Deck 13: Automating Cisco Enterprise Solutions (ENAUTO)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/84
Play
Full screen (f)
Deck 13: Automating Cisco Enterprise Solutions (ENAUTO)
1
What are two benefits of leveraging Ansible for automation of Cisco IOS XE Software? (Choose two.)
A) Ansible playbooks are packaged and installed on IOS XE devices for automatic execution when an IOS device reboots.
B) All IOS XE operating systems include Ansible playbooks for basic system administration tasks.
C) It is a device-independent method for automation and can be used with any type of device or operating system.
D) Ansible playbooks can be written from the IOS XE EXEC command line to configure the device itself.
E) It does not require any modules of software except SSH to be loaded on the network device.
A) Ansible playbooks are packaged and installed on IOS XE devices for automatic execution when an IOS device reboots.
B) All IOS XE operating systems include Ansible playbooks for basic system administration tasks.
C) It is a device-independent method for automation and can be used with any type of device or operating system.
D) Ansible playbooks can be written from the IOS XE EXEC command line to configure the device itself.
E) It does not require any modules of software except SSH to be loaded on the network device.
Ansible playbooks are packaged and installed on IOS XE devices for automatic execution when an IOS device reboots.
It is a device-independent method for automation and can be used with any type of device or operating system.
It is a device-independent method for automation and can be used with any type of device or operating system.
2
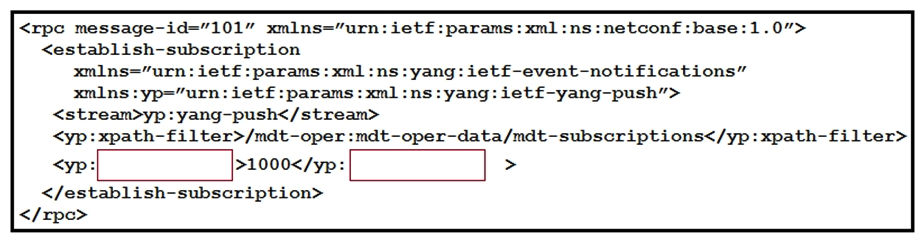 Refer to the exhibit. Which XML tag completes this NETCONF telemetry subscription with a Cisco IOS XE device?
Refer to the exhibit. Which XML tag completes this NETCONF telemetry subscription with a Cisco IOS XE device?A) crontab
B) cadence
C) frequency
D) period
period
3
![<strong> Refer to the exhibits. An engineer creates a Python scripts using ncclient to display interface information. The code must be completed so that it can be tested. Which expression completes the highlighted section in the format call?</strong> A) intf_info B) intf_config C) intf_get D) intf_config[0]](https://d2lvgg3v3hfg70.cloudfront.net/C1178/11ec5360_dad2_6537_8515_037d2c321a68_C1178_00.jpg)
![<strong> Refer to the exhibits. An engineer creates a Python scripts using ncclient to display interface information. The code must be completed so that it can be tested. Which expression completes the highlighted section in the format call?</strong> A) intf_info B) intf_config C) intf_get D) intf_config[0]](https://d2lvgg3v3hfg70.cloudfront.net/C1178/11ec5360_dad2_6538_8515_772489f87e2e_C1178_00.jpg) Refer to the exhibits. An engineer creates a Python scripts using ncclient to display interface information. The code must be completed so that it can be tested. Which expression completes the highlighted section in the format call?
Refer to the exhibits. An engineer creates a Python scripts using ncclient to display interface information. The code must be completed so that it can be tested. Which expression completes the highlighted section in the format call?A) intf_info
B) intf_config
C) intf_get
D) intf_config[0]
intf_info
4
An engineer stored source code in a Git repository and is ready to develop a new feature. The production release is stored in the "master" branch. Which commands create the new feature in a separate branch called "feature" and check out the new version?
A)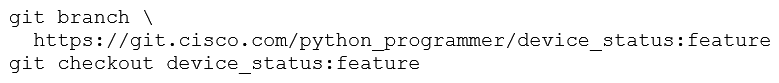
B)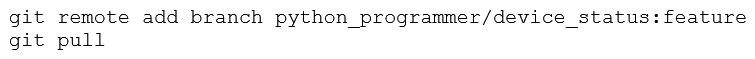
C)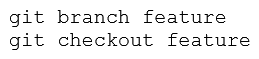
D)
A)

B)
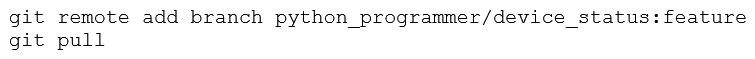
C)
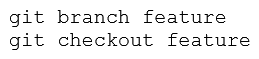
D)


Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
5
Which two statements are benefits of YANG-push telemetry data over traditional data collection methods? (Choose two.)
A) The subscription requests use less bandwidth than SNMP polls.
B) It uses UDP rather than TCP.
C) You can precisely define data subscriptions.
D) It scales better than SNMP.
E) It is supported on more devices than SNMP.
A) The subscription requests use less bandwidth than SNMP polls.
B) It uses UDP rather than TCP.
C) You can precisely define data subscriptions.
D) It scales better than SNMP.
E) It is supported on more devices than SNMP.

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
6
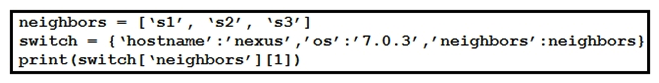 Refer to the exhibit. What is the result when running the Python scripts?
Refer to the exhibit. What is the result when running the Python scripts?A) s1
B) s2
C) s1, s2, s3
D) s3

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
7
Setting is used for the dampening period when configuring an on-change publication for YANG-push versus OpenConfig. What are two characteristics of synchronous calls to APIs? (Choose two.)
A) They block until a response is returned from the servers
B) They make an application less portable, so asynchronous calls are preferred
C) They add perceived latency to an application if data is not received
D) Calls are limited to specific programming languages
E) They do not block while waiting for the API to be processed
A) They block until a response is returned from the servers
B) They make an application less portable, so asynchronous calls are preferred
C) They add perceived latency to an application if data is not received
D) Calls are limited to specific programming languages
E) They do not block while waiting for the API to be processed

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
8
What are two characteristics of RPC API calls? (Choose two.)
A) They can be used only on network devices.
B) They use only UDP for communications.
C) Parameters can be passed to the calls.
D) They must use SSL/TLS.
E) They call a single function or service.
A) They can be used only on network devices.
B) They use only UDP for communications.
C) Parameters can be passed to the calls.
D) They must use SSL/TLS.
E) They call a single function or service.

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
9
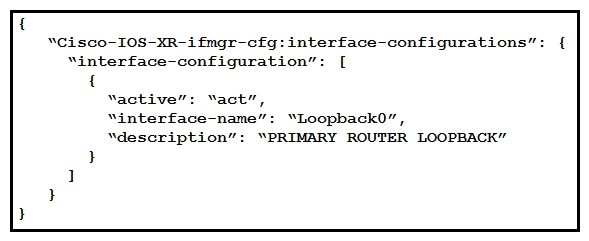 Refer to the exhibit. Which type of YANG container is described by the JSON instance provided?
Refer to the exhibit. Which type of YANG container is described by the JSON instance provided?A) interface-configurations
B) active
C) interface-name
D) description

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
10
Which two actions do Python virtual environments allow users to perform? (Choose two.)
A) Simplify the CI/CD pipeline when checking a project into a version control system, such as Git.
B) Efficiently port code between different languages, such as JavaScript and Python.
C) Run and simulate other operating systems within a development environment.
D) Quickly create any Python environment for testing and debugging purposes.
E) Quickly create an isolated Python environment with module dependencies.
A) Simplify the CI/CD pipeline when checking a project into a version control system, such as Git.
B) Efficiently port code between different languages, such as JavaScript and Python.
C) Run and simulate other operating systems within a development environment.
D) Quickly create any Python environment for testing and debugging purposes.
E) Quickly create an isolated Python environment with module dependencies.

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
11
The automation engineer must replace device configuration using RESTCONF. How is this configured using the Python library Requests ?
A) delete()
B) post()
C) put()
D) patch()
A) delete()
B) post()
C) put()
D) patch()

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
12
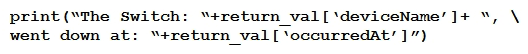
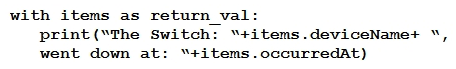
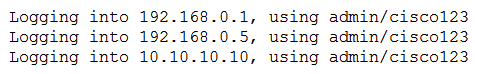
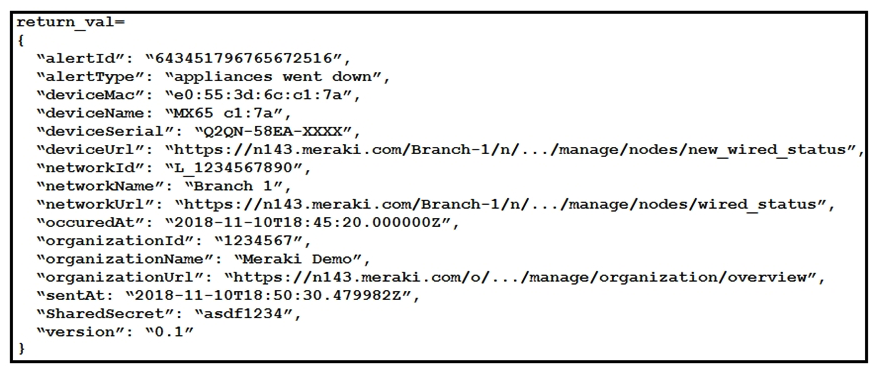 Refer to the exhibit. The task is to create a Python script to display an alert message when a Meraki MX Security Appliance goes down. The exhibit shows sample data that is received. Which Python snippet displays the device name and the time at which the switch went down?
Refer to the exhibit. The task is to create a Python script to display an alert message when a Meraki MX Security Appliance goes down. The exhibit shows sample data that is received. Which Python snippet displays the device name and the time at which the switch went down?A)
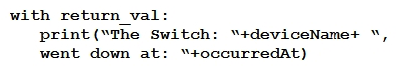
B)

C)
D)

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
13
![<strong> Refer to the exhibit. A Python script is used to configure a Cisco IOS XE device. The script must be updated to print the IP addresses of all the loopback interfaces. Which statement should be added before the loop?</strong> A) interfaces = response.json()[ietf-interfaces:interfaces] B) interface = response.json()[ietf-interfaces:interfaces] C) interface = response.json()[ietf-interfaces:interfaces][interface] D) interfaces = response.json()[ietf-interfaces:interfaces][interface]](https://d2lvgg3v3hfg70.cloudfront.net/C1178/11ec5360_dad2_8c49_8515_ef97b2e79f7c_C1178_00.jpg) Refer to the exhibit. A Python script is used to configure a Cisco IOS XE device. The script must be updated to print the IP addresses of all the loopback interfaces. Which statement should be added before the loop?
Refer to the exhibit. A Python script is used to configure a Cisco IOS XE device. The script must be updated to print the IP addresses of all the loopback interfaces. Which statement should be added before the loop?A) interfaces = response.json()["ietf-interfaces:interfaces"]
B) interface = response.json()["ietf-interfaces:interfaces"]
C) interface = response.json()["ietf-interfaces:interfaces"]["interface"]
D) interfaces = response.json()["ietf-interfaces:interfaces"]["interface"]

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
14
Which two Netmiko methods are used to configure a device? (Choose two.)
A) send_config()
B) send_control_from_file()
C) send_config_set()
D) send_command()
E) send_config_from_file()
A) send_config()
B) send_control_from_file()
C) send_config_set()
D) send_command()
E) send_config_from_file()

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
15
Which statement describe the difference between OpenConfig and native YANG data models?
A) Native models are designed to be independent of the underlying platform and are developed by vendors and standards bodies, such as the IETF.
B) Native models are developed by individual developers and designed to apply configurations on platforms.
C) OpenConfig models are developed by vendors and designed to integrate to features or configurations that are relevant only to that platform.
D) Native models are developed by vendors and designed to integrate to features or configurations that are relevant only to that platform.
A) Native models are designed to be independent of the underlying platform and are developed by vendors and standards bodies, such as the IETF.
B) Native models are developed by individual developers and designed to apply configurations on platforms.
C) OpenConfig models are developed by vendors and designed to integrate to features or configurations that are relevant only to that platform.
D) Native models are developed by vendors and designed to integrate to features or configurations that are relevant only to that platform.

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
16
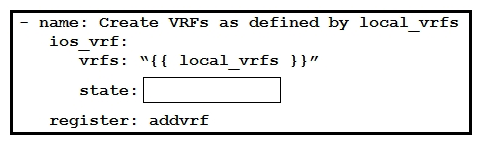 Refer to the exhibit. An engineer creates an Ansible playbook to configure VRF information using a local_vrfs variable. The code must be completed so that it can be tested. Which string completes the code?
Refer to the exhibit. An engineer creates an Ansible playbook to configure VRF information using a local_vrfs variable. The code must be completed so that it can be tested. Which string completes the code?A) present
B) up
C) on
D) active

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
17
What are two characteristics of synchronous calls to APIs? (Choose two.)
A) They can be used only with certain programming languages.
B) They make your application less portable, so asynchronous calls are preferred.
C) They can add perceived latency to your application if data is not received.
D) They block until a response is returned from the servers.
E) They do not block while waiting for the API to be processed.
A) They can be used only with certain programming languages.
B) They make your application less portable, so asynchronous calls are preferred.
C) They can add perceived latency to your application if data is not received.
D) They block until a response is returned from the servers.
E) They do not block while waiting for the API to be processed.

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
18
Which tag is required when establishing a YANG-push subscription with a Cisco IOS XE device?
A)
B)
C)
D)
A)
B)
C)
D)

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
19
Which statement is true for Cisco IOS XE Software?
A) RESTCONF supports JSON and XML and NETCONF supports XML.
B) RESTCONF supports XML and NETCONF supports JSON and XML.
C) RESTCONF and NETCONF supports JSON and XML.
D) RESTCONF supports XML and NETCONF supports JSON.
A) RESTCONF supports JSON and XML and NETCONF supports XML.
B) RESTCONF supports XML and NETCONF supports JSON and XML.
C) RESTCONF and NETCONF supports JSON and XML.
D) RESTCONF supports XML and NETCONF supports JSON.

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
20
Which function is available in NETCONF and unavailable in RESTCONF?
A) configuration changes are automatically activated
B) uses the YANG data models to communicate
C) supports JSON and data encoding
D) validates the content of a candidate datastore
A) configuration changes are automatically activated
B) uses the YANG data models to communicate
C) supports JSON and data encoding
D) validates the content of a candidate datastore

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
21
Which two API calls are used to trigger a device configuration sync in Cisco DNA Center? (Choose two.)
A) PUT /dna/intent/api/v1/network-device
B) PUT /dna/intent/api/v1/network-device/sync-all
C) PUT /dna/intent/api/v1/network-device/{networkDeviceId}/sync
D) PUT /dna/intent/api/v1/network-device/sync
E) POST /dna/intent/api/v1/network-device/{networkDeviceId}/sync
A) PUT /dna/intent/api/v1/network-device
B) PUT /dna/intent/api/v1/network-device/sync-all
C) PUT /dna/intent/api/v1/network-device/{networkDeviceId}/sync
D) PUT /dna/intent/api/v1/network-device/sync
E) POST /dna/intent/api/v1/network-device/{networkDeviceId}/sync

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
22
A network administrator must troubleshoot a network issue using Cisco DNA Center. Which API request helps to determine issue details, impacted hosts, or suggested actions for the resolution?
A) /dna/intent/v1/issues
B) /dna/intent/api/v1/issues
C) /dna/intent/v1/issue-enrichment-details
D) /dna/api/v1/client-health/issues
A) /dna/intent/v1/issues
B) /dna/intent/api/v1/issues
C) /dna/intent/v1/issue-enrichment-details
D) /dna/api/v1/client-health/issues

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
23
The Cisco DNA Center Sites API must be used to add a device to a site, but only the site name is available. Which API call must be used to retrieve the site identifier so that the device can be properly added to the network?
A) /dna/intent/api/site/siteId
B) /dna/intent/api/site
C) /dna/intent/api/v1/site
D) /dna/intent/api/v1/site/siteName
A) /dna/intent/api/site/siteId
B) /dna/intent/api/site
C) /dna/intent/api/v1/site
D) /dna/intent/api/v1/site/siteName

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
24
When accessing the /device-detail endpoint in Cisco DNA Center, what is an acceptable SearchBy parameter value?
A) platform type
B) IP address
C) software version
D) MAC address
A) platform type
B) IP address
C) software version
D) MAC address

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
25
Webhooks that are generated by Cisco DNA Center are REST calls with which properties?
A) JSON payload delivered via PUT
B) XML payload delivered via POST
C) JSON payload delivered via POST
D) XML payload delivered via PUT
A) JSON payload delivered via PUT
B) XML payload delivered via POST
C) JSON payload delivered via POST
D) XML payload delivered via PUT

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
26
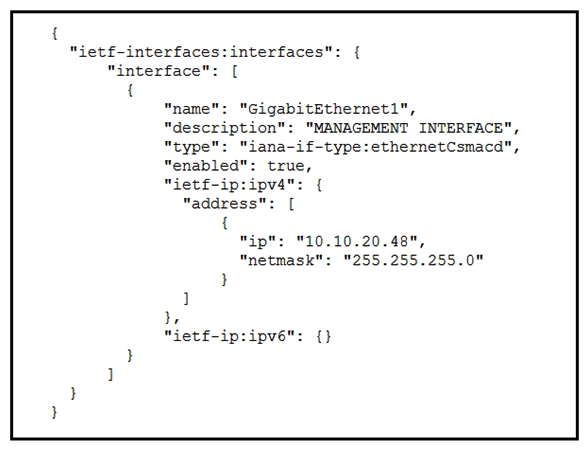 Refer to the exhibit. A RESTCONF GET request is sent to a Cisco IOS XE device. A portion of the response is shown in the exhibit. Which module name corresponds to the YANG model referenced in the request?
Refer to the exhibit. A RESTCONF GET request is sent to a Cisco IOS XE device. A portion of the response is shown in the exhibit. Which module name corresponds to the YANG model referenced in the request?A) ietf-interfaces:ietf-ipv4
B) iana-if-type:ethernetCsmacd
C) ietf-interfaces:interfaces
D) ietf-interfaces

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
27
![<strong> Refer to the exhibit. A Python script has been created that calls the Cisco SD-WAN vManage Device Inventory API to get the list of vEdges. The JSON data that returns to a Python dictionary has been converted and assigned to a variable named d. A portion of the JSON is shown in the exhibit. Which code will complete the expression hostname= to access the hostname?</strong> A) d[data][0][host-name] B) d[data][0][host-name] C) d(data)[0](host-name) D) d[host-name][data]{0}](https://d2lvgg3v3hfg70.cloudfront.net/C1178/11ec5360_dad3_9dc2_8515_2bfeb9ae0739_C1178_00.jpg) Refer to the exhibit. A Python script has been created that calls the Cisco SD-WAN vManage Device Inventory API to get the list of vEdges. The JSON data that returns to a Python dictionary has been converted and assigned to a variable named "d". A portion of the JSON is shown in the exhibit. Which code will complete the expression hostname= to access the hostname?
Refer to the exhibit. A Python script has been created that calls the Cisco SD-WAN vManage Device Inventory API to get the list of vEdges. The JSON data that returns to a Python dictionary has been converted and assigned to a variable named "d". A portion of the JSON is shown in the exhibit. Which code will complete the expression hostname= to access the hostname?A) d["data"][0]["host-name"]
B) d[data][0][host-name]
C) d("data")[0]("host-name")
D) d["host-name"]["data"]{"0"}

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
28
In which direction does the Cisco DNA Center Intent API communicate?
A) westbound
B) eastbound
C) northbound
D) southbound
A) westbound
B) eastbound
C) northbound
D) southbound

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
29
During a network outage, a network administrator used the Cisco SD-WAN vManage Troubleshooting Dashboard APIs to troubleshoot the cause of the issue. Which detail is captured during troubleshooting with these APIs?
A) VPN health
B) public cloud resources
C) connections summary
D) OMP connection health
A) VPN health
B) public cloud resources
C) connections summary
D) OMP connection health

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
30
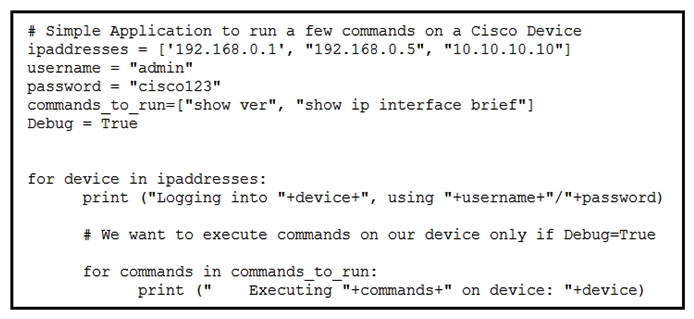 Refer to the exhibit. What is the expected output from the Python code?
Refer to the exhibit. What is the expected output from the Python code?A)
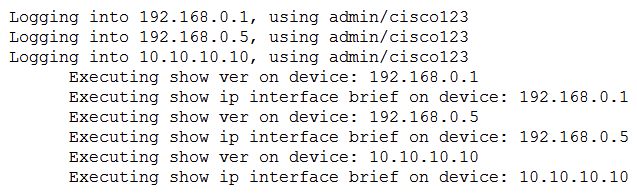
B)
C)

D)

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
31
Which action allows for creating a Python script to pull inventory for Cisco SD-WAN Viptela devices using the Viptela library in the code?
A) from urllib.request import Viptela
B) from viptela.devices import Viptela
C) from viptela.viptela import Viptela
D) from viptela.library import Viptela
A) from urllib.request import Viptela
B) from viptela.devices import Viptela
C) from viptela.viptela import Viptela
D) from viptela.library import Viptela

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
32
Which field must be completed in Cisco DNA Center when a network discovery is initiated?
A) SNMP read community string
B) Enable password
C) NETCONF port
D) Discovery type
A) SNMP read community string
B) Enable password
C) NETCONF port
D) Discovery type

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
33
What is primary purpose of using the Cisco SD-WAN vManage Certificate Management API?
A) to securely deploy vManage
B) to report an issue to Cisco TAC
C) to install signed certificates
D) to contact Enterprise Certificate Authority
A) to securely deploy vManage
B) to report an issue to Cisco TAC
C) to install signed certificates
D) to contact Enterprise Certificate Authority

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
34
![<strong> Refer to the exhibit. Cisco SD-WAN deployment must be troubleshooted using vManage APIs. A call to vEdge Hardware Health API returns the data in the exhibit (only a portion is shown). If this JSON is converted to a Python dictionary and assigned to the variable d , how the status is accessed that is indicated on line 16?</strong> A) d[data][0][statusList][0][status] B) d['data']['statusList']['status'] C) d{'data'}[0]{'statusList'}[0]{'status'} D) d['data'][0]['statusList'][0]['status']](https://d2lvgg3v3hfg70.cloudfront.net/C1178/11ec5360_dad3_4fa1_8515_132dc11a95a5_C1178_00.jpg) Refer to the exhibit. Cisco SD-WAN deployment must be troubleshooted using vManage APIs. A call to vEdge Hardware Health API returns the data in the exhibit (only a portion is shown). If this JSON is converted to a Python dictionary and assigned to the variable "d" , how the status is accessed that is indicated on line 16?
Refer to the exhibit. Cisco SD-WAN deployment must be troubleshooted using vManage APIs. A call to vEdge Hardware Health API returns the data in the exhibit (only a portion is shown). If this JSON is converted to a Python dictionary and assigned to the variable "d" , how the status is accessed that is indicated on line 16?A) d[data][0][statusList][0][status]
B) d['data']['statusList']['status']
C) d{'data'}[0]{'statusList'}[0]{'status'}
D) d['data'][0]['statusList'][0]['status']

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
35
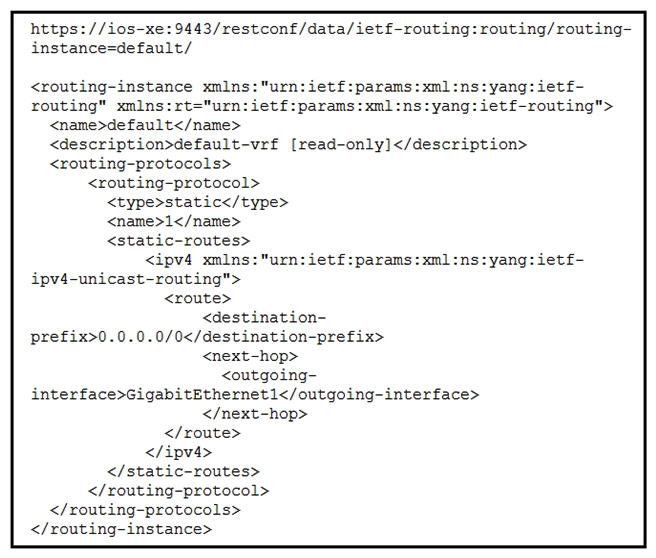 Refer to the exhibit. A RESTCONF GET request is sent to a Cisco IOS XE device. The base URL of the request and the response in XML format are shown in the exhibit. What is the YANG data node that is referenced in the response?
Refer to the exhibit. A RESTCONF GET request is sent to a Cisco IOS XE device. The base URL of the request and the response in XML format are shown in the exhibit. What is the YANG data node that is referenced in the response?A) route is a leaf list
B) static-routes is a container
C) static-routes is a list
D) routing-instance is a container

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
36
Which two API calls must be issued to attach a device template in Cisco SD-WAN? (Choose two.)
A) "monitor device action status" GET API request with the device ID to display the status of the attach action
B) "monitor device action status" GET API request with the process ID to display the status of the attach action
C) PUT call to initiate the attach action
D) POST call to initiate the attach action
E) GET call to initiate the attach action
A) "monitor device action status" GET API request with the device ID to display the status of the attach action
B) "monitor device action status" GET API request with the process ID to display the status of the attach action
C) PUT call to initiate the attach action
D) POST call to initiate the attach action
E) GET call to initiate the attach action

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
37
What are two characteristics of REST API calls? (Choose two.)
A) unencrypted
B) non-cacheable
C) stateless
D) implemented over HTTP
E) parameters passed in the headers
A) unencrypted
B) non-cacheable
C) stateless
D) implemented over HTTP
E) parameters passed in the headers

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
38
Which environment must be enabled to complete the Zero-Touch Provisioning process on a Cisco IOS XE device?
A) TCL
B) ZTP Open Service Container
C) EEM
D) Guest Shell
A) TCL
B) ZTP Open Service Container
C) EEM
D) Guest Shell

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
39
When the Cisco DNA Center Intent API is used as part of an automation process, what prompts receiving a HTTP 206 status code on a call?
A) The client authentication credentials that are included with the request are missing or invalid
B) The client made a request for partial content matching a range header
C) The client request was successful, but there is no content associated with the request
D) The client made a request that has been received but not yet acted upon
A) The client authentication credentials that are included with the request are missing or invalid
B) The client made a request for partial content matching a range header
C) The client request was successful, but there is no content associated with the request
D) The client made a request that has been received but not yet acted upon

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
40
What is the purpose of using the Cisco SD-WAN vManage Certificate Management API?
A) to generate a CSR
B) to allocate resources to the certificate server
C) to request a certificate from the certificate server
D) to enable vManage Center
A) to generate a CSR
B) to allocate resources to the certificate server
C) to request a certificate from the certificate server
D) to enable vManage Center

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
41
 Refer to the exhibit. Which two parameters are mandatory when the Cisco Meraki API is used to create a network? (Choose two.)
Refer to the exhibit. Which two parameters are mandatory when the Cisco Meraki API is used to create a network? (Choose two.)A) timezone
B) disableMyMerakiCom
C) type
D) tags
E) organizationId

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
42
What is the maximum number of switches that can be stacked using Cisco StackWise?
A) 4
B) 5
C) 8
D) 9
E) 10
F) 13
A) 4
B) 5
C) 8
D) 9
E) 10
F) 13

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
43
Which Cisco feature can be run on a Cisco router that terminates a WAN connection, to gather and provide WAN circuit information that helps switchover to dynamically back up the WAN circuit?
A) Cisco Express Forwarding
B) IP SLA
C) passive interface
D) traffic shaping
A) Cisco Express Forwarding
B) IP SLA
C) passive interface
D) traffic shaping

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
44
Which URI removes an administrator from a Meraki network using an API call?
A) DELETE https://api/meraki.com/api/v0/organizations//admins/
B) DELETE https://api/meraki.com/api/v0/admins/
C) PUT https://api/meraki.com/api/v0/organizations//admins/?delete=
D) DELETE https://api/meraki.com/api/v0/organizations//admins/
A) DELETE https://api/meraki.com/api/v0/organizations/
B) DELETE https://api/meraki.com/api/v0/admins/
C) PUT https://api/meraki.com/api/v0/organizations/
D) DELETE https://api/meraki.com/api/v0/organizations/

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
45
With the MV Sense API, which REST endpoint provides LUX level?
A) /merakimv/XXXX-XXXX-XXXX/light
B) /merakimv/XXXX-XXXX-XXXX/raw_detections
C) /merakimv/XXXX-XXXX-XXXX/0
D) /merakimv/XXXX-XXXX-XXXX/zones
A) /merakimv/XXXX-XXXX-XXXX/light
B) /merakimv/XXXX-XXXX-XXXX/raw_detections
C) /merakimv/XXXX-XXXX-XXXX/0
D) /merakimv/XXXX-XXXX-XXXX/zones

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
46
Which two types of solution are built with the Meraki Location Scanning API? (Choose two.)
A) networking automation
B) mapping
C) guest Wi-Fi
D) Sense
E) wayfinder
A) networking automation
B) mapping
C) guest Wi-Fi
D) Sense
E) wayfinder

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
47
Which HTTP request is valid to create a new wireless network called "Demo Wireless Network" in the organization "QASD-EROA-MKAW"?
A)
B)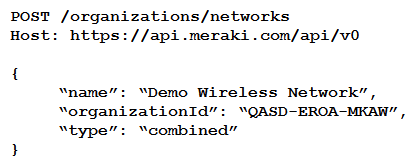
C)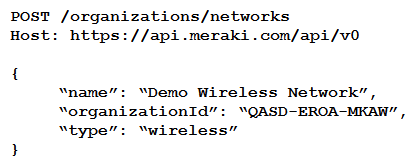
D)
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
48
 Refer to the exhibit. A Python script must be created to deactivate vSmart Policy Cisco SD-WAN vManage Configuration APIs. The documentation states the URL is as shown in the exhibit for this REST call using POST, and that "policyId" is a required request parameter. Which line of Python code makes this call, assuming the variable "s" is a valid Requests session object and the variable "policy-id" is the policyId?
Refer to the exhibit. A Python script must be created to deactivate vSmart Policy Cisco SD-WAN vManage Configuration APIs. The documentation states the URL is as shown in the exhibit for this REST call using POST, and that "policyId" is a required request parameter. Which line of Python code makes this call, assuming the variable "s" is a valid Requests session object and the variable "policy-id" is the policyId?A) s.port('https://vmanage:8443/dataservice/template/policy/vsmart/activate?policyId=%s' % policy_id)
B) s.port('https://vmanage:8443/dataservice/template/policy/vsmart/activate/%s' % policy_id)
C) s.port('https://vmanage:8443/dataservice/template/policy/vsmart/activate&policyId=%s' % policy_id)
D) s.port('https://vmanage:8443/dataservice/template/policy/vsmart/activate/', data = {'policyId': policy_id})

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
49
A network engineer wants to connect two sites via a WAN technology and to securely pass multicast traffic over this WAN technology. Which WAN technology should be configured?
A) IPsec
B) GRE
C) pure MPLS
D) GRE over IPsec
A) IPsec
B) GRE
C) pure MPLS
D) GRE over IPsec

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
50
What two features are inherent advantages of MPLS VPN services? (Choose two.)
A) service providers can provide additional services
B) virtual private networks segment traffic and ensure privacy
C) easier to troubleshoot than Layer 2 WAN technologies
D) faster data transfer speeds at lower costs
E) functions without Cisco Express Forwarding
A) service providers can provide additional services
B) virtual private networks segment traffic and ensure privacy
C) easier to troubleshoot than Layer 2 WAN technologies
D) faster data transfer speeds at lower costs
E) functions without Cisco Express Forwarding

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
51
Which Python snippet receives a Meraki webhook request?
A)
B)
C)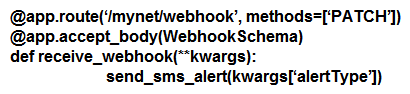
D)
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
52
Which CLI command do you use to shut down the 2.4 GHz radio of the Floor1_AP1 AP on a Cisco 3850 Switch?
A) ap name Floor1_AP1 dot11 shutdown 24ghz
B) ap name Floor1_AP1 dot11 5ghz shutdown
C) ap name Floor1_AP1 dot11 24ghz shutdown
D) ap name Floor1_AP1 shutdown dot11 24ghz
A) ap name Floor1_AP1 dot11 shutdown 24ghz
B) ap name Floor1_AP1 dot11 5ghz shutdown
C) ap name Floor1_AP1 dot11 24ghz shutdown
D) ap name Floor1_AP1 shutdown dot11 24ghz

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
53
Which two WAN technologies support IEEE 802.1Q, site-to-site connectivity, and point-to-point connectivity between two offices? (Choose two.)
A) Ethernet over MPLS
B) VPLS
C) Layer 3 MPLS
D) DSL
E) cable
A) Ethernet over MPLS
B) VPLS
C) Layer 3 MPLS
D) DSL
E) cable

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
54
Which two factors influence the location accuracy of a device using Scanning APIs? (Choose two.)
A) AP placement
B) device manufacturer/OS
C) client device orientation
D) battery life of the device
E) amount of device antennas
A) AP placement
B) device manufacturer/OS
C) client device orientation
D) battery life of the device
E) amount of device antennas

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
55
Which protocol should be run on the LAN side of two edge routers (that are terminating primary and backup WAN circuits) to provide quick failover in case of primary WAN circuit failure?
A) VTP
B) STP
C) VRRP
D) RIP
A) VTP
B) STP
C) VRRP
D) RIP

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
56
Which REST endpoint is used to create a Cisco Meraki network?
A) POST /organizations/{organizationId}/networks
B) PATCH /networks{networkId}
C) PUT /organizations/{organizationId}/networks
D) POST /networks{networkId}
A) POST /organizations/{organizationId}/networks
B) PATCH /networks{networkId}
C) PUT /organizations/{organizationId}/networks
D) POST /networks{networkId}

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
57
Which two methods are available to connect a Cisco IOS device to an active directory domain for authentication? (Choose two.)
A) Lightweight Directory Access Protocol
B) DNS Based Authentication of Named Entities
C) Microsoft Challenge-Handshake Authentication Protocol
D) RADIUS server
E) Directory Access Protocol
A) Lightweight Directory Access Protocol
B) DNS Based Authentication of Named Entities
C) Microsoft Challenge-Handshake Authentication Protocol
D) RADIUS server
E) Directory Access Protocol

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
58
Refer to the exhibit. 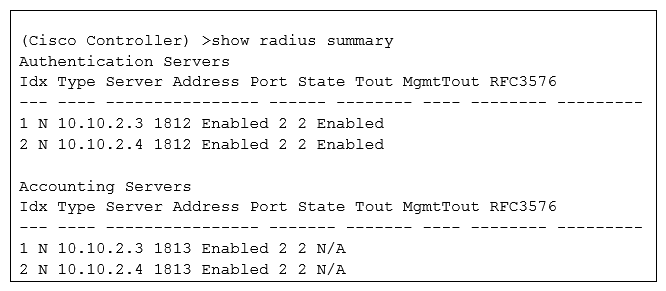 An engineer utilizing ISE as the wireless AAA service noticed that the accounting process on the server at 10.10.2.3 has failed, but authentication process is still functional. Which ISE nodes receive WLC RADIUS traffic, using the CLI output and assuming the WLAN uses the servers in their indexed order?
An engineer utilizing ISE as the wireless AAA service noticed that the accounting process on the server at 10.10.2.3 has failed, but authentication process is still functional. Which ISE nodes receive WLC RADIUS traffic, using the CLI output and assuming the WLAN uses the servers in their indexed order?
A) authentication to 10.10.2.4, accounting to 10.10.2.3.
B) authentication to 10.10.2.3, accounting to 10.10.2.3.
C) authentication to 10.10.2.4, accounting to 10.10.2.4.
D) authentication to 10.10.2.3, accounting to 10.10.2.4.
 An engineer utilizing ISE as the wireless AAA service noticed that the accounting process on the server at 10.10.2.3 has failed, but authentication process is still functional. Which ISE nodes receive WLC RADIUS traffic, using the CLI output and assuming the WLAN uses the servers in their indexed order?
An engineer utilizing ISE as the wireless AAA service noticed that the accounting process on the server at 10.10.2.3 has failed, but authentication process is still functional. Which ISE nodes receive WLC RADIUS traffic, using the CLI output and assuming the WLAN uses the servers in their indexed order?A) authentication to 10.10.2.4, accounting to 10.10.2.3.
B) authentication to 10.10.2.3, accounting to 10.10.2.3.
C) authentication to 10.10.2.4, accounting to 10.10.2.4.
D) authentication to 10.10.2.3, accounting to 10.10.2.4.

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
59
Which CLI command do you use on Cisco IOS XE Software to put the AP named Floor1_AP1 back in the default AP group?
A) ap Floor1_AP1 ap-groupname default-group
B) ap name Floor1_AP1 apgroup default-group
C) ap name Floor1_AP1 ap-groupname default-group
D) ap name Floor1_AP1 ap-groupname default
A) ap Floor1_AP1 ap-groupname default-group
B) ap name Floor1_AP1 apgroup default-group
C) ap name Floor1_AP1 ap-groupname default-group
D) ap name Floor1_AP1 ap-groupname default

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
60
A company requires redundancy for its multihomed BGP external connections. What two features can be configured on the WAN routers to automate failover for both outbound and inbound traffic? (Choose two.)
A) AS path prepending
B) local preference
C) floating static route
D) HSRP
E) MED
F) weight
A) AS path prepending
B) local preference
C) floating static route
D) HSRP
E) MED
F) weight

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
61
Which two features are foundations of a software-defined network instead of a traditional network? (Choose two.)
A) control plane and data plane are tightly coupled
B) build upon a robust software stack
C) requires device by device-level configurations
D) automated through expressed intent to a software controller
E) requires significant physical hardware resources
A) control plane and data plane are tightly coupled
B) build upon a robust software stack
C) requires device by device-level configurations
D) automated through expressed intent to a software controller
E) requires significant physical hardware resources

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
62
Which curl command is used to update the SNMP community of network ID "1234567" to read-only?
A)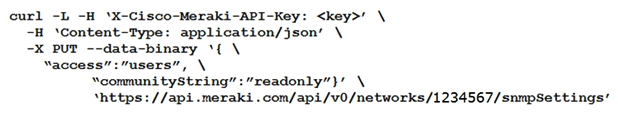
B)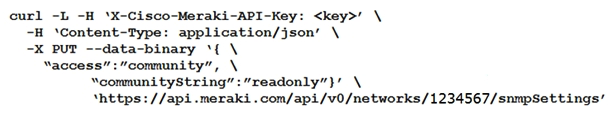
C)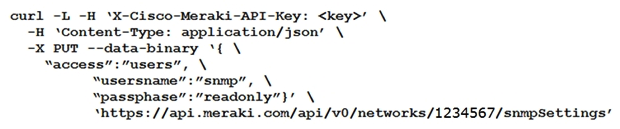
D)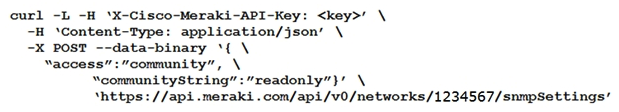
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
63
You are designing a scalable cluster that contains a combination of Cisco APIC-M and APIC-L controllers. Which controller provides the scalability used in the cluster?
A) APIC-M
B) APIC-EM
C) combination of APIC-M and APIC -I
D) APIC-L
A) APIC-M
B) APIC-EM
C) combination of APIC-M and APIC -I
D) APIC-L

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
64
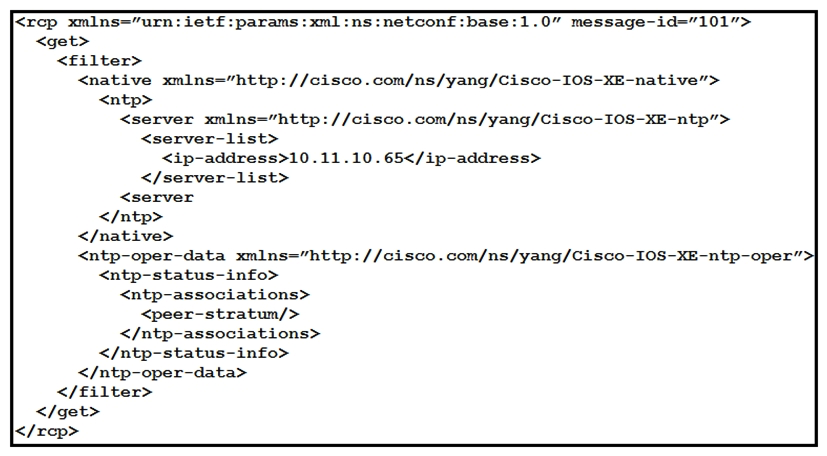 Refer to the exhibit. How many YANG models does the NETCONF
Refer to the exhibit. How many YANG models does the NETCONF A) one
B) two
C) three
D) four

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
65
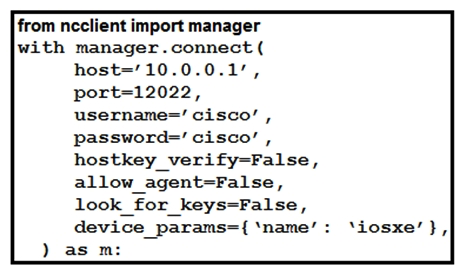 Refer to the exhibit. What is the correct ncclient method to use to collect the running configuration of a Cisco IOS XE device that uses NETCONF?
Refer to the exhibit. What is the correct ncclient method to use to collect the running configuration of a Cisco IOS XE device that uses NETCONF?A) config=m.copy_config(source='running')
B) config=m.get(source='running')
C) config=m.collect_config(source='running')
D) config=m.get_config(source='running')

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
66
Recently, the WAN links between the headquarters and branch offices have been slow under peak congestion, yet multiple alternate WAN paths exist that are not always congested. What technology can allow traffic to be routed in a more informed manner to utilize transport characteristics such as delay, loss, or link load?
A) performance routing
B) static routing
C) on demand routing
D) policy based routing
A) performance routing
B) static routing
C) on demand routing
D) policy based routing

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
67
Which benefit of using VRRP v3 as compared to VRRP v2 is true?
A) supports authentication
B) supports preemption
C) supports stateful switchover
D) supports IPv4 and IPv6 in separate VRRP groups
A) supports authentication
B) supports preemption
C) supports stateful switchover
D) supports IPv4 and IPv6 in separate VRRP groups

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
68
Refer to the exhibit. 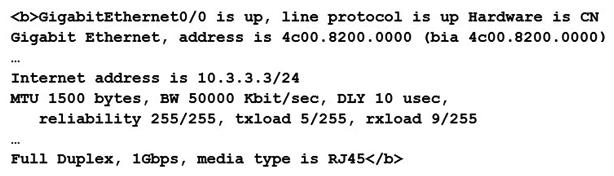 An engineering team is analyzing the WAN connection for a site that has a 50 Mbps Ethernet circuit. Which technology should be used to keep the router from overrunning the carrier's 50 Mbps rate?
An engineering team is analyzing the WAN connection for a site that has a 50 Mbps Ethernet circuit. Which technology should be used to keep the router from overrunning the carrier's 50 Mbps rate?
A) Access Control List
B) Shaping
C) Policing
D) Rate-Limit
 An engineering team is analyzing the WAN connection for a site that has a 50 Mbps Ethernet circuit. Which technology should be used to keep the router from overrunning the carrier's 50 Mbps rate?
An engineering team is analyzing the WAN connection for a site that has a 50 Mbps Ethernet circuit. Which technology should be used to keep the router from overrunning the carrier's 50 Mbps rate?A) Access Control List
B) Shaping
C) Policing
D) Rate-Limit

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
69
Which description of how virtual MAC addresses are assigned to the members of a GLBP group is true?
A) Each device assigns its own address
B) The AVG assigns the addresses
C) The AVF assigns the addresses
D) The device that has the highest IP address assigns the addresses
A) Each device assigns its own address
B) The AVG assigns the addresses
C) The AVF assigns the addresses
D) The device that has the highest IP address assigns the addresses

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
70
What does the command boot ipxe forever switch 1 perform when executed on a Cisco IOS XE device?
A) It continuously sends DHCP requests for iPXE until the device boots with an image.
B) It continuously sends DNS requests for iPXE until the device restarts.
C) It continuously sends DNS requests for iPXE until the device boots with an image.
D) It continuously sends DHCP requests for iPXE until the device restarts.
A) It continuously sends DHCP requests for iPXE until the device boots with an image.
B) It continuously sends DNS requests for iPXE until the device restarts.
C) It continuously sends DNS requests for iPXE until the device boots with an image.
D) It continuously sends DHCP requests for iPXE until the device restarts.

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
71
A customer has several remote sites connected with the HQ via microwave links. An engineer has been asked to propose a backup WAN connectivity for these sites with these requirements: Physical WAN connectivity is not available for most of these sites. A low-cost and fast-to-implement backup solution must be deployed. Bandwidth needs for the backup link are low. Users can tolerate a WAN outage of up to 2 hours. Which backup WAN link type does the engineer recommend?
A) LTE
B) 802.16 WiMAX
C) laser link
D) 802.15.1 Bluetooth
A) LTE
B) 802.16 WiMAX
C) laser link
D) 802.15.1 Bluetooth

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
72
![<strong> Refer to the exhibit. Which NETCONF statement type is represented by +--rw address* [ip] ?</strong> A) list B) leaf-list C) container D) submodule](https://d2lvgg3v3hfg70.cloudfront.net/C1178/11ec5360_dad6_0eda_8515_d36dfcb79229_C1178_00.jpg) Refer to the exhibit. Which NETCONF statement type is represented by +--rw address* [ip] ?
Refer to the exhibit. Which NETCONF statement type is represented by +--rw address* [ip] ?A) list
B) leaf-list
C) container
D) submodule

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
73
A new project called "device_status" must be stored in a central Git repository called "device_status" with the first file named "device_status.py". The Git repository is created using the account python_programmer. Which set of commands inserts the project into Git?
A)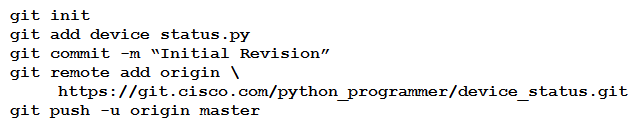
B)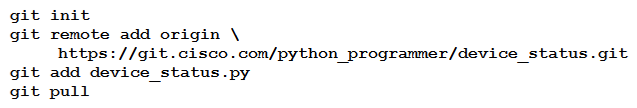
C)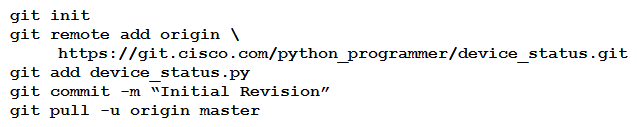
D)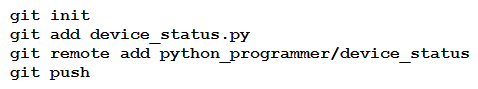
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
74
Which two security measures must an engineer follow when implementing Layer 2 and Layer 3 network design? (Choose two.)
A) Utilize DHCP snooping on a per VLAN basis and apply ip dhcp snooping untrusted on all ports. Utilize DHCP snooping on a per VLAN basis and apply ip dhcp snooping untrusted on all ports.
B) Utilize the native VLAN only on trunk ports to reduce the risk of a Double-Tagged 802.1q VLAN hopping attack.
C) Utilize an access list to prevent the use of ARP to modify entries to the table.
D) Utilize private VLANs and ensure that all ports are part of the isolated port group.
E) Utilize the ARP inspection feature to help prevent the misuse of gARP.
A) Utilize DHCP snooping on a per VLAN basis and apply ip dhcp snooping untrusted on all ports. Utilize DHCP snooping on a per VLAN basis and apply ip dhcp snooping untrusted on all ports.
B) Utilize the native VLAN only on trunk ports to reduce the risk of a Double-Tagged 802.1q VLAN hopping attack.
C) Utilize an access list to prevent the use of ARP to modify entries to the table.
D) Utilize private VLANs and ensure that all ports are part of the isolated port group.
E) Utilize the ARP inspection feature to help prevent the misuse of gARP.

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
75
While planning a new WAN design, an engineering team is asked to use software defined networking as part of the wide area network strategy. Which SDN controller allows for applications iWAN control, Plug and Play and Enterprise Service Automation?
A) Enterprise NFV
B) APIC
C) Wide Area Application Service
D) APIC-EM
A) Enterprise NFV
B) APIC
C) Wide Area Application Service
D) APIC-EM

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
76
Due to financial constraints, an engineer is forced to use WAN edge routers with limited memory. BGP is used to exchange routing information with external customers. Which two additional actions are taken in this design? (Choose two.)
A) Utilize iBGP to reduce memory utilization.
B) Allow any BGP route that has external customer AS in the AS path.
C) Filter any BGP routes that were not originated in external customer AS.
D) Implement the Maximum-Prefix feature.
E) Permit only specific routes from the external customers.
A) Utilize iBGP to reduce memory utilization.
B) Allow any BGP route that has external customer AS in the AS path.
C) Filter any BGP routes that were not originated in external customer AS.
D) Implement the Maximum-Prefix feature.
E) Permit only specific routes from the external customers.

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
77
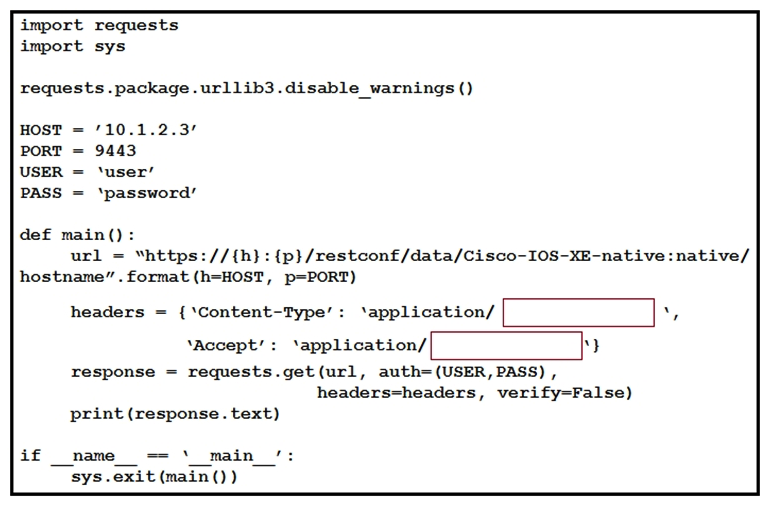 Refer to the exhibit. An engineer creates a Python script using RESTCONF to display hostname information. The code must be completed so that it can be tested. Which string completes the highlighted areas in the exhibit?
Refer to the exhibit. An engineer creates a Python script using RESTCONF to display hostname information. The code must be completed so that it can be tested. Which string completes the highlighted areas in the exhibit?A) yang-data+json
B) yang +json
C) yang.data+json
D) json

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
78
A customer has an existing WAN circuit with a capacity of 10 Mbps. The circuit has 6 Mbps of various user traffic and 5 Mbps of real-time audio traffic on average. Which two measures could be taken to avoid loss of real time traffic? (Choose two.)
A) Police the traffic to 3.3 Mbps and allow excess traffic to be remarked to the default queue.
B) Configure congestion avoidance mechanism WRED within the priority queue.
C) Ensure that real time traffic is prioritized over other traffic.
D) Police the traffic to 5 Mbps and allow excess traffic to be remarked to the default queue.
E) Increase the WAN circuit bandwidth.
A) Police the traffic to 3.3 Mbps and allow excess traffic to be remarked to the default queue.
B) Configure congestion avoidance mechanism WRED within the priority queue.
C) Ensure that real time traffic is prioritized over other traffic.
D) Police the traffic to 5 Mbps and allow excess traffic to be remarked to the default queue.
E) Increase the WAN circuit bandwidth.

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
79
Refer to the exhibit. 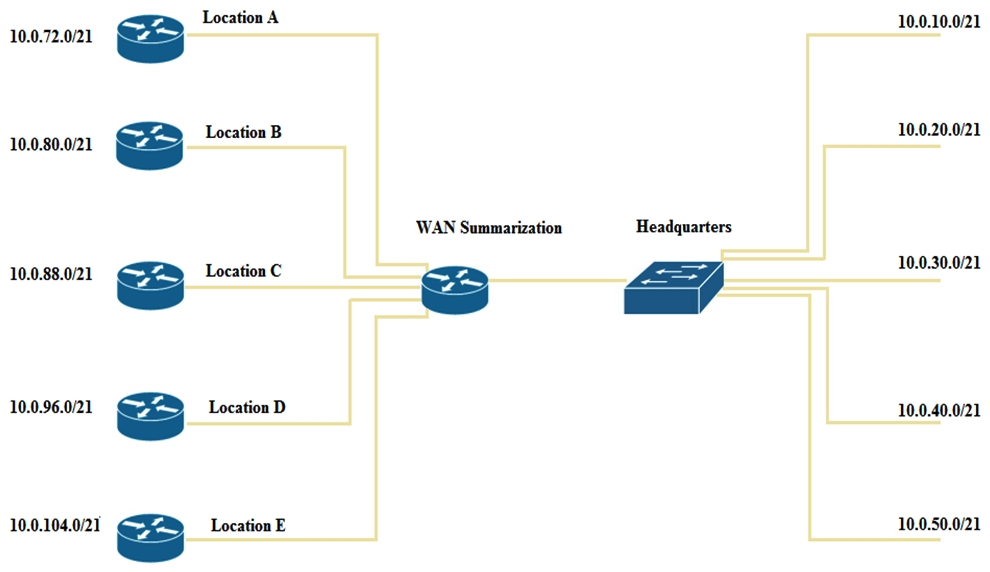 An engineer must apply IP addressing to five new WAN sites and chooses the new subnets pictured. The previous administrator applied the addressing at Headquarters. What is the minimum summary range to cover the existing WAN sites while also allowing for three additional WAN sites of the same size, for future growth?
An engineer must apply IP addressing to five new WAN sites and chooses the new subnets pictured. The previous administrator applied the addressing at Headquarters. What is the minimum summary range to cover the existing WAN sites while also allowing for three additional WAN sites of the same size, for future growth?
A) 10.0.60.0/18
B) 10.0.64.0/18
C) 10.0.64.0/17
D) 10.0.0.0/17
 An engineer must apply IP addressing to five new WAN sites and chooses the new subnets pictured. The previous administrator applied the addressing at Headquarters. What is the minimum summary range to cover the existing WAN sites while also allowing for three additional WAN sites of the same size, for future growth?
An engineer must apply IP addressing to five new WAN sites and chooses the new subnets pictured. The previous administrator applied the addressing at Headquarters. What is the minimum summary range to cover the existing WAN sites while also allowing for three additional WAN sites of the same size, for future growth?A) 10.0.60.0/18
B) 10.0.64.0/18
C) 10.0.64.0/17
D) 10.0.0.0/17

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck
80
A customer has several small to medium-sized remote branches and with these specific per-site requirements: WAN link redundancy no need for consistent end-to-end QoS (QoS is applied to the edge routers.) low cost for WAN links no strict SLA requirements for the WAN links Which type of WAN edge connectivity design does an engineer propose?
A) dual-homed Internet with dual edge routers running a hub-and-spoke VPN topology
B) dual-homed WAN MPLS and Internet links via dual edge routers
C) dual-homed WAN MPLS with a single edge router
D) dual-homed Internet with a single edge router running a site-to-site VPN topology
A) dual-homed Internet with dual edge routers running a hub-and-spoke VPN topology
B) dual-homed WAN MPLS and Internet links via dual edge routers
C) dual-homed WAN MPLS with a single edge router
D) dual-homed Internet with a single edge router running a site-to-site VPN topology

Unlock Deck
Unlock for access to all 84 flashcards in this deck.
Unlock Deck
k this deck



