Deck 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/106
Play
Full screen (f)
Deck 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)
1
An organization is using a PKI management server and a SOAR platform to manage the certificate lifecycle. The SOAR platform queries a certificate management tool to check all endpoints for SSL certificates that have either expired or are nearing expiration. Engineers are struggling to manage problematic certificates outside of PKI management since deploying certificates and tracking them requires searching server owners manually. Which action will improve workflow automation?
A) Implement a new workflow within SOAR to create tickets in the incident response system, assign problematic certificate update requests to server owners, and register change requests.
B) Integrate a PKI solution within SOAR to create certificates within the SOAR engines to track, update, and monitor problematic certificates.
C) Implement a new workflow for SOAR to fetch a report of assets that are outside of the PKI zone, sort assets by certification management leads and automate alerts that updates are needed.
D) Integrate a SOAR solution with Active Directory to pull server owner details from the AD and send an automated email for problematic certificates requesting updates.
A) Implement a new workflow within SOAR to create tickets in the incident response system, assign problematic certificate update requests to server owners, and register change requests.
B) Integrate a PKI solution within SOAR to create certificates within the SOAR engines to track, update, and monitor problematic certificates.
C) Implement a new workflow for SOAR to fetch a report of assets that are outside of the PKI zone, sort assets by certification management leads and automate alerts that updates are needed.
D) Integrate a SOAR solution with Active Directory to pull server owner details from the AD and send an automated email for problematic certificates requesting updates.
Implement a new workflow for SOAR to fetch a report of assets that are outside of the PKI zone, sort assets by certification management leads and automate alerts that updates are needed.
2
Which command does an engineer use to set read/write/execute access on a folder for everyone who reaches the resource?
A) chmod 666
B) chmod 774
C) chmod 775
D) chmod 777
A) chmod 666
B) chmod 774
C) chmod 775
D) chmod 777
chmod 777
3
An engineer received an alert of a zero-day vulnerability affecting desktop phones through which an attacker sends a crafted packet to a device, resets the credentials, makes the device unavailable, and allows a default administrator account login. Which step should an engineer take after receiving this alert?
A) Initiate a triage meeting to acknowledge the vulnerability and its potential impact
B) Determine company usage of the affected products
C) Search for a patch to install from the vendor
D) Implement restrictions within the VoIP VLANS
A) Initiate a triage meeting to acknowledge the vulnerability and its potential impact
B) Determine company usage of the affected products
C) Search for a patch to install from the vendor
D) Implement restrictions within the VoIP VLANS
Search for a patch to install from the vendor
4
Refer to the exhibit. A threat actor behind a single computer exploited a cloud-based application by sending multiple concurrent API requests. These requests made the application unresponsive. Which solution protects the application from being overloaded and ensures more equitable application access across the end-user community? 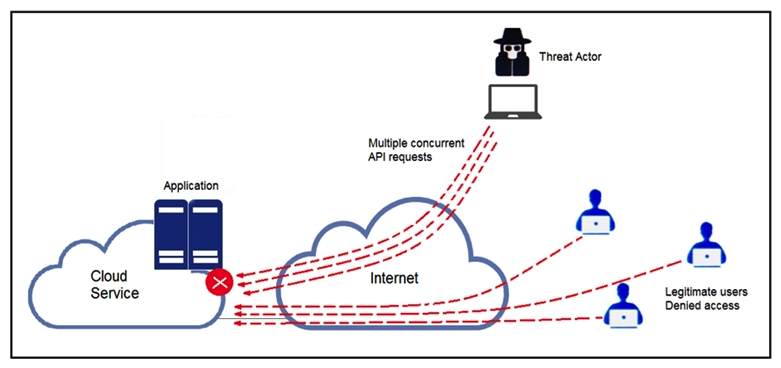
A) Limit the number of API calls that a single client is allowed to make
B) Add restrictions on the edge router on how often a single client can access the API
C) Reduce the amount of data that can be fetched from the total pool of active clients that call the API
D) Increase the application cache of the total pool of active clients that call the API

A) Limit the number of API calls that a single client is allowed to make
B) Add restrictions on the edge router on how often a single client can access the API
C) Reduce the amount of data that can be fetched from the total pool of active clients that call the API
D) Increase the application cache of the total pool of active clients that call the API

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
5
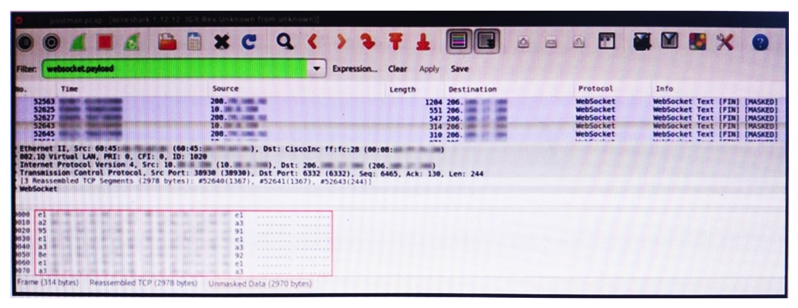 Refer to the exhibit. An engineer is analyzing this Vlan0392-int12-239.pcap file in Wireshark after detecting a suspicious network activity. The origin header for the direct IP connections in the packets was initiated by a google chrome extension on a WebSocket protocol. The engineer checked message payloads to determine what information was being sent off-site but the payloads are obfuscated and unreadable. What does this STIX indicate?
Refer to the exhibit. An engineer is analyzing this Vlan0392-int12-239.pcap file in Wireshark after detecting a suspicious network activity. The origin header for the direct IP connections in the packets was initiated by a google chrome extension on a WebSocket protocol. The engineer checked message payloads to determine what information was being sent off-site but the payloads are obfuscated and unreadable. What does this STIX indicate?A) The extension is not performing as intended because of restrictions since ports 80 and 443 should be accessible
B) The traffic is legitimate as the google chrome extension is reaching out to check for updates and fetches this information
C) There is a possible data leak because payloads should be encoded as UTF-8 text
D) There is a malware that is communicating via encrypted channels to the command and control server

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
6
A threat actor used a phishing email to deliver a file with an embedded macro. The file was opened, and a remote code execution attack occurred in a company's infrastructure. Which steps should an engineer take at the recovery stage?
A) Determine the systems involved and deploy available patches
B) Analyze event logs and restrict network access
C) Review access lists and require users to increase password complexity
D) Identify the attack vector and update the IDS signature list
A) Determine the systems involved and deploy available patches
B) Analyze event logs and restrict network access
C) Review access lists and require users to increase password complexity
D) Identify the attack vector and update the IDS signature list

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
7
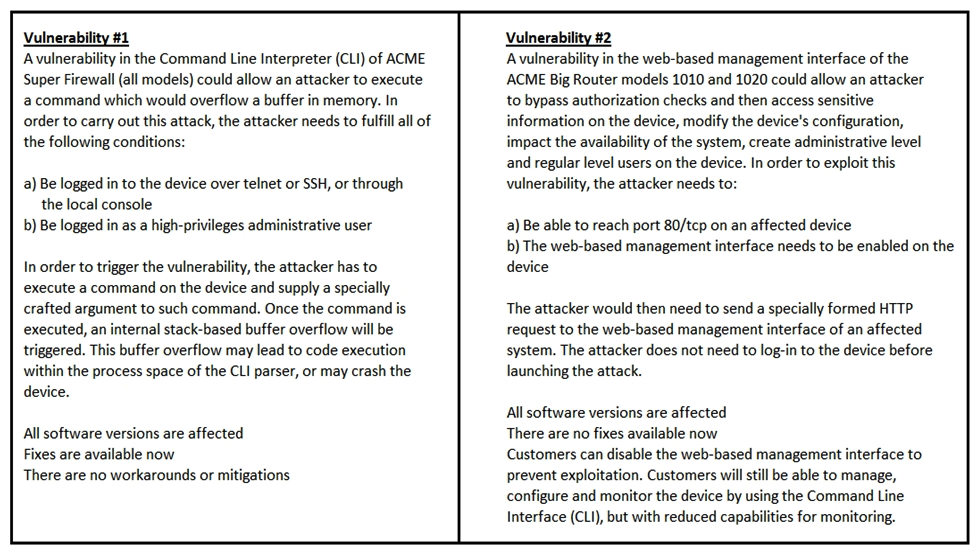 Refer to the exhibit. How must these advisories be prioritized for handling?
Refer to the exhibit. How must these advisories be prioritized for handling?A) The highest priority for handling depends on the type of institution deploying the devices
B) Vulnerability #2 is the highest priority for every type of institution
C) Vulnerability #1 and vulnerability #2 have the same priority
D) Vulnerability #1 is the highest priority for every type of institution

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
8
What do 2xx HTTP response codes indicate for REST APIs?
A) additional action must be taken by the client to complete the request
B) the server takes responsibility for error status codes
C) communication of transfer protocol-level information
D) successful acceptance of the client's request
A) additional action must be taken by the client to complete the request
B) the server takes responsibility for error status codes
C) communication of transfer protocol-level information
D) successful acceptance of the client's request

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
9
The incident response team was notified of detected malware. The team identified the infected hosts, removed the malware, restored the functionality and data of infected systems, and planned a company meeting to improve the incident handling capability. Which step was missed according to the NIST incident handling guide?
A) Contain the malware
B) Install IPS software
C) Determine the escalation path
D) Perform vulnerability assessment
A) Contain the malware
B) Install IPS software
C) Determine the escalation path
D) Perform vulnerability assessment

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
10
The physical security department received a report that an unauthorized person followed an authorized individual to enter a secured premise. The incident was documented and given to a security specialist to analyze. Which step should be taken at this stage?
A) Determine the assets to which the attacker has access
B) Identify assets the attacker handled or acquired
C) Change access controls to high risk assets in the enterprise
D) Identify movement of the attacker in the enterprise
A) Determine the assets to which the attacker has access
B) Identify assets the attacker handled or acquired
C) Change access controls to high risk assets in the enterprise
D) Identify movement of the attacker in the enterprise

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
11
A malware outbreak is detected by the SIEM and is confirmed as a true positive. The incident response team follows the playbook to mitigate the threat. What is the first action for the incident response team?
A) Assess the network for unexpected behavior
B) Isolate critical hosts from the network
C) Patch detected vulnerabilities from critical hosts
D) Perform analysis based on the established risk factors
A) Assess the network for unexpected behavior
B) Isolate critical hosts from the network
C) Patch detected vulnerabilities from critical hosts
D) Perform analysis based on the established risk factors

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
12
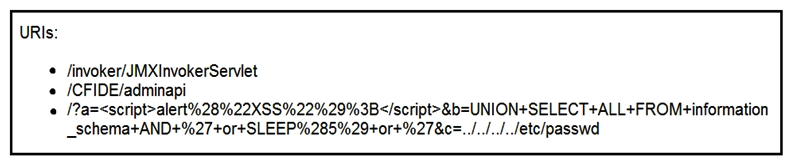 Refer to the exhibit. At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests from known malicious Internet scanners?
Refer to the exhibit. At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests from known malicious Internet scanners?A) exploitation
B) actions on objectives
C) delivery
D) reconnaissance

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
13
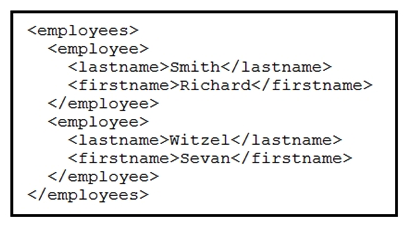 Refer to the exhibit. Which data format is being used?
Refer to the exhibit. Which data format is being used?A) JSON
B) HTML
C) XML
D) CSV

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
14
An organization had a breach due to a phishing attack. An engineer leads a team through the recovery phase of the incident response process. Which action should be taken during this phase?
A) Host a discovery meeting and define configuration and policy updates
B) Update the IDS/IPS signatures and reimage the affected hosts
C) Identify the systems that have been affected and tools used to detect the attack
D) Identify the traffic with data capture using Wireshark and review email filters
A) Host a discovery meeting and define configuration and policy updates
B) Update the IDS/IPS signatures and reimage the affected hosts
C) Identify the systems that have been affected and tools used to detect the attack
D) Identify the traffic with data capture using Wireshark and review email filters

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
15
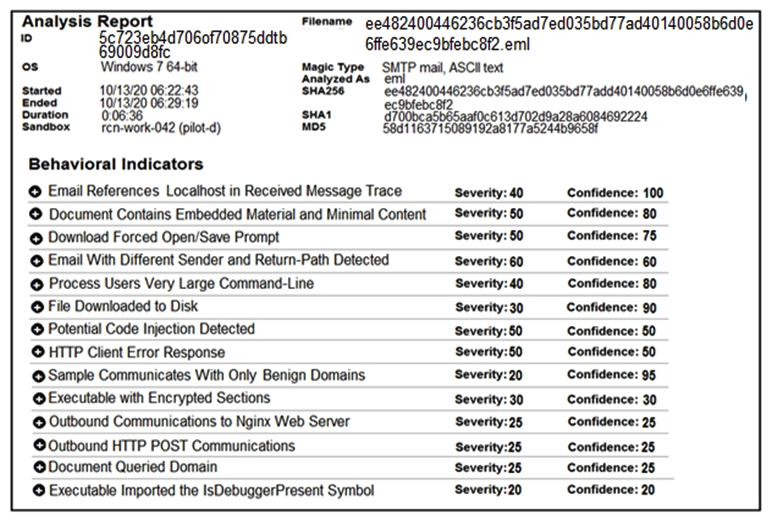 Refer to the exhibit. Cisco Advanced Malware Protection installed on an end-user desktop automatically submitted a low prevalence file to the Threat Grid analysis engine. What should be concluded from this report?
Refer to the exhibit. Cisco Advanced Malware Protection installed on an end-user desktop automatically submitted a low prevalence file to the Threat Grid analysis engine. What should be concluded from this report?A) Threat scores are high, malicious ransomware has been detected, and files have been modified
B) Threat scores are low, malicious ransomware has been detected, and files have been modified
C) Threat scores are high, malicious activity is detected, but files have not been modified
D) Threat scores are low and no malicious file activity is detected

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
16
A new malware variant is discovered hidden in pirated software that is distributed on the Internet. Executives have asked for an organizational risk assessment. The security officer is given a list of all assets. According to NIST, which two elements are missing to calculate the risk assessment? (Choose two.)
A) incident response playbooks
B) asset vulnerability assessment
C) report of staff members with asset relations
D) key assets and executives
E) malware analysis report
A) incident response playbooks
B) asset vulnerability assessment
C) report of staff members with asset relations
D) key assets and executives
E) malware analysis report

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
17
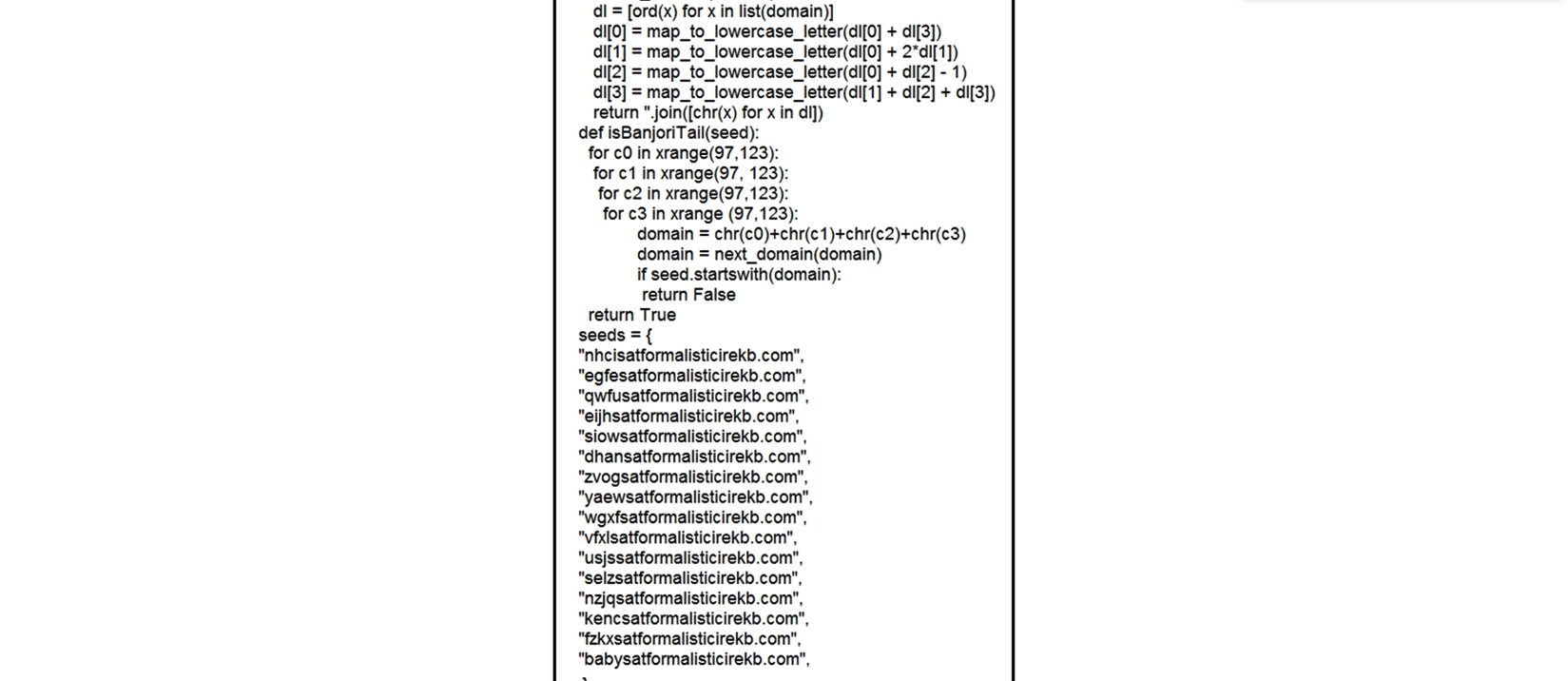 Refer to the exhibit. What results from this script?
Refer to the exhibit. What results from this script?A) Seeds for existing domains are checked
B) A search is conducted for additional seeds
C) Domains are compared to seed rules
D) A list of domains as seeds is blocked

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
18
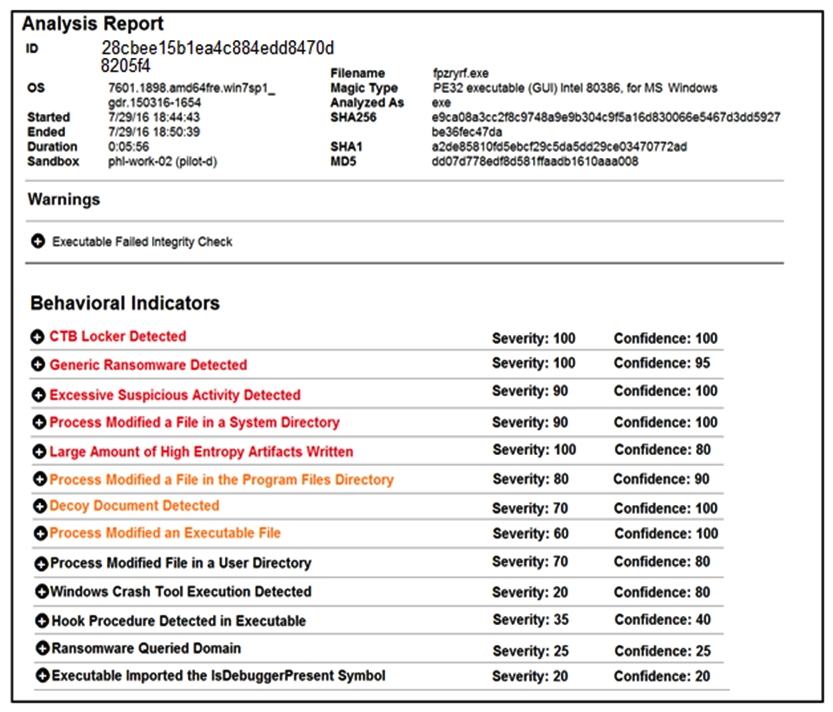 Refer to the exhibit. Cisco Advanced Malware Protection installed on an end-user desktop has automatically submitted a low prevalence file to the Threat Grid analysis engine for further analysis. What should be concluded from this report?
Refer to the exhibit. Cisco Advanced Malware Protection installed on an end-user desktop has automatically submitted a low prevalence file to the Threat Grid analysis engine for further analysis. What should be concluded from this report?A) The prioritized behavioral indicators of compromise do not justify the execution of the "ransomware" because the scores do not indicate the likelihood of malicious ransomware.
B) The prioritized behavioral indicators of compromise do not justify the execution of the "ransomware" because the scores are high and do not indicate the likelihood of malicious ransomware.
C) The prioritized behavioral indicators of compromise justify the execution of the "ransomware" because the scores are high and indicate the likelihood that malicious ransomware has been detected.
D) The prioritized behavioral indicators of compromise justify the execution of the "ransomware" because the scores are low and indicate the likelihood that malicious ransomware has been detected.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
19
According to GDPR, what should be done with data to ensure its confidentiality, integrity, and availability?
A) Perform a vulnerability assessment
B) Conduct a data protection impact assessment
C) Conduct penetration testing
D) Perform awareness testing
A) Perform a vulnerability assessment
B) Conduct a data protection impact assessment
C) Conduct penetration testing
D) Perform awareness testing

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
20
A payroll administrator noticed unexpected changes within a piece of software and reported the incident to the incident response team. Which actions should be taken at this step in the incident response workflow?
A) Classify the criticality of the information, research the attacker's motives, and identify missing patches
B) Determine the damage to the business, extract reports, and save evidence according to a chain of custody
C) Classify the attack vector, understand the scope of the event, and identify the vulnerabilities being exploited
D) Determine the attack surface, evaluate the risks involved, and communicate the incident according to the escalation plan
A) Classify the criticality of the information, research the attacker's motives, and identify missing patches
B) Determine the damage to the business, extract reports, and save evidence according to a chain of custody
C) Classify the attack vector, understand the scope of the event, and identify the vulnerabilities being exploited
D) Determine the attack surface, evaluate the risks involved, and communicate the incident according to the escalation plan

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
21
A company's web server availability was breached by a DDoS attack and was offline for 3 hours because it was not deemed a critical asset in the incident response playbook. Leadership has requested a risk assessment of the asset. An analyst conducted the risk assessment using the threat sources, events, and vulnerabilities. Which additional element is needed to calculate the risk?
A) assessment scope
B) event severity and likelihood
C) incident response playbook
D) risk model framework
A) assessment scope
B) event severity and likelihood
C) incident response playbook
D) risk model framework

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
22
A security expert is investigating a breach that resulted in a $32 million loss from customer accounts. Hackers were able to steal API keys and two-factor codes due to a vulnerability that was introduced in a new code a few weeks before the attack. Which step was missed that would have prevented this breach?
A) use of the Nmap tool to identify the vulnerability when the new code was deployed
B) implementation of a firewall and intrusion detection system
C) implementation of an endpoint protection system
D) use of SecDevOps to detect the vulnerability during development
A) use of the Nmap tool to identify the vulnerability when the new code was deployed
B) implementation of a firewall and intrusion detection system
C) implementation of an endpoint protection system
D) use of SecDevOps to detect the vulnerability during development

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
23
A security architect is working in a processing center and must implement a DLP solution to detect and prevent any type of copy and paste attempts of sensitive data within unapproved applications and removable devices. Which technical architecture must be used?
A) DLP for data in motion
B) DLP for removable data
C) DLP for data in use
D) DLP for data at rest
A) DLP for data in motion
B) DLP for removable data
C) DLP for data in use
D) DLP for data at rest

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
24
An employee abused PowerShell commands and script interpreters, which lead to an indicator of compromise (IOC) trigger. The IOC event shows that a known malicious file has been executed, and there is an increased likelihood of a breach. Which indicator generated this IOC event?
A) ExecutedMalware.ioc
B) Crossrider.ioc
C) ConnectToSuspiciousDomain.ioc
D) W32.AccesschkUtility.ioc
A) ExecutedMalware.ioc
B) Crossrider.ioc
C) ConnectToSuspiciousDomain.ioc
D) W32.AccesschkUtility.ioc

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
25
An engineer implemented a SOAR workflow to detect and respond to incorrect login attempts and anomalous user behavior. Since the implementation, the security team has received dozens of false positive alerts and negative feedback from system administrators and privileged users. Several legitimate users were tagged as a threat and their accounts blocked, or credentials reset because of unexpected login times and incorrectly typed credentials. How should the workflow be improved to resolve these issues?
A) Meet with privileged users to increase awareness and modify the rules for threat tags and anomalous behavior alerts
B) Change the SOAR configuration flow to remove the automatic remediation that is increasing the false positives and triggering threats
C) Add a confirmation step through which SOAR informs the affected user and asks them to confirm whether they made the attempts
D) Increase incorrect login tries and tune anomalous user behavior not to affect privileged accounts
A) Meet with privileged users to increase awareness and modify the rules for threat tags and anomalous behavior alerts
B) Change the SOAR configuration flow to remove the automatic remediation that is increasing the false positives and triggering threats
C) Add a confirmation step through which SOAR informs the affected user and asks them to confirm whether they made the attempts
D) Increase incorrect login tries and tune anomalous user behavior not to affect privileged accounts

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
26
How is a SIEM tool used?
A) To collect security data from authentication failures and cyber attacks and forward it for analysis
B) To search and compare security data against acceptance standards and generate reports for analysis
C) To compare security alerts against configured scenarios and trigger system responses
D) To collect and analyze security data from network devices and servers and produce alerts
A) To collect security data from authentication failures and cyber attacks and forward it for analysis
B) To search and compare security data against acceptance standards and generate reports for analysis
C) To compare security alerts against configured scenarios and trigger system responses
D) To collect and analyze security data from network devices and servers and produce alerts

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
27
What is the HTTP response code when the REST API information requested by the authenticated user cannot be found?
A) 401
B) 402
C) 403
D) 404
E) 405
A) 401
B) 402
C) 403
D) 404
E) 405

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
28
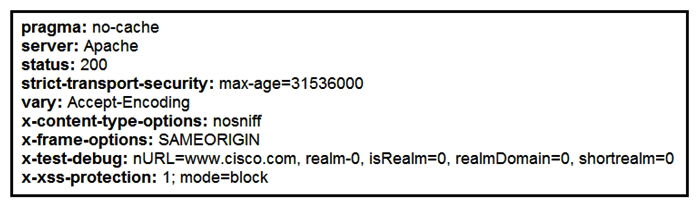 Refer to the exhibit. Where does it signify that a page will be stopped from loading when a scripting attack is detected?
Refer to the exhibit. Where does it signify that a page will be stopped from loading when a scripting attack is detected?A) x-frame-options
B) x-content-type-options
C) x-xss-protection
D) x-test-debug

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
29
A security analyst receives an escalation regarding an unidentified connection on the Accounting A1 server within a monitored zone. The analyst pulls the logs and discovers that a Powershell process and a WMI tool process were started on the server after the connection was established and that a PE format file was created in the system directory. What is the next step the analyst should take?
A) Isolate the server and perform forensic analysis of the file to determine the type and vector of a possible attack
B) Identify the server owner through the CMDB and contact the owner to determine if these were planned and identifiable activities
C) Review the server backup and identify server content and data criticality to assess the intrusion risk
D) Perform behavioral analysis of the processes on an isolated workstation and perform cleaning procedures if the file is malicious
A) Isolate the server and perform forensic analysis of the file to determine the type and vector of a possible attack
B) Identify the server owner through the CMDB and contact the owner to determine if these were planned and identifiable activities
C) Review the server backup and identify server content and data criticality to assess the intrusion risk
D) Perform behavioral analysis of the processes on an isolated workstation and perform cleaning procedures if the file is malicious

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
30
Refer to the exhibit. Which indicator of compromise is represented by this STIX? 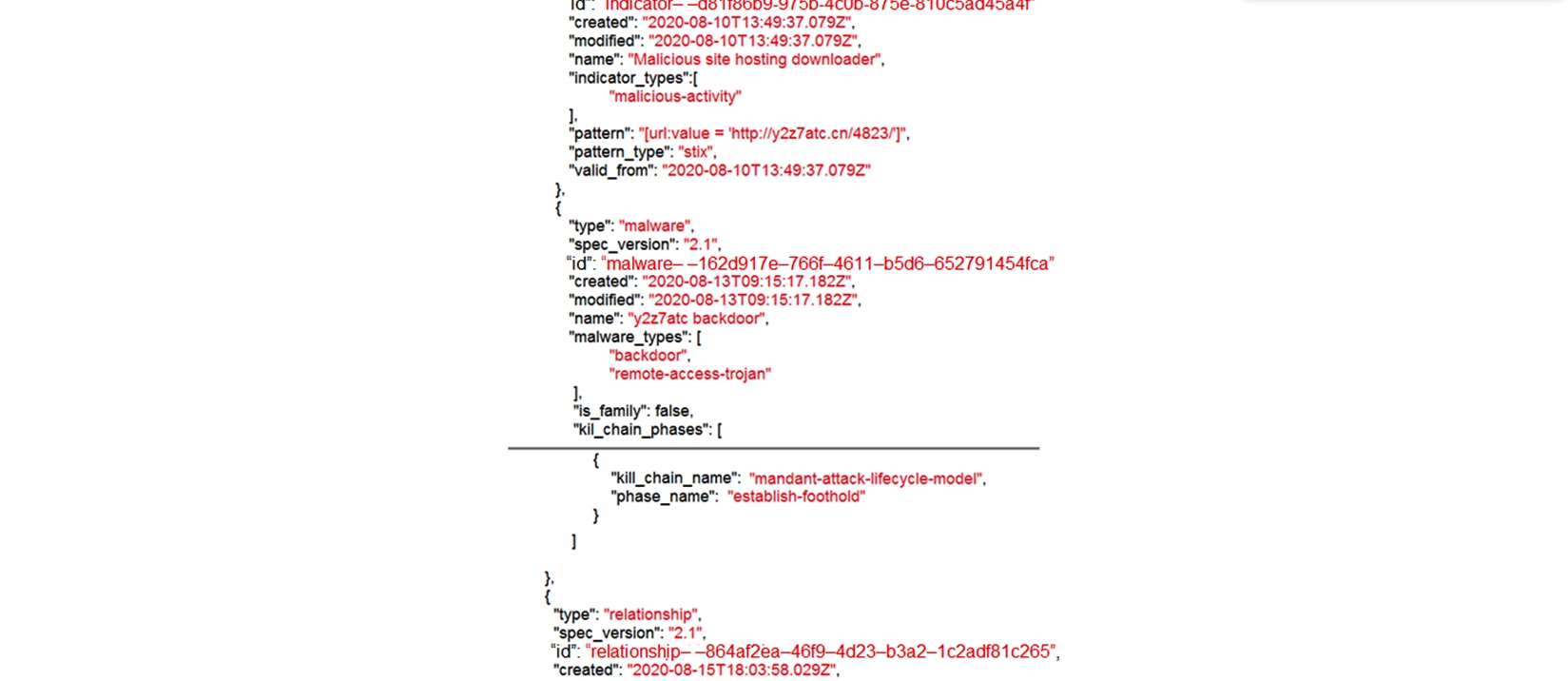
A) website redirecting traffic to ransomware server
B) website hosting malware to download files
C) web server vulnerability exploited by malware
D) cross-site scripting vulnerability to backdoor server

A) website redirecting traffic to ransomware server
B) website hosting malware to download files
C) web server vulnerability exploited by malware
D) cross-site scripting vulnerability to backdoor server

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
31
A customer is using a central device to manage network devices over SNMPv2. A remote attacker caused a denial of service condition and can trigger this vulnerability by issuing a GET request for the ciscoFlashMIB OID on an affected device. Which should be disabled to resolve the issue?
A) SNMPv2
B) TCP small services
C) port UDP 161 and 162
D) UDP small services
A) SNMPv2
B) TCP small services
C) port UDP 161 and 162
D) UDP small services

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
32
An engineer receives a report that indicates a possible incident of a malicious insider sending company information to outside parties. What is the first action the engineer must take to determine whether an incident has occurred?
A) Analyze environmental threats and causes
B) Inform the product security incident response team to investigate further
C) Analyze the precursors and indicators
D) Inform the computer security incident response team to investigate further
A) Analyze environmental threats and causes
B) Inform the product security incident response team to investigate further
C) Analyze the precursors and indicators
D) Inform the computer security incident response team to investigate further

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
33
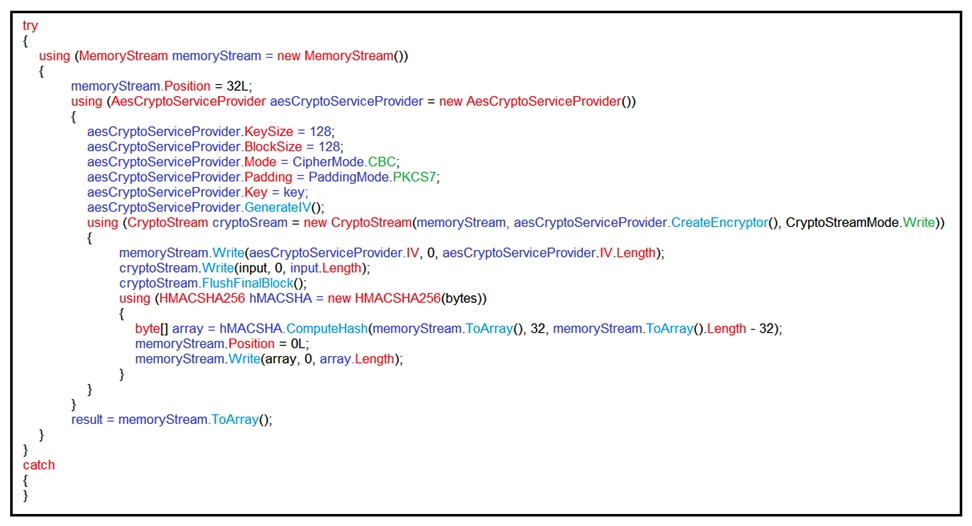 Refer to the exhibit. An engineer is performing a static analysis on a malware and knows that it is capturing keys and webcam events on a company server. What is the indicator of compromise?
Refer to the exhibit. An engineer is performing a static analysis on a malware and knows that it is capturing keys and webcam events on a company server. What is the indicator of compromise?A) The malware is performing comprehensive fingerprinting of the host, including a processor, motherboard manufacturer, and connected removable storage.
B) The malware is a ransomware querying for installed anti-virus products and operating systems to encrypt and render unreadable until payment is made for file decryption.
C) The malware has moved to harvesting cookies and stored account information from major browsers and configuring a reverse proxy for intercepting network activity.
D) The malware contains an encryption and decryption routine to hide URLs/IP addresses and is storing the output of loggers and webcam captures in locally encrypted files for retrieval.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
34
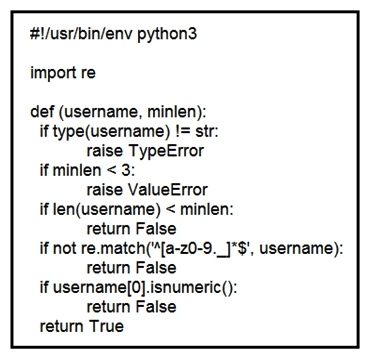 Refer to the exhibit. An organization is using an internal application for printing documents that requires a separate registration on the website. The application allows format-free user creation, and users must match these required conditions to comply with the company's user creation policy: minimum length: 3 usernames can only use letters, numbers, dots, and underscores usernames cannot begin with a number The application administrator has to manually change and track these daily to ensure compliance. An engineer is tasked to implement a script to automate the process according to the company user creation policy. The engineer implemented this piece of code within the application, but users are still able to create format-free usernames. Which change is needed to apply the restrictions?
Refer to the exhibit. An organization is using an internal application for printing documents that requires a separate registration on the website. The application allows format-free user creation, and users must match these required conditions to comply with the company's user creation policy: minimum length: 3 usernames can only use letters, numbers, dots, and underscores usernames cannot begin with a number The application administrator has to manually change and track these daily to ensure compliance. An engineer is tasked to implement a script to automate the process according to the company user creation policy. The engineer implemented this piece of code within the application, but users are still able to create format-free usernames. Which change is needed to apply the restrictions?A) modify code to return error on restrictions def return false_user(username, minlen)
B) automate the restrictions def automate_user(username, minlen)
C) validate the restrictions, def validate_user(username, minlen)
D) modify code to force the restrictions, def force_user(username, minlen)

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
35
An engineer receives an incident ticket with hundreds of intrusion alerts that require investigation. An analysis of the incident log shows that the alerts are from trusted IP addresses and internal devices. The final incident report stated that these alerts were false positives and that no intrusions were detected. What action should be taken to harden the network?
A) Move the IPS to after the firewall facing the internal network
B) Move the IPS to before the firewall facing the outside network
C) Configure the proxy service on the IPS
D) Configure reverse port forwarding on the IPS
A) Move the IPS to after the firewall facing the internal network
B) Move the IPS to before the firewall facing the outside network
C) Configure the proxy service on the IPS
D) Configure reverse port forwarding on the IPS

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
36
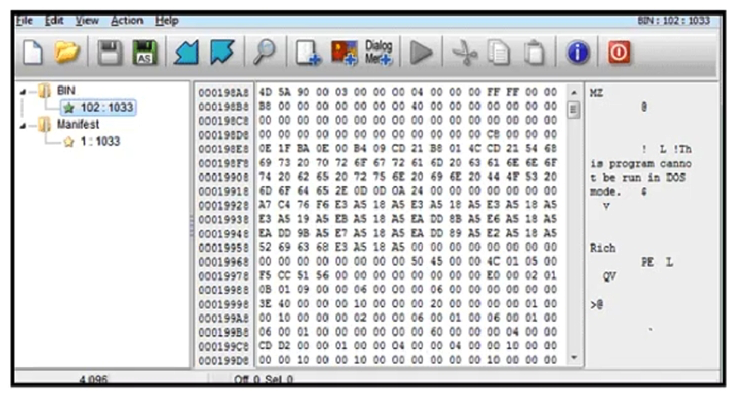 Refer to the exhibit. An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?
Refer to the exhibit. An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?A) a DOS MZ executable format
B) a MS-DOS executable archive
C) an archived malware
D) a Windows executable file

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
37
An API developer is improving an application code to prevent DDoS attacks. The solution needs to accommodate instances of a large number of API requests coming for legitimate purposes from trustworthy services. Which solution should be implemented?
A) Restrict the number of requests based on a calculation of daily averages. If the limit is exceeded, temporarily block access from the IP address and return a 402 HTTP error code.
B) Implement REST API Security Essentials solution to automatically mitigate limit exhaustion. If the limit is exceeded, temporarily block access from the service and return a 409 HTTP error code.
C) Increase a limit of replies in a given interval for each API. If the limit is exceeded, block access from the API key permanently and return a 450 HTTP error code.
D) Apply a limit to the number of requests in a given time interval for each API. If the rate is exceeded, block access from the API key temporarily and return a 429 HTTP error code.
A) Restrict the number of requests based on a calculation of daily averages. If the limit is exceeded, temporarily block access from the IP address and return a 402 HTTP error code.
B) Implement REST API Security Essentials solution to automatically mitigate limit exhaustion. If the limit is exceeded, temporarily block access from the service and return a 409 HTTP error code.
C) Increase a limit of replies in a given interval for each API. If the limit is exceeded, block access from the API key permanently and return a 450 HTTP error code.
D) Apply a limit to the number of requests in a given time interval for each API. If the rate is exceeded, block access from the API key temporarily and return a 429 HTTP error code.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
38
An audit is assessing a small business that is selling automotive parts and diagnostic services. Due to increased customer demands, the company recently started to accept credit card payments and acquired a POS terminal. Which compliance regulations must the audit apply to the company?
A) HIPAA
B) FISMA
C) COBIT
D) PCI DSS
A) HIPAA
B) FISMA
C) COBIT
D) PCI DSS

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
39
What is a principle of Infrastructure as Code?
A) System maintenance is delegated to software systems
B) Comprehensive initial designs support robust systems
C) Scripts and manual configurations work together to ensure repeatable routines
D) System downtime is grouped and scheduled across the infrastructure
A) System maintenance is delegated to software systems
B) Comprehensive initial designs support robust systems
C) Scripts and manual configurations work together to ensure repeatable routines
D) System downtime is grouped and scheduled across the infrastructure

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
40
Where do threat intelligence tools search for data to identify potential malicious IP addresses, domain names, and URLs?
A) customer data
B) internal database
C) internal cloud
D) Internet
A) customer data
B) internal database
C) internal cloud
D) Internet

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
41
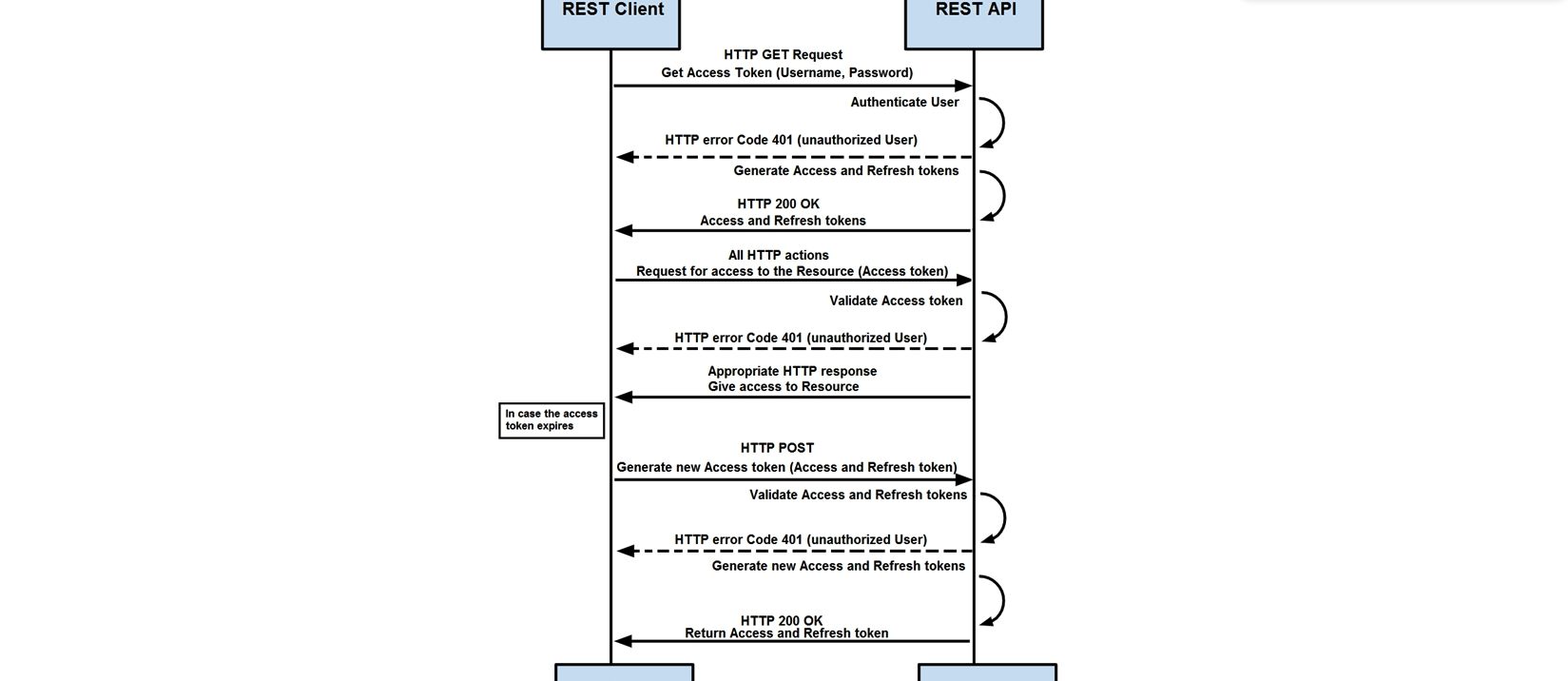 Refer to the exhibit. How are tokens authenticated when the REST API on a device is accessed from a REST API client?
Refer to the exhibit. How are tokens authenticated when the REST API on a device is accessed from a REST API client?A) The token is obtained by providing a password. The REST client requests access to a resource using the access token. The REST API validates the access token and gives access to the resource.
B) The token is obtained by providing a password. The REST API requests access to a resource using the access token, validates the access token, and gives access to the resource.
C) The token is obtained before providing a password. The REST API provides resource access, refreshes tokens, and returns them to the REST client. The REST client requests access to a resource using the access token.
D) The token is obtained before providing a password. The REST client provides access to a resource using the access token. The REST API encrypts the access token and gives access to the resource.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
42
A SOC analyst is notified by the network monitoring tool that there are unusual types of internal traffic on IP subnet 103.921.2239.0/24. The analyst discovers unexplained encrypted data files on a computer system that belongs on that specific subnet. What is the cause of the issue?
A) DDoS attack
B) phishing attack
C) virus outbreak
D) malware outbreak
A) DDoS attack
B) phishing attack
C) virus outbreak
D) malware outbreak

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
43
Employees report computer system crashes within the same week. An analyst is investigating one of the computers that crashed and discovers multiple shortcuts in the system's startup folder. It appears that the shortcuts redirect users to malicious URLs. What is the next step the engineer should take to investigate this case?
A) Remove the shortcut files
B) Check the audit logs
C) Identify affected systems
D) Investigate the malicious URLs
A) Remove the shortcut files
B) Check the audit logs
C) Identify affected systems
D) Investigate the malicious URLs

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
44
A SOC analyst is investigating a recent email delivered to a high-value user for a customer whose network their organization monitors. The email includes a suspicious attachment titled "Invoice RE: 0004489". The hash of the file is gathered from the Cisco Email Security Appliance. After searching Open Source Intelligence, no available history of this hash is found anywhere on the web. What is the next step in analyzing this attachment to allow the analyst to gather indicators of compromise?
A) Run and analyze the DLP Incident Summary Report from the Email Security Appliance
B) Ask the company to execute the payload for real time analysis
C) Investigate further in open source repositories using YARA to find matches
D) Obtain a copy of the file for detonation in a sandbox
A) Run and analyze the DLP Incident Summary Report from the Email Security Appliance
B) Ask the company to execute the payload for real time analysis
C) Investigate further in open source repositories using YARA to find matches
D) Obtain a copy of the file for detonation in a sandbox

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
45
A Mac laptop user notices that several files have disappeared from their laptop documents folder. While looking for the files, the user notices that the browser history was recently cleared. The user raises a case, and an analyst reviews the network usage and discovers that it is abnormally high. Which step should be taken to continue the investigation?
A) Run the sudo sysdiagnose command Run the sudo sysdiagnose command
B) Run the sh command sh
C) Run the w command w
D) Run the who command who
A) Run the sudo sysdiagnose command Run the sudo sysdiagnose command
B) Run the sh command sh
C) Run the w command w
D) Run the who command who

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
46
An engineer has created a bash script to automate a complicated process. During script execution, this error occurs: permission denied. Which command must be added to execute this script?
A) chmod +x ex.sh
B) source ex.sh
C) chroot ex.sh
D) sh ex.sh
A) chmod +x ex.sh
B) source ex.sh
C) chroot ex.sh
D) sh ex.sh

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
47
What is the purpose of hardening systems?
A) to securely configure machines to limit the attack surface
B) to create the logic that triggers alerts when anomalies occur
C) to identify vulnerabilities within an operating system
D) to analyze attacks to identify threat actors and points of entry
A) to securely configure machines to limit the attack surface
B) to create the logic that triggers alerts when anomalies occur
C) to identify vulnerabilities within an operating system
D) to analyze attacks to identify threat actors and points of entry

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
48
A threat actor has crafted and sent a spear-phishing email with what appears to be a trustworthy link to the site of a conference that an employee recently attended. The employee clicked the link and was redirected to a malicious site through which the employee downloaded a PDF attachment infected with ransomware. The employee opened the attachment, which exploited vulnerabilities on the desktop. The ransomware is now installed and is calling back to its command and control server. Which security solution is needed at this stage to mitigate the attack?
A) web security solution
B) email security solution
C) endpoint security solution
D) network security solution
A) web security solution
B) email security solution
C) endpoint security solution
D) network security solution

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
49
An engineer is developing an application that requires frequent updates to close feedback loops and enable teams to quickly apply patches. The team wants their code updates to get to market as often as possible. Which software development approach should be used to accomplish these goals?
A) continuous delivery
B) continuous integration
C) continuous deployment
D) continuous monitoring
A) continuous delivery
B) continuous integration
C) continuous deployment
D) continuous monitoring

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
50
An organization installed a new application server for IP phones. An automated process fetched user credentials from the Active Directory server, and the application will have access to on-premises and cloud services. Which security threat should be mitigated first?
A) aligning access control policies
B) exfiltration during data transfer
C) attack using default accounts
D) data exposure from backups
A) aligning access control policies
B) exfiltration during data transfer
C) attack using default accounts
D) data exposure from backups

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
51
Refer to the exhibit. What is occurring in this packet capture? 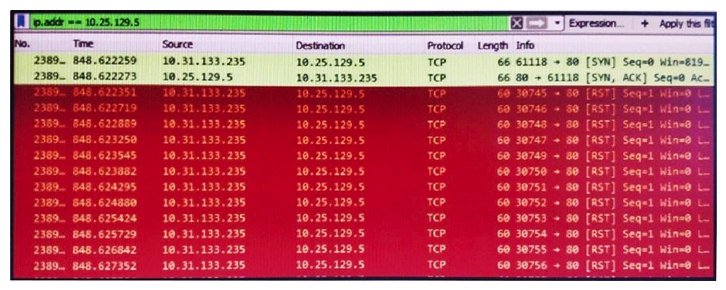
A) TCP port scan
B) TCP flood
C) DNS flood
D) DNS tunneling

A) TCP port scan
B) TCP flood
C) DNS flood
D) DNS tunneling

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
52
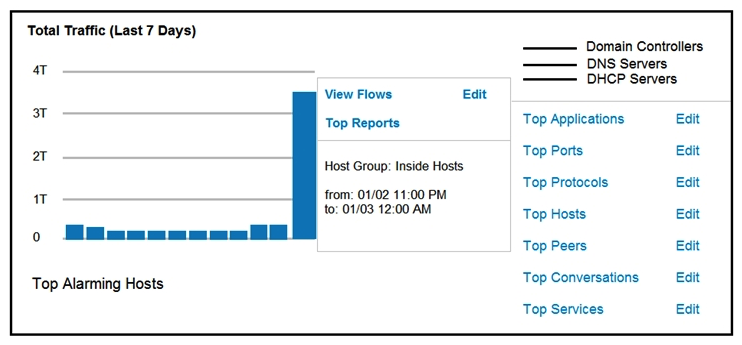 Refer to the exhibit. An engineer notices a significant anomaly in the traffic in one of the host groups in Cisco Secure Network Analytics (Stealthwatch) and must analyze the top data transmissions. Which tool accomplishes this task?
Refer to the exhibit. An engineer notices a significant anomaly in the traffic in one of the host groups in Cisco Secure Network Analytics (Stealthwatch) and must analyze the top data transmissions. Which tool accomplishes this task?A) Top Peers
B) Top Hosts
C) Top Conversations
D) Top Ports

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
53
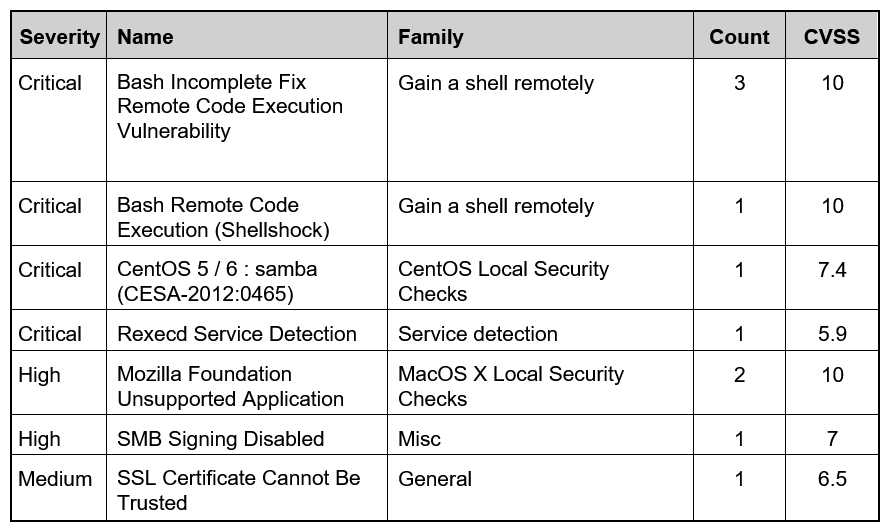 Refer to the exhibit. Based on the detected vulnerabilities, what is the next recommended mitigation step?
Refer to the exhibit. Based on the detected vulnerabilities, what is the next recommended mitigation step?A) Evaluate service disruption and associated risk before prioritizing patches.
B) Perform root cause analysis for all detected vulnerabilities.
C) Remediate all vulnerabilities with descending CVSS score order.
D) Temporarily shut down unnecessary services until patch deployment ends.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
54
Refer to the exhibit. What is the connection status of the ICMP event? 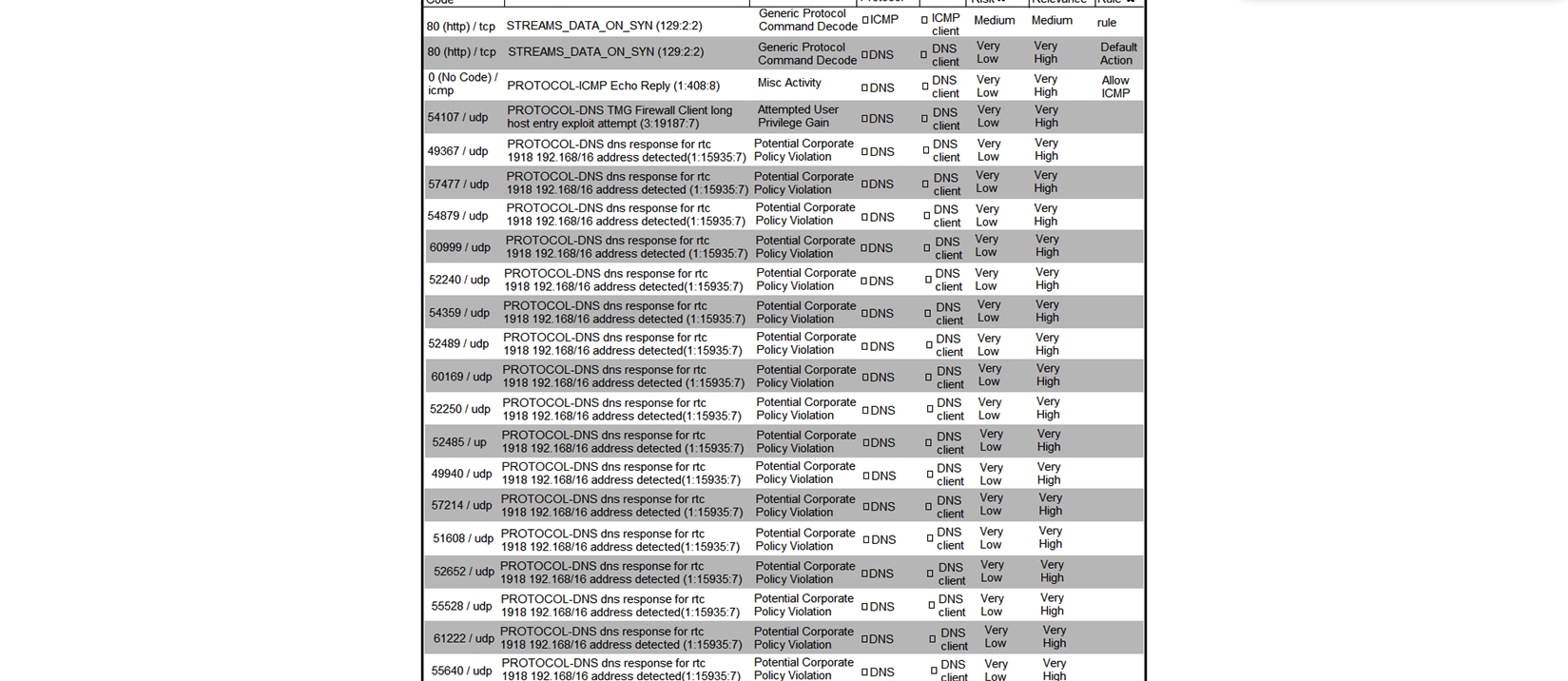
A) blocked by a configured access policy rule
B) allowed by a configured access policy rule
C) blocked by an intrusion policy rule
D) allowed in the default action

A) blocked by a configured access policy rule
B) allowed by a configured access policy rule
C) blocked by an intrusion policy rule
D) allowed in the default action

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
55
An analyst wants to upload an infected file containing sensitive information to a hybrid-analysis sandbox. According to the NIST.SP 800-150 guide to cyber threat information sharing, what is the analyst required to do before uploading the file to safeguard privacy?
A) Verify hash integrity.
B) Remove all personally identifiable information.
C) Ensure the online sandbox is GDPR compliant.
D) Lock the file to prevent unauthorized access.
A) Verify hash integrity.
B) Remove all personally identifiable information.
C) Ensure the online sandbox is GDPR compliant.
D) Lock the file to prevent unauthorized access.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
56
A company launched an e-commerce website with multiple points of sale through internal and external e-stores. Customers access the stores from the public website, and employees access the stores from the intranet with an SSO. Which action is needed to comply with PCI standards for hardening the systems?
A) Mask PAN numbers
B) Encrypt personal data
C) Encrypt access
D) Mask sales details
A) Mask PAN numbers
B) Encrypt personal data
C) Encrypt access
D) Mask sales details

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
57
Refer to the exhibit. Which asset has the highest risk value? 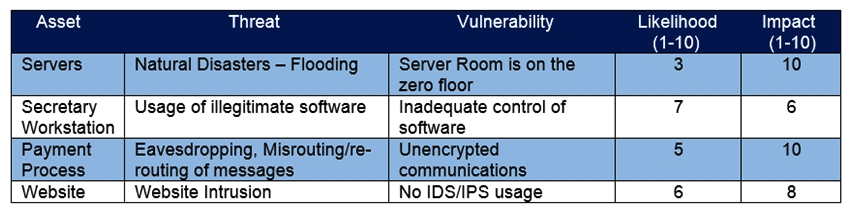
A) servers
B) website
C) payment process
D) secretary workstation

A) servers
B) website
C) payment process
D) secretary workstation

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
58
What is a limitation of cyber security risk insurance?
A) It does not cover the costs to restore stolen identities as a result of a cyber attack
B) It does not cover the costs to hire forensics experts to analyze the cyber attack
C) It does not cover the costs of damage done by third parties as a result of a cyber attack
D) It does not cover the costs to hire a public relations company to help deal with a cyber attack
A) It does not cover the costs to restore stolen identities as a result of a cyber attack
B) It does not cover the costs to hire forensics experts to analyze the cyber attack
C) It does not cover the costs of damage done by third parties as a result of a cyber attack
D) It does not cover the costs to hire a public relations company to help deal with a cyber attack

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
59
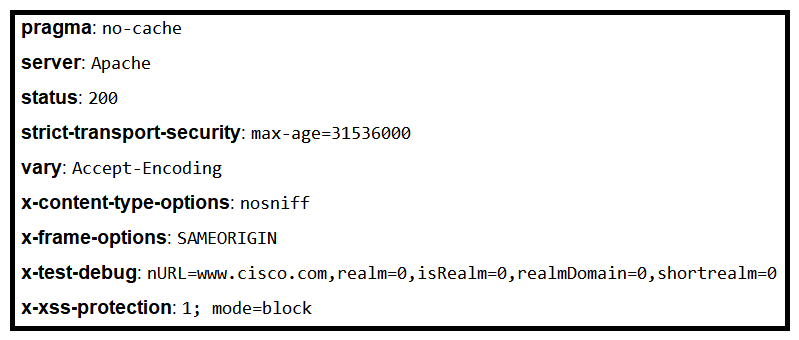 Refer to the exhibit. Where is the MIME type that should be followed indicated?
Refer to the exhibit. Where is the MIME type that should be followed indicated?A) x-test-debug
B) strict-transport-security
C) x-xss-protection
D) x-content-type-options

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
60
An engineer is investigating several cases of increased incoming spam emails and suspicious emails from the HR and service departments. While checking the event sources, the website monitoring tool showed several web scraping alerts overnight. Which type of compromise is indicated?
A) phishing
B) dumpster diving
C) social engineering
D) privilege escalation
A) phishing
B) dumpster diving
C) social engineering
D) privilege escalation

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
61
What is idempotence?
A) the assurance of system uniformity throughout the whole delivery process
B) the ability to recover from failures while keeping critical services running
C) the necessity of setting maintenance of individual deployment environments
D) the ability to set the target environment configuration regardless of the starting state
A) the assurance of system uniformity throughout the whole delivery process
B) the ability to recover from failures while keeping critical services running
C) the necessity of setting maintenance of individual deployment environments
D) the ability to set the target environment configuration regardless of the starting state

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
62
What is the impact of hardening machine images for deployment?
A) reduces the attack surface
B) increases the speed of patch deployment
C) reduces the steps needed to mitigate threats
D) increases the availability of threat alerts
A) reduces the attack surface
B) increases the speed of patch deployment
C) reduces the steps needed to mitigate threats
D) increases the availability of threat alerts

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
63
A SOC engineer discovers that the organization had three DDOS attacks overnight. Four servers are reported offline, even though the hardware seems to be working as expected. One of the offline servers is affecting the pay system reporting times. Three employees, including executive management, have reported ransomware on their laptops. Which steps help the engineer understand a comprehensive overview of the incident?
A) Run and evaluate a full packet capture on the workloads, review SIEM logs, and define a root cause.
B) Run and evaluate a full packet capture on the workloads, review SIEM logs, and plan mitigation steps.
C) Check SOAR to learn what the security systems are reporting about the overnight events, research the attacks, and plan mitigation step.
D) Check SOAR to know what the security systems are reporting about the overnight events, review the threat vectors, and define a root cause.
A) Run and evaluate a full packet capture on the workloads, review SIEM logs, and define a root cause.
B) Run and evaluate a full packet capture on the workloads, review SIEM logs, and plan mitigation steps.
C) Check SOAR to learn what the security systems are reporting about the overnight events, research the attacks, and plan mitigation step.
D) Check SOAR to know what the security systems are reporting about the overnight events, review the threat vectors, and define a root cause.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
64
A security manager received an email from an anomaly detection service, that one of their contractors has downloaded 50 documents from the company's confidential document management folder using a company-owned asset al039-ice-4ce687TL0500. A security manager reviewed the content of downloaded documents and noticed that the data affected is from different departments. What are the actions a security manager should take?
A) Measure confidentiality level of downloaded documents.
B) Report to the incident response team.
C) Escalate to contractor's manager.
D) Communicate with the contractor to identify the motives.
A) Measure confidentiality level of downloaded documents.
B) Report to the incident response team.
C) Escalate to contractor's manager.
D) Communicate with the contractor to identify the motives.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
65
A company recently started accepting credit card payments in their local warehouses and is undergoing a PCI audit. Based on business requirements, the company needs to store sensitive authentication data for 45 days. How must data be stored for compliance?
A) post-authorization by non-issuing entities if there is a documented business justification
B) by entities that issue the payment cards or that perform support issuing services
C) post-authorization by non-issuing entities if the data is encrypted and securely stored
D) by issuers and issuer processors if there is a legitimate reason
A) post-authorization by non-issuing entities if there is a documented business justification
B) by entities that issue the payment cards or that perform support issuing services
C) post-authorization by non-issuing entities if the data is encrypted and securely stored
D) by issuers and issuer processors if there is a legitimate reason

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
66
A security architect in an automotive factory is working on the Cyber Security Management System and is implementing procedures and creating policies to prevent attacks. Which standard must the architect apply?
A) IEC62446
B) IEC62443
C) IEC62439-3
D) IEC62439-2
A) IEC62446
B) IEC62443
C) IEC62439-3
D) IEC62439-2

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
67
Which bash command will print all lines from the "colors.txt" file containing the non case-sensitive pattern "Yellow"?
A) grep -i "yellow" colors.txt
B) locate "yellow" colors.txt
C) locate -i "Yellow" colors.txt
D) grep "Yellow" colors.txt
A) grep -i "yellow" colors.txt
B) locate "yellow" colors.txt
C) locate -i "Yellow" colors.txt
D) grep "Yellow" colors.txt

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
68
An organization suffered a security breach in which the attacker exploited a Netlogon Remote Protocol vulnerability for further privilege escalation. Which two actions should the incident response team take to prevent this type of attack from reoccurring? (Choose two.)
A) Implement a patch management process.
B) Scan the company server files for known viruses.
C) Apply existing patches to the company servers.
D) Automate antivirus scans of the company servers.
E) Define roles and responsibilities in the incident response playbook.
A) Implement a patch management process.
B) Scan the company server files for known viruses.
C) Apply existing patches to the company servers.
D) Automate antivirus scans of the company servers.
E) Define roles and responsibilities in the incident response playbook.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
69
An organization had an incident with the network availability during which devices unexpectedly malfunctioned. An engineer is investigating the incident and found that the memory pool buffer usage reached a peak before the malfunction. Which action should the engineer take to prevent this issue from reoccurring?
A) Disable memory limit.
B) Disable CPU threshold trap toward the SNMP server.
C) Enable memory tracing notifications.
D) Enable memory threshold notifications.
A) Disable memory limit.
B) Disable CPU threshold trap toward the SNMP server.
C) Enable memory tracing notifications.
D) Enable memory threshold notifications.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
70
A logistic company must use an outdated application located in a private VLAN during the migration to new technologies. The IPS blocked and reported an unencrypted communication. Which tuning option should be applied to IPS?
A) Allow list only authorized hosts to contact the application's IP at a specific port.
B) Allow list HTTP traffic through the corporate VLANS.
C) Allow list traffic to application's IP from the internal network at a specific port.
D) Allow list only authorized hosts to contact the application's VLAN.
A) Allow list only authorized hosts to contact the application's IP at a specific port.
B) Allow list HTTP traffic through the corporate VLANS.
C) Allow list traffic to application's IP from the internal network at a specific port.
D) Allow list only authorized hosts to contact the application's VLAN.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
71
An engineer notices that every Sunday night, there is a two-hour period with a large load of network activity. Upon further investigation, the engineer finds that the activity is from locations around the globe outside the organization's service area. What are the next steps the engineer must take?
A) Assign the issue to the incident handling provider because no suspicious activity has been observed during business hours.
B) Review the SIEM and FirePower logs, block all traffic, and document the results of calling the call center.
C) Define the access points using StealthWatch or SIEM logs, understand services being offered during the hours in question, and cross-correlate other source events.
D) Treat it as a false positive, and accept the SIEM issue as valid to avoid alerts from triggering on weekends.
A) Assign the issue to the incident handling provider because no suspicious activity has been observed during business hours.
B) Review the SIEM and FirePower logs, block all traffic, and document the results of calling the call center.
C) Define the access points using StealthWatch or SIEM logs, understand services being offered during the hours in question, and cross-correlate other source events.
D) Treat it as a false positive, and accept the SIEM issue as valid to avoid alerts from triggering on weekends.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
72
A SOC team receives multiple alerts by a rule that detects requests to malicious URLs and informs the incident response team to block the malicious URLs requested on the firewall. Which action will improve the effectiveness of the process?
A) Block local to remote HTTP/HTTPS requests on the firewall for users who triggered the rule.
B) Inform the user by enabling an automated email response when the rule is triggered.
C) Inform the incident response team by enabling an automated email response when the rule is triggered.
D) Create an automation script for blocking URLs on the firewall when the rule is triggered.
A) Block local to remote HTTP/HTTPS requests on the firewall for users who triggered the rule.
B) Inform the user by enabling an automated email response when the rule is triggered.
C) Inform the incident response team by enabling an automated email response when the rule is triggered.
D) Create an automation script for blocking URLs on the firewall when the rule is triggered.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
73
An analyst received multiple alerts on the SIEM console of users that are navigating to malicious URLs. The analyst needs to automate the task of receiving alerts and processing the data for further investigations. Three variables are available from the SIEM console to include in an automation script: console_ip, api_token, and reference_set_name. What must be added to this script to receive a successful HTTP response? #!/usr/bin/python import sys import requests
A) {1}, {2}
B) {1}, {3}
C) console_ip, api_token
D) console_ip, reference_set_name
A) {1}, {2}
B) {1}, {3}
C) console_ip, api_token
D) console_ip, reference_set_name

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
74
Which action should be taken when the HTTP response code 301 is received from a web application?
A) Update the cached header metadata.
B) Confirm the resource's location.
C) Increase the allowed user limit.
D) Modify the session timeout setting.
A) Update the cached header metadata.
B) Confirm the resource's location.
C) Increase the allowed user limit.
D) Modify the session timeout setting.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
75
A cloud engineer needs a solution to deploy applications on a cloud without being able to manage and control the server OS. Which type of cloud environment should be used?
A) IaaS
B) PaaS
C) DaaS
D) SaaS
A) IaaS
B) PaaS
C) DaaS
D) SaaS

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
76
Engineers are working to document, list, and discover all used applications within an organization. During the regular assessment of applications from the HR backup server, an engineer discovered an unknown application. The analysis showed that the application is communicating with external addresses on a non-secure, unencrypted channel. Information gathering revealed that the unknown application does not have an owner and is not being used by a business unit. What are the next two steps the engineers should take in this investigation? (Choose two.)
A) Determine the type of data stored on the affected asset, document the access logs, and engage the incident response team.
B) Identify who installed the application by reviewing the logs and gather a user access log from the HR department.
C) Verify user credentials on the affected asset, modify passwords, and confirm available patches and updates are installed.
D) Initiate a triage meeting with department leads to determine if the application is owned internally or used by any business unit and document the asset owner.
A) Determine the type of data stored on the affected asset, document the access logs, and engage the incident response team.
B) Identify who installed the application by reviewing the logs and gather a user access log from the HR department.
C) Verify user credentials on the affected asset, modify passwords, and confirm available patches and updates are installed.
D) Initiate a triage meeting with department leads to determine if the application is owned internally or used by any business unit and document the asset owner.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
77
An engineer received multiple reports from users trying to access a company website and instead of landing on the website, they are redirected to a malicious website that asks them to fill in sensitive personal data. Which type of attack is occurring?
A) Address Resolution Protocol poisoning
B) session hijacking attack
C) teardrop attack
D) Domain Name System poisoning
A) Address Resolution Protocol poisoning
B) session hijacking attack
C) teardrop attack
D) Domain Name System poisoning

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
78
A security engineer discovers that a spreadsheet containing confidential information for nine of their employees was fraudulently posted on a competitor's website. The spreadsheet contains names, salaries, and social security numbers. What is the next step the engineer should take in this investigation?
A) Determine if there is internal knowledge of this incident.
B) Check incoming and outgoing communications to identify spoofed emails.
C) Disconnect the network from Internet access to stop the phishing threats and regain control.
D) Engage the legal department to explore action against the competitor that posted the spreadsheet.
A) Determine if there is internal knowledge of this incident.
B) Check incoming and outgoing communications to identify spoofed emails.
C) Disconnect the network from Internet access to stop the phishing threats and regain control.
D) Engage the legal department to explore action against the competitor that posted the spreadsheet.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
79
An engineer detects an intrusion event inside an organization's network and becomes aware that files that contain personal data have been accessed. Which action must be taken to contain this attack?
A) Disconnect the affected server from the network.
B) Analyze the source.
C) Access the affected server to confirm compromised files are encrypted.
D) Determine the attack surface.
A) Disconnect the affected server from the network.
B) Analyze the source.
C) Access the affected server to confirm compromised files are encrypted.
D) Determine the attack surface.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck
80
What is the difference between process orchestration and automation?
A) Orchestration combines a set of automated tools, while automation is focused on the tools to automate process flows.
B) Orchestration arranges the tasks, while automation arranges processes.
C) Orchestration minimizes redundancies, while automation decreases the time to recover from redundancies.
D) Automation optimizes the individual tasks to execute the process, while orchestration optimizes frequent and repeatable processes.
A) Orchestration combines a set of automated tools, while automation is focused on the tools to automate process flows.
B) Orchestration arranges the tasks, while automation arranges processes.
C) Orchestration minimizes redundancies, while automation decreases the time to recover from redundancies.
D) Automation optimizes the individual tasks to execute the process, while orchestration optimizes frequent and repeatable processes.

Unlock Deck
Unlock for access to all 106 flashcards in this deck.
Unlock Deck
k this deck



