Deck 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/49
Play
Full screen (f)
Deck 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)
1
What causes authentication failures on a Cisco WSA when LDAP is used for authentication?
A) when the passphrase contains only 5 characters
B) when the passphrase contains characters that are not 7-bit ASCI
C) when the passphrase contains one of following characters '@ # $ % ^'
D) when the passphrase contains 50 characters
A) when the passphrase contains only 5 characters
B) when the passphrase contains characters that are not 7-bit ASCI
C) when the passphrase contains one of following characters '@ # $ % ^'
D) when the passphrase contains 50 characters
when the passphrase contains characters that are not 7-bit ASCI
2
By default, which two pieces of information does the Cisco WSA access log contain? (Choose two.)
A) HTTP Request Code
B) Content Type
C) Client IP Address
D) User Agent
E) Transaction ID
A) HTTP Request Code
B) Content Type
C) Client IP Address
D) User Agent
E) Transaction ID
HTTP Request Code
Client IP Address
Client IP Address
3
Which two benefits does AMP provide compared to the other scanning engines on the Cisco WSA? (Choose two.)
A) protection against malware
B) protection against zero-day attacks
C) protection against spam
D) protection against viruses
E) protection against targeted file-based attacks
A) protection against malware
B) protection against zero-day attacks
C) protection against spam
D) protection against viruses
E) protection against targeted file-based attacks
protection against zero-day attacks
protection against viruses
protection against viruses
4
Which IP address and port are used by default to run the system setup wizard?
A) http://192.168.42.42:80
B) https://192.168.42.42:8080
C) https://192.168.42.10:8443
D) http://192.168.43.42:8080
A) http://192.168.42.42:80
B) https://192.168.42.42:8080
C) https://192.168.42.10:8443
D) http://192.168.43.42:8080

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
5
Which two configuration options are available on a Cisco WSA within a decryption policy? (Choose two.)
A) Pass Through
B) Warn
C) Decrypt
D) Allow
E) Block
A) Pass Through
B) Warn
C) Decrypt
D) Allow
E) Block

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
6
Which information in the HTTP request is used to determine if it is subject to the referrer exceptions feature in the Cisco WSA?
A) protocol
B) version
C) header
D) payload
A) protocol
B) version
C) header
D) payload

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
7
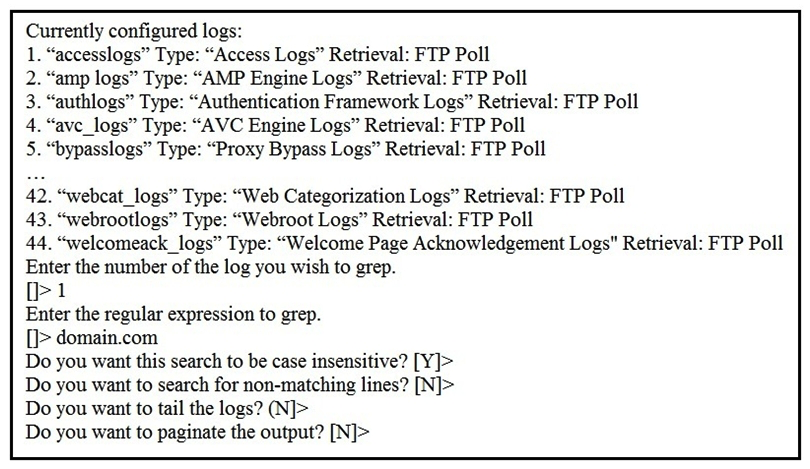 Refer to the exhibit. Which command displays this output?
Refer to the exhibit. Which command displays this output?A) grep
B) logconfig
C) rollovernow
D) tail

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
8
Which behavior is seen while the policy trace tool is used to troubleshoot a Cisco WSA?
A) External DLP polices are evaluated by the tool
B) A real client request is processed and an EUN page is displayed
C) SOCKS policies are evaluated by the tool
D) The web proxy does not record the policy trace test requests in the access log when the tool is in use
A) External DLP polices are evaluated by the tool
B) A real client request is processed and an EUN page is displayed
C) SOCKS policies are evaluated by the tool
D) The web proxy does not record the policy trace test requests in the access log when the tool is in use

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
9
What is required on the Cisco WSA when an AMP file reputation server private cloud is configured?
A) private key from the server to encrypt messages
B) private key to decrypt messages
C) public and private keys from the server
D) public key from the server
A) private key from the server to encrypt messages
B) private key to decrypt messages
C) public and private keys from the server
D) public key from the server

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
10
A user browses to a company website that is categorized as "Business and Industry" and contains a Facebook post. The user cannot see the Facebook post because the category "Social Networking" is blocked. Which configuration allows the user to see the Facebook post?
A)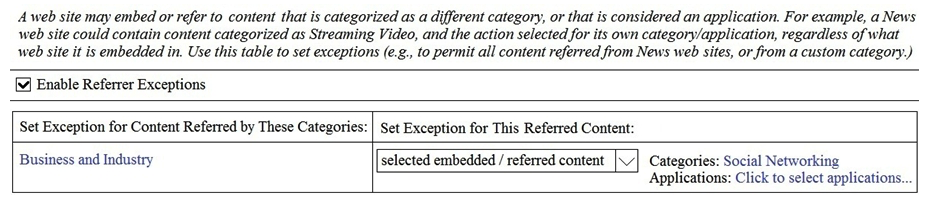
B)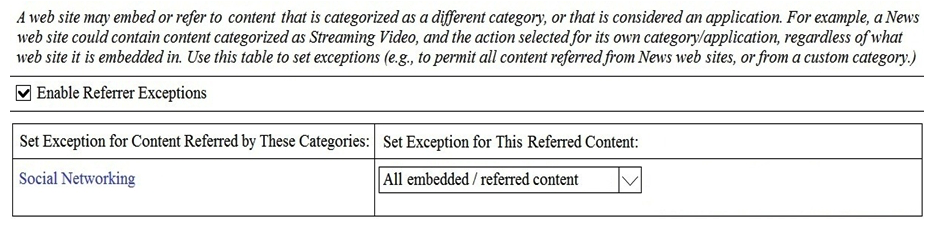
C)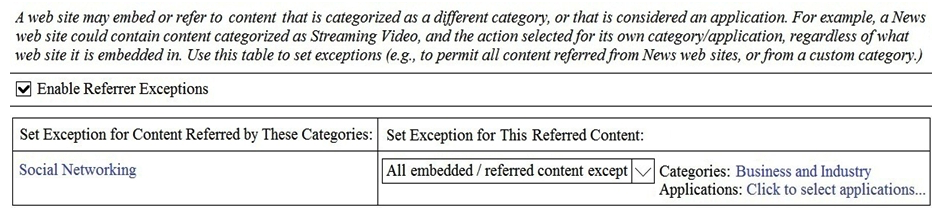
D)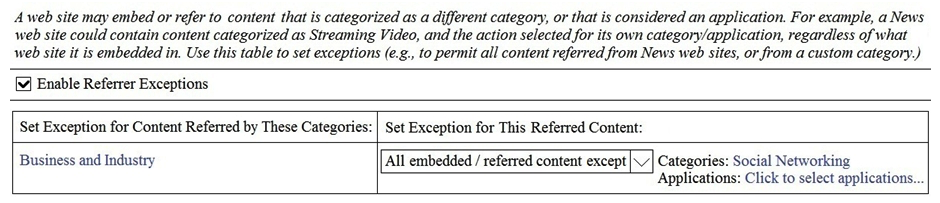
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
11
Which method is used by AMP against zero-day and targeted file-based attacks?
A) analyzing behavior of all files that are not yet known to the reputation service
B) periodically evaluating emerging threats as new information becomes available
C) implementing security group tags
D) obtaining the reputation of known files
A) analyzing behavior of all files that are not yet known to the reputation service
B) periodically evaluating emerging threats as new information becomes available
C) implementing security group tags
D) obtaining the reputation of known files

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
12
Which certificate format does a Cisco WSA need when HTTPS proxy is configured?
A) DER
B) CER
C) PEM
D) CRL
A) DER
B) CER
C) PEM
D) CRL

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
13
Which command is used to flush a single user from authentication memory?
A) isedata
B) authcache
C) diagnostic
D) clear
A) isedata
B) authcache
C) diagnostic
D) clear

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
14
When a Cisco WSA is installed with default settings, which port is assigned to the web proxy if the M1 port is used exclusively for management?
A) T1
B) P2
C) T2
D) P1
A) T1
B) P2
C) T2
D) P1

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
15
What is a benefit of integrating Cisco Cognitive Threat Analytics with a Cisco WSA?
A) It adds additional information to the Cisco WSA reports
B) It adds additional malware protection to the Cisco WSA
C) It provides the ability to use artificial intelligence to block viruses
D) It reduces time to identify threats in the network
A) It adds additional information to the Cisco WSA reports
B) It adds additional malware protection to the Cisco WSA
C) It provides the ability to use artificial intelligence to block viruses
D) It reduces time to identify threats in the network

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
16
Which statement about Cisco Advanced Web Security Reporting integration is true?
A) AWSR uses IP addresses to differentiate Cisco WSA deployments
B) AWSR does not require a license to index data
C) AWSR can remove log files after they are indexed
D) AWSR installation is CLI-based on Windows and Red Hat Linux systems
A) AWSR uses IP addresses to differentiate Cisco WSA deployments
B) AWSR does not require a license to index data
C) AWSR can remove log files after they are indexed
D) AWSR installation is CLI-based on Windows and Red Hat Linux systems

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
17
What are all of the available options for configuring an exception to blocking for referred content?
A) all embedded/referred and all embedded/referred except
B) selected embedded/referred except, all embedded/referred, and selected embedded/referred
C) selected embedded/referred and all embedded/referred except
D) all embedded/referred, selected embedded/referred, and all embedded/referred except
A) all embedded/referred and all embedded/referred except
B) selected embedded/referred except, all embedded/referred, and selected embedded/referred
C) selected embedded/referred and all embedded/referred except
D) all embedded/referred, selected embedded/referred, and all embedded/referred except

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
18
What is used to configure WSA as an explicit proxy?
A) IP Spoofing from router
B) Network settings from user browser
C) WCCP redirection from firewall
D) Auto redirection using PBR from switch
A) IP Spoofing from router
B) Network settings from user browser
C) WCCP redirection from firewall
D) Auto redirection using PBR from switch

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
19
What must be configured first when creating an access policy that matches the Active Directory group?
A) authentication, authorization, and accounting of groups
B) FQDN specification
C) authentication realm
D) authorized groups specification
A) authentication, authorization, and accounting of groups
B) FQDN specification
C) authentication realm
D) authorized groups specification

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
20
What is a valid predefined time range when configuring a Web Tracking query?
A) year
B) minute
C) hour
D) month
A) year
B) minute
C) hour
D) month

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
21
What is the default action when a new custom category is created and added to an access policy?
A) monitor
B) allow
C) block
D) decrypt
A) monitor
B) allow
C) block
D) decrypt

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
22
What must be configured to require users to click through an acceptance page before they are allowed to go to the Internet through the Cisco WSA?
A) Enable End-User Acknowledgement Page and set to Required in Identification Profiles Enable End-User Acknowledgement Page and set to Required in Identification Profiles
B) Enable End -User URL Filtering Warning Page and set to Required in Identification Profiles Enable End -User URL Filtering Warning Page and set to
C) Enable End-User Acknowledgement Page and set to Required in Access Policies in Access Policies
D) Enable End-User URL Filtering Warning Page and set to Required in Access Policies Enable End-User URL Filtering Warning Page and set to
A) Enable End-User Acknowledgement Page and set to Required in Identification Profiles Enable End-User Acknowledgement Page and set to Required in Identification Profiles
B) Enable End -User URL Filtering Warning Page and set to Required in Identification Profiles Enable End -User URL Filtering Warning Page and set to
C) Enable End-User Acknowledgement Page and set to Required in Access Policies in Access Policies
D) Enable End-User URL Filtering Warning Page and set to Required in Access Policies Enable End-User URL Filtering Warning Page and set to

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
23
How does dynamic content analysis improve URL categorization?
A) It analyzes content based on cached destination content
B) It adds intelligence to detect categories by analyzing responses
C) It can be used as the only URL analysis method
D) It analyzes content of categorized URL to tune decisions and correct categorization errors
A) It analyzes content based on cached destination content
B) It adds intelligence to detect categories by analyzing responses
C) It can be used as the only URL analysis method
D) It analyzes content of categorized URL to tune decisions and correct categorization errors

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
24
Which key is needed to pair a Cisco WSA and Cisco ScanCenter for CTA?
A) public SSH key that the Cisco WSA generates
B) public SSH key that Cisco ScanCenter generates
C) private SSH key that Cisco ScanCenter generates
D) private SSH key that the Cisco WSA generates
A) public SSH key that the Cisco WSA generates
B) public SSH key that Cisco ScanCenter generates
C) private SSH key that Cisco ScanCenter generates
D) private SSH key that the Cisco WSA generates

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
25
Which statement about identification profile default settings on the Cisco WSA is true?
A) Identification profiles do not require authentication
B) Guest identification profile should be processed first
C) Identification profiles can include only one user group
D) AsyncOS processes identification profiles alphabetically
A) Identification profiles do not require authentication
B) Guest identification profile should be processed first
C) Identification profiles can include only one user group
D) AsyncOS processes identification profiles alphabetically

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
26
Which two caching modes are available in the Cisco WSA? (Choose two.)
A) active cache
B) all cache
C) aggressive cache
D) safe cache
E) no cache
A) active cache
B) all cache
C) aggressive cache
D) safe cache
E) no cache

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
27
Which two modes of operation does the Cisco WSA provide? (Choose two.)
A) connector
B) proxy
C) transparent
D) standard
E) explicit
A) connector
B) proxy
C) transparent
D) standard
E) explicit

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
28
Which two log types does the Cisco WSA provide to troubleshoot Cisco data security and external data loss prevention policies? (Choose two.)
A) upload data
B) data security
C) default proxy
D) data access
E) external data
A) upload data
B) data security
C) default proxy
D) data access
E) external data

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
29
What is the purpose of using AMP file analysis on a Cisco WSA to continuously evaluate emerging threats?
A) to take appropriate action on new files that enter the network
B) to remove files from quarantine by stopping their retention period
C) to notify you of files that are determined to be threats after they have entered your network
D) to send all files downloaded through the Cisco WSA to the AMP cloud
A) to take appropriate action on new files that enter the network
B) to remove files from quarantine by stopping their retention period
C) to notify you of files that are determined to be threats after they have entered your network
D) to send all files downloaded through the Cisco WSA to the AMP cloud

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
30
When an access policy is created, what is the default option for the Application Settings?
A) Use Global Policy Applications Settings
B) Define the Applications Custom Setting
C) Set all applications to Block
D) Set all applications to Monitor
A) Use Global Policy Applications Settings
B) Define the Applications Custom Setting
C) Set all applications to Block
D) Set all applications to Monitor

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
31
Which two parameters are mandatory to control access to websites with proxy authentication on a Cisco WSA? (Choose two.)
A) External Authentication
B) Identity Enabled Authentication
C) Transparent User Identification
D) Credential Encryption
E) Authentication Realm
A) External Authentication
B) Identity Enabled Authentication
C) Transparent User Identification
D) Credential Encryption
E) Authentication Realm

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
32
Which two features on the Cisco WSA help prevent outbound data loss for HTTP or FTP traffic? (Choose two.)
A) web reputation filters
B) Advanced Malware Protection
C) third-party DLP integration
D) data security filters
E) SOCKS proxy
A) web reputation filters
B) Advanced Malware Protection
C) third-party DLP integration
D) data security filters
E) SOCKS proxy

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
33
Which type of certificate must be installed on a Cisco WSA for HTTPS inspection?
A) server
B) client
C) root
D) wildcard
A) server
B) client
C) root
D) wildcard

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
34
What is needed to enable an HTTPS proxy?
A) self-signed server certificate
B) trusted third-party CA signed root certificate
C) self-signed CSR
D) self-signed root certificate
A) self-signed server certificate
B) trusted third-party CA signed root certificate
C) self-signed CSR
D) self-signed root certificate

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
35
Which statement about the SOCKS proxy is true?
A) SOCKS is a general purpose proxy
B) SOCKS operates on TCP port 80, 443, and 8334
C) SOCKS is used only for traffic that is redirected through a firewall
D) SOCKS is used for UDP traffic only
A) SOCKS is a general purpose proxy
B) SOCKS operates on TCP port 80, 443, and 8334
C) SOCKS is used only for traffic that is redirected through a firewall
D) SOCKS is used for UDP traffic only

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
36
An administrator wants to restrict file uploads to Facebook using the AVC feature. Under which two actions must the administrator apply this restriction to an access policy? (Choose two.)
A) Monitor Facebook General
B) Monitor Social Networking
C) Monitor Facebook Photos and Videos
D) Monitor Facebook Messages and Chat
E) Monitor Facebook Application
A) Monitor Facebook General
B) Monitor Social Networking
C) Monitor Facebook Photos and Videos
D) Monitor Facebook Messages and Chat
E) Monitor Facebook Application

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
37
What is the function of a PAC file on a Cisco WSA?
A) The file allows redirection of web traffic to a specific proxy server
B) The file is mandatory for a transparent proxy to redirect user traffic
C) The file provides instructions about which URL categories are permitted
D) The file is mandatory for an explicit proxy to forward user traffic
A) The file allows redirection of web traffic to a specific proxy server
B) The file is mandatory for a transparent proxy to redirect user traffic
C) The file provides instructions about which URL categories are permitted
D) The file is mandatory for an explicit proxy to forward user traffic

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
38
Which port is configured in a browser to use the Cisco WSA web proxy with default settings?
A) 8080
B) 8443
C) 8021
D) 3128
A) 8080
B) 8443
C) 8021
D) 3128

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
39
A network administrator noticed that all traffic that is redirected to the Cisco WSA from the Cisco ASA firewall cannot get to the Internet in a Transparent proxy environment using WCCP. Which troubleshooting action must be taken on the CLI to make sure that WCCP communication is not failing?
A) Disable WCCP to see if the WCCP service is causing the issue
B) Explicitly point the browser to the proxy
C) Ping the WCCP device
D) Check WCCP logs in debug mode
A) Disable WCCP to see if the WCCP service is causing the issue
B) Explicitly point the browser to the proxy
C) Ping the WCCP device
D) Check WCCP logs in debug mode

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
40
Which configuration option is suitable for explicit mode deployment?
A) PAC
B) WCCP
C) ITD
D) PBR
A) PAC
B) WCCP
C) ITD
D) PBR

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
41
How does the Cisco WSA choose which scanning engine verdict to use when there is more than one verdict?
A) based on the least restrictive verdict
B) based on the most restrictive verdict
C) based on the first verdict returned
D) based on the last verdict returned
A) based on the least restrictive verdict
B) based on the most restrictive verdict
C) based on the first verdict returned
D) based on the last verdict returned

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
42
Which information within Cisco Advanced Web Security Reporting is used to generate a report that lists visited domains?
A) URL categories
B) web reputation
C) websites
D) application visibility
A) URL categories
B) web reputation
C) websites
D) application visibility

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
43
Which configuration mode does the Cisco WSA use to create an Active Directory realm for Kerberos authentication?
A) Forward
B) Connector
C) Transparent
D) Standard
A) Forward
B) Connector
C) Transparent
D) Standard

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
44
Which two sources provide data to Cisco Advanced Web Security Reporting to create dashboards? (Choose two.)
A) Cisco WSA devices
B) Cisco ISE
C) Cisco ASAv
D) Cisco Security MARS
E) Cisco Cloud Web Security gateways
A) Cisco WSA devices
B) Cisco ISE
C) Cisco ASAv
D) Cisco Security MARS
E) Cisco Cloud Web Security gateways

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
45
Which two configuration options can be configured when invalid certificates are processed with the HTTPS proxy on WSA enabled? (Choose two.)
A) allow
B) monitor
C) drop
D) block
E) redirect
A) allow
B) monitor
C) drop
D) block
E) redirect

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
46
Which type of FTP proxy does the Cisco WSA support?
A) non-native FTP
B) FTP over UDP tunneling
C) FTP over HTTP
D) hybrid FTP
A) non-native FTP
B) FTP over UDP tunneling
C) FTP over HTTP
D) hybrid FTP

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
47
What is the primary benefit of using Cisco Advanced Web Security Reporting?
A) ability to see the malicious activity of a user
B) L4TM report with client-malware risk
C) centralized and granular reporting
D) access to a day report with historical data
A) ability to see the malicious activity of a user
B) L4TM report with client-malware risk
C) centralized and granular reporting
D) access to a day report with historical data

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
48
Which statement about configuring an identification profile for machine authentication is true?
A) Cloud Web Security Connector mode with an active directory enabled supports machine authentication
B) Identification profile machine ID is supported locally, but the Cisco WSA does not support machine ID authentication
C) Cloud Web Security with Kerberos enabled supports machine authentication
D) If an Active Directory realm is used, identification can be performed for an authenticated user or IP address but not for a machine ID
A) Cloud Web Security Connector mode with an active directory enabled supports machine authentication
B) Identification profile machine ID is supported locally, but the Cisco WSA does not support machine ID authentication
C) Cloud Web Security with Kerberos enabled supports machine authentication
D) If an Active Directory realm is used, identification can be performed for an authenticated user or IP address but not for a machine ID

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
49
Which two caches must be cleared on a Cisco WSA to resolve an issue in processing requests? (Choose two.)
A) authentication cache
B) application cache
C) logging cache
D) DNS cache
E) HTTP cache
A) authentication cache
B) application cache
C) logging cache
D) DNS cache
E) HTTP cache

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck



