container (CPU and memory) and application (requests per second and heap size) are being collected by Prometheus and displayed with Grafana. Users report transaction timeout problems with the application, but the metric graphs all look within normal levels. Which type of failure would prevent the engineer from seeing the problem using the captured metrics?
A) Grafana has lost connectivity to Prometheus, which causes graphs to display only the cached data.
B) CPU and memory metrics from Kubernetes nodes are not accurate due to the way that containers share resources.
C) Some containers are crashing regularly and being restarted automatically by Kubernetes.
D) The metricbeat agent has crashed and is no longer sending new data to Prometheus, so the metrics are not updating.
A) Grafana has lost connectivity to Prometheus, which causes graphs to display only the cached data.
B) CPU and memory metrics from Kubernetes nodes are not accurate due to the way that containers share resources.
C) Some containers are crashing regularly and being restarted automatically by Kubernetes.
D) The metricbeat agent has crashed and is no longer sending new data to Prometheus, so the metrics are not updating.

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
14
What is the effective way to manage computing costs in a public cloud?
A) Monitor data transfers to minimize cost.
B) Use dedicated hardware for all instances.
C) Select the largest instance option available in order to pay for only one instance.
D) Make use of elastic services and scale on demand.
A) Monitor data transfers to minimize cost.
B) Use dedicated hardware for all instances.
C) Select the largest instance option available in order to pay for only one instance.
D) Make use of elastic services and scale on demand.

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
15
A company has experienced serious growth and the hosted applications are getting more and more hits. Based on the increased work load, applications have started to show signs of reduced performance, which is affecting the user experience. Which two server metrics should be tracked to ensure that the customer experience remains within acceptable limits? (Choose two.)
A) application feature sprawl
B) CPU peak usage
C) CPU average usage
D) microservices count
E) CPU frequency
A) application feature sprawl
B) CPU peak usage
C) CPU average usage
D) microservices count
E) CPU frequency

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
16
Which type of testing should be integrated into a CI/CD pipeline to ensure the correct behavior of all of the modules in the source code that were developed using TDD?
A) soak testing
B) unit testing
C) load testing
D) volume testing
A) soak testing
B) unit testing
C) load testing
D) volume testing

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
17
A DevOps engineer must validate the working state of the network before implementing a CI/CD pipeline model. Which configuration management tool is designed to accomplish this?
A) Jenkins
B) Genie CLI
C) Travis CI
D) Python YAML data libraries
A) Jenkins
B) Genie CLI
C) Travis CI
D) Python YAML data libraries

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
18
A user wants to deploy a new service to a Kubernetes cluster. Which two commands accomplish this goal? (Choose two.)
A) Apply
B) Install
C) Deploy
D) Create
E) Expose
A) Apply
B) Install
C) Deploy
D) Create
E) Expose

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
19
Which two actions help limit the attack surface of your Docker container? (Choose two.)
A) Run only a single service in each container.
B) Run all services in a single image.
C) Use version tags for base images and dependencies.
D) Use Kali Linux as a base image.
E) Download images over HTTPS supporting sites.
A) Run only a single service in each container.
B) Run all services in a single image.
C) Use version tags for base images and dependencies.
D) Use Kali Linux as a base image.
E) Download images over HTTPS supporting sites.

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
20
What is the purpose of using a build tool in software development?
A) It complies source code into binaries and executables.
B) It provides a way to edit source code using a graphical interface.
C) It is a manual process that is followed to build software.
D) It tracks bugs and incidents in a built application.
A) It complies source code into binaries and executables.
B) It provides a way to edit source code using a graphical interface.
C) It is a manual process that is followed to build software.
D) It tracks bugs and incidents in a built application.

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
21
Which interface is most commonly used to integrate logging, monitoring, and alerting applications into your CI/CD pipeline?
A) AMQP
B) SNMP
C) SSH
D) REST
A) AMQP
B) SNMP
C) SSH
D) REST

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
22
The E-commerce application is being monitored using AppDynamics. AppDynamics has noticed that the application response has degraded and has identified some thread contention that might be the cause of the delays. Where in the interface does AppDynamics bring this to your attention?
A) Potential Issues section of an individual transaction
B) Transaction Score graph of a business transaction
C) Code Deadlock section of the Event List
D) Slow Calls and Errors tab of the application
A) Potential Issues section of an individual transaction
B) Transaction Score graph of a business transaction
C) Code Deadlock section of the Event List
D) Slow Calls and Errors tab of the application

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
23
An end user is seeing long web page load times on the internal business application that they are trying to view. The user is seeing this issue across multiple web browsers, and other users encounter the same issue. Which action should the system administrator take to start looking for the cause of this issue?
A) Check to make sure Nginx is running.
B) Check for response times in Nginx logs.
C) Check to make sure the web API response is coming back in JSON.
D) Check the size of the database that the application is using.
A) Check to make sure Nginx is running.
B) Check for response times in Nginx logs.
C) Check to make sure the web API response is coming back in JSON.
D) Check the size of the database that the application is using.

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
24
A developer is nearing the end of a software development cycle and is ready to deploy the software. The customer wants to continue using a secure software development lifecycle methodology and must plan for postproduction components. Which two areas should be the developer address? (Choose two.)
A) performing code reviews
B) requirement gathering
C) change management process
D) new code scanning
E) rollback plans
A) performing code reviews
B) requirement gathering
C) change management process
D) new code scanning
E) rollback plans

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
25
Which two elements help to secure your API keys? (Choose two.)
A) ramdomness
B) SHA1
C) triple AES
D) rotation
E) dictionary
A) ramdomness
B) SHA1
C) triple AES
D) rotation
E) dictionary

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
26
What are two advantages of using Configuration Management Tools? (Choose two.)
A) reduction in policy violations caused by human errors
B) reduction in administration costs
C) reduction in network changes already performed automatically
D) reduction of on-premises networking equipment
E) reduction in networking team skills
A) reduction in policy violations caused by human errors
B) reduction in administration costs
C) reduction in network changes already performed automatically
D) reduction of on-premises networking equipment
E) reduction in networking team skills

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
27
What is chaos engineering?
A) designing an application with fuzzy logic that makes it hard to predict
B) a product engineering approach that lacks a formal methodology
C) splitting a project between teams that do not communicate with each other
D) introducing problems into a system to study behavior and improve reliability
A) designing an application with fuzzy logic that makes it hard to predict
B) a product engineering approach that lacks a formal methodology
C) splitting a project between teams that do not communicate with each other
D) introducing problems into a system to study behavior and improve reliability

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
28
How does eliminating hardcoded or default passwords help to secure an environment?
A) helps by enforcing your password in a repository and storing it in a secure vault
B) helps to manage passwords centrally
C) helps penetration testing team to focus on other issues more efficiently
D) helps by removing back doors in your environments
A) helps by enforcing your password in a repository and storing it in a secure vault
B) helps to manage passwords centrally
C) helps penetration testing team to focus on other issues more efficiently
D) helps by removing back doors in your environments

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
29
Which type of security testing should be performed as a part of a CI/CD pipeline by analyzing the source code itself without compiling the code into a running executable?
A) Dynamic Application Security Testing
B) Runtime Application Health-Protection
C) Continuous Application Security Testing
D) Static Analysis Security Testing
A) Dynamic Application Security Testing
B) Runtime Application Health-Protection
C) Continuous Application Security Testing
D) Static Analysis Security Testing

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
30
AppDynamics is being used to monitor your distributed Python application. Each individual container of the application is instrumented with an AppD agent. Which two configuration variables uniquely determine the module being monitored? (Choose two.)
A) node
B) app
C) agent
D) tier
E) event
A) node
B) app
C) agent
D) tier
E) event

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
31
Which method is a safe way to provide a username/password combination to an application running as a service in a Docker container?
A) encode the value with base64 in a secure DNS CTEXT entry
B) as an environment variable in the Dockerfile
C) Docker environment variable
D) Docker secrets
A) encode the value with base64 in a secure DNS CTEXT entry
B) as an environment variable in the Dockerfile
C) Docker environment variable
D) Docker secrets

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
32
Which step must be taken to enable centralized logging in a Kubernetes environment?
A) No steps need to be taken. The master node automatically aggregates logs from all worker nodes and stores them on the specified persistent volume.
B) Create a CustomResourceDefinition in each deployment that specifies the IP or names the log collector.
C) Deploy a sidecar node that aggregates logs from the entire cluster.
D) Create a DaemonSet that deploys a container with a logging agent on every node in the cluster.
A) No steps need to be taken. The master node automatically aggregates logs from all worker nodes and stores them on the specified persistent volume.
B) Create a CustomResourceDefinition in each deployment that specifies the IP or names the log collector.
C) Deploy a sidecar node that aggregates logs from the entire cluster.
D) Create a DaemonSet that deploys a container with a logging agent on every node in the cluster.

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck
33
A developer wants to deploy a highly available web server cluster and decides to put a load balancer in front of multiple clustered nodes that run the same web service. The goal is for the load balancer to take in users and distribute the load across the whole cluster. What kind of high-availability configuration is the developer running?
A) active
B) passive
C) active-passive
D) active-active
A) active
B) passive
C) active-passive
D) active-active

Unlock Deck
Unlock for access to all 33 flashcards in this deck.
Unlock Deck
k this deck



