Deck 9: Discovering Computers: Computer Security and Safety, Ethics, and Privacy
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/112
Play
Full screen (f)
Deck 9: Discovering Computers: Computer Security and Safety, Ethics, and Privacy
1
____ is a technique intruders use to make their network or Internet transmission appear legitimate to a victim computer or network.
A)Rebuking
B)Spoofing
C)Transmitting
D)Victimizing
A)Rebuking
B)Spoofing
C)Transmitting
D)Victimizing
B
2
If an antivirus program cannot remove an infection, it often ____.
A)quarantines the infected file
B)reports the user computer
C)disables the drive the file is on
D)removes the user from its registry
A)quarantines the infected file
B)reports the user computer
C)disables the drive the file is on
D)removes the user from its registry
A
3
In applications that allow users to write ____, the security level should be set so the application warns users that a document they are attempting to open contains a macro.
A)Javascript
B)macros
C)antivirus definitions
D)antispyware definitions
A)Javascript
B)macros
C)antivirus definitions
D)antispyware definitions
B
4
Many systems implement access controls using a two-phase process called ____.
A)access or deny
B)identification and authentication
C)access and approval
D)identification and approval
A)access or deny
B)identification and authentication
C)access and approval
D)identification and approval

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
5
A ____ is someone who uses the Internet or network to destroy or damage computers for political reasons.
A)hacker
B)script kiddie
C)cyberextortionist
D)cyberterrorist
A)hacker
B)script kiddie
C)cyberextortionist
D)cyberterrorist

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
6
____ protects a computer against viruses by identifying and removing any computer viruses found in memory, on storage media, or on incoming files.
A)An anti-spam program
B)E-mail encryption
C)An antivirus program
D)E-mail filtering
A)An anti-spam program
B)E-mail encryption
C)An antivirus program
D)E-mail filtering

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
7
 ____ detection software automatically analyzes all network traffic, assesses system vulnerabilities, identifies any unauthorized access (intrusions), and notifies network administrators of suspicious behavior patterns or system breaches, including violations of firewalls like the ones in the accompanying figure.
____ detection software automatically analyzes all network traffic, assesses system vulnerabilities, identifies any unauthorized access (intrusions), and notifies network administrators of suspicious behavior patterns or system breaches, including violations of firewalls like the ones in the accompanying figure.A)Violation
B)Password
C)Intrusion
D)Traffic

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
8
 All networked and online computer users should implement a ____, like the one shown in the accompanying figure.
All networked and online computer users should implement a ____, like the one shown in the accompanying figure.A)firewall solution
B)back door
C)DoS attack
D)all of the above

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
9
A computer ____ risk is any event or action that could cause a loss of or damage to computer hardware, software, data, information, or processing capability.
A)security
B)liability
C)terrorism
D)network
A)security
B)liability
C)terrorism
D)network

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
10
____ is a server outside a company's network that controls which communications pass into the company's network.
A)A firewall
B)Intrusion detection software
C)A proxy server
D)An audit trail
A)A firewall
B)Intrusion detection software
C)A proxy server
D)An audit trail

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
11
A ____ is someone who uses e-mail as a vehicle for extortion.
A)hacker
B)script kiddie
C)cyberextortionist
D)cyberterrorist
A)hacker
B)script kiddie
C)cyberextortionist
D)cyberterrorist

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
12
A virus hoax often is in the form of a(n)____.
A)photo attachment
B)newsletter
C)chain letter
D)advertisement
A)photo attachment
B)newsletter
C)chain letter
D)advertisement

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
13
Which of the following is not true of intrusion detection software?
A)It is complex.
B)It is difficult to interpret.
C)It is inexpensive.
D)It is not designed for home use.
A)It is complex.
B)It is difficult to interpret.
C)It is inexpensive.
D)It is not designed for home use.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
14
A ____ is the destructive event or prank malware is intended to deliver.
A)payload
B)hoax
C)spoof
D)rebuke
A)payload
B)hoax
C)spoof
D)rebuke

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
15
The term ____ refers to online or Internet-based illegal acts.
A)malware
B)cyberthreat
C)cybercrime
D)cyberextortion
A)malware
B)cyberthreat
C)cybercrime
D)cyberextortion

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
16
All of the following are common ways computers become infected with malware, except ____.
A)opening infected files
B)running an infected program
C)booting the computer with infected removable media inserted in a drive or plugged in a port
D)installing a software package from a CD
A)opening infected files
B)running an infected program
C)booting the computer with infected removable media inserted in a drive or plugged in a port
D)installing a software package from a CD

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
17
A ____ has the same intent as a cracker but does not have the technical skills and knowledge.
A)hacker
B)script kiddie
C)cyberextortionist
D)cyberterrorist
A)hacker
B)script kiddie
C)cyberextortionist
D)cyberterrorist

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
18
 As shown in the accompanying figure, a ____ is hardware and/or software that protects a network's resources from intrusion by users on another network such as the Internet.
As shown in the accompanying figure, a ____ is hardware and/or software that protects a network's resources from intrusion by users on another network such as the Internet.A)quarantine
B)biometric device
C)firewall
D)router

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
19
Currently, more than ____ Web sites can infect your computer with known viruses, worms, Trojan horses, rootkits, and other malware programs.
A)11,000
B)22,000
C)151,000
D)300,000
A)11,000
B)22,000
C)151,000
D)300,000

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
20
Any illegal act involving a computer generally is referred to as a ____.
A)cyberthreat
B)computer crime
C)malware
D)hoax
A)cyberthreat
B)computer crime
C)malware
D)hoax

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
21
Social engineers can obtain information by ____.
A)snooping around computers looking for openly displayed confidential information
B)watching or filming people dialing telephone numbers or using ATMs
C)sifting through company dumpsters
D)all of the above
A)snooping around computers looking for openly displayed confidential information
B)watching or filming people dialing telephone numbers or using ATMs
C)sifting through company dumpsters
D)all of the above

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
22
 As shown in the accompanying figure, many Web sites require a user to enter a user ____, which is a unique combination of characters, such as letters of the alphabet or numbers, that identifies one specific user.
As shown in the accompanying figure, many Web sites require a user to enter a user ____, which is a unique combination of characters, such as letters of the alphabet or numbers, that identifies one specific user.A)term
B)link
C)name
D)key

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
23
Information ____ refers to the right of individuals and companies to deny or restrict the collection and use of information about them.
A)rights
B)acceptable use
C)restrictions
D)privacy
A)rights
B)acceptable use
C)restrictions
D)privacy

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
24
 If a password used on a site like the one shown in the accompanying figure is 4 characters long, the average time it would take a computer to discover the password is ____.
If a password used on a site like the one shown in the accompanying figure is 4 characters long, the average time it would take a computer to discover the password is ____.A)1 second
B)30 seconds
C)7 minutes
D)2 hours

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
25
 A(n)____ device, like the one in the accompanying figure, authenticates a person's identity by translating a personal characteristic, such as a fingerprint, into a digital code that then is compared with a digital code stored in the computer verifying a physical or behavioral characteristic.
A(n)____ device, like the one in the accompanying figure, authenticates a person's identity by translating a personal characteristic, such as a fingerprint, into a digital code that then is compared with a digital code stored in the computer verifying a physical or behavioral characteristic.A)authentication
B)personal
C)identification
D)biometric

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
26
Software ____ occurs when someone steals software media, intentionally erases programs, or illegally copies a program.
A)theft
B)extortion
C)piracy
D)terrorism
A)theft
B)extortion
C)piracy
D)terrorism

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
27
 As shown in the accompanying figure, many Web sites require a user to enter a ____, which is a private combination of characters associated with a user name that allows access to certain computer resources.
As shown in the accompanying figure, many Web sites require a user to enter a ____, which is a private combination of characters associated with a user name that allows access to certain computer resources.A)PIN
B)password
C)secure key
D)passterm

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
28
A ____ protector uses special electrical components to provide a stable current flow to the computer and other electronic equipment.
A)Joule
B)spike
C)surge
D)hash
A)Joule
B)spike
C)surge
D)hash

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
29
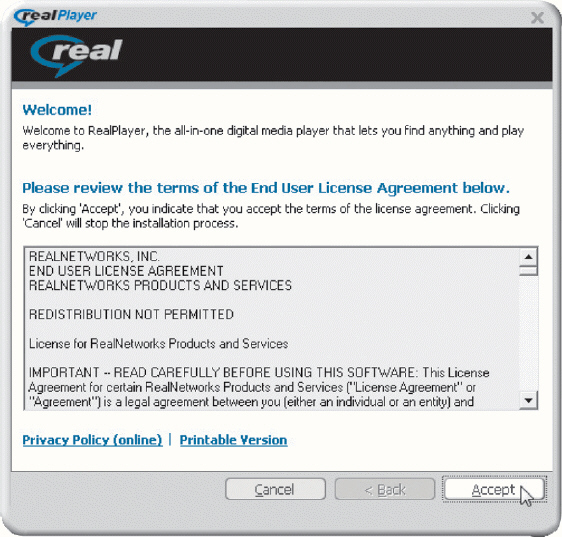 To protect themselves from software piracy, software manufacturers issue a(n)____ agreement like the one shown in the accompanying figure, which gives users the right to use the software.
To protect themselves from software piracy, software manufacturers issue a(n)____ agreement like the one shown in the accompanying figure, which gives users the right to use the software.A)intellectual property
B)license
C)access
D)copyright

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
30
____ occurs when someone steals personal or confidential information.
A)Plagiarism
B)Decryption
C)Information theft
D)Cyberpiracy
A)Plagiarism
B)Decryption
C)Information theft
D)Cyberpiracy

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
31
Which of the following is an example of a possessed object?
A)user name and password
B)face recognition systems
C)badges and keys
D)fingerprint scanner
A)user name and password
B)face recognition systems
C)badges and keys
D)fingerprint scanner

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
32
____ theft is the act of stealing computer equipment.
A)Hardware
B)Cyber
C)SMS
D)Software
A)Hardware
B)Cyber
C)SMS
D)Software

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
33
A(n)____ is an injury or disorder of the muscles, nerves, tendons, ligaments, and joints.
A)TSR
B)RSI
C)RIT
D)TRI
A)TSR
B)RSI
C)RIT
D)TRI

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
34
____ can lead to system failure.
A)Aging hardware
B)Natural disasters, such as fires, floods, or hurricanes
C)Errors in computer programs
D)All of the above
A)Aging hardware
B)Natural disasters, such as fires, floods, or hurricanes
C)Errors in computer programs
D)All of the above

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
35
Which of the following is not an example of a biometric device?
A)smart card
B)face recognition system
C)hand geometry system
D)fingerprint scanner
A)smart card
B)face recognition system
C)hand geometry system
D)fingerprint scanner

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
36
Computer ____ are the moral guidelines that govern the use of computers and information systems.
A)logistics
B)mechanics
C)ethics
D)rights
A)logistics
B)mechanics
C)ethics
D)rights

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
37
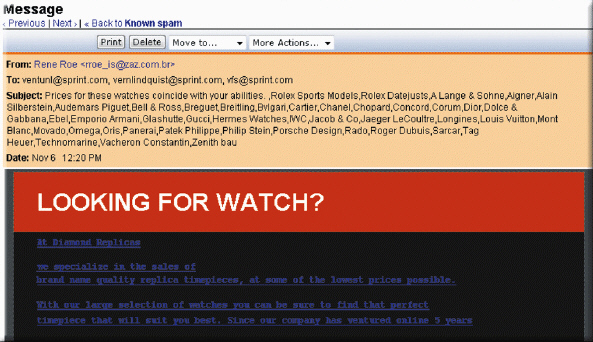 As shown in the accompanying figure, an unsolicited e-mail message or newsgroup posting sent to multiple recipients or newsgroups at once is called ____.
As shown in the accompanying figure, an unsolicited e-mail message or newsgroup posting sent to multiple recipients or newsgroups at once is called ____.A)spyware
B)spam
C)cookies
D)adware

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
38
Which method of encryption inserts characters between existing characters?
A)transposition
B)substitution
C)expansion
D)compaction
A)transposition
B)substitution
C)expansion
D)compaction

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
39
A(n)____ is the prolonged malfunction of a computer.
A)hardware vandalism
B)system failure
C)unauthorized access
D)software theft
A)hardware vandalism
B)system failure
C)unauthorized access
D)software theft

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
40
As related to the use of computers, ____ is defined as gaining unauthorized access or obtaining confidential information by taking advantage of the trusting human nature of some victims and the naivety of others.
A)DoS
B)social engineering
C)DRM
D)scamming
A)DoS
B)social engineering
C)DRM
D)scamming

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
41
Modified Multiple Choice Employee monitoring involves the use of computers to observe, record, and review an employee's ____.
A)e-mail messages
B)phone calls
C)keyboard activity
D)Web sites visited
A)e-mail messages
B)phone calls
C)keyboard activity
D)Web sites visited

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
42
Computer crime refers to online or Internet-based illegal acts.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
43
Shrink-wrapped software from major developers does not need to be scanned for infections.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
44
A digital certificate is an encrypted code attached to an electronic message to verify the identity of the message sender.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
45
Modified Multiple Choice Digital forensics analysis involves the examination of ____.
A)computer media
B)servers
C)data and log files
D)networks
A)computer media
B)servers
C)data and log files
D)networks

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
46
Once a Trojan horse is installed, its author can execute programs, change settings, monitor activity, and access files on the remote computer.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
47
Encrypted data is called plaintext.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
48

A fingerprint reader is an example of a biometric system, as shown in the accompanying figure.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
49
Modified Multiple Choice ____ is a category of perpetrator of cybercrime and other similar intrusions.
A)Hacker
B)Script kiddie
C)Cracker
D)Corporate spy
A)Hacker
B)Script kiddie
C)Cracker
D)Corporate spy

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
50

Most systems require that users select their own passwords, to be entered in forms such as the one shown in the accompanying figure.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
51
The substitution encryption method switches the order of characters.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
52
Most antivirus programs do not provide updated virus signature files for users.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
53
Modified Multiple Choice Intellectual property (IP)covers ____.
A)natural resources
B)art
C)ideas
D)processes
A)natural resources
B)art
C)ideas
D)processes

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
54
A cyberextortionist is someone who uses the Internet or a network to destroy or damage computers for political reasons.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
55
Modified Multiple Choice Adware is a program that displays an online advertisement in a banner or pop-up window on ____.
A)Telnet sessions
B)e-mail
C)Web pages
D)FTP transfers
A)Telnet sessions
B)e-mail
C)Web pages
D)FTP transfers

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
56
Companies should review successful access attempts for irregularities.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
57

Some operating systems, such as Windows, include personal firewalls, like the ones shown in the accompanying figure.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
58
The term, unauthorized access, refers to the use of a computer or its data for unapproved or possibly illegal activities.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
59
A DoS attack is a technique intruders use to make their network or Internet transmission appear legitimate to a victim computer or network.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
60
The term, cracker, originally was a complimentary word for a computer enthusiast.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
61
A(n)____________________ is a potentially damaging computer program that affects, or infects, a computer negatively by altering the way the computer works without the user's knowledge or permission.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
62
Physical access controls, such as locked doors and windows, usually are adequate to protect computer equipment from hardware theft.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
63
The term, ____________________, refers to online or Internet-based illegal acts.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
64
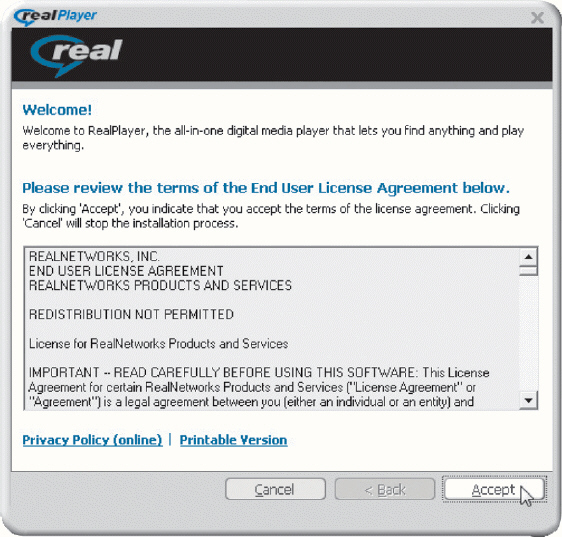
Software users with a EULA, like the one in the accompanying figure, may make as many backup copies of the software as they want.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
65
An encryption key often uses a combination of encryption methods.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
66
If computer equipment is networked, a single power disturbance can damage multiple systems.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
67
A(n)____________________ is a program that copies itself repeatedly, for example in memory or on a network, using up resources and possibly shutting down the computer or network.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
68
A(n)____________________ is a program that hides within or looks like a legitimate program.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
69
For visually impaired users, the CAPTCHA text can be read aloud.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
70
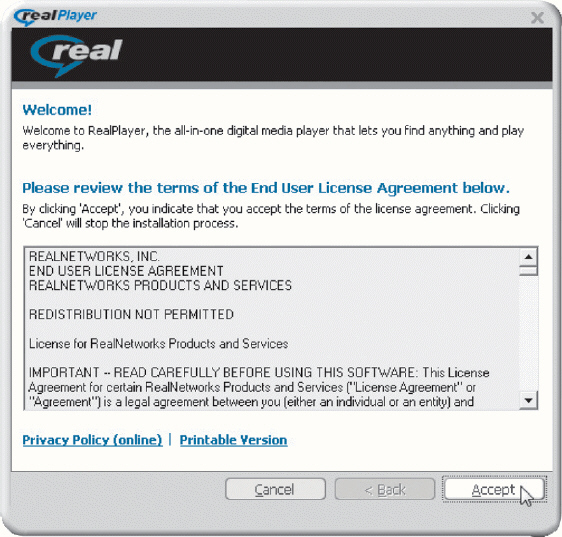
With a license agreement, like the one shown in the accompanying figure, the user becomes the owner of the software.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
71

If a shorter password were in use in the accompanying figure, it would provide greater security than a longer one.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
72
With a selective backup, users decide which folders and files to include in a backup.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
73

Hackers use computer automated tools to assist them with guessing passwords, like the one shown in the accompanying figure.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
74
Copyright law gives the public fair use to copyrighted material.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
75
Wireless access poses additional security risks.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
76
If you disable cookie use, you will not be able to use many of the e-commerce Web sites.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
77
A(n)____________________ is someone who accesses a computer or network illegally but has the intent of destroying data, stealing information, or other malicious action.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
78
To access a wireless network, perpetrators must be in the range of the wireless network.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
79
Electrical power variation is one of the least common causes of system failure.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
80
Spam is a program placed on a computer without the user's knowledge that secretly collects information about the user.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck



