Deck 1: Computer Networks, Databases, and Programming Languages
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/135
Play
Full screen (f)
Deck 1: Computer Networks, Databases, and Programming Languages
1
Which of the following is not usually associated with a Wide Area Network
A) The computers are geographically dispersed
B) The organisation can be connected permanently or not to the WAN
C) The shape usually represents a Ring Network Topology
D) WAN's are usually controlled by a specialised company such as BT or PTT
E) Wide Area Networks can provide access to VAN's.
A) The computers are geographically dispersed
B) The organisation can be connected permanently or not to the WAN
C) The shape usually represents a Ring Network Topology
D) WAN's are usually controlled by a specialised company such as BT or PTT
E) Wide Area Networks can provide access to VAN's.
The shape usually represents a Ring Network Topology
2
One of the uses of a spreadsheet model is to ask 'what if' questions and carry out analysis. Which of the following is a correct description of a
'what if' analysis?
A) All the cells in a spreadsheet will be updated whenever an entry is changed
B) Numerical cells in a spreadsheet can be formatted in a variety of ways
C) The model can be emptied of data when circumstances require it to be changed
D) Changes in data input will cause the model to recalculate giving an indication of the possible results of the change
E) A management technique which is just a management fad
'what if' analysis?
A) All the cells in a spreadsheet will be updated whenever an entry is changed
B) Numerical cells in a spreadsheet can be formatted in a variety of ways
C) The model can be emptied of data when circumstances require it to be changed
D) Changes in data input will cause the model to recalculate giving an indication of the possible results of the change
E) A management technique which is just a management fad
Changes in data input will cause the model to recalculate giving an indication of the possible results of the change
3
The link between the logical view and the physical view of data is the?
A) application program
B) the database management system
C) the database
D) programming
E) the data dictionary
A) application program
B) the database management system
C) the database
D) programming
E) the data dictionary
the database management system
4
Who usually writes computer viruses?
A) Disgruntled workers
B) Terrorists
C) Hackers
D) Academic Experience
E) All of the above
A) Disgruntled workers
B) Terrorists
C) Hackers
D) Academic Experience
E) All of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
5
All of the following are types of tangible software except:
A) systems software
B) operating software
C) management decision making software
D) application software
E) cyberspace software
A) systems software
B) operating software
C) management decision making software
D) application software
E) cyberspace software

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
6
Which language is the hardest for humans to write and understand
A) machine code (Binary)
B) assembly language
C) COBOL
D) BASIC
E) PASCAL
A) machine code (Binary)
B) assembly language
C) COBOL
D) BASIC
E) PASCAL

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
7
Which of the following has limited facilities for mathematical notation but
has excellent facilities for character data processing and business use?
A) FORTRAN
B) COBOL
C) PASCAL
D) ADA
E) VORGON
has excellent facilities for character data processing and business use?
A) FORTRAN
B) COBOL
C) PASCAL
D) ADA
E) VORGON

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
8
What is the essence of object-oriented programming?
A) versatility
B) objectivity
C) inheritance
D) all of the above
E) removing the human from computer programming
A) versatility
B) objectivity
C) inheritance
D) all of the above
E) removing the human from computer programming

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
9
The basic data storage hierarchy consists of (in order from the smallest
upwards):
A) byte, bit, record, file, field and database
B) byte, bit, field, record, database, file
C) bit, byte, field, record, file, database
D) bit, byte, field, file, record, database
E) data, information, knowledge, wisdom
upwards):
A) byte, bit, record, file, field and database
B) byte, bit, field, record, database, file
C) bit, byte, field, record, file, database
D) bit, byte, field, file, record, database
E) data, information, knowledge, wisdom

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
10
A file in database terms is:
A) the field which uniquely identifies a record
B) a collection of related records
C) all the files of an organisation
D) a character of information
E) a collection of meaningful information
A) the field which uniquely identifies a record
B) a collection of related records
C) all the files of an organisation
D) a character of information
E) a collection of meaningful information

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
11
In file management systems, the duplication of items of data, so that
they appear in two or more data files is known as:
A) data integrity
B) data redundancy
C) data duplication
D) data manipulation
E) data entry
they appear in two or more data files is known as:
A) data integrity
B) data redundancy
C) data duplication
D) data manipulation
E) data entry

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
12
Which of the following is not usually associated with computer networks?
A) Local Area Network
B) Value Added Network
C) Multi-purpose Network
D) Metropolitan Network
E) Wide Area Network
A) Local Area Network
B) Value Added Network
C) Multi-purpose Network
D) Metropolitan Network
E) Wide Area Network

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
13
A __________________ is a set of rules governing information flow in a
communication system.
A) message envelope
B) standard
C) communication protocol
D) transmission mode
E) modem
communication system.
A) message envelope
B) standard
C) communication protocol
D) transmission mode
E) modem

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
14
The Hybrid Network is the best network (e.g.: Ethernet) to have for every organisations.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
15
The logical data structure with a one to many relationship is the:
A) tree structure
B) network structure
C) tabular structure
D) none of the above
E) all of the above
A) tree structure
B) network structure
C) tabular structure
D) none of the above
E) all of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
16
Due to its conceptual simplicity and powerful data manipulation
capabilities, the use of this type of database is increasing in popularity.
A) network structure
B) tree structure
C) graphical structure
D) relational structure
E) a big one
capabilities, the use of this type of database is increasing in popularity.
A) network structure
B) tree structure
C) graphical structure
D) relational structure
E) a big one

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
17
The most widely used application on personal computers today is?
A) databases
B) electronic spreadsheets
C) word processing
D) graphics
E) none of the above
A) databases
B) electronic spreadsheets
C) word processing
D) graphics
E) none of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
18
Which one of the following is NOT a 3rd Generation Computing
A) ASSEMBLER
B) FORTRAN
C) COBOL
D) BASIC
E) ADA
A) ASSEMBLER
B) FORTRAN
C) COBOL
D) BASIC
E) ADA

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
19
Which of the following is an example of a LAN network topology?
A) The Chain
B) The Plug
C) The Ring
D) The Slot
E) The Ring Pull
A) The Chain
B) The Plug
C) The Ring
D) The Slot
E) The Ring Pull

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
20
Which is the correct definition of the Open Systems Interconnection
A) Data Link Layer, Transport Layer, Physical Layer, Application Layer, Session Layer, Presentation Layer, Network Layer
B) Transport Layer, Network Layer, Data Link Layer, Presentation Layer, Application Layer, Physical Layer, Session Layer
C) Physical Layer, Data Link Layer, Network Layer, Transport Layer, Session Layer, Presentation Layer, Application Layer
D) Presentation Layer, Transport Layer, Physical Layer, Application Layer, Session Layer, Network Layer, Data Link Layer
E) Physical Layer, Data Link Layer, Network Layer, Transport Layer, Presentation Layer, Session Layer, Application Layer
A) Data Link Layer, Transport Layer, Physical Layer, Application Layer, Session Layer, Presentation Layer, Network Layer
B) Transport Layer, Network Layer, Data Link Layer, Presentation Layer, Application Layer, Physical Layer, Session Layer
C) Physical Layer, Data Link Layer, Network Layer, Transport Layer, Session Layer, Presentation Layer, Application Layer
D) Presentation Layer, Transport Layer, Physical Layer, Application Layer, Session Layer, Network Layer, Data Link Layer
E) Physical Layer, Data Link Layer, Network Layer, Transport Layer, Presentation Layer, Session Layer, Application Layer

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
21
If we were to add these two numbers together 5 + 9 we would get 14.
How would a computer show the number 14 in binary code?
A) 101
B) 111
C) 1100
D) 1110
E) 0101
How would a computer show the number 14 in binary code?
A) 101
B) 111
C) 1100
D) 1110
E) 0101

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
22
Which of the following is a characteristic of a Local Area Network
A) Computers are geographically dispersed
B) Usually connected together by satellite link
C) Allows the sharing of data with other organisations
D) Must confirm to industry standards
E) Does not have to confirm to industry standards
A) Computers are geographically dispersed
B) Usually connected together by satellite link
C) Allows the sharing of data with other organisations
D) Must confirm to industry standards
E) Does not have to confirm to industry standards

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
23
Which of the following is not an advantage of the database approach?
A) elimination of data redundancy
B) ability to associate related data
C) increased security
D) program data independence
E) all of the above are advantages
A) elimination of data redundancy
B) ability to associate related data
C) increased security
D) program data independence
E) all of the above are advantages

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
24
Which is NOT normally associated with being one of the main functions
A) cash flow forecasting
B) What if analysis
C) Goal Seeking
D) Storing price lists of information
E) Sensitivity analysis
A) cash flow forecasting
B) What if analysis
C) Goal Seeking
D) Storing price lists of information
E) Sensitivity analysis

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
25
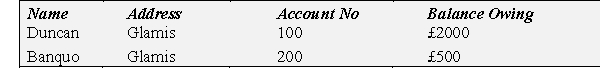
-Which of the following statements relating to the print-out extract is
correct?
A) Duncan is a field entry
B) The extract from the print out is a single record
C) Banquo is a character
D) The extract from the print-out is a field
E) None of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
26

-Which field will be the key field in the records?
A) address
B) balance owing
C) name
D) account no
E) Duncan

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
27
In database management systems the structure is a ______________
representation of the data.
A) physical
B) logical
C) relational
D) tabular
E) hierarchical
representation of the data.
A) physical
B) logical
C) relational
D) tabular
E) hierarchical

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
28
The development of Computer Programming Languages aim to
1. move programming to the 'end user'
2. automate the process of programming as much as possible
3. be reliable
4. be easy maintained
5. be portable
6. be transferable with other computers
A) 1, 2, 3, 5, and 6
B) 2, 3, 4, 5, and 6
C) 1, 2, 4, 5, and 6
D) 3, 4, and 5
E) 1, 2, 3, 4, 5, and 6
1. move programming to the 'end user'
2. automate the process of programming as much as possible
3. be reliable
4. be easy maintained
5. be portable
6. be transferable with other computers
A) 1, 2, 3, 5, and 6
B) 2, 3, 4, 5, and 6
C) 1, 2, 4, 5, and 6
D) 3, 4, and 5
E) 1, 2, 3, 4, 5, and 6

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
29
Computers use the binary system to represent data. Which of the
following statements is true?
A) Binary codes cannot be used by computers to represent text
B) Numbers must be processed into ASCII code in order to be processed by a computer
C) Binary code is used because computers recognise only two states
D) The English alphabet is the only thing a computer understands
E) Arithmetical operations are the only things that computers understand
following statements is true?
A) Binary codes cannot be used by computers to represent text
B) Numbers must be processed into ASCII code in order to be processed by a computer
C) Binary code is used because computers recognise only two states
D) The English alphabet is the only thing a computer understands
E) Arithmetical operations are the only things that computers understand

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
30
Read the following statements, and select the most appropriate outcome.
A. Value-added networks provide additional value by offering services other than the simple transmission of a communication.
B. Local Area Networks and Wide Area Networks are usually connected by gateways.
A) Only A is true
B) Only B is true
C) Both A and B are true
D) Both A and B are false
E) Don't Know
A. Value-added networks provide additional value by offering services other than the simple transmission of a communication.
B. Local Area Networks and Wide Area Networks are usually connected by gateways.
A) Only A is true
B) Only B is true
C) Both A and B are true
D) Both A and B are false
E) Don't Know

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
31
In computing terms what is 'Half-Duplex' transmitting?
A) The sending and receiving of messages in both directions
B) The sending and receiving of messages in one direction
C) The sending of a message which never gets to its destination
D) The receiving of a message which is distorted
E) The receiving of a message which is not appropriate to the user
A) The sending and receiving of messages in both directions
B) The sending and receiving of messages in one direction
C) The sending of a message which never gets to its destination
D) The receiving of a message which is distorted
E) The receiving of a message which is not appropriate to the user

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
32
A Trojan Horse in computing terms can be defined as:
A) Badware which when run will perform some malicious function when some pre-defined set of conditions arise, i.e., date, time, the millionth action, etc.
B) A program inside which a virus and or logic bomb can hide during either its transmission phase between machines or its running phase on a host computer
C) Don't Know
A) Badware which when run will perform some malicious function when some pre-defined set of conditions arise, i.e., date, time, the millionth action, etc.
B) A program inside which a virus and or logic bomb can hide during either its transmission phase between machines or its running phase on a host computer
C) Don't Know

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
33
Information can be classified under the following risk categories.
A) Intentional caused by insiders usually in the course of business
B) Unintentional caused by insiders
C) Intentional, caused by outsiders usually external to the normal routine of business operations (e.g.: industrial espionage)
D) Unintentional, caused by natural disasters (fire, flood etc.)
E) Nothing to worry about and it is all hyped up by the press
A) Intentional caused by insiders usually in the course of business
B) Unintentional caused by insiders
C) Intentional, caused by outsiders usually external to the normal routine of business operations (e.g.: industrial espionage)
D) Unintentional, caused by natural disasters (fire, flood etc.)
E) Nothing to worry about and it is all hyped up by the press

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
34
A database is an organised collection of data

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
35
A Database Management System has the following characteristics?
A) Aids the user to create, store, change, sort and retrieve data
B) Aids the user to protect data only
C) Aids the user when trying to determine what databases to buy
D) Aids the user to store, change and retrieve data only
E) Aids the user to retrieve and manipulate data only
A) Aids the user to create, store, change, sort and retrieve data
B) Aids the user to protect data only
C) Aids the user when trying to determine what databases to buy
D) Aids the user to store, change and retrieve data only
E) Aids the user to retrieve and manipulate data only

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
36
The link between the logical view and the physical view of data is the:
A) application program
B) DBMS
C) database
D) programming
E) Data Flow Diagrams
A) application program
B) DBMS
C) database
D) programming
E) Data Flow Diagrams

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
37
Which database structure arranges data in some natural hierarchy?
A) tree
B) tabular
C) relational
D) network
E) sorted
A) tree
B) tabular
C) relational
D) network
E) sorted

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
38
A spreadsheet is particularly suitable for accounting use because it
automatically provides an audit trail
automatically provides an audit trail

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
39
Listed below are methods which can be used to secure information
systems. Which one of the following is the odd one out?
A) Procedural controls
B) Technical controls
C) Management controls
D) Legal enforcement
E) Allowing professional hackers to enter your computing systems without any resistance
systems. Which one of the following is the odd one out?
A) Procedural controls
B) Technical controls
C) Management controls
D) Legal enforcement
E) Allowing professional hackers to enter your computing systems without any resistance

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
40
The standardisation of computer programming languages contributes
greatly to
A) compilation
B) portability
C) modularity
D) simplicity
E) none of the above
greatly to
A) compilation
B) portability
C) modularity
D) simplicity
E) none of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
41
Which is the only international accepted network standard that is designed to allow devices from different manufactures to communicate with one another?
A) System Application Architecture (SAA)
B) Open System Interconnection (OSI)
C) Electronic Data Interchange (EDI)
D) System Network Architecture (SNA)
E) Accessible Communication Coded Enforced Set of Standards (ACCESS)
A) System Application Architecture (SAA)
B) Open System Interconnection (OSI)
C) Electronic Data Interchange (EDI)
D) System Network Architecture (SNA)
E) Accessible Communication Coded Enforced Set of Standards (ACCESS)

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
42
A file created for the process of updating records in a computerised
system is know as:
A) a master file
B) a reference file
C) a transaction file
D) a static file
E) a normal file
system is know as:
A) a master file
B) a reference file
C) a transaction file
D) a static file
E) a normal file

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
43
Due to its conceptual simplicity and powerful data manipulation
capabilities, the use of this type of database is increasing in popularity.
A) network structure
B) tree structure
C) graphical structure
D) relational structure
E) a big one
capabilities, the use of this type of database is increasing in popularity.
A) network structure
B) tree structure
C) graphical structure
D) relational structure
E) a big one

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
44
A record in a file will be uniquely identified by ? (chose from the list
below) in relational databases
A) a protected field
B) a check digit
C) a key field
D) the field length
E) the file structure
below) in relational databases
A) a protected field
B) a check digit
C) a key field
D) the field length
E) the file structure

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
45
What provides the capability of writing, assembling, designing, and
printing high quality documents?
A) word processing
B) desktop publishing
C) data processing
D) office automation
E) databases
printing high quality documents?
A) word processing
B) desktop publishing
C) data processing
D) office automation
E) databases

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
46
Conversion from analogue signals to digital is called?
A) modulation
B) electronic data interchange
C) communication protocol
D) ISO
E) demodulation
A) modulation
B) electronic data interchange
C) communication protocol
D) ISO
E) demodulation

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
47
A component of the CPU that executes instructions and performs basic operations such as add, divide, multiply and compare, is the:
A) Register
B) Control Unit
C) ALU
D) Input Devices
E) Output Devices
A) Register
B) Control Unit
C) ALU
D) Input Devices
E) Output Devices

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
48
What size is a Kilobyte in computing terms?
A) 1048576 bytes
B) 1073741102 bytes
C) 1024 bytes
D) 8 bites
E) 1000 bytes
A) 1048576 bytes
B) 1073741102 bytes
C) 1024 bytes
D) 8 bites
E) 1000 bytes

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
49
Data can be processed into information in a number of way. Listed below are a number of ways. Which way is the odd one out?
A) classifying
B) associating
C) summarising
D) sorting
E) understanding
A) classifying
B) associating
C) summarising
D) sorting
E) understanding

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
50
In the Information Systems Hierarchy. What are the levels from top to bottom?
A) Management Planning and control systems, Transaction-processing
Systems, Strategic Planning Systems, Operational Planning and Control
Systems
B) Strategic Planning Systems, Management Planning and Control Systems, Operational Planning and Control Systems, Transaction-processing Systems.
C) Transaction-processing Systems, Operational Planning and Control
Systems, Management Planning and Control Systems, Strategic Planning
Systems
D) Strategic Planning Systems, Transaction-processing Systems, Management Planning and Control Systems, Operational Planning and Control Systems
E) Expert Systems, Executive Information Systems, Decision Support
systems, Management Information Systems, Data processing Systems
A) Management Planning and control systems, Transaction-processing
Systems, Strategic Planning Systems, Operational Planning and Control
Systems
B) Strategic Planning Systems, Management Planning and Control Systems, Operational Planning and Control Systems, Transaction-processing Systems.
C) Transaction-processing Systems, Operational Planning and Control
Systems, Management Planning and Control Systems, Strategic Planning
Systems
D) Strategic Planning Systems, Transaction-processing Systems, Management Planning and Control Systems, Operational Planning and Control Systems
E) Expert Systems, Executive Information Systems, Decision Support
systems, Management Information Systems, Data processing Systems

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
51
What is an example of a transaction processing system
A) Accounts receivable
B) payroll activity
C) airline reservation system
D) book ordering system of a book shop
E) all of the above
A) Accounts receivable
B) payroll activity
C) airline reservation system
D) book ordering system of a book shop
E) all of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
52
Which came first in the Microprocessor development 808286 or the 808486?
A) The 808286
B) The 808486
A) The 808286
B) The 808486

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
53
Who can be regarded as inventing the first computer?
A) John Eniac
B) Blasé Pascal
C) Charles Babbage
D) Charles Transistor
E) James Shockly
A) John Eniac
B) Blasé Pascal
C) Charles Babbage
D) Charles Transistor
E) James Shockly

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
54
Data (in computing terms) can be defined as:
A) Meaningful Information
B) Having Increased Knowledge and being able to use it
C) Unorganised facts that have not been processed into information yet
D) Better Information
E) The android in Star Trek the New Generation
A) Meaningful Information
B) Having Increased Knowledge and being able to use it
C) Unorganised facts that have not been processed into information yet
D) Better Information
E) The android in Star Trek the New Generation

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
55
Programmed decisions are:
A) Decisions that are made when a computer program is being written
B) Only made by a computer programme
C) Routine and repetitive decisions
D) Decisions that are taken in response to unusual circumstances
E) Decisions which have a variety of alternative solutions
A) Decisions that are made when a computer program is being written
B) Only made by a computer programme
C) Routine and repetitive decisions
D) Decisions that are taken in response to unusual circumstances
E) Decisions which have a variety of alternative solutions

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
56
In computing terminology, the point of contact between a computer
operator and the system is known as:
A) the system boundary
B) the operating system
C) the user interface
D) the environment
E) cyberspace
operator and the system is known as:
A) the system boundary
B) the operating system
C) the user interface
D) the environment
E) cyberspace

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
57
Computer systems may be used at all levels of management in an organisation. A computerised system designed to support the highest level of management is sometimes known as:
A) A Transaction or Data Processing System
B) A Database Management System
C) An Executive Information System
D) An Open System
E) A Decision Making System
A) A Transaction or Data Processing System
B) A Database Management System
C) An Executive Information System
D) An Open System
E) A Decision Making System

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
58
A system can be defined as:
A) the parts or components are connected together in an organised way
B) the parts or components are affected by being in the system (and are changed by leaving it)
C) the assembly does nothing
D) the assembly has been identified by someone as being of special interest
E) all of the above can define what a system is
A) the parts or components are connected together in an organised way
B) the parts or components are affected by being in the system (and are changed by leaving it)
C) the assembly does nothing
D) the assembly has been identified by someone as being of special interest
E) all of the above can define what a system is

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
59
Which of the following is not an inputting device in computing?
A) Bar-code
B) Voice Character Recognition
C) Video
D) Thermal Image Printer
E) CD-ROM
A) Bar-code
B) Voice Character Recognition
C) Video
D) Thermal Image Printer
E) CD-ROM

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
60
On a tour of a factory, you are shown a computer system which produces invoice, each month. This invoicing system is an example of:
A) A decision support system
B) A transactional processing system
C) An executive information system
D) An expert system
E) A management information system
A) A decision support system
B) A transactional processing system
C) An executive information system
D) An expert system
E) A management information system

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
61
Which one of the following is not a function of an operating system?
A) multiprocessing
B) multiprogramming
C) configuring the systems hardware
D) spell checking of documents
E) accessing files
A) multiprocessing
B) multiprogramming
C) configuring the systems hardware
D) spell checking of documents
E) accessing files

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
62
Information can be defined as:
A) Data plus the meaning attributed to it by a human or a computer programmed by a human
B) Having Knowledge which is valid and relevant
C) Data plus Knowledge
D) Meaningless Data
E) The output from a computer
A) Data plus the meaning attributed to it by a human or a computer programmed by a human
B) Having Knowledge which is valid and relevant
C) Data plus Knowledge
D) Meaningless Data
E) The output from a computer

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
63
Information must be:
1 Accurate
2 Complete
3 Relevant
4 Timely
5 Verifiable
A) 1 and 3
B) 1, 2 and 3
C) 1, 2, 3, 4, and 5
D) 1, 3, 4, and 5
E) 1, 3 and 5
1 Accurate
2 Complete
3 Relevant
4 Timely
5 Verifiable
A) 1 and 3
B) 1, 2 and 3
C) 1, 2, 3, 4, and 5
D) 1, 3, 4, and 5
E) 1, 3 and 5

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
64
Information Technology can be regarded as:
The collective technologies for the;
A) acquisition, transmission, processing and dissemination of information.
B) acquisition, transmission, protection of information
C) capture, processing and deleting of information
D) processing and dissemination of information
E) the understanding of a computer
The collective technologies for the;
A) acquisition, transmission, processing and dissemination of information.
B) acquisition, transmission, protection of information
C) capture, processing and deleting of information
D) processing and dissemination of information
E) the understanding of a computer

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
65
A Computer Systems is made up of several key parts. These parts are:
A) input and output
B) input, Visual Display Unit, processing, and Secondary Storage
C) secondary Storage, output and processing
D) input, processing (transformation), output, and secondary storage.
E) processing of data into information
A) input and output
B) input, Visual Display Unit, processing, and Secondary Storage
C) secondary Storage, output and processing
D) input, processing (transformation), output, and secondary storage.
E) processing of data into information

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
66
In today's modern world, information systems exist to help organisations and managers do:
A) communicating and confusing
B) decision making and communicating
C) decision making and to outwit competitors
D) decision making and communication
E) decision making, communicating and to outwit competitors
A) communicating and confusing
B) decision making and communicating
C) decision making and to outwit competitors
D) decision making and communication
E) decision making, communicating and to outwit competitors

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
67
Managers of companies never use external information when making decisions.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
68
An Information System has to be a computer based system Is this statement:

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
69
In the XYZ Corporation, payroll information is processed on a monthly basis. Which of the following does not describe the nature of this information?
A) External
B) Structured
C) Repetitive
D) Deterministic
E) Detailed
A) External
B) Structured
C) Repetitive
D) Deterministic
E) Detailed

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
70
What is meant by 'on-line' processing?
A) Data entities are stored in groups and updated in bulk
B) Data entities are stored in groups and processed individually
C) Data entities are ignored until there is a gap in the systems processing
D) Data entities are processed instantly and each request is individual.
E) Information is available to users immediately
A) Data entities are stored in groups and updated in bulk
B) Data entities are stored in groups and processed individually
C) Data entities are ignored until there is a gap in the systems processing
D) Data entities are processed instantly and each request is individual.
E) Information is available to users immediately

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
71
Information can only every be informal. Is this statement:

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
72
What level of systems are the 'building blocks' for all the other information systems in an organisation?
A) Management Information Systems
B) Transactional processing systems.
C) Expert Systems
D) Executive Information Systems
E) Expert Systems.
A) Management Information Systems
B) Transactional processing systems.
C) Expert Systems
D) Executive Information Systems
E) Expert Systems.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
73
Which of the following can best be described as a tactical level decision
for the management of a paint manufacturer?
A) The compilation of daily production schedules
B) The location of a new factory premises
C) The introduction of computerised factory production
D) Cash flow forecasting
E) The recording of stock items required
for the management of a paint manufacturer?
A) The compilation of daily production schedules
B) The location of a new factory premises
C) The introduction of computerised factory production
D) Cash flow forecasting
E) The recording of stock items required

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
74
At the heart of UK banking lies CHAPS a computer system. What does CHAPS stand for?
A) Clearing House Automated Payment System
B) Clearing House Automatic Payroll System
C) Clearing House Automated Pension System
D) Clearing House Additional Productivity System
E) Clearance House Additional Protection System
A) Clearing House Automated Payment System
B) Clearing House Automatic Payroll System
C) Clearing House Automated Pension System
D) Clearing House Additional Productivity System
E) Clearance House Additional Protection System

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
75
When looking at Valve and Relay hardware developments. Which characteristics listed below is NOT usually associated with Valves and Relays Technology?
A) Punched cards for inputting and outputting
B) Difficult to programme
C) Batch Operation
D) Non-Time Critical Applications only, e.g.: Payroll
E) Used Voice inputting hardware devices
A) Punched cards for inputting and outputting
B) Difficult to programme
C) Batch Operation
D) Non-Time Critical Applications only, e.g.: Payroll
E) Used Voice inputting hardware devices

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
76
You are planning to take a holiday in Tampa, Florida starting on 29th of November and request travel details from a travel agent. A detailed USA travel catalogue arrives on 26 November with a letter suggesting that you try the Everglades Hotel. You find the details confusing, but eventually find that the Everglades Hotel is actually in Orlando
Which of the following qualities of good information do the details from the travel agent display?
A) It was relevant
B) It was timely
C) It was clear
D) It was accurate
E) It was summarised
Which of the following qualities of good information do the details from the travel agent display?
A) It was relevant
B) It was timely
C) It was clear
D) It was accurate
E) It was summarised

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
77
The function of accounting can be regarded as a closed system? Is this statement :

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
78
Who invented the concept of an integrated circuit?
A) Drummer
B) Ambrose
C) Mr Spock
D) Flemming
E) Charles Babbage
A) Drummer
B) Ambrose
C) Mr Spock
D) Flemming
E) Charles Babbage

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
79
Decisions taken within organisations which have few or clear cut solutions are sometimes known as:
A) probability decisions
B) ad-hoc decisions
C) deterministic decisions
D) long-term decisions
E) tactical decisions
A) probability decisions
B) ad-hoc decisions
C) deterministic decisions
D) long-term decisions
E) tactical decisions

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
80
MIS is oriented towards ........................
A) using the data to produce management information
B) keeping track of daily business events
C) the automation of routine task
D) a and b
E) to act as an expert system
A) using the data to produce management information
B) keeping track of daily business events
C) the automation of routine task
D) a and b
E) to act as an expert system

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck



