Deck 11: Computer Crime and Information Security
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/150
Play
Full screen (f)
Deck 11: Computer Crime and Information Security
1
Viruses and security attacks have decreased consistently each year.
False
2
Like tangible objects, intellectual property has value and is owned by an individual or organization.
True
3
The digitization of many forms of intellectual property, including books, movies, artwork, and music, has transformed intangible products into tangible products.
False
4
In 2009, President Obama created a new senior-level position in the White House to oversee cybersecurity across all areas of government and national infrastructure.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
5
Very few cyberattacks originate overseas.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
6
Many attackers use the Microsoft monthly announcements to reverse-engineer hacking tools that take advantage of the newly found bugs.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
7
Recently, the RIAA has changed strategies from having music fans cut off from the Internet, to suing them instead.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
8
All hackers are considered unethical.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
9
Passwords are considered the weakest form of authentication because they can be used by others to access systems without your knowledge.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
10
A scary statistic from a study performed by security firm Sophos showed that 40 percent of Internet users use one common password for all their online accounts.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
11
Cameras posted at airport security gates and on city streets can continuously scan for faces of known criminals.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
12
Fingerprint scans are becoming a less and less common method of authentication for access to secure areas.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
13
Unlike speech recognition, voice recognition is not concerned with determining what words are being spoken, but with who is speaking them.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
14
Voice recognition is sometimes classified as behaviormetrics rather than biometrics, since the analysis is based on the study of the manner in which a person speaks, which is a behavior rather than a physical trait.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
15
Research shows that over 75% of computer users have a regular backup procedure in place.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
16
When a computer is connected to a network, security risks increase a hundredfold.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
17
Users do not have the power to set permission settings of the files they own.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
18
By default, the personal files and folders on both Windows Vista and Mac OS X computers are available to others on a network.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
19
Employers are legally responsible for notifying employees of network usage policies.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
20
By default, access points are set to broadcast their presence.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
21
Today's virus scanners are programmed to detect hundreds of thousands of different viruses, worms, Trojan horses, and other potentially unwanted applications. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
22
Each time you use software, listen to music, read a book or newspaper article, or see a movie, you are enjoying someone else's physical property. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
23
Protection of intellectual property can take many forms, including copyrights, trademarks, trade secrets, and patents. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
24
The Sarbanes-Oakley Act of 2002 fights corporate corruption by imposing stringent reporting requirements and internal controls on electronic financial records and transactions. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
25
Social-terrorism is a form of terrorism that uses attacks over the Internet to intimidate and harm a population. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
26
Microsoft has, in the past, extended a hand to the hacking community, hoping to get black-hat hackers on its side. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
27
Computer forensics is the process of examining computing equipment to determine if it has been used for illegal, unauthorized, or unusual activities. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
28
ID cards may contain forms of identification in a magnetic strip or in a microchip, as is found in a(n) knowledge card. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
29
Retinal scanning analyzes the pattern of blood vessels at the back of the eye. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
30
Speech recognition, also called speaker authentication, identifies a user by the sound of his or her voice. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
31
The system administrator is responsible for setting the access rights of users and for setting the permissions on system resources. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
32
Most Wi-Fi networks are centered around a device called a(n) portal point. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
33
A social engineer may go junkyard diving; that is, rummaging through trash to steal credit card numbers or other personal information. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
34
In distributed denial-of-service attacks, many computers are used to launch simultaneous repeated requests at a Web server in order to overwhelm it so that it is unable to function. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
35
A(n) firewall is network hardware or software that examines all incoming packets and filters out packets that are potentially dangerous. _________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
36
The 2008 Computer Security Institute's Computer Crime and Security survey found that ____ percent of businesses experience computer virus infestations.
A) 29
B) 49
C) 69
D) 89
A) 29
B) 49
C) 69
D) 89

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
37
The 2008 Computer Security Institute's Computer Crime and Security survey found that ____ percent of businesses suffer targeted attacks from hackers.
A) 7
B) 17
C) 27
D) 37
A) 7
B) 17
C) 27
D) 37

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
38
The 2008 Computer Security Institute's Computer Crime and Security survey found that ____ percent of businesses suffer from electronic financial fraud.
A) 2
B) 12
C) 22
D) 32
A) 2
B) 12
C) 22
D) 32

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
39
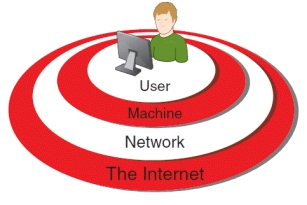
-The accompanying figure illustrates that the ____ level is the most important component of total information security.
A) User
B) Machine
C) Network
D) The Internet

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
40

-Referring to the accompanying figure, as you move from the machine level to the network level to the Internet level, you face ____ exposure and risks.
A) increasing
B) decreasing
C) it varies between a. and b.
D) neither a. nor b.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
41
$264 million were reported lost to Internet fraud in 2008 in ____ alone.
A) Canada
B) the United States
C) France
D) Mexico
A) Canada
B) the United States
C) France
D) Mexico

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
42
____ information security refers to securing all components of the global digital information infrastructure-from cell phones to PCs, to business and government networks, to Internet routers and communications satellites.
A) Complete
B) Global
C) Total
D) Comprehensive
A) Complete
B) Global
C) Total
D) Comprehensive

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
43
The concept of information security is built on the assumption that the information you create, store, maintain, and transfer is ____.
A) valuable
B) confidential
C) worth protecting
D) all of the above
A) valuable
B) confidential
C) worth protecting
D) all of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
44
____ fraud is the most common form of ID theft, making up 20 percent of ID theft cases.
A) Government documents/benefits
B) Credit card
C) Employment fraud
D) Phone or utilities
A) Government documents/benefits
B) Credit card
C) Employment fraud
D) Phone or utilities

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
45
Protection of ____ property can take many forms, including copyrights, trademarks, trade secrets, and patents.
A) physical
B) intellectual
C) both a. and b.
D) neither a. nor b.
A) physical
B) intellectual
C) both a. and b.
D) neither a. nor b.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
46
A ____ protects the words, music, and other expressions for the life of the holder plus 70 years.
A) copyright
B) trademark
C) trade secret
D) patent
A) copyright
B) trademark
C) trade secret
D) patent

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
47
A ____ protects a unique symbol or word used by a business to identify a product or service.
A) copyright
B) trademark
C) trade secret
D) patent
A) copyright
B) trademark
C) trade secret
D) patent

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
48
A ____ protects secrets or proprietary information of individuals and organizations as long as it is adequately protected.
A) copyright
B) trademark
C) trade secret
D) patent
A) copyright
B) trademark
C) trade secret
D) patent

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
49
A ____ protects an invention by giving the holder a monopoly on the use of the invention for 20 years after the application has been applied.
A) trademark
B) copyright
C) trade secret
D) patent
A) trademark
B) copyright
C) trade secret
D) patent

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
50
The ____ of 1996 requires those in the health industry to protect the privacy of health information and provides policies and procedures for doing so.
A) HILAA
B) HIMAA
C) HINAA
D) HIPAA
A) HILAA
B) HIMAA
C) HINAA
D) HIPAA

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
51
The Consumer ____ Privacy Protection Act of 1997 requires data collectors to alert people that their personal information is being shared with other organizations.
A) Online
B) Internet
C) Network
D) Web
A) Online
B) Internet
C) Network
D) Web

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
52
Gramm-Leach-Bliley Act (GLBA) of ____ requires banks and financial institutions to alert customers to their policies and practices in disclosing customer information.
A) 1991
B) 1995
C) 1999
D) 2003
A) 1991
B) 1995
C) 1999
D) 2003

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
53
The Children's Online ____ Protection Act of 1998 gives parents control over what information is collected from their children online and how such information may be used.
A) Privacy
B) Rights
C) Confidentiality
D) Psychological
A) Privacy
B) Rights
C) Confidentiality
D) Psychological

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
54
Security vulnerabilities or security ____ are software bugs that allow violations of information security.
A) rips
B) tears
C) ditches
D) holes
A) rips
B) tears
C) ditches
D) holes

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
55
Software ____ are corrections to the software bugs that cause security vulnerabilities.
A) covers
B) blankets
C) bandages
D) patches
A) covers
B) blankets
C) bandages
D) patches

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
56
A military commander entering the wrong GPS coordinates for enemy troops into the computer is an example of ____.
A) mishandling of computer output
B) errors in computer programs
C) data-entry errors
D) improper installation and setup of computer systems
A) mishandling of computer output
B) errors in computer programs
C) data-entry errors
D) improper installation and setup of computer systems

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
57
A medical office sending lab results to the wrong person is an example of ____.
A) mishandling of computer output
B) errors in computer programs
C) data-entry errors
D) improper installation and setup of computer systems
A) mishandling of computer output
B) errors in computer programs
C) data-entry errors
D) improper installation and setup of computer systems

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
58
A payroll program multiplying a person's pay rate by 2 for overtime instead of 1.5 is an example of ____.
A) mishandling of computer output
B) errors in computer programs
C) data-entry errors
D) improper installation and setup of computer systems
A) mishandling of computer output
B) errors in computer programs
C) data-entry errors
D) improper installation and setup of computer systems

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
59
A person neglecting to properly set the necessary security settings to secure a home wireless network is an example of ____.
A) mishandling of computer output
B) errors in computer programs
C) data-entry errors
D) improper installation and setup of computer systems
A) mishandling of computer output
B) errors in computer programs
C) data-entry errors
D) improper installation and setup of computer systems

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
60
The ____ Industry Association of America (RIAA) has sued thousands of individuals involved in illegal MP3 file sharing for significant financial settlements.
A) Record
B) Radio
C) Recording
D) Rock and Roll
A) Record
B) Radio
C) Recording
D) Rock and Roll

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
61
A ____ is someone who takes advantage of security vulnerabilities to gain unlawful access to private networks for the purpose of private advantage.
A) black-hat hacker
B) white-hat hacker
C) gray-hat hacker
D) script kiddie
A) black-hat hacker
B) white-hat hacker
C) gray-hat hacker
D) script kiddie

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
62
A ____ is someone who considers it working for the common good to hack into networks in order to call attention to flaws in security so that they can be fixed.
A) black-hat hacker
B) white-hat hacker
C) gray-hat hacker
D) script kiddie
A) black-hat hacker
B) white-hat hacker
C) gray-hat hacker
D) script kiddie

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
63
A ____ is someone of questionable ethics.
A) red-hat hacker
B) white-hat hacker
C) gray-hat hacker
D) script kiddie
A) red-hat hacker
B) white-hat hacker
C) gray-hat hacker
D) script kiddie

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
64
A ____ is a person with little technical knowledge who follows the instructions of others to hack networks.
A) black-hat hacker
B) white-hat hacker
C) gray-hat hacker
D) script kiddie
A) black-hat hacker
B) white-hat hacker
C) gray-hat hacker
D) script kiddie

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
65
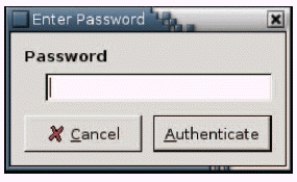
-The accompanying figure, showing an "Enter Password" dialog box, is an example of ____ security.
A) something you know
B) something you have
C) something about you
D) someone you know

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
66

-The accompanying figure, showing someone with their finger over a red light, is an example of ____ security.
A) something you know
B) something you have
C) something about you
D) someone you know

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
67

-The accompanying figure, showing someone with a white card, is an example of ____ security.
A) something you know
B) something you have
C) something about you
D) someone you know

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
68
The most popular type of devices used to identify users and provide access to restricted areas and computer systems are ____ that sometimes take the form of a keychain fob.
A) ID cards
B) tokens
C) both a.and b.
D) neither a. nor b.
A) ID cards
B) tokens
C) both a.and b.
D) neither a. nor b.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
69
Los Angeles International Airport reported that on average, ____ laptops per week are lost on its premises.
A) 300
B) 600
C) 1,200
D) 2,000
A) 300
B) 600
C) 1,200
D) 2,000

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
70
The most common cause of data loss, according to engineers at data recovery vendor Ontrack, is ____.
A) hardware failure
B) human error
C) software corruption
D) viruses
A) hardware failure
B) human error
C) software corruption
D) viruses

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
71
A(n) ____ disk is created while a system is operational and backs up important operating systems files.
A) help
B) index
C) search
D) rescue
A) help
B) index
C) search
D) rescue

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
72
Windows PC users who find their system damaged but are still able to start the computer can benefit from the System ____ utility.
A) Reset
B) Restore
C) Save
D) Stability
A) Reset
B) Restore
C) Save
D) Stability

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
73
The backup software option of backing up all files is called a ____ backup.
A) full
B) mass
C) global
D) group
A) full
B) mass
C) global
D) group

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
74
The backup software option of backing up just those files that have changed since the last backup is called a(n) ____ backup.
A) stopgap
B) incremental
C) half
D) replacement
A) stopgap
B) incremental
C) half
D) replacement

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
75
With remote data backups, changes to your hard drive are ____ and transmitted via your Internet connection to remote data centers.
A) collected
B) compressed
C) encrypted
D) all of the above
A) collected
B) compressed
C) encrypted
D) all of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
76
Most software has an update feature that applies patches to ____ discovered in the software after release.
A) worms
B) bugs
C) trojans
D) viruses
A) worms
B) bugs
C) trojans
D) viruses

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
77
About ____ percent of data loss is attributed to software corruption.
A) 4
B) 9
C) 14
D) 19
A) 4
B) 9
C) 14
D) 19

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
78
____ software referred to as Windows cleaners, or Windows Registry cleaners, such as CleanMyPC and Registry Mechanic, scan the Windows Registry, correcting incorrect or obsolete information
A) AntiVirus
B) Utility
C) Productivity
D) Pop-up Blocker
A) AntiVirus
B) Utility
C) Productivity
D) Pop-up Blocker

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
79
Connecting to the Internet increases risks ____ times that of a stand-alone computer.
A) one thousand
B) ten thousand
C) one hundred thousand
D) one million
A) one thousand
B) ten thousand
C) one hundred thousand
D) one million

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
80
Microsoft Windows Vista uses three classifications for user accounts that do NOT include ____.
A) Administrator
B) Owner
C) Standard
D) Guest
A) Administrator
B) Owner
C) Standard
D) Guest

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck



