Deck 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/101
Play
Full screen (f)
Deck 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)
1
The IT manager is asking the wireless team to get a report for all guest user associations during the past two weeks. In which two formats can Cisco Prime save this report? (Choose two.)
A) CSV
B) PDF
C) XLS
D) DOC
E) plain text
A) CSV
B) PDF
C) XLS
D) DOC
E) plain text
CSV
PDF
2
An engineer configures the wireless LAN controller to perform 802.1x user authentication. Which configuration must be enabled to ensure that client devices can connect to the wireless, even when WLC cannot communicate with the RADIUS?
A) pre-authentication
B) local EAP
C) authentication caching
D) Cisco Centralized Key Management
A) pre-authentication
B) local EAP
C) authentication caching
D) Cisco Centralized Key Management
local EAP
3
A network engineer observes a spike in controller CPU overhead and overall network utilization after multicast is enabled on a controller with 500 APs. Which feature connects the issue?
A) controller IGMP snooping
B) multicast AP multicast mode
C) broadcast forwarding
D) unicast AP multicast mode
A) controller IGMP snooping
B) multicast AP multicast mode
C) broadcast forwarding
D) unicast AP multicast mode
multicast AP multicast mode
4
On a branch office deployment, it has been noted that if the FlexConnect AP is in standalone mode and loses connection to the WLC, all clients are disconnected, and the SSID is no longer advertised. Considering that FlexConnect local switching is enabled, which setting is causing this behavior?
A) ISE NAC is enabled
B) 802.11r Fast Transition is enabled
C) Client Exclusion is enabled
D) FlexConnect Local Auth is disabled
A) ISE NAC is enabled
B) 802.11r Fast Transition is enabled
C) Client Exclusion is enabled
D) FlexConnect Local Auth is disabled

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
5
Refer to the exhibit. An engineer must connect a fork lift via a WGB to a wireless network and must authenticate the WGB certificate against the RADIUS server. Which three steps are required for this configuration? (Choose three.) 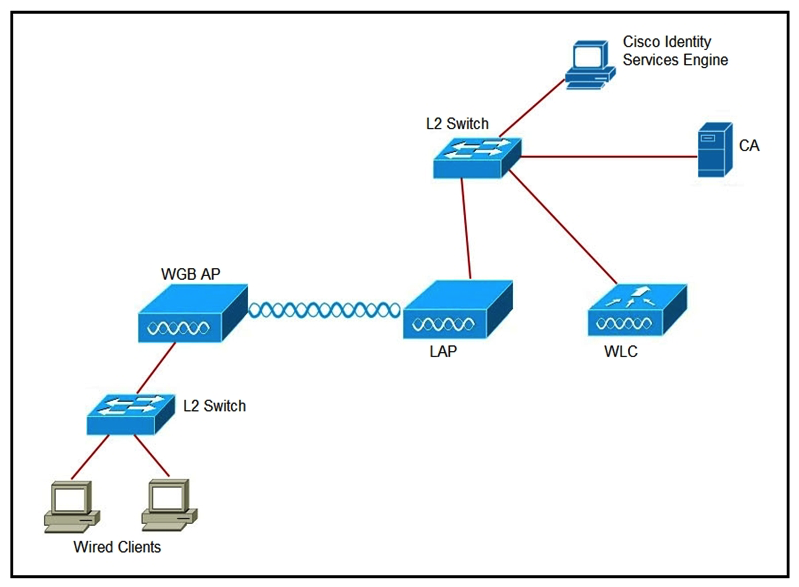
A) Configure the certificate, WLAN, and radio interface on WGB.
B) Configure the certificate on the WLC.
C) Configure WLAN to authenticate using ISE.
D) Configure the access point with the root certificate from ISE.
E) Configure WGB as a network device in ISE.
F) Configure a policy on ISE to allow devices to connect that validate the certificate.

A) Configure the certificate, WLAN, and radio interface on WGB.
B) Configure the certificate on the WLC.
C) Configure WLAN to authenticate using ISE.
D) Configure the access point with the root certificate from ISE.
E) Configure WGB as a network device in ISE.
F) Configure a policy on ISE to allow devices to connect that validate the certificate.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
6
What is the default IEEE 802.1x AP authentication configuration on a Cisco Catalyst 9800 Series Wireless Controller?
A) EAP-PEAP with 802.1x port authentication
B) EAP-TLS with 802.1x port authentication
C) EAP-FAST with CAPWAP DTLS + port authentication
D) EAP-FAST with CAPWAP DTLS
A) EAP-PEAP with 802.1x port authentication
B) EAP-TLS with 802.1x port authentication
C) EAP-FAST with CAPWAP DTLS + port authentication
D) EAP-FAST with CAPWAP DTLS

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
7
All APs are receiving multicast traffic, instead of only the APs that need it. What is the cause of this problem?
A) The multicast group includes all APs
B) The wrong multicast address was used
C) The multicast group is assigned the wrong VLAN
D) Multicast IGMP snooping is not enabled
A) The multicast group includes all APs
B) The wrong multicast address was used
C) The multicast group is assigned the wrong VLAN
D) Multicast IGMP snooping is not enabled

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
8
An engineer wants the wireless voice traffic class of service to be used to determine the queue order for packets received, and then have the differentiated services code point set to match when it is resent to another port on the switch. Which configuration is required in the network?
A) Platinum QoS configured on the WLAN
B) WMM set to required on the WLAN
C) msl qos trust dscp configured on the controller switch port msl qos trust dscp configured on the controller switch port
D) msl qos trust cos configured on the controller switch port msl qos trust cos
A) Platinum QoS configured on the WLAN
B) WMM set to required on the WLAN
C) msl qos trust dscp configured on the controller switch port msl qos trust dscp configured on the controller switch port
D) msl qos trust cos configured on the controller switch port msl qos trust cos

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
9
Which two statements about the requirements for a Cisco Hyperlocation deployment are true? (Choose two.)
A) After enabling Cisco Hyperlocation on Cisco CMX, the APs and the wireless LAN controller must be restarted.
B) NTP can be configured, but that is not recommended.
C) The Cisco Hyperlocation feature must be enabled on the wireless LAN controller and Cisco CMX.
D) The Cisco Hyperlocation feature must be enabled only on the wireless LAN controller.
E) If the Cisco CMX server is a VM, a high-end VM is needed for Cisco Hyperlocation deployments.
A) After enabling Cisco Hyperlocation on Cisco CMX, the APs and the wireless LAN controller must be restarted.
B) NTP can be configured, but that is not recommended.
C) The Cisco Hyperlocation feature must be enabled on the wireless LAN controller and Cisco CMX.
D) The Cisco Hyperlocation feature must be enabled only on the wireless LAN controller.
E) If the Cisco CMX server is a VM, a high-end VM is needed for Cisco Hyperlocation deployments.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
10
A user is trying to connect to a wireless network that is configured for WPA2-Enterprise security using a corporate laptop. The CA certificate for the authentication server has been installed on the Trusted Root Certification Authorities store on the laptop. The user has been prompted to enter the credentials multiple times, but the authentication has not succeeded. What is causing the issue?
A) There is an IEEE invalid 802.1X authentication policy on the authentication server.
B) The user Active Directory account is locked out after several failed attempts.
C) There is an invalid 802.1X authentication policy on the authenticator.
D) The laptop has not received a valid IP address from the wireless controller.
A) There is an IEEE invalid 802.1X authentication policy on the authentication server.
B) The user Active Directory account is locked out after several failed attempts.
C) There is an invalid 802.1X authentication policy on the authenticator.
D) The laptop has not received a valid IP address from the wireless controller.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
11
Which devices can be tracked with the Cisco Context Aware Services?
A) wired and wireless devices
B) wireless devices
C) wired devices
D) Cisco certified wireless devices
A) wired and wireless devices
B) wireless devices
C) wired devices
D) Cisco certified wireless devices

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
12
An engineer is performing a Cisco Hyperlocation accuracy test and executes the cmxloc start command on Cisco CMX. Which two parameters are relevant? (Choose two.)
A) X, Y real location
B) client description
C) AP name
D) client MAC address
E) WLC IP address
A) X, Y real location
B) client description
C) AP name
D) client MAC address
E) WLC IP address

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
13
Which QoS level is recommended for guest services?
A) gold
B) bronze
C) platinum
D) silver
A) gold
B) bronze
C) platinum
D) silver

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
14
Which two restrictions are in place with regards to configuring mDNS? (Choose two.)
A) mDNS uses only UDP port 5436 as a destination port.
B) mDNS cannot use UDP port 5353 as the destination port.
C) mDNS is not supported on FlexConnect APs with a locally switched WLAN.
D) Controller software must be newer than 7.0.6+.
E) mDNS is not supported over IPv6.
A) mDNS uses only UDP port 5436 as a destination port.
B) mDNS cannot use UDP port 5353 as the destination port.
C) mDNS is not supported on FlexConnect APs with a locally switched WLAN.
D) Controller software must be newer than 7.0.6+.
E) mDNS is not supported over IPv6.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
15
An engineer must implement rogue containment for an SSID. What is the maximum number of APs that should be used for containment?
A) 1
B) 2
C) 3
D) 4
A) 1
B) 2
C) 3
D) 4

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
16
Which two events are outcomes of a successful RF jamming attack? (Choose two.)
A) disruption of WLAN services
B) unauthentication association
C) deauthentication broadcast
D) deauthentication multicast
E) physical damage to AP hardware
A) disruption of WLAN services
B) unauthentication association
C) deauthentication broadcast
D) deauthentication multicast
E) physical damage to AP hardware

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
17
A wireless engineer must implement a corporate wireless network for a large company in the most efficient way possible. The wireless network must support 32 VLANs for 300 employees in different departments. Which solution must the engineer choose?
A) Configure a second WLC to support half of the APs in the deployment.
B) Configure one single SSID and implement Cisco ISE for VLAN assignment according to different user roles.
C) Configure different AP groups to support different VLANs, so that all of the WLANs can be broadcast on both radios.
D) Configure 16 WLANs to be broadcast on the 2.4-GHz band and 16 WLANs to be broadcast on the 5.0-GHz band.
A) Configure a second WLC to support half of the APs in the deployment.
B) Configure one single SSID and implement Cisco ISE for VLAN assignment according to different user roles.
C) Configure different AP groups to support different VLANs, so that all of the WLANs can be broadcast on both radios.
D) Configure 16 WLANs to be broadcast on the 2.4-GHz band and 16 WLANs to be broadcast on the 5.0-GHz band.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
18
An engineer must use Cisco AVC on a Cisco WLC to prioritize Cisco IP cameras that use the wireless network. Which element do you configure in a rule?
A) permit-ACL
B) WMM required
C) mark
D) rate-limit
A) permit-ACL
B) WMM required
C) mark
D) rate-limit

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
19
What is the maximum time range that can be viewed on the Cisco DNA Center issues and alarms page?
A) 3 hours
B) 24 hours
C) 3 days
D) 7 days
A) 3 hours
B) 24 hours
C) 3 days
D) 7 days

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
20
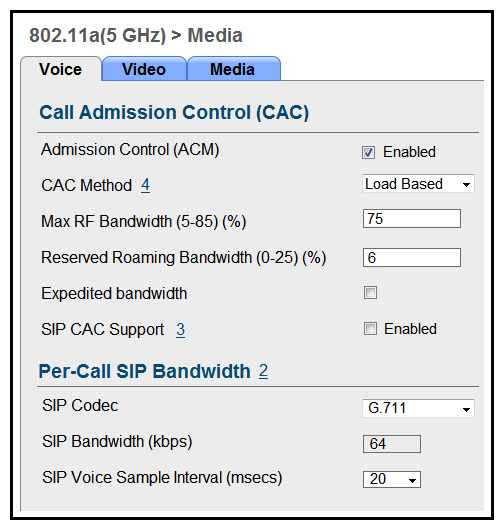 Refer to the exhibit. Which two items must be supported on the VoWLAN phones to take full advantage of this WLAN configuration? (Choose two.)
Refer to the exhibit. Which two items must be supported on the VoWLAN phones to take full advantage of this WLAN configuration? (Choose two.)A) TSPEC
B) SIFS
C) 802.11e
D) WMM
E) APSD

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
21
Which statement about the VideoStream/Multicast Direct feature is true?
A) IP multicast traffic is reliable over WLAN by default as defined by the IEEE 802.11 wireless multicast delivery mechanism.
B) Each VideoStream client acknowledges receiving a video IP multicast stream.
C) It converts the unicast frame to a multicast frame over the air.
D) It makes the delivery of the IP multicast stream less reliable over the air, but reliable over Ethernet.
A) IP multicast traffic is reliable over WLAN by default as defined by the IEEE 802.11 wireless multicast delivery mechanism.
B) Each VideoStream client acknowledges receiving a video IP multicast stream.
C) It converts the unicast frame to a multicast frame over the air.
D) It makes the delivery of the IP multicast stream less reliable over the air, but reliable over Ethernet.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
22
A customer is experiencing performance issues with its wireless network and asks a wireless engineer to provide information about all sources of interference and their impacts to the wireless network over the past few days. Where can the requested information be accessed?
A) CleanAir reports on Cisco Prime Infrastructure
B) Performance reports on Cisco Prime Infrastructure
C) Interference Devices reports on Cisco Wireless LAN Controller
D) Air Quality reports on Cisco Wireless LAN Controller
A) CleanAir reports on Cisco Prime Infrastructure
B) Performance reports on Cisco Prime Infrastructure
C) Interference Devices reports on Cisco Wireless LAN Controller
D) Air Quality reports on Cisco Wireless LAN Controller

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
23
Which component must be integrated with Cisco DNA Center to display the location of a client that is experiencing connectivity issues?
A) Cisco Hyperlocation Module
B) Wireless Intrusion Prevention System
C) Cisco Connected Mobile Experiences
D) Cisco Mobility Services Engine
A) Cisco Hyperlocation Module
B) Wireless Intrusion Prevention System
C) Cisco Connected Mobile Experiences
D) Cisco Mobility Services Engine

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
24
An engineer is configuring multicast for wireless for an all-company video meeting on a network using EIGRP and BGP within a single domain from a single source. Which type of multicast routing should be implemented?
A) Protocol Independent Multicast Dense Mode
B) Source Specific Multicast
C) Multicast Source Discovery Protocol
D) Protocol Independent Multicast Sparse Mode
A) Protocol Independent Multicast Dense Mode
B) Source Specific Multicast
C) Multicast Source Discovery Protocol
D) Protocol Independent Multicast Sparse Mode

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
25
Which two protocols are used to communicate between the Cisco MSE and the Cisco Prime Infrastructure network management software? (Choose two.)
A) HTTPS
B) Telnet
C) SOAP
D) SSH
E) NMSP
A) HTTPS
B) Telnet
C) SOAP
D) SSH
E) NMSP

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
26
Which AP model of the Cisco Aironet Active Sensor is used with Cisco DNA Center?
A) 1800s
B) 3600e
C) 3800s
D) 4800i
A) 1800s
B) 3600e
C) 3800s
D) 4800i

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
27
Which three characteristics of a rogue AP pose a high security risk? (Choose three.)
A) open authentication
B) high RSSI
C) foreign SSID
D) accepts clients
E) low RSSI
F) distant location
A) open authentication
B) high RSSI
C) foreign SSID
D) accepts clients
E) low RSSI
F) distant location

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
28
An engineer completed the basic installation for two Cisco CMX servers and is in the process of configuring high availability, but it fails. Which two statements about the root of the issue are true? (Choose two.)
A) The Cisco CMX instances are installed in the same subnet.
B) The types of the primary and secondary Cisco CMX installations differ.
C) The delay between the primary and secondary instance is 200 ms.
D) The sizes of the primary and secondary Cisco CMX installations differ.
E) Both Cisco CMX installations are virtual.
A) The Cisco CMX instances are installed in the same subnet.
B) The types of the primary and secondary Cisco CMX installations differ.
C) The delay between the primary and secondary instance is 200 ms.
D) The sizes of the primary and secondary Cisco CMX installations differ.
E) Both Cisco CMX installations are virtual.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
29
An engineer is implementing Cisco Identity-Based Networking on a Cisco AireOS controller. The engineer has two ACLs on the controller. The first ACL, named BASE_ACL, is applied to the corporate_clients interface on the WLC, which is used for all corporate clients. The second ACL, named HR_ACL, is referenced by ISE in the Human Resources group policy. What is the resulting ACL when a Human Resources user connects?
A) HR_ACL appended with BASE_ACL
B) HR_ACL only
C) BASE_ACL appended with HR_ACL
D) BASE_ACL only
A) HR_ACL appended with BASE_ACL
B) HR_ACL only
C) BASE_ACL appended with HR_ACL
D) BASE_ACL only

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
30
An engineer wants to configure WebEx to adjust the precedence and override the QoS profile on the WLAN. Which configuration is needed to complete this task?
A) Change the WLAN reserved bandwidth for WebEx
B) Create an AVC profile for WebEx
C) Create an ACL for WebEx
D) Change the AVC application WebEx-app-sharing to mark
A) Change the WLAN reserved bandwidth for WebEx
B) Create an AVC profile for WebEx
C) Create an ACL for WebEx
D) Change the AVC application WebEx-app-sharing to mark

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
31
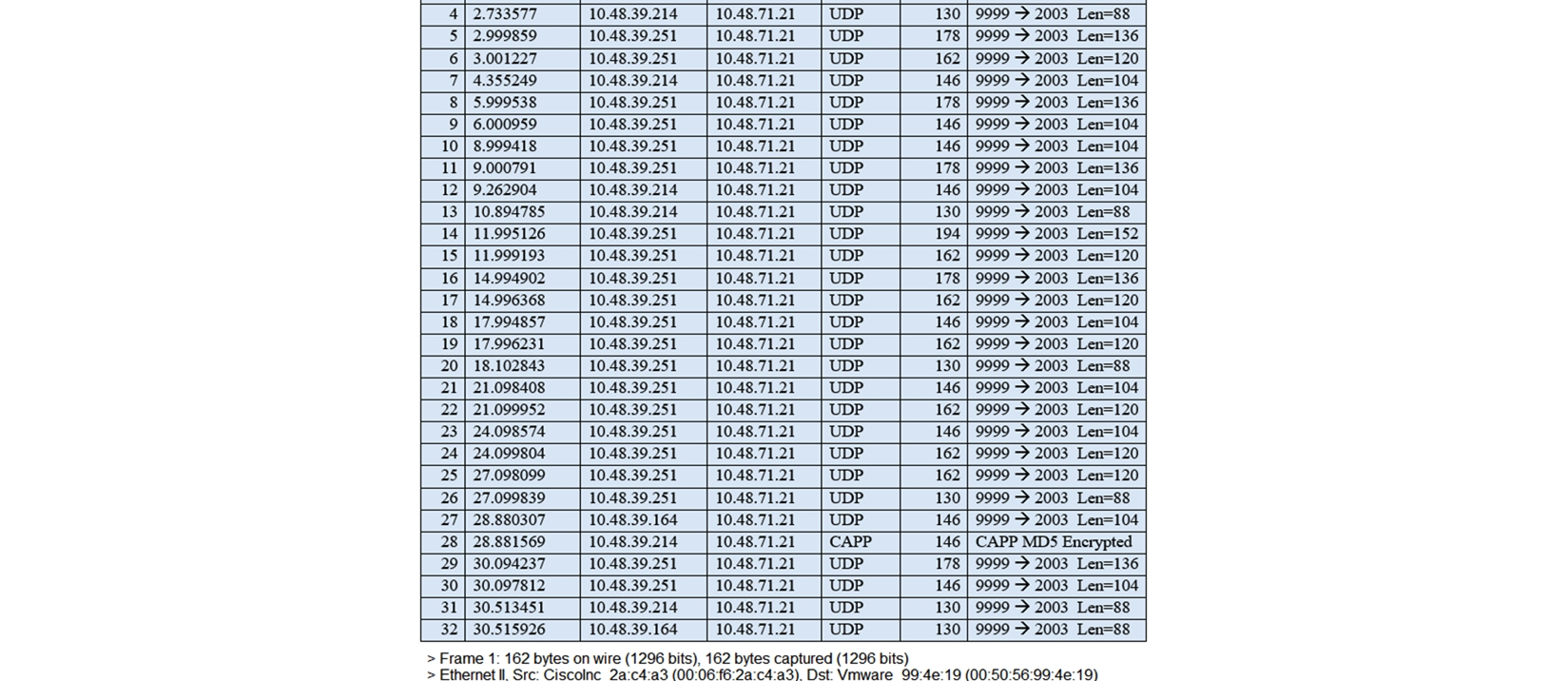 Refer to the exhibit. The image shows a packet capture that was taken at the CLI of the Cisco CMX server. It shows UDP traffic from the WLC coming into the server. What does the capture prove?
Refer to the exhibit. The image shows a packet capture that was taken at the CLI of the Cisco CMX server. It shows UDP traffic from the WLC coming into the server. What does the capture prove?A) The Cisco CMX server receives NetFlow data from the WLC.
B) The Cisco CMX server receives NMSP traffic from the WLC.
C) The Cisco CMX server receives SNMP traffic from the WLC.
D) The Cisco CMX server receives Angle-of-Arrival data from the WLC.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
32
Which three properties are used for client profiling of wireless clients? (Choose three.)
A) HTTP user agent
B) DHCP
C) MAC OUI
D) hostname
E) OS version
F) IP address
A) HTTP user agent
B) DHCP
C) MAC OUI
D) hostname
E) OS version
F) IP address

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
33
An engineer must configure a Cisco WLC to support Cisco Aironet 600 Series OfficeExtend APs. Which two Layer 2 security options are supported in this environment? (Choose two.)
A) Static WEP + 802.1X
B) WPA+WPA2
C) Static WEP
D) CKIP
E) 802.1X
A) Static WEP + 802.1X
B) WPA+WPA2
C) Static WEP
D) CKIP
E) 802.1X

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
34
Refer to the exhibit. An engineer is creating an ACL to restrict some traffic to the WLC CPU. Which selection must be made from the direction drop-down list? 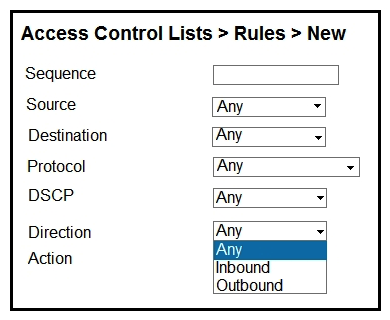
A) It must be Inbound because traffic goes to the WLC.
B) Packet direction has no significance; it is always Any.
C) It must be Outbound because it is traffic that is generated from the WLC.
D) To have the complete list of options, the CPU ACL must be created only by the CLI.

A) It must be Inbound because traffic goes to the WLC.
B) Packet direction has no significance; it is always Any.
C) It must be Outbound because it is traffic that is generated from the WLC.
D) To have the complete list of options, the CPU ACL must be created only by the CLI.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
35
A Cisco WLC has been added to the network and Cisco ISE as a network device, but authentication is failing. Which configuration within the network device configuration should be verified?
A) SNMP RO community
B) device interface credentials
C) device ID
D) shared secret
A) SNMP RO community
B) device interface credentials
C) device ID
D) shared secret

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
36
A new MSE with wIPS service has been installed and no alarm information appears to be reaching the MSE from controllers. Which protocol must be allowed to reach the MSE from the controllers?
A) SOAP/XML
B) NMSP
C) CAPWAP
D) SNMP
A) SOAP/XML
B) NMSP
C) CAPWAP
D) SNMP

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
37
What is the default NMSP echo interval between Cisco MSE and a Wireless LAN Controller?
A) 10 seconds
B) 15 seconds
C) 30 seconds
D) 60 seconds
A) 10 seconds
B) 15 seconds
C) 30 seconds
D) 60 seconds

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
38
Where is a Cisco OEAP enabled on a Cisco Catalyst 9800 Series Wireless Controller?
A) RF Profile
B) Flex Profile
C) Policy Profile
D) AP Join Profile
A) RF Profile
B) Flex Profile
C) Policy Profile
D) AP Join Profile

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
39
Where is Cisco Hyperlocation enabled on a Cisco Catalyst 9800 Series Wireless Controller web interface?
A) Policy Profile
B) AP Join Profile
C) Flex Profile
D) RF Profile
A) Policy Profile
B) AP Join Profile
C) Flex Profile
D) RF Profile

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
40
A FlexConnect remote office deployment is using five 2702i APs indoors and two 1532i APs outdoors. When a code upgrade is performed and FlexConnect Smart AP Image Upgrade is leveraged, but no FlexConnect Master AP has been configured, how many image transfers between the WLC and APs will occur?
A) 1
B) 2
C) 5
D) 7
A) 1
B) 2
C) 5
D) 7

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
41
For security purposes, an engineer enables CPU ACL and chooses an ACL on the Security > Access Control Lists > CPU Access Control Lists menu. Which kind of traffic does this change apply to, as soon as the change is made?
A) wireless traffic only
B) wired traffic only
C) VPN traffic
D) wireless and wired traffic
A) wireless traffic only
B) wired traffic only
C) VPN traffic
D) wireless and wired traffic

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
42
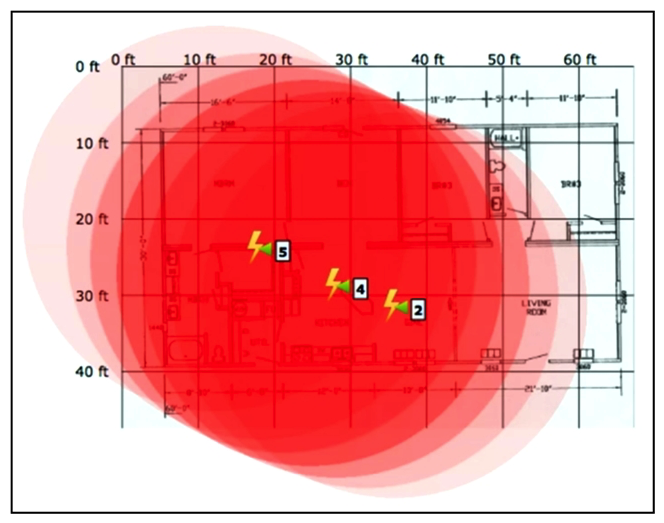 Refer to the exhibit. An engineer needs to manage non-802.11 interference. What is observed in the output on PI?
Refer to the exhibit. An engineer needs to manage non-802.11 interference. What is observed in the output on PI?A) At least one strong interferer is impacting connectivity at this site.
B) Several light interferers are collectively impacting connectivity at this site.
C) The three individual clusters shown indicate poor AP placement.
D) RF at this site is unable provide adequate wireless performance.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
43
An engineer must implement Cisco Identity-Based Networking Services at a remote site using ISE to dynamically assign groups of users to specific IP subnets. If the subnet assigned to a client is available at the remote site, then traffic must be offloaded locally, and subnets are unavailable at the remote site must be tunneled back to the WLC. Which feature meets these requirements?
A) learn client IP address
B) FlexConnect local authentication
C) VLAN-based central switching
D) central DHCP processing
A) learn client IP address
B) FlexConnect local authentication
C) VLAN-based central switching
D) central DHCP processing

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
44
An engineer is following the proper upgrade path to upgrade a Cisco AireOS WLC from version 7.3 to 8.9. Which two ACLs for Cisco CWA must be configured when upgrading from the specified codes? (Choose two.)
A) Permit 0.0.0.0 0.0.0.0 UDP any any
B) Permit 0.0.0.0 0.0.0.0 any DNS any
C) Permit 0.0.0.0 0.0.0.0 UDP DNS any
D) Permit 0.0.0.0 0.0.0.0 UDP any DNS
E) Permit any any any
A) Permit 0.0.0.0 0.0.0.0 UDP any any
B) Permit 0.0.0.0 0.0.0.0 any DNS any
C) Permit 0.0.0.0 0.0.0.0 UDP DNS any
D) Permit 0.0.0.0 0.0.0.0 UDP any DNS
E) Permit any any any

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
45
An organization is supporting remote workers in different locations. In order to provide wireless network connectivity and services, OfficeExtend has been implemented. The wireless connectivity is working, but users report losing connectivity to their local network printers. Which solution must be used to address this issue?
A) OEAP gateway override
B) OEAP split tunnel
C) WLAN static IP tunneling
D) FlexConnect local switching
A) OEAP gateway override
B) OEAP split tunnel
C) WLAN static IP tunneling
D) FlexConnect local switching

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
46
Branch wireless users report that they can no longer access services from head office but can access services locally at the site. New wireless users can associate to the wireless while the WAN is down. Which three elements (Cisco FlexConnect state, operation mode, and authentication method) are seen in this scenario? (Choose three.)
A) authentication-local/switch-local
B) WPA2 personal
C) authentication-central/switch-central
D) lightweight mode
E) standalone mode
F) WEB authentication
A) authentication-local/switch-local
B) WPA2 personal
C) authentication-central/switch-central
D) lightweight mode
E) standalone mode
F) WEB authentication

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
47
An engineer must configure MSE to provide guests access using social media authentication. Which service does the engineer configure so that guests use Facebook credentials to authenticate?
A) Social Connect
B) Client Connect
C) Visitor Connect
D) Guest Connect
A) Social Connect
B) Client Connect
C) Visitor Connect
D) Guest Connect

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
48
Which two steps are needed to complete integration of the MSE to Cisco Prime Infrastructure and be able to track the location of clients/rogues on maps? (Choose two.)
A) Synchronize access points with the MSE.
B) Add the MSE to Cisco Prime Infrastructure using the CLI credentials.
C) Add the MSE to Cisco Prime Infrastructure using the Cisco Prime Infrastructure communication credentials configured during set up.
D) Apply a valid license for Wireless Intrusion Prevention System.
E) Apply a valid license for location tracking.
A) Synchronize access points with the MSE.
B) Add the MSE to Cisco Prime Infrastructure using the CLI credentials.
C) Add the MSE to Cisco Prime Infrastructure using the Cisco Prime Infrastructure communication credentials configured during set up.
D) Apply a valid license for Wireless Intrusion Prevention System.
E) Apply a valid license for location tracking.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
49
A network engineer observes a spike in controller CPU overhead and overall network utilization after multicast is enabled on a controller with 500 APs. Which feature corrects the issue?
A) controller IGMP snooping
B) multicast AP multicast mode
C) broadcast forwarding
D) unicast AP multicast mode
A) controller IGMP snooping
B) multicast AP multicast mode
C) broadcast forwarding
D) unicast AP multicast mode

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
50
An engineer is implementing a FlexConnect group for access points at a remote location using local switching but central DHCP. Which client feature becomes available only if this configuration is changed?
A) multicast
B) static IP
C) fast roaming
D) mDNS
A) multicast
B) static IP
C) fast roaming
D) mDNS

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
51
A wireless engineer needs to implement client tracking. Which method does the angle of arrival use to determine the location of a wireless device?
A) received signal strength
B) triangulation
C) time distance of arrival
D) angle of incidence
A) received signal strength
B) triangulation
C) time distance of arrival
D) angle of incidence

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
52
A network engineer is deploying 8865 IP phones with wireless clients connected to them. In order to apply the appropriate QoS, the IP voice traffic needs to be distinguished from client data traffic. Which switch configuration feature must be enabled?
A) Voice VLAN
B) QBSS
C) WME
D) QoS routing
A) Voice VLAN
B) QBSS
C) WME
D) QoS routing

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
53
What is configured to use more than one port on the OEAP to extend the wired network?
A) remote LAN ACL
B) AAA override
C) client load balancing
D) remote LAN
A) remote LAN ACL
B) AAA override
C) client load balancing
D) remote LAN

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
54
An engineer has been hired to implement a way for users to stream video content without having issues on the wireless network. To accomplish this goal, the engineer must set up a reliable way for a Media Stream to work between Cisco FlexConnect APs. Which feature must be enabled to guarantee delivery?
A) Unicast Direct
B) IGMP Direct
C) Multicast Direct
D) Multicast-to-Unicast Direct
A) Unicast Direct
B) IGMP Direct
C) Multicast Direct
D) Multicast-to-Unicast Direct

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
55
A corporation is spread across different countries and uses MPLS to connect the offices. The senior management wants to utilize the wireless network for all the employees. To ensure strong connectivity and minimize delays, an engineer needs to control the amount of traffic that is traversing between the APs and the central WLC. Which configuration should be used to accomplish this goal?
A) FlexConnect mode with central switching enabled
B) FlexConnect mode with central authentication
C) FlexConnect mode with OfficeExtend enabled
D) FlexConnect mode with local authentication
A) FlexConnect mode with central switching enabled
B) FlexConnect mode with central authentication
C) FlexConnect mode with OfficeExtend enabled
D) FlexConnect mode with local authentication

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
56
What is the difference between PIM sparse mode and PIM dense mode?
A) Sparse mode supports only one switch. Dense mode supports multiswitch networks.
B) Sparse mode floods. Dense mode uses distribution trees.
C) Sparse mode uses distribution trees. Dense mode floods.
D) Sparse mode supports multiswitch networks. Dense mode supports only one switch.
A) Sparse mode supports only one switch. Dense mode supports multiswitch networks.
B) Sparse mode floods. Dense mode uses distribution trees.
C) Sparse mode uses distribution trees. Dense mode floods.
D) Sparse mode supports multiswitch networks. Dense mode supports only one switch.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
57
A company is collecting the requirements for an on-premises event. During the event, a wireless client connected to a dedicated WLAN will run a video application that will need on average 391595179 bits per second to function properly. What is the QoS marking that needs to be applied to that WLAN?
A) Platinum
B) Gold
C) Silver
D) Bronze
A) Platinum
B) Gold
C) Silver
D) Bronze

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
58
When implementing self-registration for guest/BYOD devices, what happens when an employee tries to connect four devices to the network at the same time?
A) The last device is removed and the newly added device is updated as active device.
B) The registration is allowed, but only one device is connected at any given time.
C) All devices are allowed on the network simultaneously.
D) Purge time dictates how long a device is registered to the portal.
A) The last device is removed and the newly added device is updated as active device.
B) The registration is allowed, but only one device is connected at any given time.
C) All devices are allowed on the network simultaneously.
D) Purge time dictates how long a device is registered to the portal.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
59
The Cisco Hyperlocation detection threshold is currently set to -50 dBm. After reviewing the wireless user location, discrepancies have been noticed. To improve the Cisco Hyperlocation accuracy, an engineer attempts to change the detection threshold to -100 dBm. However, the Cisco Catalyst 9800 Series Wireless Controller does not allow this change to be applied. What actions should be taken to resolve this issue?
A) Disable Cisco Hyperlocation, change the Cisco Hyperlocation detection threshold, and then enable it.
B) Create a new profile on Cisco CMX with the new Cisco Hyperlocation detection range, and apply it on the WLAN.
C) Place the APs to monitor mode, shutdown the radios, and then change Cisco Hyperlocation detection threshold.
D) Shutdown all radios on the controller, change the Cisco Hyperlocation detection range, and enable the radios again.
A) Disable Cisco Hyperlocation, change the Cisco Hyperlocation detection threshold, and then enable it.
B) Create a new profile on Cisco CMX with the new Cisco Hyperlocation detection range, and apply it on the WLAN.
C) Place the APs to monitor mode, shutdown the radios, and then change Cisco Hyperlocation detection threshold.
D) Shutdown all radios on the controller, change the Cisco Hyperlocation detection range, and enable the radios again.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
60
A network engineer has been hired to perform a new MSE implementation on an existing network. The MSE must be installed in a different network than the Cisco WLC. Which configuration allows the devices to communicate over NMSP?
A) Allow UDP/16113 port on the central switch.
B) Allow TCP/16113 port on the firewall.
C) Allow UDP/16666 port on the VPN router.
D) Allow TCP/16666 port on the router.
A) Allow UDP/16113 port on the central switch.
B) Allow TCP/16113 port on the firewall.
C) Allow UDP/16666 port on the VPN router.
D) Allow TCP/16666 port on the router.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
61
An engineer must implement a BYOD policy with these requirements: Onboarding unknown machines Easily scalable Low overhead on the wireless network Which method satisfies these requirements?
A) triple SSID
B) single SSID
C) open SSID
D) dual SSID
A) triple SSID
B) single SSID
C) open SSID
D) dual SSID

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
62
An engineer set up identity-based networking with ISE and configured AAA override on the WLAN. Which two attributes must be used to change the client behavior from the default settings? (Choose two.)
A) DHCP timeout
B) DNS server
C) IPv6 ACL
D) DSCP value
E) multicast address
A) DHCP timeout
B) DNS server
C) IPv6 ACL
D) DSCP value
E) multicast address

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
63
An IT team is growing quickly and needs a solution for management device access. The solution must authenticate users from an external repository instead of the current local on the WLC, and it must also identify the user and determine what level of access users should have. Which protocol do you recommend to achieve these goals?
A) network policy server
B) RADIUS
C) TACACS+
D) LDAP
A) network policy server
B) RADIUS
C) TACACS+
D) LDAP

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
64
A corporation has recently implemented a BYOD policy at their HQ. Which two risks should the security director be concerned about? (Choose two.)
A) network analyzers
B) malware
C) lost and stolen devices
D) keyloggers
E) unauthorized users
A) network analyzers
B) malware
C) lost and stolen devices
D) keyloggers
E) unauthorized users

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
65
An engineer is setting up a WLAN to work with a Cisco ISE as the AAA server. The company policy requires that all users be denied access to any resources until they pass the validation. Which component must be configured to achieve this stipulation?
A) WPA2 passkey
B) AAA override
C) CPU ACL
D) preauthentication ACL
A) WPA2 passkey
B) AAA override
C) CPU ACL
D) preauthentication ACL

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
66
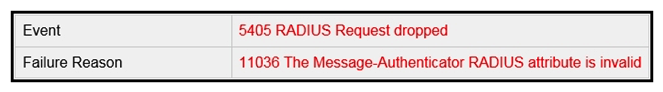 Refer to the exhibit. A wireless engineer has integrated the wireless network with a RADIUS server. Although the configuration on the RADIUS is correct, users are reporting that they are unable to connect. During troubleshooting, the engineer notices that the authentication requests are being dropped. Which action will resolve the issue?
Refer to the exhibit. A wireless engineer has integrated the wireless network with a RADIUS server. Although the configuration on the RADIUS is correct, users are reporting that they are unable to connect. During troubleshooting, the engineer notices that the authentication requests are being dropped. Which action will resolve the issue?A) Allow connectivity from the wireless controller to the IP of the RADIUS server.
B) Provide a valid client username that has been configured on the RADIUS server.
C) Configure the shared-secret keys on the controller and the RADIUS server.
D) Authenticate the client using the same EAP type that has been set up on the RADIUS server.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
67
An engineer is implementing profiling for BYOD devices using Cisco ISE. When using a distributed model, which persona must the engineer configure with the profiling service?
A) Device Admin Node
B) Primary Admin Node
C) Monitor Node
D) Policy Services Node
A) Device Admin Node
B) Primary Admin Node
C) Monitor Node
D) Policy Services Node

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
68
An engineer must track guest traffic flow using the WLAN infrastructure. Which Cisco CMX feature must be configured and used to accomplish this tracking?
A) analytics
B) connect and engage
C) presence
D) detect and locate
A) analytics
B) connect and engage
C) presence
D) detect and locate

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
69
Which command set configures a Cisco Catalyst 9800 Series Wireless Controller so that the client traffic enters the network at the AP switch port?
A)
B)
C)
D)
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
70
During the EAP process and specifically related to the client authentication session, which encrypted key is sent from the RADIUS server to the access point?
A) WPA key
B) session key
C) encryption key
D) shared-secret key
A) WPA key
B) session key
C) encryption key
D) shared-secret key

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
71
Refer to the exhibit. A network administrator deploys the DHCP profiler service in two ISE servers: 10.3.10.101 and 10.3.10.102. All BYOD devices connecting to WLAN on VLAN63 have been incorrectly profiled and are assigned as unknown profiled endpoints. Which action efficiently rectifies the issue according to Cisco recommendations? 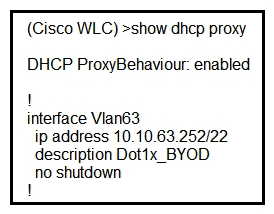
A) Nothing needed to be added on the Cisco WLC or VLAN interface. The ISE configuration must be fixed.
B) Disable DHCP proxy on the Cisco WLC.
C) Disable DHCP proxy on the Cisco WLC and run the ip helper-address command under the VLAN interface to point to DHCP and the two ISE servers. Disable DHCP proxy on the Cisco WLC and run the ip helper-address command under the VLAN interface to point to DHCP and the two ISE servers.
D) Keep DHCP proxy enabled on the Cisco WLC and define helper-address under the VLAN interface to point to the two ISE servers.

A) Nothing needed to be added on the Cisco WLC or VLAN interface. The ISE configuration must be fixed.
B) Disable DHCP proxy on the Cisco WLC.
C) Disable DHCP proxy on the Cisco WLC and run the ip helper-address command under the VLAN interface to point to DHCP and the two ISE servers. Disable DHCP proxy on the Cisco WLC and run the ip helper-address command under the VLAN interface to point to DHCP and the two ISE servers.
D) Keep DHCP proxy enabled on the Cisco WLC and define helper-address under the VLAN interface to point to the two ISE servers.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
72
What must be configured on the Global Configuration page of the WLC for an access point to use 802.1x to authenticate to the wired infrastructure?
A) local access point credentials
B) RADIUS shared secret
C) TACACS server IP address
D) supplicant credentials
A) local access point credentials
B) RADIUS shared secret
C) TACACS server IP address
D) supplicant credentials

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
73
What is an important consideration when implementing a dual SSID design for BYOD?
A) After using the provisioning SSID, an ACL that used to make the client switch SSIDs forces the user to associate and traverse the network by MAC filtering.
B) If multiple WLCs are used, the WLAN IDs must be exact for the clients to be provisioned and traverse the network correctly.
C) SSIDs for this setup must be configured with NAC State-RADIUS NAC for the clients to authenticate with Cisco ISE, or with NAC State-ISE NAC for Cisco ISE to associate the client.
D) One SSID is for provisioning and the other SSID is for gaining access to the network. The use of an ACL should not be enforced to make the client connect to the REAL SSID after provisioning.
A) After using the provisioning SSID, an ACL that used to make the client switch SSIDs forces the user to associate and traverse the network by MAC filtering.
B) If multiple WLCs are used, the WLAN IDs must be exact for the clients to be provisioned and traverse the network correctly.
C) SSIDs for this setup must be configured with NAC State-RADIUS NAC for the clients to authenticate with Cisco ISE, or with NAC State-ISE NAC for Cisco ISE to associate the client.
D) One SSID is for provisioning and the other SSID is for gaining access to the network. The use of an ACL should not be enforced to make the client connect to the REAL SSID after provisioning.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
74
An engineer must provide a graphical report with summary grouped data of the total number of wireless clients on the network. Which Cisco Prime Infrastructure report provides the required data?
A) Client Traffic Stream Metrics
B) Client Summary
C) Posture Status Count
D) Mobility Client Summary
A) Client Traffic Stream Metrics
B) Client Summary
C) Posture Status Count
D) Mobility Client Summary

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
75
A customer reports that wireless clients are not able to receive multicast data from known working multicast servers on the wired network. The client is connecting at the highest mandatory wireless rate of 24 Mbps and the wireless controller is configured for multicast-unicast mode. What three actions should the engineer take next to troubleshoot the issue? (Choose three.)
A) verify that the L3 interfaces are configured for pim sparse-dense-mode on the VLAN servicing the wireless access points as well as the wireless controller's management VLAN
B) change the wireless controller from Multicast-Unicast mode to Multicast-Multicast mode and assign a multicast address in the 239.X.X.X/8 subnet
C) verify that IGMP snooping is disabled on the wireless controller since the access points are handling IGMP messages from the clients
D) verify that Global Multicast mode has been enabled
E) make sure the highest mandatory rate is set to 54 Mbps so that the multicast traffic has sufficient bandwidth
F) verify Multicast Listener Discovery (MLD) v1 snooping has been enabled to keep track of and deliver IPv4 multicast flows
A) verify that the L3 interfaces are configured for pim sparse-dense-mode on the VLAN servicing the wireless access points as well as the wireless controller's management VLAN
B) change the wireless controller from Multicast-Unicast mode to Multicast-Multicast mode and assign a multicast address in the 239.X.X.X/8 subnet
C) verify that IGMP snooping is disabled on the wireless controller since the access points are handling IGMP messages from the clients
D) verify that Global Multicast mode has been enabled
E) make sure the highest mandatory rate is set to 54 Mbps so that the multicast traffic has sufficient bandwidth
F) verify Multicast Listener Discovery (MLD) v1 snooping has been enabled to keep track of and deliver IPv4 multicast flows

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
76
An engineer is tuning RRM parameters to improve client connectivity. Which channel band results in the best 802.11n client compatibility?
A) UNII-2
B) UNII-2e
C) UNII-3
D) UNII
E) UNII-1
A) UNII-2
B) UNII-2e
C) UNII-3
D) UNII
E) UNII-1

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
77
An engineer has successfully implemented 10 active RFID tags in an office environment. The tags are not visible when the location accuracy is tested on the Cisco CMX Detect and Locate window. Which setting on Cisco CMX allows the engineer to view the tags?
A) Enable RFID tags in tracking options.
B) Enable probing clients for active tags.
C) Define an RFID group globally and add the tags.
D) Enable hyperlocation services for RFID.
A) Enable RFID tags in tracking options.
B) Enable probing clients for active tags.
C) Define an RFID group globally and add the tags.
D) Enable hyperlocation services for RFID.

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
78
An engineer must create an account to log in to the CLI of an access point for troubleshooting. Which configuration on the WLC will accomplish this?
A) Allow New Telnet Sessions
B) ReadWrite User Access Mode
C) SNMP V3 User
D) Global Configuration Enable Password
A) Allow New Telnet Sessions
B) ReadWrite User Access Mode
C) SNMP V3 User
D) Global Configuration Enable Password

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
79
An engineer needs to configure an autonomous AP for 802.1x authentication. To achieve the highest security an authentication server is used for user authentication. During testing, the AP fails to pass the user authentication request to the authentication server. Which two details need to be configured on the AP to allow communication between the server and the AP? (Choose two.)
A) username and password
B) PAC encryption key
C) RADIUS IP address
D) shared secret
E) group name
A) username and password
B) PAC encryption key
C) RADIUS IP address
D) shared secret
E) group name

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck
80
You are designing a WLAN for 50 branch offices that require central management. Which controller architecture do you use?
A) per-branch local controllers
B) anchor controllers
C) FlexConnect controllers
D) autonomous access points
A) per-branch local controllers
B) anchor controllers
C) FlexConnect controllers
D) autonomous access points

Unlock Deck
Unlock for access to all 101 flashcards in this deck.
Unlock Deck
k this deck



