Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/442
Play
Full screen (f)
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
1
An internal penetration tester was assessing a recruiting page for potential issues before it was pushed to the production website. The penetration tester discovers an issue that must be corrected before the page goes live. The web host administrator collects the log files below and gives them to the development team so improvements can be made to the security design of the website. 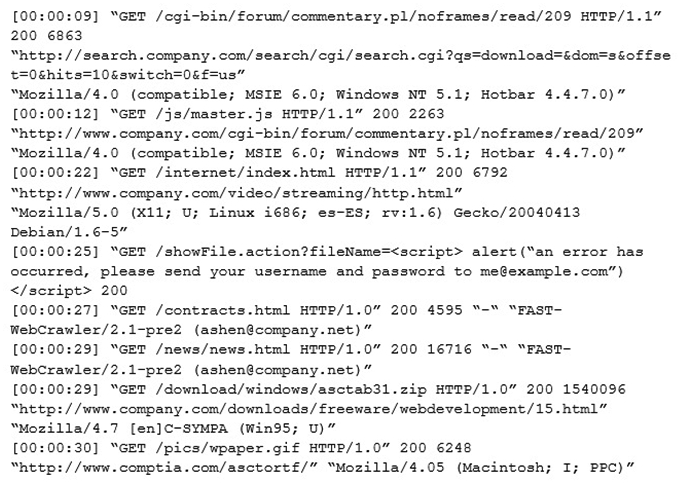 Which of the following types of attack vector did the penetration tester use?
Which of the following types of attack vector did the penetration tester use?
A) SQL injection
B) CSRF
C) Brute force
D) XSS
E) TOC/TOU
 Which of the following types of attack vector did the penetration tester use?
Which of the following types of attack vector did the penetration tester use?A) SQL injection
B) CSRF
C) Brute force
D) XSS
E) TOC/TOU
CSRF
2
A company has hired an external security consultant to conduct a thorough review of all aspects of corporate security. The company is particularly concerned about unauthorized access to its physical offices resulting in network compromises. Which of the following should the consultant recommend be performed to evaluate potential risks?
A) The consultant should attempt to gain access to physical offices through social engineering and then attempt data exfiltration
B) The consultant should be granted access to all physical access control systems to review logs and evaluate the likelihood of the threat
C) The company should conduct internal audits of access logs and employee social media feeds to identify potential insider threats
D) The company should install a temporary CCTV system to detect unauthorized access to physical offices
A) The consultant should attempt to gain access to physical offices through social engineering and then attempt data exfiltration
B) The consultant should be granted access to all physical access control systems to review logs and evaluate the likelihood of the threat
C) The company should conduct internal audits of access logs and employee social media feeds to identify potential insider threats
D) The company should install a temporary CCTV system to detect unauthorized access to physical offices
The consultant should attempt to gain access to physical offices through social engineering and then attempt data exfiltration
3
An infrastructure team is at the end of a procurement process and has selected a vendor. As part of the final negotiations, there are a number of outstanding issues, including: 1. Indemnity clauses have identified the maximum liability 2. The data will be hosted and managed outside of the company's geographical location The number of users accessing the system will be small, and no sensitive data will be hosted in the solution. As the security consultant on the project, which of the following should the project's security consultant recommend as the NEXT step?
A) Develop a security exemption, as it does not meet the security policies
B) Mitigate the risk by asking the vendor to accept the in-country privacy principles
C) Require the solution owner to accept the identified risks and consequences
D) Review the entire procurement process to determine the lessons learned
A) Develop a security exemption, as it does not meet the security policies
B) Mitigate the risk by asking the vendor to accept the in-country privacy principles
C) Require the solution owner to accept the identified risks and consequences
D) Review the entire procurement process to determine the lessons learned
Require the solution owner to accept the identified risks and consequences
4
A financial consulting firm recently recovered from some damaging incidents that were associated with malware installed via rootkit. Post-incident analysis is ongoing, and the incident responders and systems administrators are working to determine a strategy to reduce the risk of recurrence. The firm's systems are running modern operating systems and feature UEFI and TPMs. Which of the following technical options would provide the MOST preventive value?
A) Update and deploy GPOs
B) Configure and use measured boot
C) Strengthen the password complexity requirements
D) Update the antivirus software and definitions
A) Update and deploy GPOs
B) Configure and use measured boot
C) Strengthen the password complexity requirements
D) Update the antivirus software and definitions

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
5
A recent penetration test identified that a web server has a major vulnerability. The web server hosts a critical shipping application for the company and requires 99.99% availability. Attempts to fix the vulnerability would likely break the application. The shipping application is due to be replaced in the next three months. Which of the following would BEST secure the web server until the replacement web server is ready?
A) Patch management
B) Antivirus
C) Application firewall
D) Spam filters
E) HIDS
A) Patch management
B) Antivirus
C) Application firewall
D) Spam filters
E) HIDS

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
6
A systems security engineer is assisting an organization's market survey team in reviewing requirements for an upcoming acquisition of mobile devices. The engineer expresses concerns to the survey team about a particular class of devices that uses a separate SoC for baseband radio I/O. For which of the following reasons is the engineer concerned?
A) These devices can communicate over networks older than HSPA+ and LTE standards, exposing device communications to poor encryptions routines
B) The organization will be unable to restrict the use of NFC, electromagnetic induction, and Bluetooth technologies
C) The associated firmware is more likely to remain out of date and potentially vulnerable
D) The manufacturers of the baseband radios are unable to enforce mandatory access controls within their driver set
A) These devices can communicate over networks older than HSPA+ and LTE standards, exposing device communications to poor encryptions routines
B) The organization will be unable to restrict the use of NFC, electromagnetic induction, and Bluetooth technologies
C) The associated firmware is more likely to remain out of date and potentially vulnerable
D) The manufacturers of the baseband radios are unable to enforce mandatory access controls within their driver set

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
7
The Chief Information Security Officer (CISO) for an organization wants to develop custom IDS rulesets faster, prior to new rules being released by IDS vendors. Which of the following BEST meets this objective?
A) Identify a third-party source for IDS rules and change the configuration on the applicable IDSs to pull in the new rulesets
B) Encourage cybersecurity analysts to review open-source intelligence products and threat database to generate new IDS rules based on those sources
C) Leverage the latest TCP- and UDP-related RFCs to arm sensors and IDSs with appropriate heuristics for anomaly detection
D) Use annual hacking conventions to document the latest attacks and threats, and then develop IDS rules to counter those threats
A) Identify a third-party source for IDS rules and change the configuration on the applicable IDSs to pull in the new rulesets
B) Encourage cybersecurity analysts to review open-source intelligence products and threat database to generate new IDS rules based on those sources
C) Leverage the latest TCP- and UDP-related RFCs to arm sensors and IDSs with appropriate heuristics for anomaly detection
D) Use annual hacking conventions to document the latest attacks and threats, and then develop IDS rules to counter those threats

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
8
A user workstation was infected with a new malware variant as a result of a drive-by download. The security administrator reviews key controls on the infected workstation and discovers the following: 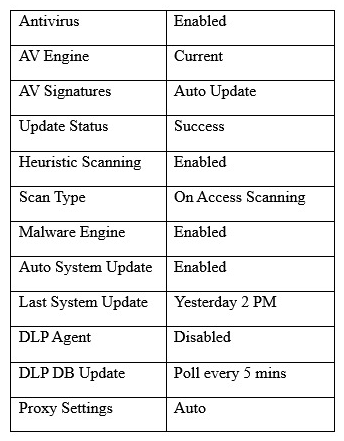 Which of the following would BEST prevent the problem from reoccurring in the future? (Choose two.)
Which of the following would BEST prevent the problem from reoccurring in the future? (Choose two.)
A) Install HIPS
B) Enable DLP
C) Install EDR
D) Install HIDS
E) Enable application blacklisting
F) Improve patch management processes
 Which of the following would BEST prevent the problem from reoccurring in the future? (Choose two.)
Which of the following would BEST prevent the problem from reoccurring in the future? (Choose two.)A) Install HIPS
B) Enable DLP
C) Install EDR
D) Install HIDS
E) Enable application blacklisting
F) Improve patch management processes

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
9
An organization is in the process of integrating its operational technology and information technology areas. As part of the integration, some of the cultural aspects it would like to see include more efficient use of resources during change windows, better protection of critical infrastructure, and the ability to respond to incidents. The following observations have been identified: The ICS supplier has specified that any software installed will result in lack of support. There is no documented trust boundary defined between the SCADA and corporate networks. Operational technology staff have to manage the SCADA equipment via the engineering workstation. There is a lack of understanding of what is within the SCADA network. Which of the following capabilities would BEST improve the security position?
A) VNC, router, and HIPS
B) SIEM, VPN, and firewall
C) Proxy, VPN, and WAF
D) IDS, NAC, and log monitoring
A) VNC, router, and HIPS
B) SIEM, VPN, and firewall
C) Proxy, VPN, and WAF
D) IDS, NAC, and log monitoring

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
10
During a security assessment, an organization is advised of inadequate control over network segmentation. The assessor explains that the organization's reliance on VLANs to segment traffic is insufficient to provide segmentation based on regulatory standards. Which of the following should the organization consider implementing along with VLANs to provide a greater level of segmentation?
A) Air gaps
B) Access control lists
C) Spanning tree protocol
D) Network virtualization
E) Elastic load balancing
A) Air gaps
B) Access control lists
C) Spanning tree protocol
D) Network virtualization
E) Elastic load balancing

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
11
To prepare for an upcoming audit, the Chief Information Security Officer (CISO) asks for all 1200 vulnerabilities on production servers to be remediated. The security engineer must determine which vulnerabilities represent real threats that can be exploited so resources can be prioritized to migrate the most dangerous risks. The CISO wants the security engineer to act in the same manner as would an external threat, while using vulnerability scan results to prioritize any actions. Which of the following approaches is described?
A) Blue team
B) Red team
C) Black box
D) White team
A) Blue team
B) Red team
C) Black box
D) White team

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
12
A security incident responder discovers an attacker has gained access to a network and has overwritten key system files with backdoor software. The server was reimaged and patched offline. Which of the following tools should be implemented to detect similar attacks?
A) Vulnerability scanner
B) TPM
C) Host-based firewall
D) File integrity monitor
E) NIPS
A) Vulnerability scanner
B) TPM
C) Host-based firewall
D) File integrity monitor
E) NIPS

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
13
An insurance company has two million customers and is researching the top transactions on its customer portal. It identifies that the top transaction is currently password reset. Due to users not remembering their secret questions, a large number of calls are consequently routed to the contact center for manual password resets. The business wants to develop a mobile application to improve customer engagement in the future, continue with a single factor of authentication, minimize management overhead of the solution, remove passwords, and eliminate to the contact center. Which of the following techniques would BEST meet the requirements? (Choose two.)
A) Magic link sent to an email address
B) Customer ID sent via push notification
C) SMS with OTP sent to a mobile number
D) Third-party social login
E) Certificate sent to be installed on a device
F) Hardware tokens sent to customers
A) Magic link sent to an email address
B) Customer ID sent via push notification
C) SMS with OTP sent to a mobile number
D) Third-party social login
E) Certificate sent to be installed on a device
F) Hardware tokens sent to customers

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
14
A server (10.0.0.2) on the corporate network is experiencing a DoS from a number of marketing desktops that have been compromised and are connected to a separate network segment. The security engineer implements the following configuration on the management router: 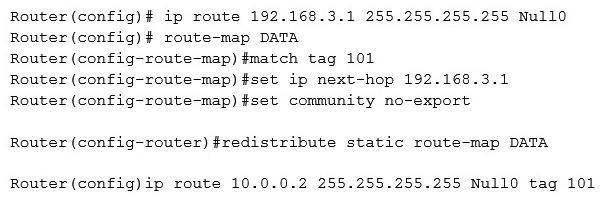 Which of the following is the engineer implementing?
Which of the following is the engineer implementing?
A) Remotely triggered black hole
B) Route protection
C) Port security
D) Transport security
E) Address space layout randomization
 Which of the following is the engineer implementing?
Which of the following is the engineer implementing?A) Remotely triggered black hole
B) Route protection
C) Port security
D) Transport security
E) Address space layout randomization

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
15
An organization has employed the services of an auditing firm to perform a gap assessment in preparation for an upcoming audit. As part of the gap assessment, the auditor supporting the assessment recommends the organization engage with other industry partners to share information about emerging attacks to organizations in the industry in which the organization functions. Which of the following types of information could be drawn from such participation?
A) Threat modeling
B) Risk assessment
C) Vulnerability data
D) Threat intelligence
E) Risk metrics
F) Exploit frameworks
A) Threat modeling
B) Risk assessment
C) Vulnerability data
D) Threat intelligence
E) Risk metrics
F) Exploit frameworks

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
16
One of the objectives of a bank is to instill a security awareness culture. Which of the following are techniques that could help to achieve this? (Choose two.)
A) Blue teaming
B) Phishing simulations
C) Lunch-and-learn
D) Random audits
E) Continuous monitoring
F) Separation of duties
A) Blue teaming
B) Phishing simulations
C) Lunch-and-learn
D) Random audits
E) Continuous monitoring
F) Separation of duties

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
17
A company monitors the performance of all web servers using WMI. A network administrator informs the security engineer that web servers hosting the company's client-facing portal are running slowly today. After some investigation, the security engineer notices a large number of attempts at enumerating host information via SNMP from multiple IP addresses. Which of the following would be the BEST technique for the security engineer to employ in an attempt to prevent reconnaissance activity?
A) Install a HIPS on the web servers
B) Disable inbound traffic from offending sources
C) Disable SNMP on the web servers
D) Install anti-DDoS protection in the DMZ
A) Install a HIPS on the web servers
B) Disable inbound traffic from offending sources
C) Disable SNMP on the web servers
D) Install anti-DDoS protection in the DMZ

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
18
A company has entered into a business agreement with a business partner for managed human resources services. The Chief Information Security Officer (CISO) has been asked to provide documentation that is required to set up a business-to-business VPN between the two organizations. Which of the following is required in this scenario?
A) ISA
B) BIA
C) SLA
D) RA
A) ISA
B) BIA
C) SLA
D) RA

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
19
A Chief Information Security Officer (CISO) is reviewing the results of a gap analysis with an outside cybersecurity consultant. The gap analysis reviewed all procedural and technical controls and found the following: High-impact controls implemented: 6 out of 10 Medium-impact controls implemented: 409 out of 472 Low-impact controls implemented: 97 out of 1000 The report includes a cost-benefit analysis for each control gap. The analysis yielded the following information: Average high-impact control implementation cost: $15,000; Probable ALE for each high-impact control gap: $95,000 Average medium-impact control implementation cost: $6,250; Probable ALE for each medium-impact control gap: $11,000 Due to the technical construction and configuration of the corporate enterprise, slightly more than 50% of the medium-impact controls will take two years to fully implement. Which of the following conclusions could the CISO draw from the analysis?
A) Too much emphasis has been placed on eliminating low-risk vulnerabilities in the past
B) The enterprise security team has focused exclusively on mitigating high-level risks
C) Because of the significant ALE for each high-risk vulnerability, efforts should be focused on those controls
D) The cybersecurity team has balanced residual risk for both high and medium controls
A) Too much emphasis has been placed on eliminating low-risk vulnerabilities in the past
B) The enterprise security team has focused exclusively on mitigating high-level risks
C) Because of the significant ALE for each high-risk vulnerability, efforts should be focused on those controls
D) The cybersecurity team has balanced residual risk for both high and medium controls

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
20
A security analyst is reviewing the corporate MDM settings and notices some disabled settings, which consequently permit users to download programs from untrusted developers and manually install them. After some conversations, it is confirmed that these settings were disabled to support the internal development of mobile applications. The security analyst is now recommending that developers and testers have a separate device profile allowing this, and that the rest of the organization's users do not have the ability to manually download and install untrusted applications. Which of the following settings should be toggled to achieve the goal? (Choose two.)
A) OTA updates
B) Remote wiping
C) Side loading
D) Sandboxing
E) Containerization
F) Signed applications
A) OTA updates
B) Remote wiping
C) Side loading
D) Sandboxing
E) Containerization
F) Signed applications

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
21
The board of a financial services company has requested that the senior security analyst acts as a cybersecurity advisor in order to comply with recent federal legislation. The analyst is required to give a report on current cybersecurity and threat trends in the financial services industry at the next board meeting. Which of the following would be the BEST methods to prepare this report? (Choose two.)
A) Review the CVE database for critical exploits over the past year
B) Use social media to contact industry analysts
C) Use intelligence gathered from the Internet relay chat channels
D) Request information from security vendors and government agencies
E) Perform a penetration test of the competitor's network and share the results with the board
A) Review the CVE database for critical exploits over the past year
B) Use social media to contact industry analysts
C) Use intelligence gathered from the Internet relay chat channels
D) Request information from security vendors and government agencies
E) Perform a penetration test of the competitor's network and share the results with the board

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
22
Management is reviewing the results of a recent risk assessment of the organization's policies and procedures. During the risk assessment it is determined that procedures associated with background checks have not been effectively implemented. In response to this risk, the organization elects to revise policies and procedures related to background checks and use a third-party to perform background checks on all new employees. Which of the following risk management strategies has the organization employed?
A) Transfer
B) Mitigate
C) Accept
D) Avoid
E) Reject
A) Transfer
B) Mitigate
C) Accept
D) Avoid
E) Reject

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
23
A software development team has spent the last 18 months developing a new web-based front-end that will allow clients to check the status of their orders as they proceed through manufacturing. The marketing team schedules a launch party to present the new application to the client base in two weeks. Before the launch, the security team discovers numerous flaws that may introduce dangerous vulnerabilities, allowing direct access to a database used by manufacturing. The development team did not plan to remediate these vulnerabilities during development. Which of the following SDLC best practices should the development team have followed?
A) Implementing regression testing
B) Completing user acceptance testing
C) Verifying system design documentation
D) Using a SRTM
A) Implementing regression testing
B) Completing user acceptance testing
C) Verifying system design documentation
D) Using a SRTM

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
24
A company wants to perform analysis of a tool that is suspected to contain a malicious payload. A forensic analyst is given the following snippet: ^32^[34fda19(fd^43gfd/home / user/lib/module.so.343jk^rfw(342fds43g Which of the following did the analyst use to determine the location of the malicious payload?
A) Code deduplicators
B) Binary reverse-engineering
C) Fuzz testing
D) Security containers
A) Code deduplicators
B) Binary reverse-engineering
C) Fuzz testing
D) Security containers

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
25
Legal authorities notify a company that its network has been compromised for the second time in two years. The investigation shows the attackers were able to use the same vulnerability on different systems in both attacks. Which of the following would have allowed the security team to use historical information to protect against the second attack?
A) Key risk indicators
B) Lessons learned
C) Recovery point objectives
D) Tabletop exercise
A) Key risk indicators
B) Lessons learned
C) Recovery point objectives
D) Tabletop exercise

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
26
A SaaS-based email service provider often receives reports from legitimate customers that their IP netblocks are on blacklists and they cannot send email. The SaaS has confirmed that affected customers typically have IP addresses within broader network ranges and some abusive customers within the same IP ranges may have performed spam campaigns. Which of the following actions should the SaaS provider perform to minimize legitimate customer impact?
A) Inform the customer that the service provider does not have any control over third-party blacklist entries. The customer should reach out to the blacklist operator directly
B) Perform a takedown of any customer accounts that have entries on email blacklists because this is a strong indicator of hostile behavior
C) Work with the legal department and threaten legal action against the blacklist operator if the netblocks are not removed because this is affecting legitimate traffic
D) Establish relationship with a blacklist operators so broad entries can be replaced with more granular entries and incorrect entries can be quickly pruned
A) Inform the customer that the service provider does not have any control over third-party blacklist entries. The customer should reach out to the blacklist operator directly
B) Perform a takedown of any customer accounts that have entries on email blacklists because this is a strong indicator of hostile behavior
C) Work with the legal department and threaten legal action against the blacklist operator if the netblocks are not removed because this is affecting legitimate traffic
D) Establish relationship with a blacklist operators so broad entries can be replaced with more granular entries and incorrect entries can be quickly pruned

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
27
A web developer has implemented HTML5 optimizations into a legacy web application. One of the modifications the web developer made was the following client side optimization: localStorage.setItem("session-cookie", document.cookie); Which of the following should the security engineer recommend?
A) SessionStorage should be used so authorized cookies expire after the session ends
B) Cookies should be marked as "secure" and "HttpOnly"
C) Cookies should be scoped to a relevant domain/path
D) Client-side cookies should be replaced by server-side mechanisms
A) SessionStorage should be used so authorized cookies expire after the session ends
B) Cookies should be marked as "secure" and "HttpOnly"
C) Cookies should be scoped to a relevant domain/path
D) Client-side cookies should be replaced by server-side mechanisms

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
28
The Chief Information Security Officer (CISO) has asked the security team to determine whether the organization is susceptible to a zero-day exploit utilized in the banking industry and whether attribution is possible. The CISO has asked what process would be utilized to gather the information, and then wants to apply signatureless controls to stop these kinds of attacks in the future. Which of the following are the MOST appropriate ordered steps to take to meet the CISO's request?
A) 1. Perform the ongoing research of the best practices 2. Determine current vulnerabilities and threats 3. Apply Big Data techniques 4. Use antivirus control
B) 1. Apply artificial intelligence algorithms for detection 2. Inform the CERT team 3. Research threat intelligence and potential adversaries 4. Utilize threat intelligence to apply Big Data techniques
C) 1. Obtain the latest IOCs from the open source repositories 2. Perform a sweep across the network to identify positive matches 3. Sandbox any suspicious files 4. Notify the CERT team to apply a future proof threat model
D) 1. Analyze the current threat intelligence 2. Utilize information sharing to obtain the latest industry IOCs 3. Perform a sweep across the network to identify positive matches 4. Apply machine learning algorithms
A) 1. Perform the ongoing research of the best practices 2. Determine current vulnerabilities and threats 3. Apply Big Data techniques 4. Use antivirus control
B) 1. Apply artificial intelligence algorithms for detection 2. Inform the CERT team 3. Research threat intelligence and potential adversaries 4. Utilize threat intelligence to apply Big Data techniques
C) 1. Obtain the latest IOCs from the open source repositories 2. Perform a sweep across the network to identify positive matches 3. Sandbox any suspicious files 4. Notify the CERT team to apply a future proof threat model
D) 1. Analyze the current threat intelligence 2. Utilize information sharing to obtain the latest industry IOCs 3. Perform a sweep across the network to identify positive matches 4. Apply machine learning algorithms

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
29
An organization is preparing to develop a business continuity plan. The organization is required to meet regulatory requirements relating to confidentiality and availability, which are well-defined. Management has expressed concern following initial meetings that the organization is not fully aware of the requirements associated with the regulations. Which of the following would be MOST appropriate for the project manager to solicit additional resources for during this phase of the project?
A) After-action reports
B) Gap assessment
C) Security requirements traceability matrix
D) Business impact assessment
E) Risk analysis
A) After-action reports
B) Gap assessment
C) Security requirements traceability matrix
D) Business impact assessment
E) Risk analysis

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
30
A hospital's security team recently determined its network was breached and patient data was accessed by an external entity. The Chief Information Security Officer (CISO) of the hospital approaches the executive management team with this information, reports the vulnerability that led to the breach has already been remediated, and explains the team is continuing to follow the appropriate incident response plan. The executive team is concerned about the hospital's brand reputation and asks the CISO when the incident should be disclosed to the affected patients. Which of the following is the MOST appropriate response?
A) When it is mandated by their legal and regulatory requirements
B) As soon as possible in the interest of the patients
C) As soon as the public relations department is ready to be interviewed
D) When all steps related to the incident response plan are completed
E) Upon the approval of the Chief Executive Officer (CEO) to release information to the public
A) When it is mandated by their legal and regulatory requirements
B) As soon as possible in the interest of the patients
C) As soon as the public relations department is ready to be interviewed
D) When all steps related to the incident response plan are completed
E) Upon the approval of the Chief Executive Officer (CEO) to release information to the public

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
31
A deployment manager is working with a software development group to assess the security of a new version of the organization's internally developed ERP tool. The organization prefers to not perform assessment activities following deployment, instead focusing on assessing security throughout the life cycle. Which of the following methods would BEST assess the security of the product?
A) Static code analysis in the IDE environment
B) Penetration testing of the UAT environment
C) Vulnerability scanning of the production environment
D) Penetration testing of the production environment
E) Peer review prior to unit testing
A) Static code analysis in the IDE environment
B) Penetration testing of the UAT environment
C) Vulnerability scanning of the production environment
D) Penetration testing of the production environment
E) Peer review prior to unit testing

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
32
A security engineer must establish a method to assess compliance with company security policies as they apply to the unique configuration of individual endpoints, as well as to the shared configuration policies of common devices. 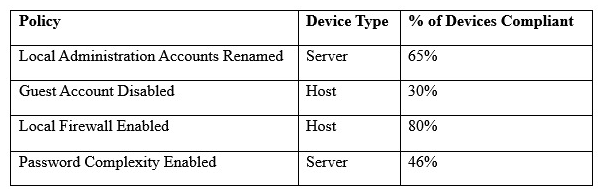 Which of the following tools is the security engineer using to produce the above output?
Which of the following tools is the security engineer using to produce the above output?
A) Vulnerability scanner
B) SIEM
C) Port scanner
D) SCAP scanner
 Which of the following tools is the security engineer using to produce the above output?
Which of the following tools is the security engineer using to produce the above output?A) Vulnerability scanner
B) SIEM
C) Port scanner
D) SCAP scanner

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
33
Which of the following BEST represents a risk associated with merging two enterprises during an acquisition?
A) The consolidation of two different IT enterprises increases the likelihood of the data loss because there are now two backup systems
B) Integrating two different IT systems might result in a successful data breach if threat intelligence is not shared between the two enterprises
C) Merging two enterprise networks could result in an expanded attack surface and could cause outages if trust and permission issues are not handled carefully
D) Expanding the set of data owners requires an in-depth review of all data classification decisions, impacting availability during the review
A) The consolidation of two different IT enterprises increases the likelihood of the data loss because there are now two backup systems
B) Integrating two different IT systems might result in a successful data breach if threat intelligence is not shared between the two enterprises
C) Merging two enterprise networks could result in an expanded attack surface and could cause outages if trust and permission issues are not handled carefully
D) Expanding the set of data owners requires an in-depth review of all data classification decisions, impacting availability during the review

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
34
A company is developing requirements for a customized OS build that will be used in an embedded environment. The company procured hardware that is capable of reducing the likelihood of successful buffer overruns while executables are processing. Which of the following capabilities must be included for the OS to take advantage of this critical hardware-based countermeasure?
A) Application whitelisting
B) NX/XN bit
C) ASLR
D) TrustZone
E) SCP
A) Application whitelisting
B) NX/XN bit
C) ASLR
D) TrustZone
E) SCP

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
35
A team is at the beginning stages of designing a new enterprise-wide application. The new application will have a large database and require a capital investment in hardware. The Chief Information Officer (?IO) has directed the team to save money and reduce the reliance on the datacenter, and the vendor must specialize in hosting large databases in the cloud. Which of the following cloud-hosting options would BEST meet these needs?
A) Multi-tenancy SaaS
B) Hybrid IaaS
C) Single-tenancy PaaS
D) Community IaaS
A) Multi-tenancy SaaS
B) Hybrid IaaS
C) Single-tenancy PaaS
D) Community IaaS

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
36
An agency has implemented a data retention policy that requires tagging data according to type before storing it in the data repository. The policy requires all business emails be automatically deleted after two years. During an open records investigation, information was found on an employee's work computer concerning a conversation that occurred three years prior and proved damaging to the agency's reputation. Which of the following MOST likely caused the data leak?
A) The employee manually changed the email client retention settings to prevent deletion of emails
B) The file that contained the damaging information was mistagged and retained on the server for longer than it should have been
C) The email was encrypted and an exception was put in place via the data classification application
D) The employee saved a file on the computer's hard drive that contained archives of emails, which were more than two years old
A) The employee manually changed the email client retention settings to prevent deletion of emails
B) The file that contained the damaging information was mistagged and retained on the server for longer than it should have been
C) The email was encrypted and an exception was put in place via the data classification application
D) The employee saved a file on the computer's hard drive that contained archives of emails, which were more than two years old

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
37
A company is acquiring incident response and forensic assistance from a managed security service provider in the event of a data breach. The company has selected a partner and must now provide required documents to be reviewed and evaluated. Which of the following documents would BEST protect the company and ensure timely assistance? (Choose two.)
A) RA
B) BIA
C) NDA
D) RFI
E) RFQ
F) MSA
A) RA
B) BIA
C) NDA
D) RFI
E) RFQ
F) MSA

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
38
A security architect is implementing security measures in response to an external audit that found vulnerabilities in the corporate collaboration tool suite. The report identified the lack of any mechanism to provide confidentiality for electronic correspondence between users and between users and group mailboxes. Which of the following controls would BEST mitigate the identified vulnerability?
A) Issue digital certificates to all users, including owners of group mailboxes, and enable S/MIME
B) Federate with an existing PKI provider, and reject all non-signed emails
C) Implement two-factor email authentication, and require users to hash all email messages upon receipt
D) Provide digital certificates to all systems, and eliminate the user group or shared mailboxes
A) Issue digital certificates to all users, including owners of group mailboxes, and enable S/MIME
B) Federate with an existing PKI provider, and reject all non-signed emails
C) Implement two-factor email authentication, and require users to hash all email messages upon receipt
D) Provide digital certificates to all systems, and eliminate the user group or shared mailboxes

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
39
A security administrator wants to allow external organizations to cryptographically validate the company's domain name in email messages sent by employees. Which of the following should the security administrator implement?
A) SPF
B) S/MIME
C) TLS
D) DKIM
A) SPF
B) S/MIME
C) TLS
D) DKIM

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
40
A software development team is conducting functional and user acceptance testing of internally developed web applications using a COTS solution. For automated testing, the solution uses valid user credentials from the enterprise directory to authenticate to each application. The solution stores the username in plain text and the corresponding password as an encoded string in a script within a file, located on a globally accessible network share. The account credentials used belong to the development team lead. To reduce the risks associated with this scenario while minimizing disruption to ongoing testing, which of the following are the BEST actions to take? (Choose two.)
A) Restrict access to the network share by adding a group only for developers to the share's ACL
B) Implement a new COTS solution that does not use hard-coded credentials and integrates with directory services
C) Obfuscate the username within the script file with encoding to prevent easy identification and the account used
D) Provision a new user account within the enterprise directory and enable its use for authentication to the target applications. Share the username and password with all developers for use in their individual scripts
E) Redesign the web applications to accept single-use, local account credentials for authentication
A) Restrict access to the network share by adding a group only for developers to the share's ACL
B) Implement a new COTS solution that does not use hard-coded credentials and integrates with directory services
C) Obfuscate the username within the script file with encoding to prevent easy identification and the account used
D) Provision a new user account within the enterprise directory and enable its use for authentication to the target applications. Share the username and password with all developers for use in their individual scripts
E) Redesign the web applications to accept single-use, local account credentials for authentication

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
41
The legal department has required that all traffic to and from a company's cloud-based word processing and email system is logged. To meet this requirement, the Chief Information Security Officer (CISO) has implemented a next-generation firewall to perform inspection of the secure traffic and has decided to use a cloud-based log aggregation solution for all traffic that is logged. Which of the following presents a long-term risk to user privacy in this scenario?
A) Confidential or sensitive documents are inspected by the firewall before being logged.
B) Latency when viewing videos and other online content may increase.
C) Reports generated from the firewall will take longer to produce due to more information from inspected traffic.
D) Stored logs may contain non-encrypted usernames and passwords for personal websites.
A) Confidential or sensitive documents are inspected by the firewall before being logged.
B) Latency when viewing videos and other online content may increase.
C) Reports generated from the firewall will take longer to produce due to more information from inspected traffic.
D) Stored logs may contain non-encrypted usernames and passwords for personal websites.

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
42
A large enterprise with thousands of users is experiencing a relatively high frequency of malicious activity from the insider threats. Much of the activity appears to involve internal reconnaissance that results in targeted attacks against privileged users and network file shares. Given this scenario, which of the following would MOST likely prevent or deter these attacks? (Choose two.)
A) Conduct role-based training for privileged users that highlights common threats against them and covers best practices to thwart attacks
B) Increase the frequency at which host operating systems are scanned for vulnerabilities, and decrease the amount of time permitted between vulnerability identification and the application of corresponding patches
C) Enforce command shell restrictions via group policies for all workstations by default to limit which native operating system tools are available for use
D) Modify the existing rules of behavior to include an explicit statement prohibiting users from enumerating user and file directories using available tools and/or accessing visible resources that do not directly pertain to their job functions
E) For all workstations, implement full-disk encryption and configure UEFI instances to require complex passwords for authentication
F) Implement application blacklisting enforced by the operating systems of all machines in the enterprise
A) Conduct role-based training for privileged users that highlights common threats against them and covers best practices to thwart attacks
B) Increase the frequency at which host operating systems are scanned for vulnerabilities, and decrease the amount of time permitted between vulnerability identification and the application of corresponding patches
C) Enforce command shell restrictions via group policies for all workstations by default to limit which native operating system tools are available for use
D) Modify the existing rules of behavior to include an explicit statement prohibiting users from enumerating user and file directories using available tools and/or accessing visible resources that do not directly pertain to their job functions
E) For all workstations, implement full-disk encryption and configure UEFI instances to require complex passwords for authentication
F) Implement application blacklisting enforced by the operating systems of all machines in the enterprise

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
43
Given the code snippet below: 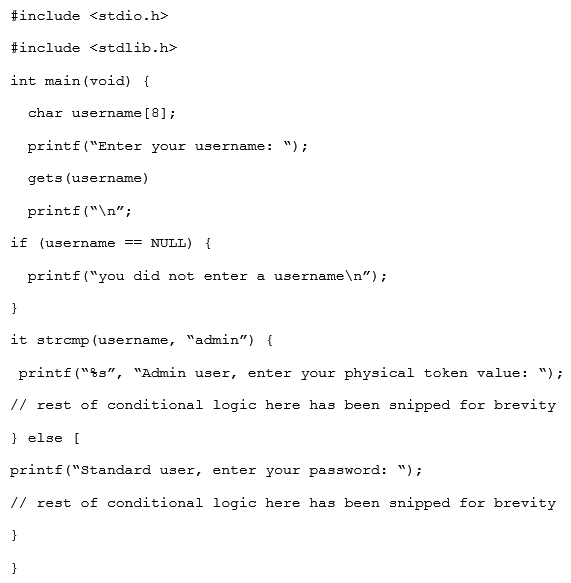 Which of the following vulnerability types in the MOST concerning?
Which of the following vulnerability types in the MOST concerning?
A) Only short usernames are supported, which could result in brute forcing of credentials.
B) Buffer overflow in the username parameter could lead to a memory corruption vulnerability.
C) Hardcoded usernames with different code paths taken depend on which user is entered.
D) Format string vulnerability is present for admin users but not for standard users.
 Which of the following vulnerability types in the MOST concerning?
Which of the following vulnerability types in the MOST concerning?A) Only short usernames are supported, which could result in brute forcing of credentials.
B) Buffer overflow in the username parameter could lead to a memory corruption vulnerability.
C) Hardcoded usernames with different code paths taken depend on which user is entered.
D) Format string vulnerability is present for admin users but not for standard users.

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
44
To meet an SLA, which of the following document should be drafted, defining the company's internal interdependent unit responsibilities and delivery timelines.
A) BPA
B) OLA
C) MSA
D) MOU
A) BPA
B) OLA
C) MSA
D) MOU

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
45
An organization's network engineering team recently deployed a new software encryption solution to ensure the confidentiality of data at rest, which was found to add 300ms of latency to data read-write requests in storage, impacting business operations. Which of the following alternative approaches would BEST address performance requirements while meeting the intended security objective?
A) Employ hardware FDE or SED solutions.
B) Utilize a more efficient cryptographic hash function.
C) Replace HDDs with SSD arrays.
D) Use a FIFO pipe a multithreaded software solution.
A) Employ hardware FDE or SED solutions.
B) Utilize a more efficient cryptographic hash function.
C) Replace HDDs with SSD arrays.
D) Use a FIFO pipe a multithreaded software solution.

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
46
A systems administrator recently joined an organization and has been asked to perform a security assessment of controls on the organization's file servers, which contain client data from a number of sensitive systems. The administrator needs to compare documented access requirements to the access implemented within the file system. Which of the following is MOST likely to be reviewed during the assessment? (Select two.)
A) Access control list
B) Security requirements traceability matrix
C) Data owner matrix
D) Roles matrix
E) Data design document
F) Data access policies
A) Access control list
B) Security requirements traceability matrix
C) Data owner matrix
D) Roles matrix
E) Data design document
F) Data access policies

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
47
A business is growing and starting to branch out into other locations. In anticipation of opening an office in a different country, the Chief Information Security Officer (CISO) and legal team agree they need to meet the following criteria regarding data to open the new office: Store taxation-related documents for five years Store customer addresses in an encrypted format Destroy customer information after one year Keep data only in the customer's home country Which of the following should the CISO implement to BEST meet these requirements? (Choose three.)
A) Capacity planning policy
B) Data retention policy
C) Data classification standard
D) Legal compliance policy
E) Data sovereignty policy
F) Backup policy
G) Acceptable use policy
H) Encryption standard
A) Capacity planning policy
B) Data retention policy
C) Data classification standard
D) Legal compliance policy
E) Data sovereignty policy
F) Backup policy
G) Acceptable use policy
H) Encryption standard

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
48
A company wants to extend its help desk availability beyond business hours. The Chief Information Officer (CIO) decides to augment the help desk with a third-party service that will answer calls and provide Tier 1 problem resolution, such as password resets and remote assistance. The security administrator implements the following firewall change: 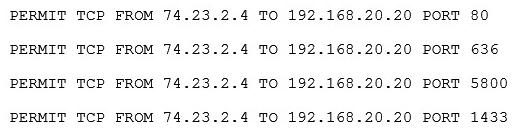 The administrator provides the appropriate path and credentials to the third-party company. Which of the following technologies is MOST likely being used to provide access to the third company?
The administrator provides the appropriate path and credentials to the third-party company. Which of the following technologies is MOST likely being used to provide access to the third company?
A) LDAP
B) WAYF
C) OpenID
D) RADIUS
E) SAML
 The administrator provides the appropriate path and credentials to the third-party company. Which of the following technologies is MOST likely being used to provide access to the third company?
The administrator provides the appropriate path and credentials to the third-party company. Which of the following technologies is MOST likely being used to provide access to the third company?A) LDAP
B) WAYF
C) OpenID
D) RADIUS
E) SAML

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
49
A recent CRM upgrade at a branch office was completed after the desired deadline. Several technical issues were found during the upgrade and need to be discussed in depth before the next branch office is upgraded. Which of the following should be used to identify weak processes and other vulnerabilities?
A) Gap analysis
B) Benchmarks and baseline results
C) Risk assessment
D) Lessons learned report
A) Gap analysis
B) Benchmarks and baseline results
C) Risk assessment
D) Lessons learned report

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
50
A threat advisory alert was just emailed to the IT security staff. The alert references specific types of host operating systems that can allow an unauthorized person to access files on a system remotely. A fix was recently published, but it requires a recent endpoint protection engine to be installed prior to running the fix. Which of the following MOST likely need to be configured to ensure the system are mitigated accordingly? (Select two.)
A) Antivirus
B) HIPS
C) Application whitelisting
D) Patch management
E) Group policy implementation
F) Firmware updates
A) Antivirus
B) HIPS
C) Application whitelisting
D) Patch management
E) Group policy implementation
F) Firmware updates

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
51
An architect was recently hired by a power utility to increase the security posture of the company's power generation and distribution sites. Upon review, the architect identifies legacy hardware with highly vulnerable and unsupported software driving critical operations. These systems must exchange data with each other, be highly synchronized, and pull from the Internet time sources. Which of the following architectural decisions would BEST reduce the likelihood of a successful attack without harming operational capability? (Choose two.)
A) Isolate the systems on their own network
B) Install a firewall and IDS between systems and the LAN
C) Employ own stratum-0 and stratum-1 NTP servers
D) Upgrade the software on critical systems
E) Configure the systems to use government-hosted NTP servers
A) Isolate the systems on their own network
B) Install a firewall and IDS between systems and the LAN
C) Employ own stratum-0 and stratum-1 NTP servers
D) Upgrade the software on critical systems
E) Configure the systems to use government-hosted NTP servers

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
52
A software development manager is running a project using agile development methods. The company cybersecurity engineer has noticed a high number of vulnerabilities have been making it into production code on the project. Which of the following methods could be used in addition to an integrated development environment to reduce the severity of the issue?
A) Conduct a penetration test on each function as it is developed
B) Develop a set of basic checks for common coding errors
C) Adopt a waterfall method of software development
D) Implement unit tests that incorporate static code analyzers
A) Conduct a penetration test on each function as it is developed
B) Develop a set of basic checks for common coding errors
C) Adopt a waterfall method of software development
D) Implement unit tests that incorporate static code analyzers

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
53
A company contracts a security engineer to perform a penetration test of its client-facing web portal. Which of the following activities would be MOST appropriate?
A) Use a protocol analyzer against the site to see if data input can be replayed from the browser
B) Scan the website through an interception proxy and identify areas for the code injection
C) Scan the site with a port scanner to identify vulnerable services running on the web server
D) Use network enumeration tools to identify if the server is running behind a load balancer
A) Use a protocol analyzer against the site to see if data input can be replayed from the browser
B) Scan the website through an interception proxy and identify areas for the code injection
C) Scan the site with a port scanner to identify vulnerable services running on the web server
D) Use network enumeration tools to identify if the server is running behind a load balancer

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
54
A new cluster of virtual servers has been set up in a lab environment and must be audited before being allowed on the production network. The security manager needs to ensure unnecessary services are disabled and all system accounts are using strong credentials. Which of the following tools should be used? (Choose two.)
A) Fuzzer
B) SCAP scanner
C) Packet analyzer
D) Password cracker
E) Network enumerator
F) SIEM
A) Fuzzer
B) SCAP scanner
C) Packet analyzer
D) Password cracker
E) Network enumerator
F) SIEM

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
55
While attending a meeting with the human resources department, an organization's information security officer sees an employee using a username and password written on a memo pad to log into a specific service. When the information security officer inquires further as to why passwords are being written down, the response is that there are too many passwords to remember for all the different services the human resources department is required to use. Additionally, each password has specific complexity requirements and different expiration time frames. Which of the following would be the BEST solution for the information security officer to recommend?
A) Utilizing MFA
B) Implementing SSO
C) Deploying 802.1X
D) Pushing SAML adoption
E) Implementing TACACS
A) Utilizing MFA
B) Implementing SSO
C) Deploying 802.1X
D) Pushing SAML adoption
E) Implementing TACACS

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
56
An organization enables BYOD but wants to allow users to access the corporate email, calendar, and contacts from their devices. The data associated with the user's accounts is sensitive, and therefore, the organization wants to comply with the following requirements: Active full-device encryption Enabled remote-device wipe Blocking unsigned applications Containerization of email, calendar, and contacts Which of the following technical controls would BEST protect the data from attack or loss and meet the above requirements?
A) Require frequent password changes and disable NFC.
B) Enforce device encryption and activate MAM.
C) Install a mobile antivirus application.
D) Configure and monitor devices with an MDM.
A) Require frequent password changes and disable NFC.
B) Enforce device encryption and activate MAM.
C) Install a mobile antivirus application.
D) Configure and monitor devices with an MDM.

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
57
A security analyst sees some suspicious entries in a log file from a web server website, which has a form that allows customers to leave feedback on the company's products. The analyst believes a malicious actor is scanning the web form. To know which security controls to put in place, the analyst first needs to determine the type of activity occurring to design a control. Given the log below: 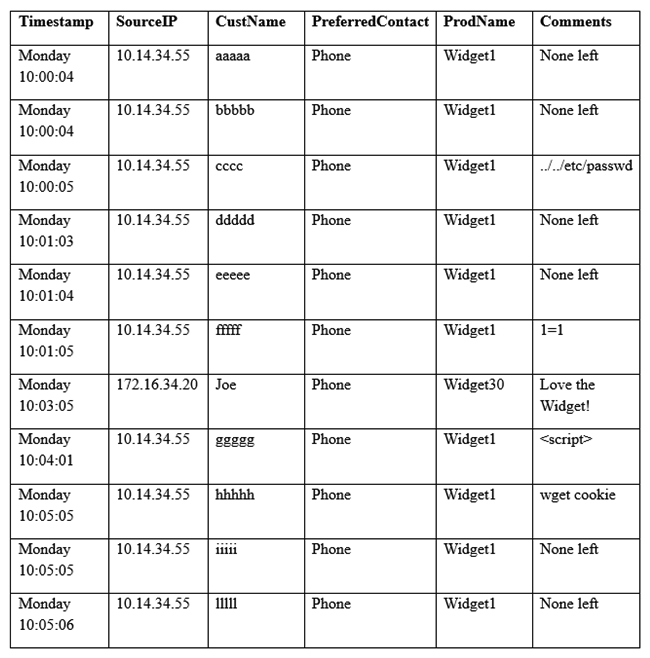 Which of the following is the MOST likely type of activity occurring?
Which of the following is the MOST likely type of activity occurring?
A) SQL injection
B) XSS scanning
C) Fuzzing
D) Brute forcing
 Which of the following is the MOST likely type of activity occurring?
Which of the following is the MOST likely type of activity occurring?A) SQL injection
B) XSS scanning
C) Fuzzing
D) Brute forcing

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
58
A network engineer is attempting to design-in resiliency characteristics for an enterprise network's VPN services. If the engineer wants to help ensure some resilience against zero-day vulnerabilities exploited against the VPN implementation, which of the following decisions would BEST support this objective?
A) Implement a reverse proxy for VPN traffic that is defended and monitored by the organization's SOC with near-real-time alerting to administrators.
B) Subscribe to a managed service provider capable of supporting the mitigation of advanced DDoS attacks on the enterprise's pool of VPN concentrators.
C) Distribute the VPN concentrators across multiple systems at different physical sites to ensure some backup services are available in the event of primary site loss.
D) Employ a second VPN layer concurrently where the other layer's cryptographic implementation is sourced from a different vendor.
A) Implement a reverse proxy for VPN traffic that is defended and monitored by the organization's SOC with near-real-time alerting to administrators.
B) Subscribe to a managed service provider capable of supporting the mitigation of advanced DDoS attacks on the enterprise's pool of VPN concentrators.
C) Distribute the VPN concentrators across multiple systems at different physical sites to ensure some backup services are available in the event of primary site loss.
D) Employ a second VPN layer concurrently where the other layer's cryptographic implementation is sourced from a different vendor.

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
59
A security engineer is working with a software development team. The engineer is tasked with ensuring all security requirements are adhered to by the developers. Which of the following BEST describes the contents of the supporting document the engineer is creating?
A) A series of ad-hoc tests that each verify security control functionality of the entire system at once.
B) A series of discrete tasks that, when viewed in total, can be used to verify and document each individual constraint from the SRTM.
C) A set of formal methods that apply to one or more of the programing languages used on the development project.
D) A methodology to verify each security control in each unit of developed code prior to committing the code.
A) A series of ad-hoc tests that each verify security control functionality of the entire system at once.
B) A series of discrete tasks that, when viewed in total, can be used to verify and document each individual constraint from the SRTM.
C) A set of formal methods that apply to one or more of the programing languages used on the development project.
D) A methodology to verify each security control in each unit of developed code prior to committing the code.

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
60
Legal counsel has notified the information security manager of a legal matter that will require the preservation of electronic records for 2000 sales force employees. Source records will be email, PC, network shares, and applications. After all restrictions have been lifted, which of the following should the information manager review?
A) Data retention policy
B) Legal hold
C) Chain of custody
D) Scope statement
A) Data retention policy
B) Legal hold
C) Chain of custody
D) Scope statement

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
61
An information security manager is concerned that connectivity used to configure and troubleshoot critical network devices could be attacked. The manager has tasked a network security engineer with meeting the following requirements: Encrypt all traffic between the network engineer and critical devices. Segregate the different networking planes as much as possible. Do not let access ports impact configuration tasks. Which of the following would be the BEST recommendation for the network security engineer to present?
A) Deploy control plane protections.
B) Use SSH over out-of-band management.
C) Force only TACACS to be allowed.
D) Require the use of certificates for AAA.
A) Deploy control plane protections.
B) Use SSH over out-of-band management.
C) Force only TACACS to be allowed.
D) Require the use of certificates for AAA.

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
62
An organization is engaged in international business operations and is required to comply with various legal frameworks. In addition to changes in legal frameworks, which of the following is a primary purpose of a compliance management program?
A) Following new requirements that result from contractual obligations
B) Answering requests from auditors that relate to e-discovery
C) Responding to changes in regulatory requirements
D) Developing organizational policies that relate to hiring and termination procedures
A) Following new requirements that result from contractual obligations
B) Answering requests from auditors that relate to e-discovery
C) Responding to changes in regulatory requirements
D) Developing organizational policies that relate to hiring and termination procedures

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
63
Given the following code snippet: 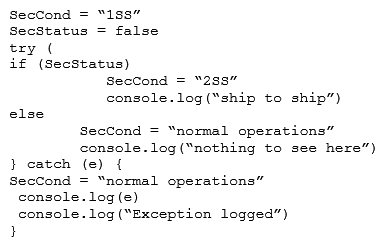 Which of the following failure modes would the code exhibit?
Which of the following failure modes would the code exhibit?
A) Open
B) Secure
C) Halt
D) Exception
 Which of the following failure modes would the code exhibit?
Which of the following failure modes would the code exhibit?A) Open
B) Secure
C) Halt
D) Exception

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
64
A security engineer is performing an assessment again for a company. The security engineer examines the following output from the review: Which of the following tools is the engineer utilizing to perform this assessment? 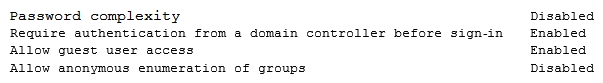
A) Vulnerability scanner
B) SCAP scanner
C) Port scanner
D) Interception proxy

A) Vulnerability scanner
B) SCAP scanner
C) Port scanner
D) Interception proxy

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
65
Given the following output from a security tool in Kali: 
A) Log reduction
B) Network enumerator
C) Fuzzer
D) SCAP scanner

A) Log reduction
B) Network enumerator
C) Fuzzer
D) SCAP scanner

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
66
Which of the following is the GREATEST security concern with respect to BYOD?
A) The filtering of sensitive data out of data flows at geographic boundaries.
B) Removing potential bottlenecks in data transmission paths.
C) The transfer of corporate data onto mobile corporate devices.
D) The migration of data into and out of the network in an uncontrolled manner.
A) The filtering of sensitive data out of data flows at geographic boundaries.
B) Removing potential bottlenecks in data transmission paths.
C) The transfer of corporate data onto mobile corporate devices.
D) The migration of data into and out of the network in an uncontrolled manner.

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
67
A company has gone through a round of phishing attacks. More than 200 users have had their workstation infected because they clicked on a link in an email. An incident analysis has determined an executable ran and compromised the administrator account on each workstation. Management is demanding the information security team prevent this from happening again. Which of the following would BEST prevent this from happening again?
A) Antivirus
B) Patch management
C) Log monitoring
D) Application whitelisting
E) Awareness training
A) Antivirus
B) Patch management
C) Log monitoring
D) Application whitelisting
E) Awareness training

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
68
A newly hired security analyst has joined an established SOC team. Not long after going through corporate orientation, a new attack method on web-based applications was publicly revealed. The security analyst immediately brings this new information to the team lead, but the team lead is not concerned about it. Which of the following is the MOST likely reason for the team lead's position?
A) The organization has accepted the risks associated with web-based threats.
B) The attack type does not meet the organization's threat model.
C) Web-based applications are on isolated network segments.
D) Corporate policy states that NIPS signatures must be updated every hour.
A) The organization has accepted the risks associated with web-based threats.
B) The attack type does not meet the organization's threat model.
C) Web-based applications are on isolated network segments.
D) Corporate policy states that NIPS signatures must be updated every hour.

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
69
A penetration tester noticed special characters in a database table. The penetration tester configured the browser to use an HTTP interceptor to verify that the front-end user registration web form accepts invalid input in the user's age field. The developer was notified and asked to fix the issue. Which of the following is the MOST secure solution for the developer to implement?
A) IF $AGE == "!@#$%^&*()_+<>?":{}[]" THEN ERROR
B) IF $AGE == [1234567890] {1,3} THEN CONTINUE
C) IF $AGE != "a-bA-Z!@#$%^&*()_+<>?":{}[] "THEN CONTINUE
D) IF $AGE == [1-0] {0,2} THEN CONTINUE
A) IF $AGE == "!@#$%^&*()_+<>?":{}[]" THEN ERROR
B) IF $AGE == [1234567890] {1,3} THEN CONTINUE
C) IF $AGE != "a-bA-Z!@#$%^&*()_+<>?":{}[] "THEN CONTINUE
D) IF $AGE == [1-0] {0,2} THEN CONTINUE

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
70
A security architect is determining the best solution for a new project. The project is developing a new intranet with advanced authentication capabilities, SSO for users, and automated provisioning to streamline Day 1 access to systems. The security architect has identified the following requirements: 1. Information should be sourced from the trusted master data source. 2. There must be future requirements for identity proofing of devices and users. 3. A generic identity connector that can be reused must be developed. 4. The current project scope is for internally hosted applications only. Which of the following solution building blocks should the security architect use to BEST meet the requirements?
A) LDAP, multifactor authentication, oAuth, XACML
B) AD, certificate-based authentication, Kerberos, SPML
C) SAML, context-aware authentication, oAuth, WAYF
D) NAC, radius, 802.1x, centralized active directory
A) LDAP, multifactor authentication, oAuth, XACML
B) AD, certificate-based authentication, Kerberos, SPML
C) SAML, context-aware authentication, oAuth, WAYF
D) NAC, radius, 802.1x, centralized active directory

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
71
As a result of an acquisition, a new development team is being integrated into the company. The development team has BYOD laptops with IDEs installed, build servers, and code repositories that utilize SaaS. To have the team up and running effectively, a separate Internet connection has been procured. A stand up has identified the following additional requirements: 1. Reuse of the existing network infrastructure 2. Acceptable use policies to be enforced 3. Protection of sensitive files 4. Access to the corporate applications Which of the following solution components should be deployed to BEST meet the requirements? (Select three.)
A) IPSec VPN
B) HIDS
C) Wireless controller
D) Rights management
E) SSL VPN
F) NAC
G) WAF
H) Load balancer
A) IPSec VPN
B) HIDS
C) Wireless controller
D) Rights management
E) SSL VPN
F) NAC
G) WAF
H) Load balancer

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
72
A systems administrator has installed a disk wiping utility on all computers across the organization and configured it to perform a seven-pass wipe and an additional pass to overwrite the disk with zeros. The company has also instituted a policy that requires users to erase files containing sensitive information when they are no longer needed. To ensure the process provides the intended results, an auditor reviews the following content from a randomly selected decommissioned hard disk:  Which of the following should be included in the auditor's report based on the above findings?
Which of the following should be included in the auditor's report based on the above findings?
A) The hard disk contains bad sectors
B) The disk has been degaussed.
C) The data represents part of the disk BIOS.
D) Sensitive data might still be present on the hard drives.
 Which of the following should be included in the auditor's report based on the above findings?
Which of the following should be included in the auditor's report based on the above findings?A) The hard disk contains bad sectors
B) The disk has been degaussed.
C) The data represents part of the disk BIOS.
D) Sensitive data might still be present on the hard drives.

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
73
A government organization operates and maintains several ICS environments. The categorization of one of the ICS environments led to a moderate baseline. The organization has complied a set of applicable security controls based on this categorization. Given that this is a unique environment, which of the following should the organization do NEXT to determine if other security controls should be considered?
A) Check for any relevant or required overlays.
B) Review enhancements within the current control set.
C) Modify to a high-baseline set of controls.
D) Perform continuous monitoring.
A) Check for any relevant or required overlays.
B) Review enhancements within the current control set.
C) Modify to a high-baseline set of controls.
D) Perform continuous monitoring.

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
74
A security architect is designing a system to satisfy user demand for reduced transaction time, increased security and message integrity, and improved cryptographic security. The resultant system will be used in an environment with a broad user base where many asynchronous transactions occur every minute and must be publicly verifiable. Which of the following solutions BEST meets all of the architect's objectives?
A) An internal key infrastructure that allows users to digitally sign transaction logs
B) An agreement with an entropy-as-a-service provider to increase the amount of randomness in generated keys.
C) A publicly verified hashing algorithm that allows revalidation of message integrity at a future date.
D) An open distributed transaction ledger that requires proof of work to append entries.
A) An internal key infrastructure that allows users to digitally sign transaction logs
B) An agreement with an entropy-as-a-service provider to increase the amount of randomness in generated keys.
C) A publicly verified hashing algorithm that allows revalidation of message integrity at a future date.
D) An open distributed transaction ledger that requires proof of work to append entries.

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
75
A medical device company is implementing a new COTS antivirus solution in its manufacturing plant. All validated machines and instruments must be retested for interoperability with the new software. Which of the following would BEST ensure the software and instruments are working as designed?
A) System design documentation
B) User acceptance testing
C) Peer review
D) Static code analysis testing
E) Change control documentation
A) System design documentation
B) User acceptance testing
C) Peer review
D) Static code analysis testing
E) Change control documentation

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
76
Which of the following is an external pressure that causes companies to hire security assessors and penetration testers?
A) Lack of adequate in-house testing skills.
B) Requirements for geographically based assessments
C) Cost reduction measures
D) Regulatory insistence on independent reviews.
A) Lack of adequate in-house testing skills.
B) Requirements for geographically based assessments
C) Cost reduction measures
D) Regulatory insistence on independent reviews.

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
77
Click on the exhibit buttons to view the four messages. 
 A security architect is working with a project team to deliver an important service that stores and processes customer banking details. The project, internally known as ProjectX, is due to launch its first set of features publicly within a week, but the team has not been able to implement encryption-at-rest of the customer records. The security architect is drafting an escalation email to senior leadership. Which of the following BEST conveys the business impact for senior leadership?
A security architect is working with a project team to deliver an important service that stores and processes customer banking details. The project, internally known as ProjectX, is due to launch its first set of features publicly within a week, but the team has not been able to implement encryption-at-rest of the customer records. The security architect is drafting an escalation email to senior leadership. Which of the following BEST conveys the business impact for senior leadership?
A) Message 1
B) Message 2
C) Message 3
D) Message 4




 A security architect is working with a project team to deliver an important service that stores and processes customer banking details. The project, internally known as ProjectX, is due to launch its first set of features publicly within a week, but the team has not been able to implement encryption-at-rest of the customer records. The security architect is drafting an escalation email to senior leadership. Which of the following BEST conveys the business impact for senior leadership?
A security architect is working with a project team to deliver an important service that stores and processes customer banking details. The project, internally known as ProjectX, is due to launch its first set of features publicly within a week, but the team has not been able to implement encryption-at-rest of the customer records. The security architect is drafting an escalation email to senior leadership. Which of the following BEST conveys the business impact for senior leadership?A) Message 1
B) Message 2
C) Message 3
D) Message 4

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
78
The marketing department has developed a new marketing campaign involving significant social media outreach. The campaign includes allowing employees and customers to submit blog posts and pictures of their day-to-day experiences at the company. The information security manager has been asked to provide an informative letter to all participants regarding the security risks and how to avoid privacy and operational security issues. Which of the following is the MOST important information to reference in the letter?
A) After-action reports from prior incidents.
B) Social engineering techniques
C) Company policies and employee NDAs
D) Data classification processes
A) After-action reports from prior incidents.
B) Social engineering techniques
C) Company policies and employee NDAs
D) Data classification processes

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
79
A security analyst is attempting to break into a client's secure network. The analyst was not given prior information about the client, except for a block of public IP addresses that are currently in use. After network enumeration, the analyst's NEXT step is to perform:
A) a gray-box penetration test
B) a risk analysis
C) a vulnerability assessment
D) an external security audit
E) a red team exercise
A) a gray-box penetration test
B) a risk analysis
C) a vulnerability assessment
D) an external security audit
E) a red team exercise

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck
80
A security administrator wants to implement two-factor authentication for network switches and routers. The solution should integrate with the company's RADIUS server, which is used for authentication to the network infrastructure devices. The security administrator implements the following: An HOTP service is installed on the RADIUS server. The RADIUS server is configured to require the HOTP service for authentication. The configuration is successfully tested using a software supplicant and enforced across all network devices. Network administrators report they are unable to log onto the network devices because they are not being prompted for the second factor. Which of the following should be implemented to BEST resolve the issue?
A) Replace the password requirement with the second factor. Network administrators will enter their username and then enter the token in place of their password in the password field.
B) Configure the RADIUS server to accept the second factor appended to the password. Network administrators will enter a password followed by their token in the password field.
C) Reconfigure network devices to prompt for username, password, and a token. Network administrators will enter their username and password, and then they will enter the token.
D) Install a TOTP service on the RADIUS server in addition to the HOTP service. Use the HOTP on older devices that do not support two-factor authentication. Network administrators will use a web portal to log onto these devices.
A) Replace the password requirement with the second factor. Network administrators will enter their username and then enter the token in place of their password in the password field.
B) Configure the RADIUS server to accept the second factor appended to the password. Network administrators will enter a password followed by their token in the password field.
C) Reconfigure network devices to prompt for username, password, and a token. Network administrators will enter their username and password, and then they will enter the token.
D) Install a TOTP service on the RADIUS server in addition to the HOTP service. Use the HOTP on older devices that do not support two-factor authentication. Network administrators will use a web portal to log onto these devices.

Unlock Deck
Unlock for access to all 442 flashcards in this deck.
Unlock Deck
k this deck



