Deck 4: Internal Controls and Risks in IT Systems
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/108
Play
Full screen (f)
Deck 4: Internal Controls and Risks in IT Systems
1
Which of the following is not a general control in an IT system:
A)Processing controls
B)Authentication of Users and Limiting Unauthorized Access
C)Establishment of an Organizational Structure
D)Physical Security of IT equipment
A)Processing controls
B)Authentication of Users and Limiting Unauthorized Access
C)Establishment of an Organizational Structure
D)Physical Security of IT equipment
A
2
The risk of an unauthorized user gaining access is likely to be a risk for which of the following areas?
A)Telecommuting workers
B)Internet
C)Wireless networks
D)All of the above
A)Telecommuting workers
B)Internet
C)Wireless networks
D)All of the above
D
3
Which programmed input validation check determines whether the appropriate type of data, either alphabetic or numeric, was entered?
A)Completeness check
B)Validity check
C)Rea
D)Field check
A)Completeness check
B)Validity check
C)Rea
D)Field check
D
4
Which programmed input validation makes sure that a value was entered in all of the critical fields?
A)Completeness check
B)Validity check
C)Rea
D)Field check
A)Completeness check
B)Validity check
C)Rea
D)Field check

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
5
The risk that an unauthorized user would shut down systems within the IT system is a(n):
A)Security risk
B)Availability risk
C)Processing integrity risk
D)Confidentiality risk
A)Security risk
B)Availability risk
C)Processing integrity risk
D)Confidentiality risk

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
6
Unchecked risks and threats to the IT system could result in:
A)An interruption of the computer operations
B)Damage to an organization
C)Incorrect or incomplete accounting information
D)All of the above
A)An interruption of the computer operations
B)Damage to an organization
C)Incorrect or incomplete accounting information
D)All of the above

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
7
An IT governance committee has several responsibilities.Which of the following is least likely to be a responsibility of the IT governance committee?
A)Develop and maintain the database and ensure adequate controls over the database.
B)Develop, monitor, and review security policies.
C)Oversee and prioritize changes to IT systems.
D)Align IT investments to business strategy.
A)Develop and maintain the database and ensure adequate controls over the database.
B)Develop, monitor, and review security policies.
C)Oversee and prioritize changes to IT systems.
D)Align IT investments to business strategy.

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
8
AICPA Trust Principles describe five categories of IT risks and controls.Which of these five categories would be described by the statement, "The system is protected against unauthorized access"?
A)Security
B)Confidentiality
C)Processing integrity
D)Availability
A)Security
B)Confidentiality
C)Processing integrity
D)Availability

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
9
In order to master risks and controls and how they fit together, which of the following is NOT one of the areas to fully understand?
A)The accounting information system
B)The description of the general and application controls that should exist in IT system
C)The type and nature of risks in IT systems
D)The recognition of how controls can be used to reduce risk
A)The accounting information system
B)The description of the general and application controls that should exist in IT system
C)The type and nature of risks in IT systems
D)The recognition of how controls can be used to reduce risk

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
10
A company has the following invoices in a batch: 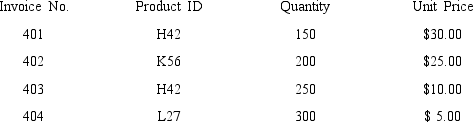 Which of the following numbers represents a valid record count?
Which of the following numbers represents a valid record count?
A)1
B)4
C)70
D)900
 Which of the following numbers represents a valid record count?
Which of the following numbers represents a valid record count?A)1
B)4
C)70
D)900

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
11
In entering client contact information in the computerized database of a telemarketing business, a clerk erroneously entered nonexistent area codes for a block of new clients.This error rendered the block of contacts useless to the company.Which of the following would most likely have led to discovery of this error into the company's computerized system?
A)Limit check
B)Validity check
C)Sequence check
D)Record count
A)Limit check
B)Validity check
C)Sequence check
D)Record count

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
12
Internal controls that apply overall to the IT accounting system, that are not restricted to any particular accounting application, are referred to as a(n):
A)Specific controls
B)Application controls
C)General controls
D)IT controls
A)Specific controls
B)Application controls
C)General controls
D)IT controls

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
13
All of the following are general controls except for:
A)Passwords
B)Physical hardware controls
C)
D)Inventory controls
A)Passwords
B)Physical hardware controls
C)
D)Inventory controls

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
14
Internal controls used specifically in accounting applications to control inputs, processing, and outputs are referred to as a(n):
A)Specific controls
B)Application controls
C)General controls
D)IT controls
A)Specific controls
B)Application controls
C)General controls
D)IT controls

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
15
Internal controls that apply overall to the IT system are called:
A)Overall Controls
B)Technology Controls
C)Application Controls
D)General Controls
A)Overall Controls
B)Technology Controls
C)Application Controls
D)General Controls

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
16
General controls are divided into five broad categories.Which of the following is not one of these categories?
A)Authentication of users and limiting unauthorized access
B)Hacking and other network break-ins
C)Fraud Prevention
D)Business Continuity
A)Authentication of users and limiting unauthorized access
B)Hacking and other network break-ins
C)Fraud Prevention
D)Business Continuity

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
17
Which of the following is not a control intended to authenticate users?
A)User logâ€"in
B)Security token
C)Encryption
D)Biometric devices
A)User logâ€"in
B)Security token
C)Encryption
D)Biometric devices

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
18
Which programmed input validation check compares the value in a field with related fields which determine whether the value is appropriate?
A)Completeness check
B)Validity check
C)Rea
D)Completeness check
A)Completeness check
B)Validity check
C)Rea
D)Completeness check

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
19
Management of an internet retail company is concerned about the possibility of computer data eavesdropping and wiretapping, and wants to maintain the confidentiality of its information as it is transmitted.The company should make use of:
A)Data encryption
B)Redundant servers
C)Input controls
D)Password codes
A)Data encryption
B)Redundant servers
C)Input controls
D)Password codes

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
20
Which control total is the total of field values that are added for control purposes, but not added for any other purpose?
A)Record count
B)Hash total
C)Batch total
D)Field total
A)Record count
B)Hash total
C)Batch total
D)Field total

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
21
Which of the following is not a good example of an effective password?
A)ABC*$123
B)a1b2c3
C)A*1b 2C$3
D)MSU#Rules$
A)ABC*$123
B)a1b2c3
C)A*1b 2C$3
D)MSU#Rules$

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
22
This term means that a user cannot deny any particular act that he or she did on the IT system:
A)Configuration
B)Proliferation
C)Verification
D)Nonrepudiation
A)Configuration
B)Proliferation
C)Verification
D)Nonrepudiation

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
23
Nonrepudiation means that:
A)A user is not authorized to change configuration settings.
B)A user is not allowed access to the authority tables.
C)A user can prevent the unauthorized flow of data in both directions.
D)A user cannot deny any particular act that he or she did on the IT system.
A)A user is not authorized to change configuration settings.
B)A user is not allowed access to the authority tables.
C)A user can prevent the unauthorized flow of data in both directions.
D)A user cannot deny any particular act that he or she did on the IT system.

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
24
All of the following are environmental control issues for physical hardware except for:
A)High temperatures
B)Fires
C)Excessive humidity
D)All of the above
E)None of the above
A)High temperatures
B)Fires
C)Excessive humidity
D)All of the above
E)None of the above

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
25
This item, that strengthens the use of passwords, is plugged into the computer's card reader and helps authenticate that the use is valid; it has an integrated circuit that displays a constantly changing ID code.These statement describe:
A)Security token
B)USB control key
C)Smart card
D)Biometrics
A)Security token
B)USB control key
C)Smart card
D)Biometrics

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
26
The use of the smart card or security tokens is referred to as a two factor authorization because:
A)It is based on
B)It requires that the user is granted the card / token in a secure environment and that the user actually uses the card / token.
C)It requires that the user has two different authorizations: (1) to receive the card / token, and (2) to use the card / token.
D)It requires the use the card / token to (1) login to the system and (2) access the applications.
A)It is based on
B)It requires that the user is granted the card / token in a secure environment and that the user actually uses the card / token.
C)It requires that the user has two different authorizations: (1) to receive the card / token, and (2) to use the card / token.
D)It requires the use the card / token to (1) login to the system and (2) access the applications.

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
27
Which of the following is not an example of physical characteristics being used in biometric devices?
A)Retina scans
B)Fingerprint matching
C)
D)Voice verification
A)Retina scans
B)Fingerprint matching
C)
D)Voice verification

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
28
Hardware, software, or a combination of both that is designed to block unauthorized access to an IT system is called:
A)Computer log
B)Biometric device
C)Firewall
D)Security token
A)Computer log
B)Biometric device
C)Firewall
D)Security token

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
29
This table contains a list of valid, authorized users and the access level granted to each one.
A)User table
B)Authority table
C)Authentication table
D)Configuration table
A)User table
B)Authority table
C)Authentication table
D)Configuration table

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
30
This type of authentication uses some unique physical characteristic of the user to identify the user and allow the appropriate access to the system.
A)Nonrepudiation card
B)Biometric device
C)Configuration table
D)Computer log
A)Nonrepudiation card
B)Biometric device
C)Configuration table
D)Computer log

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
31
There are a number of reasons that all access to an IT system be logged.Which of the following is not one of the reasons for the log to be maintained?
A)Any login or use abnormalities can be examined in more detail to determine any weaknesses in the login procedures.
B)A user cannot deny any particular act that he or she did on the system.
C)To establish nonrepudiation of sales transactions by a customer.
D)To establish a user profile.
A)Any login or use abnormalities can be examined in more detail to determine any weaknesses in the login procedures.
B)A user cannot deny any particular act that he or she did on the system.
C)To establish nonrepudiation of sales transactions by a customer.
D)To establish a user profile.

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
32
A new technology that is used to authenticate users is one that plugs into the USB port and eliminates the need for a card reader.This item is called a:
A)Biometric reader
B)Smart card
C)USB smart key
D)Security token
A)Biometric reader
B)Smart card
C)USB smart key
D)Security token

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
33
This term relates to making the computer recognize a user in order to create a connection at the beginning of the computer session.
A)User ID
B)Password
C)Smart card
D)Login
A)User ID
B)Password
C)Smart card
D)Login

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
34
The IT system includes this type of table for software, hardware, and application programs that contain the appropriate set-up and security settings.
A)Configuration table
B)Authentication table
C)User table
D)Authority table
A)Configuration table
B)Authentication table
C)User table
D)Authority table

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
35
This should be established for every authorized user and determines each user's access level to hardware, software, and data according to the individual's job responsibilities.
A)User profile
B)User password
C)User ID
D)User log
A)User profile
B)User password
C)User ID
D)User log

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
36
A process or procedure in an IT system to ensure that the person accessing the IT system is valid and authorized is called:
A)Hacking and other network break-ins
B)Physical environment and physical security
C)Authentication of users and limiting unauthorized access
D)Organizational structure
A)Hacking and other network break-ins
B)Physical environment and physical security
C)Authentication of users and limiting unauthorized access
D)Organizational structure

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
37
Which of the following is NOT one of the rules for the effective use of passwords?
A)Passwords should not be case sensitive
B)Passwords should be at least 8 characters in length
C)Passwords should contain at least one nonalphanumeric character.
D)Password should be changed every 90 days.
A)Passwords should not be case sensitive
B)Passwords should be at least 8 characters in length
C)Passwords should contain at least one nonalphanumeric character.
D)Password should be changed every 90 days.

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
38
The process of converting data into secret codes referred to cipher text is called:
A)Deciphering
B)Encryption
C)Nonrepudiation
D)Enciphering
A)Deciphering
B)Encryption
C)Nonrepudiation
D)Enciphering

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
39
A complete record of all dates, times, and uses for each person is referred to as a(n):
A)User password
B)Computer log
C)User profile
D)Configuration table
A)User password
B)Computer log
C)User profile
D)Configuration table

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
40
General controls in IT systems are divided into five broad categories.Which of the following is NOT one of those categories?
A)Authentication of uses and limiting unauthorized access
B)Output controls
C)Organization structure
D)Physical environment and physical security of the system.
A)Authentication of uses and limiting unauthorized access
B)Output controls
C)Organization structure
D)Physical environment and physical security of the system.

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
41
A self-replicating piece of program code that can attach itself to other programs and data and perform malicious actions is referred to as a(n):
A)Worm
B)Encryption
C)Virus
D)Infection
A)Worm
B)Encryption
C)Virus
D)Infection

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
42
The process of proactively examining the IT system for weaknesses that can be exploited by hackers, viruses, or malicious employees is called:
A)Intrusion detection
B)Virus management
C)Vulnerability assessment
D)Penetration testing
A)Intrusion detection
B)Virus management
C)Vulnerability assessment
D)Penetration testing

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
43
This encryption method, used with wireless network equipment, is symmetric in that both the sending and receiving network nodes must use the same encryption key.It has been proven to be susceptible to hacking.
A)Wired Equivalency Privacy (WEP)
B)Wired Encryption Policy (WEP)
C)Wireless Protection Access (WPA)
D)Wired Privacy Authentication (WPA)
A)Wired Equivalency Privacy (WEP)
B)Wired Encryption Policy (WEP)
C)Wireless Protection Access (WPA)
D)Wired Privacy Authentication (WPA)

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
44
The IT Governance Committee has several important responsibilities.Which of the following is not normally one of those responsibilities?
A)Align IT investments to business strategies
B)Oversee and prioritize changes to IT systems
C)Develop, monitor, and review security procedures
D)Investing excess IT funds in long-term investments
A)Align IT investments to business strategies
B)Oversee and prioritize changes to IT systems
C)Develop, monitor, and review security procedures
D)Investing excess IT funds in long-term investments

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
45
This form of encryption uses a public key, which is known by everyone, to encrypt data, and a private key, to decode the data.
A)Multiple encryption
B)Public key encryption
C)Wired encryption
D)Symmetric encryption
A)Multiple encryption
B)Public key encryption
C)Wired encryption
D)Symmetric encryption

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
46
This encryption method requests connection to the network via an access point and that point then requests the use identity and transmits that identity to an authentication server, substantially authenticating the computer and the user.
A)Wired Equivalency Privacy (WEP)
B)Wired Encryption Provider (WEP)
C)Wireless Provider Authentication (WPA)
D)Wireless Protection Access (WPA)
A)Wired Equivalency Privacy (WEP)
B)Wired Encryption Provider (WEP)
C)Wireless Provider Authentication (WPA)
D)Wireless Protection Access (WPA)

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
47
This communication protocol is built into web server and browser software that encrypts data transferred on that website.You can determine if a website uses this technology by looking at the URL.
A)Secure
B)Service security line
C)Secure encryption network
D)Secure service layer
A)Secure
B)Service security line
C)Secure encryption network
D)Secure service layer

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
48
The type of network uses tunnels, authentication, and encryption within the Internet network to isolate Internet communications so that unauthorized users cannot access or use certain data.
A)Residential user network
B)Service internet parameter network
C)Virtual private network
D)Virtual public network
A)Residential user network
B)Service internet parameter network
C)Virtual private network
D)Virtual public network

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
49
This form of encryption uses a single encryption key that must be used to encrypt data and also to decode the encrypted data.
A)Multiple encryption
B)Public key encryption
C)Wired encryption
D)Symmetric encryption
A)Multiple encryption
B)Public key encryption
C)Wired encryption
D)Symmetric encryption

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
50
This security feature, used on wireless networks, is a password that is passed between the sending and receiving nodes of a wireless network.
A)Secure
B)Service set identifier
C)Wired provided access
D)Virtual private network
A)Secure
B)Service set identifier
C)Wired provided access
D)Virtual private network

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
51
Which of the following URL's would indicate that the site is using browser software that encrypts data transferred to the website?
A)shttp://misu
B)https://misu
C)http://smisus
D)http.s://smisus
A)shttp://misu
B)https://misu
C)http://smisus
D)http.s://smisus

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
52
A small piece of program code that attaches to the computer's unused memory space and replicates itself until the system becomes overloaded and shuts down is called:
A)Infections
B)Virus
C)Serum
D)Worm
A)Infections
B)Virus
C)Serum
D)Worm

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
53
The process of legitimately attempting to hack into an IT system to find whether weaknesses can be exploited by unauthorized hackers is referred to as:
A)Vulnerability assessment
B)Intrusion detection
C)Penetration testing
D)Worm detection
A)Vulnerability assessment
B)Intrusion detection
C)Penetration testing
D)Worm detection

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
54
This method of monitoring exposure can involve either manual testing or automated software tools.The method can identify weaknesses before they become network break-ins and attempt to fix these weaknesses before they are exploited.
A)Vulnerability assessment
B)Intrusion detection
C)Encryption examination
D)Penetration testing
A)Vulnerability assessment
B)Intrusion detection
C)Encryption examination
D)Penetration testing

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
55
Authorized employees may need to access the company IT system from locations outside the organization.These employees should connect to the IT system using this type of network.
A)Secure
B)Service set identifier
C)Virtual private network
D)Wireless encryption portal
A)Secure
B)Service set identifier
C)Virtual private network
D)Wireless encryption portal

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
56
The function of this committee is to govern the overall development and operation of IT systems.
A)IT Budget Committee
B)IT Audit Committee
C)IT Governance Committee
D)IT Oversight Committee
A)IT Budget Committee
B)IT Audit Committee
C)IT Governance Committee
D)IT Oversight Committee

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
57
This type of software should be used to avoid destruction of data programs and to maintain operation of the IT system.It continually scans the system for viruses and worms and either deletes or quarantines them.
A)Penicillin
B)Antivirus
C)Infection
D)Internet
A)Penicillin
B)Antivirus
C)Infection
D)Internet

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
58
Specific software tools that monitor data flow within a network and alert the IT staff to hacking attempts or other unauthorized access attempts is called:
A)Security detection
B)Vulnerability assessment
C)Penetration testing
D)Intrusion detection
A)Security detection
B)Vulnerability assessment
C)Penetration testing
D)Intrusion detection

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
59
The functional responsibilities within an IT system must include the proper segregation of duties.Which of the following positions is not one of the duties that is to be segregated from the others?
A)Systems analysts
B)Chief information officer
C)Database administrator
D)Operations per
A)Systems analysts
B)Chief information officer
C)Database administrator
D)Operations per

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
60
Which of the following would normally not be found on the IT Governance Committee?
A)Computer input operators
B)Chief Executive Officer
C)Chief Information Officer
D)Heads of business units
A)Computer input operators
B)Chief Executive Officer
C)Chief Information Officer
D)Heads of business units

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
61
Unauthorized access to the operating system would allow the unauthorized user to:
A)Browse disk files for sensitive data or passwords
B)Alter data through the operating system
C)Alter application programs
D)All of the above
A)Browse disk files for sensitive data or passwords
B)Alter data through the operating system
C)Alter application programs
D)All of the above

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
62
The AICPA Trust Services Principles categorizes IT controls and risks into categories.Which of the following is not one of those categories?
A)Confidentiality
B)Security
C)Recovery
D)Availability
A)Confidentiality
B)Security
C)Recovery
D)Availability

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
63
A group of LANs connected to each other to cover a wider geographic area is called a:
A)Connected local network
B)Wide area network
C)Connected wide area
D)Wide geographic network
A)Connected local network
B)Wide area network
C)Connected wide area
D)Wide geographic network

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
64
Two or more computer network or data servers that can run identical processes or maintain the same data are called:
A)Emergency power supply
B)Uninterruptible power
C)Redundant servers
D)Business continuity planning
A)Emergency power supply
B)Uninterruptible power
C)Redundant servers
D)Business continuity planning

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
65
A computer network covering a small geographic area, which, in most cases, are within a single building or a local group of buildings is called a:
A)Land area network
B)Local access network
C)Local area network
D)Locality arena network
A)Land area network
B)Local access network
C)Local area network
D)Locality arena network

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
66
A proactive program for considering risks to the business continuation and the development of plans and procedures to reduce those risks is referred to as:
A)Redundant business planning
B)Business continuity planning
C)Unnecessary in the current safe environments
D)Emergency backup power
A)Redundant business planning
B)Business continuity planning
C)Unnecessary in the current safe environments
D)Emergency backup power

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
67
The accuracy, completeness, and timeliness of the process in IT systems is referred to as:
A)Availability Risks
B)Security Risks
C)Confidentiality Risks
D)Processing Integrity Risks
A)Availability Risks
B)Security Risks
C)Confidentiality Risks
D)Processing Integrity Risks

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
68
Examples of Business Continuity include all of the following except:
A)Disaster Recovery Plan
B)Backup Data
C)Environmental Backup Recovery Plan
D)Offsite Backup
A)Disaster Recovery Plan
B)Backup Data
C)Environmental Backup Recovery Plan
D)Offsite Backup

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
69
The work arrangement where employees work from home using some type of network connection to the office is referred to as:
A)Telecommuting
B)Telemarketing
C)Network Employment
D)Electronic working
A)Telecommuting
B)Telemarketing
C)Network Employment
D)Electronic working

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
70
The establishment of log-in procedures can help prevent or lessen security risks and are referred to as:
A)Reactive controls
B)Preventive controls
C)Availability controls
D)Confidentiality controls
A)Reactive controls
B)Preventive controls
C)Availability controls
D)Confidentiality controls

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
71
The systematic steps undertaken to plan, prioritize, authorize, oversee, test, and implement large-scale changes to the IT system are called:
A)IT Governance System
B)Operations Governance
C)System Development Life Cycle
D)Systems Analysis
A)IT Governance System
B)Operations Governance
C)System Development Life Cycle
D)Systems Analysis

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
72
Availability risks, related to the authentication of users would include:
A)Shutting down the system and shutting down programs
B)Altering data and repudiating transactions
C)Stealing data and recording nonexistent transactions
D)Sabotaging systems and destroying data
A)Shutting down the system and shutting down programs
B)Altering data and repudiating transactions
C)Stealing data and recording nonexistent transactions
D)Sabotaging systems and destroying data

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
73
A software system that manages the interface between many users and the database is called:
A)Database security system
B)Database management system
C)Database binary monetary system
D)Database assessment
A)Database security system
B)Database management system
C)Database binary monetary system
D)Database assessment

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
74
A battery to maintain power in the event of a power outage meant to keep the computer running for several minutes after the power outage is an example of a(n):
A)Uninterruptible power supply
B)System power supply
C)Emergency power supply
D)Battery power supply
A)Uninterruptible power supply
B)System power supply
C)Emergency power supply
D)Battery power supply

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
75
An alternative power supply that provides electrical power in the event that a main source is lost is called:
A)Uninterruptible power supply
B)System power supply
C)Emergency power supply
D)Battery power supply
A)Uninterruptible power supply
B)System power supply
C)Emergency power supply
D)Battery power supply

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
76
A large disk storage for accounting and operating data is referred to as a(n):
A)Operating system
B)Application
C)Database
D)Binary monetary system
A)Operating system
B)Application
C)Database
D)Binary monetary system

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
77
General controls for an IT system include:
A)Controls over the physical environment only
B)Controls over the physical access only
C)Controls over the physical environment and over the physical access
D)None of the above
A)Controls over the physical environment only
B)Controls over the physical access only
C)Controls over the physical environment and over the physical access
D)None of the above

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
78
Large-scale IT systems should be protected by physical access controls.Which of the following is not listed as one of those controls?
A)Limited access to computer rooms
B)Video surveillance equipment
C)Locked storage of backup data
D)Encryption of passwords
A)Limited access to computer rooms
B)Video surveillance equipment
C)Locked storage of backup data
D)Encryption of passwords

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
79
The software that controls the basic input and output activities of the computer are called:
A)Operating System
B)Application
C)Data Base Management System
D)Electronic Data Interchange
A)Operating System
B)Application
C)Data Base Management System
D)Electronic Data Interchange

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck
80
Many IT systems have redundant data storage such that two or more disks are exact mirror images.This is accomplished by the use of:
A)Redundant arrays of independent disks
B)Redundant mirror image disks
C)Mirror image independent disks
D)Redundant mirror image dependent disks
A)Redundant arrays of independent disks
B)Redundant mirror image disks
C)Mirror image independent disks
D)Redundant mirror image dependent disks

Unlock Deck
Unlock for access to all 108 flashcards in this deck.
Unlock Deck
k this deck



