Deck 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/130
Play
Full screen (f)
Deck 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)
1
What is the disadvantage of setting up a site-to-site VPN in a clustered-units environment?
A) VPN connections can be re-established only if the failed master unit recovers.
B) Smart License is required to maintain VPN connections simultaneously across all cluster units.
C) VPN connections must be re-established when a new master unit is elected.
D) Only established VPN connections are maintained when a new master unit is elected.
A) VPN connections can be re-established only if the failed master unit recovers.
B) Smart License is required to maintain VPN connections simultaneously across all cluster units.
C) VPN connections must be re-established when a new master unit is elected.
D) Only established VPN connections are maintained when a new master unit is elected.
VPN connections must be re-established when a new master unit is elected.
2
Which two OSPF routing features are configured in Cisco FMC and propagated to Cisco FTD? (Choose two.)
A) OSPFv2 with IPv6 capabilities
B) virtual links
C) SHA authentication to OSPF packets
D) area boundary router type 1 LSA filtering
E) MD5 authentication to OSPF packets
A) OSPFv2 with IPv6 capabilities
B) virtual links
C) SHA authentication to OSPF packets
D) area boundary router type 1 LSA filtering
E) MD5 authentication to OSPF packets
virtual links
MD5 authentication to OSPF packets
MD5 authentication to OSPF packets
3
An engineer is implementing Cisco FTD in the network and is determining which Firepower mode to use. The organization needs to have multiple virtual Firepower devices working separately inside of the FTD appliance to provide traffic segmentation. Which deployment mode should be configured in the Cisco Firepower Management Console to support these requirements?
A) multi-instance
B) multiple deployment
C) single deployment
D) single-context
A) multi-instance
B) multiple deployment
C) single deployment
D) single-context
multi-instance
4
Which Cisco Firepower Threat Defense, which two interface settings are required when configuring a routed interface? (Choose two.)
A) Redundant Interface
B) EtherChannel
C) Speed
D) Media Type
E) Duplex
A) Redundant Interface
B) EtherChannel
C) Speed
D) Media Type
E) Duplex

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
5
On the advanced tab under inline set properties, which allows interfaces to emulate a passive interface?
A) transparent inline mode
B) TAP mode
C) strict TCP enforcement
D) propagate link state
A) transparent inline mode
B) TAP mode
C) strict TCP enforcement
D) propagate link state

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
6
The event dashboard within the Cisco FMC has been inundated with low priority intrusion drop events, which are overshadowing high priority events. An engineer has been tasked with reviewing the policies and reducing the low priority events. Which action should be configured to accomplish this task?
A) drop packet
B) generate events
C) drop connection
D) drop and generate
A) drop packet
B) generate events
C) drop connection
D) drop and generate

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
7
While configuring FTD, a network engineer wants to ensure that traffic passing though the appliance does not require routing or VLAN rewriting. Which interface mode should the engineer implement to accomplish this task?
A) inline set
B) passive
C) transparent
D) inline tap
A) inline set
B) passive
C) transparent
D) inline tap

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
8
An organization has noticed that malware was downloaded from a website that does not currently have a known bad reputation. How will this issue be addressed globally in the quickest way possible and with the least amount of impact?
A) by creating a URL object in the policy to block the website.
B) Cisco Talos will automatically update the policies.
C) by denying outbound web access
D) by isolating the endpoint
A) by creating a URL object in the policy to block the website.
B) Cisco Talos will automatically update the policies.
C) by denying outbound web access
D) by isolating the endpoint

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
9
An organization has implemented Cisco Firepower without IPS capabilities and now wants to enable inspection for their traffic. They need to be able to detect protocol anomalies and utilize the Snort rule sets to detect malicious behavior. How is this accomplished?
A) Modify the network discovery policy to detect new hosts to inspect.
B) Modify the access control policy to redirect interesting traffic to the engine.
C) Modify the intrusion policy to determine the minimum severity of an event to inspect.
D) Modify the network analysis policy to process the packets for inspection.
A) Modify the network discovery policy to detect new hosts to inspect.
B) Modify the access control policy to redirect interesting traffic to the engine.
C) Modify the intrusion policy to determine the minimum severity of an event to inspect.
D) Modify the network analysis policy to process the packets for inspection.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
10
What is the difference between inline and inline tap on Cisco Firepower?
A) Inline tap mode can send a copy of the traffic to another device.
B) Inline tap mode does full packet capture.
C) Inline mode cannot do SSL decryption.
D) Inline mode can drop malicious traffic.
A) Inline tap mode can send a copy of the traffic to another device.
B) Inline tap mode does full packet capture.
C) Inline mode cannot do SSL decryption.
D) Inline mode can drop malicious traffic.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
11
A hospital network needs to upgrade their Cisco FMC managed devices and needs to ensure that a disaster recovery process is in place. What must be done in order to minimize downtime on the network?
A) Configure a second circuit to an ISP for added redundancy.
B) Keep a copy of the current configuration to use as backup.
C) Configure the Cisco FMCs for failover.
D) Configure the Cisco FMC managed devices for clustering.
A) Configure a second circuit to an ISP for added redundancy.
B) Keep a copy of the current configuration to use as backup.
C) Configure the Cisco FMCs for failover.
D) Configure the Cisco FMC managed devices for clustering.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
12
A Cisco FTD device is running in transparent firewall mode with a VTEP bridge group member ingress interface. What must be considered by an engineer tasked with specifying a destination MAC address for a packet trace?
A) The output format option for the packet logs is unavailable.
B) Only the UDP packet type is supported.
C) The destination MAC address is optional if a VLAN ID value is entered.
D) The VLAN ID and destination MAC address are optional.
A) The output format option for the packet logs is unavailable.
B) Only the UDP packet type is supported.
C) The destination MAC address is optional if a VLAN ID value is entered.
D) The VLAN ID and destination MAC address are optional.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
13
Which two dynamic routing protocols are supported in Cisco FTD without using FlexConfig? (Choose two.)
A) EIGRP
B) OSPF
C) static routing
D) IS-IS
E) BGP
A) EIGRP
B) OSPF
C) static routing
D) IS-IS
E) BGP

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
14
Which protocol establishes network redundancy in a switched Firepower device deployment?
A) STP
B) HSRP
C) GLBP
D) VRRP
A) STP
B) HSRP
C) GLBP
D) VRRP

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
15
With Cisco FTD integrated routing and bridging, which interface does the bridge group use to communicate with a routed interface?
A) subinterface
B) switch virtual
C) bridge virtual
D) bridge group member
A) subinterface
B) switch virtual
C) bridge virtual
D) bridge group member

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
16
A network engineer is extending a user segment through an FTD device for traffic inspection without creating another IP subnet. How is this accomplished on an FTD device in routed mode?
A) by assigning an inline set interface
B) by using a BVI and creating a BVI IP address in the same subnet as the user segment
C) by leveraging the ARP to direct traffic through the firewall
D) by bypassing protocol inspection by leveraging pre-filter rules
A) by assigning an inline set interface
B) by using a BVI and creating a BVI IP address in the same subnet as the user segment
C) by leveraging the ARP to direct traffic through the firewall
D) by bypassing protocol inspection by leveraging pre-filter rules

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
17
Network traffic coming from an organization's CEO must never be denied. Which access control policy configuration option should be used if the deployment engineer is not permitted to create a rule to allow all traffic?
A) Change the intrusion policy from security to balance.
B) Configure a trust policy for the CEO.
C) Configure firewall bypass.
D) Create a NAT policy just for the CEO.
A) Change the intrusion policy from security to balance.
B) Configure a trust policy for the CEO.
C) Configure firewall bypass.
D) Create a NAT policy just for the CEO.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
18
When creating a report template, how are the results limited to show only the activity of a specific subnet?
A) Create a custom search in Cisco FMC and select it in each section of the report.
B) Add an Input Parameter in the Advanced Settings of the report, and set the type to Network/IP.
C) Add a Table View section to the report with the Search field defined as the network in CIDR format.
D) Select IP Address as the X-Axis in each section of the report.
A) Create a custom search in Cisco FMC and select it in each section of the report.
B) Add an Input Parameter in the Advanced Settings of the report, and set the type to Network/IP.
C) Add a Table View section to the report with the Search field defined as the network in CIDR format.
D) Select IP Address as the X-Axis in each section of the report.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
19
Which policy rule is included in the deployment of a local DMZ during the initial deployment of a Cisco NGFW through the Cisco FMC GUI?
A) a default DMZ policy for which only a user can change the IP addresses.
B) deny ip any
C) no policy rule is included
D) permit ip any
A) a default DMZ policy for which only a user can change the IP addresses.
B) deny ip any
C) no policy rule is included
D) permit ip any

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
20
A mid-sized company is experiencing higher network bandwidth utilization due to a recent acquisition. The network operations team is asked to scale up their one Cisco FTD appliance deployment to higher capacities due to the increased network bandwidth. Which design option should be used to accomplish this goal?
A) Deploy multiple Cisco FTD HA pairs in clustering mode to increase performance.
B) Deploy multiple Cisco FTD appliances in firewall clustering mode to increase performance.
C) Deploy multiple Cisco FTD appliances using VPN load-balancing to scale performance.
D) Deploy multiple Cisco FTD HA pairs to increase performance.
A) Deploy multiple Cisco FTD HA pairs in clustering mode to increase performance.
B) Deploy multiple Cisco FTD appliances in firewall clustering mode to increase performance.
C) Deploy multiple Cisco FTD appliances using VPN load-balancing to scale performance.
D) Deploy multiple Cisco FTD HA pairs to increase performance.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
21
Which Cisco Firepower feature is used to reduce the number of events received in a period of time?
A) rate-limiting
B) suspending
C) correlation
D) thresholding
A) rate-limiting
B) suspending
C) correlation
D) thresholding

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
22
Which report template field format is available in Cisco FMC?
A) box lever chart
B) arrow chart
C) bar chart
D) benchmark chart
A) box lever chart
B) arrow chart
C) bar chart
D) benchmark chart

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
23
Which command is run on an FTD unit to associate the unit to an FMC manager that is at IP address 10.0.0.10, and that has the registration key Cisco123?
A) configure manager local 10.0.0.10 Cisco123
B) configure manager add Cisco123 10.0.0.10
C) configure manager local Cisco123 10.0.0.10
D) configure manager add 10.0.0.10 Cisco123
A) configure manager local 10.0.0.10 Cisco123
B) configure manager add Cisco123 10.0.0.10
C) configure manager local Cisco123 10.0.0.10
D) configure manager add 10.0.0.10 Cisco123

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
24
An engineer is attempting to create a new dashboard within the Cisco FMC to have a single view with widgets from many of the other dashboards. The goal is to have a mixture of threat and security related widgets along with Cisco Firepower device health information. Which two widgets must be configured to provide this information? (Choose two.)
A) Intrusion Events
B) Correlation Information
C) Appliance Status
D) Current Sessions
E) Network Compliance
A) Intrusion Events
B) Correlation Information
C) Appliance Status
D) Current Sessions
E) Network Compliance

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
25
Which action should be taken after editing an object that is used inside an access control policy?
A) Delete the existing object in use.
B) Refresh the Cisco FMC GUI for the access control policy.
C) Redeploy the updated configuration.
D) Create another rule using a different object name.
A) Delete the existing object in use.
B) Refresh the Cisco FMC GUI for the access control policy.
C) Redeploy the updated configuration.
D) Create another rule using a different object name.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
26
A network administrator is seeing an unknown verdict for a file detected by Cisco FTD. Which malware policy configuration option must be selected in order to further analyze the file in the Talos cloud?
A) malware analysis
B) dynamic analysis
C) sandbox analysis
D) Spero analysis
A) malware analysis
B) dynamic analysis
C) sandbox analysis
D) Spero analysis

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
27
Which command is run at the CLI when logged in to an FTD unit, to determine whether the unit is managed locally or by a remote FMC server?
A) system generate-troubleshoot
B) show configuration session
C) show managers
D) show running-config | include manager
A) system generate-troubleshoot
B) show configuration session
C) show managers
D) show running-config | include manager

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
28
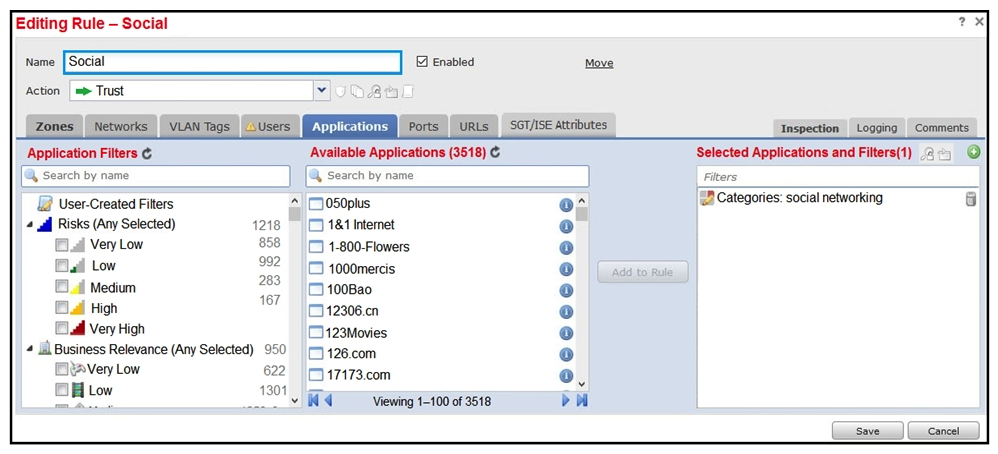 Refer to the exhibit. An organization has an access control rule with the intention of sending all social media traffic for inspection. After using the rule for some time, the administrator notices that the traffic is not being inspected, but is being automatically allowed. What must be done to address this issue?
Refer to the exhibit. An organization has an access control rule with the intention of sending all social media traffic for inspection. After using the rule for some time, the administrator notices that the traffic is not being inspected, but is being automatically allowed. What must be done to address this issue?A) Add the social network URLs to the block list.
B) Change the intrusion policy to connectivity over security.
C) Modify the selected application within the rule.
D) Modify the rule action from trust to allow.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
29
Which two routing options are valid with Cisco FTD? (Choose two.)
A) BGPv6
B) ECMP with up to three equal cost paths across multiple interfaces
C) ECMP with up to three equal cost paths across a single interface
D) BGPv4 in transparent firewall mode
E) BGPv4 with nonstop forwarding
A) BGPv6
B) ECMP with up to three equal cost paths across multiple interfaces
C) ECMP with up to three equal cost paths across a single interface
D) BGPv4 in transparent firewall mode
E) BGPv4 with nonstop forwarding

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
30
A user within an organization opened a malicious file on a workstation which in turn caused a ransomware attack on the network. What should be configured within the Cisco FMC to ensure the file is tested for viruses on a sandbox system?
A) Spero analysis
B) capacity handling
C) local malware analysis
D) dynamic analysis
A) Spero analysis
B) capacity handling
C) local malware analysis
D) dynamic analysis

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
31
A security engineer is configuring an Access Control Policy for multiple branch locations. These locations share a common rule set and utilize a network object called INSIDE_NET which contains the locally significant internal network subnets at each location. What technique will retain the policy consistency at each location but allow only the locally significant network subnet within the application rules?
A) utilizing a dynamic ACP that updates from Cisco Talos
B) creating a unique ACP per device
C) utilizing policy inheritance
D) creating an ACP with an INSIDE_NET network object and object overrides
A) utilizing a dynamic ACP that updates from Cisco Talos
B) creating a unique ACP per device
C) utilizing policy inheritance
D) creating an ACP with an INSIDE_NET network object and object overrides

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
32
An engineer configures a network discovery policy on Cisco FMC. Upon configuration, it is noticed that excessive and misleading events are filling the database and overloading the Cisco FMC. A monitored NAT device is executing multiple updates of its operating system in a short period of time. What configuration change must be made to alleviate this issue?
A) Exclude load balancers and NAT devices.
B) Leave default networks.
C) Increase the number of entries on the NAT device.
D) Change the method to TCP/SYN.
A) Exclude load balancers and NAT devices.
B) Leave default networks.
C) Increase the number of entries on the NAT device.
D) Change the method to TCP/SYN.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
33
In which two ways do access control policies operate on a Cisco Firepower system? (Choose two.)
A) Traffic inspection is interrupted temporarily when configuration changes are deployed.
B) The system performs intrusion inspection followed by file inspection.
C) They block traffic based on Security Intelligence data.
D) File policies use an associated variable set to perform intrusion prevention.
E) The system performs a preliminary inspection on trusted traffic to validate that it matches the trusted parameters.
A) Traffic inspection is interrupted temporarily when configuration changes are deployed.
B) The system performs intrusion inspection followed by file inspection.
C) They block traffic based on Security Intelligence data.
D) File policies use an associated variable set to perform intrusion prevention.
E) The system performs a preliminary inspection on trusted traffic to validate that it matches the trusted parameters.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
34
There is an increased amount of traffic on the network and for compliance reasons, management needs visibility into the encrypted traffic. What is a result of enabling TLS/SSL decryption to allow this visibility?
A) It prompts the need for a corporate managed certificate.
B) It will fail if certificate pinning is not enforced.
C) It has minimal performance impact.
D) It is not subject to any Privacy regulations.
A) It prompts the need for a corporate managed certificate.
B) It will fail if certificate pinning is not enforced.
C) It has minimal performance impact.
D) It is not subject to any Privacy regulations.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
35
An organization has seen a lot of traffic congestion on their links going out to the internet. There is a Cisco Firepower device that processes all of the traffic going to the internet prior to leaving the enterprise. How is the congestion alleviated so that legitimate business traffic reaches the destination?
A) Create a NAT policy so that the Cisco Firepower device does not have to translate as many addresses.
B) Create a flexconfig policy to use WCCP for application aware bandwidth limiting.
C) Create a QoS policy rate-limiting high bandwidth applications.
D) Create a VPN policy so that direct tunnels are established to the business applications.
A) Create a NAT policy so that the Cisco Firepower device does not have to translate as many addresses.
B) Create a flexconfig policy to use WCCP for application aware bandwidth limiting.
C) Create a QoS policy rate-limiting high bandwidth applications.
D) Create a VPN policy so that direct tunnels are established to the business applications.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
36
An engineer configures an access control rule that deploys file policy configurations to security zone or tunnel zones, and it causes the device to restart. What is the reason for the restart?
A) Source or destination security zones in the access control rule matches the security zones that are associated with interfaces on the target devices.
B) The source tunnel zone in the rule does not match a tunnel zone that is assigned to a tunnel rule in the destination policy.
C) Source or destination security zones in the source tunnel zone do not match the security zones that are associated with interfaces on the target devices.
D) The source tunnel zone in the rule does not match a tunnel zone that is assigned to a tunnel rule in the source policy.
A) Source or destination security zones in the access control rule matches the security zones that are associated with interfaces on the target devices.
B) The source tunnel zone in the rule does not match a tunnel zone that is assigned to a tunnel rule in the destination policy.
C) Source or destination security zones in the source tunnel zone do not match the security zones that are associated with interfaces on the target devices.
D) The source tunnel zone in the rule does not match a tunnel zone that is assigned to a tunnel rule in the source policy.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
37
An administrator is working on a migration from Cisco ASA to the Cisco FTD appliance and needs to test the rules without disrupting the traffic. Which policy type should be used to configure the ASA rules during this phase of the migration?
A) Prefilter
B) Intrusion
C) Access Control
D) Identity
A) Prefilter
B) Intrusion
C) Access Control
D) Identity

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
38
Which two types of objects are reusable and supported by Cisco FMC? (Choose two.)
A) dynamic key mapping objects that help link HTTP and HTTPS GET requests to Layer 7 application protocols.
B) reputation-based objects that represent Security Intelligence feeds and lists, application filters based on category and reputation, and file lists
C) network-based objects that represent IP addresses and networks, port/protocol pairs, VLAN tags, security zones, and origin/destination country
D) network-based objects that represent FQDN mappings and networks, port/protocol pairs, VXLAN tags, security zones and origin/destination country
E) reputation-based objects, such as URL categories
A) dynamic key mapping objects that help link HTTP and HTTPS GET requests to Layer 7 application protocols.
B) reputation-based objects that represent Security Intelligence feeds and lists, application filters based on category and reputation, and file lists
C) network-based objects that represent IP addresses and networks, port/protocol pairs, VLAN tags, security zones, and origin/destination country
D) network-based objects that represent FQDN mappings and networks, port/protocol pairs, VXLAN tags, security zones and origin/destination country
E) reputation-based objects, such as URL categories

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
39
Which Firepower feature allows users to configure bridges in routed mode and enables devices to perform Layer 2 switching between interfaces?
A) FlexConfig
B) BDI
C) SGT
D) IRB
A) FlexConfig
B) BDI
C) SGT
D) IRB

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
40
After deploying a network-monitoring tool to manage and monitor networking devices in your organization, you realize that you need to manually upload an MIB for the Cisco FMC. In which folder should you upload the MIB file?
A) /etc/sf/DCMIB.ALERT
B) /sf/etc/DCEALERT.MIB
C) /etc/sf/DCEALERT.MIB
D) system/etc/DCEALERT.MIB
A) /etc/sf/DCMIB.ALERT
B) /sf/etc/DCEALERT.MIB
C) /etc/sf/DCEALERT.MIB
D) system/etc/DCEALERT.MIB

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
41
What is a behavior of a Cisco FMC database purge?
A) User login and history data are removed from the database if the User Activity check box is selected.
B) Data is recovered from the device.
C) The appropriate process is restarted.
D) The specified data is removed from Cisco FMC and kept for two weeks.
A) User login and history data are removed from the database if the User Activity check box is selected.
B) Data is recovered from the device.
C) The appropriate process is restarted.
D) The specified data is removed from Cisco FMC and kept for two weeks.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
42
Which command is typed at the CLI on the primary Cisco FTD unit to temporarily stop running high-availability?
A) configure high-availability resume
B) configure high-availability disable
C) system support network-options
D) configure high-availability suspend
A) configure high-availability resume
B) configure high-availability disable
C) system support network-options
D) configure high-availability suspend

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
43
Which command is entered in the Cisco FMC CLI to generate a troubleshooting file?
A) show running-config
B) show tech-support chassis
C) system support diagnostic-cli
D) sudo sf_troubleshoot.pl
A) show running-config
B) show tech-support chassis
C) system support diagnostic-cli
D) sudo sf_troubleshoot.pl

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
44
An administrator is attempting to remotely log into a switch in the data center using SSH and is unable to connect. How does the administrator confirm that traffic is reaching the firewall?
A) by performing a packet capture on the firewall
B) by attempting to access it from a different workstation
C) by running Wireshark on the administrator's PC
D) by running a packet tracer on the firewall
A) by performing a packet capture on the firewall
B) by attempting to access it from a different workstation
C) by running Wireshark on the administrator's PC
D) by running a packet tracer on the firewall

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
45
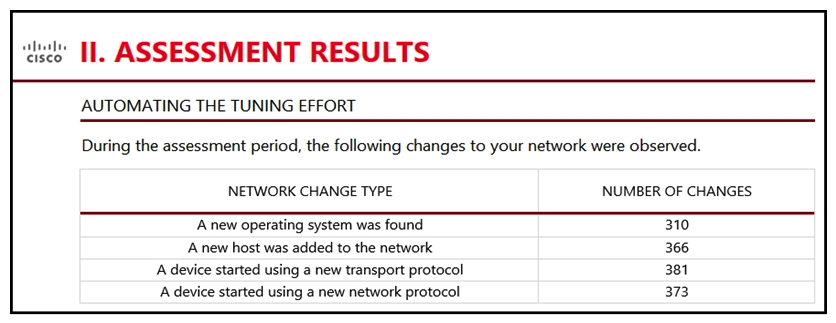 Refer to the exhibit. An engineer is analyzing the Attacks Risk Report and finds that there are over 300 instances of new operating systems being seen on the network. How is the Firepower configuration updated to protect these new operating systems?
Refer to the exhibit. An engineer is analyzing the Attacks Risk Report and finds that there are over 300 instances of new operating systems being seen on the network. How is the Firepower configuration updated to protect these new operating systems?A) The administrator manually updates the policies.
B) The administrator requests a Remediation Recommendation Report from Cisco Firepower.
C) Cisco Firepower gives recommendations to update the policies.
D) Cisco Firepower automatically updates the policies.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
46
A network engineer is receiving reports of users randomly getting disconnected from their corporate applications which traverse the data center FTD appliance. Network monitoring tools show that the FTD appliance utilization is peaking above 90% of total capacity. What must be done in order to further analyze this issue?
A) Use the Packet Export feature to save data onto external drives.
B) Use the Packet Capture feature to collect real-time network traffic.
C) Use the Packet Tracer feature for traffic policy analysis.
D) Use the Packet Analysis feature for capturing network data.
A) Use the Packet Export feature to save data onto external drives.
B) Use the Packet Capture feature to collect real-time network traffic.
C) Use the Packet Tracer feature for traffic policy analysis.
D) Use the Packet Analysis feature for capturing network data.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
47
A network administrator is configuring SNORT inspection policies and is seeing failed deployment messages in Cisco FMC. What information should the administrator generate for Cisco TAC to help troubleshoot?
A) A "troubleshoot" file for the device in question.
B) A "show tech" file for the device in question.
C) A "troubleshoot" file for the Cisco FMC.
D) A "show tech" for the Cisco FMC.
A) A "troubleshoot" file for the device in question.
B) A "show tech" file for the device in question.
C) A "troubleshoot" file for the Cisco FMC.
D) A "show tech" for the Cisco FMC.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
48
When is the file-size command needed while troubleshooting with packet capture?
A) when capture packets are less than 16 MB
B) when capture packets are restricted from the secondary memory
C) when capture packets exceed 10 GB
D) when capture packets exceed 32 MB
A) when capture packets are less than 16 MB
B) when capture packets are restricted from the secondary memory
C) when capture packets exceed 10 GB
D) when capture packets exceed 32 MB

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
49
After using Firepower for some time and learning about how it interacts with the network, an administrator is trying to correlate malicious activity with a user. Which widget should be configured to provide this visibility on the Cisco Firepower dashboards?
A) Current Sessions
B) Correlation Events
C) Current Status
D) Custom Analysis
A) Current Sessions
B) Correlation Events
C) Current Status
D) Custom Analysis

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
50
Which two packet captures does the FTD LINA engine support? (Choose two.)
A) Layer 7 network ID
B) source IP
C) application ID
D) dynamic firewall importing
E) protocol
A) Layer 7 network ID
B) source IP
C) application ID
D) dynamic firewall importing
E) protocol

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
51
What is the maximum bit size that Cisco FMC supports for HTTPS certificates?
A) 1024
B) 8192
C) 4096
D) 2048
A) 1024
B) 8192
C) 4096
D) 2048

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
52
Which command must be run to generate troubleshooting files on an FTD?
A) system support view-files
B) sudo sf_troubleshoot.pl
C) system generate-troubleshoot all
D) show tech-support
A) system support view-files
B) sudo sf_troubleshoot.pl
C) system generate-troubleshoot all
D) show tech-support

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
53
A network engineer is configuring URL Filtering on Cisco FTD. Which two port requirements on the FMC must be validated to allow communication with the cloud service? (Choose two.)
A) outbound port TCP/443
B) inbound port TCP/80
C) outbound port TCP/8080
D) inbound port TCP/443
E) outbound port TCP/80
A) outbound port TCP/443
B) inbound port TCP/80
C) outbound port TCP/8080
D) inbound port TCP/443
E) outbound port TCP/80

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
54
Which command-line mode is supported from the Cisco FMC CLI?
A) privileged
B) user
C) configuration
D) admin
A) privileged
B) user
C) configuration
D) admin

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
55
Which limitation applies to Cisco FMC dashboards in a multi-domain environment?
A) Child domains are able to view but not edit dashboards that originate from an ancestor domain.
B) Child domains have access to only a limited set of widgets from ancestor domains.
C) Only the administrator of the top ancestor domain is able to view dashboards.
D) Child domains are not able to view dashboards that originate from an ancestor domain.
A) Child domains are able to view but not edit dashboards that originate from an ancestor domain.
B) Child domains have access to only a limited set of widgets from ancestor domains.
C) Only the administrator of the top ancestor domain is able to view dashboards.
D) Child domains are not able to view dashboards that originate from an ancestor domain.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
56
Which two considerations must be made when deleting and re-adding devices while managing them via Cisco FMC? (Choose two.)
A) An option to re-apply NAT and VPN policies during registration is available, so users do not need to re-apply the policies after registration is completed.
B) Before re-adding the device in Cisco FMC, the manager must be added back.
C) Once a device has been deleted, it must be reconfigured before it is re-added to the Cisco FMC.
D) The Cisco FMC web interface prompts users to re-apply access control policies.
E) There is no option to re-apply NAT and VPN policies during registration available, so users need to re-apply the policies after registration is completed.
A) An option to re-apply NAT and VPN policies during registration is available, so users do not need to re-apply the policies after registration is completed.
B) Before re-adding the device in Cisco FMC, the manager must be added back.
C) Once a device has been deleted, it must be reconfigured before it is re-added to the Cisco FMC.
D) The Cisco FMC web interface prompts users to re-apply access control policies.
E) There is no option to re-apply NAT and VPN policies during registration available, so users need to re-apply the policies after registration is completed.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
57
An engineer has been asked to show application usages automatically on a monthly basis and send the information to management. What mechanism should be used to accomplish this task?
A) reports
B) context explorer
C) dashboards
D) event viewer
A) reports
B) context explorer
C) dashboards
D) event viewer

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
58
Which group within Cisco does the Threat Response team use for threat analysis and research?
A) Cisco Deep Analytics
B) OpenDNS Group
C) Cisco Network Response
D) Cisco Talos
A) Cisco Deep Analytics
B) OpenDNS Group
C) Cisco Network Response
D) Cisco Talos

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
59
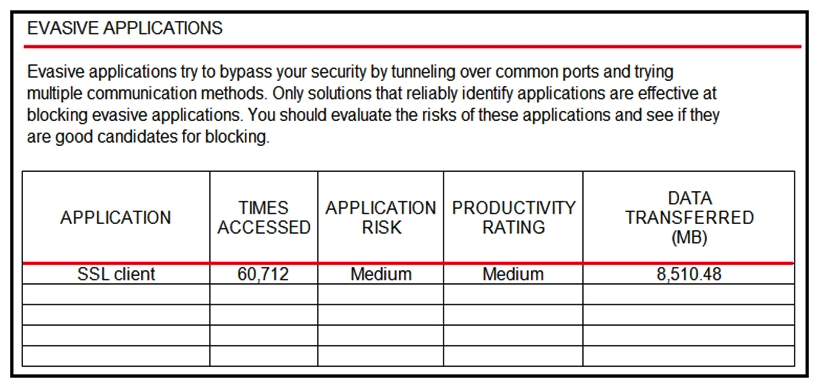 Refer to the exhibit. An administrator is looking at some of the reporting capabilities for Cisco Firepower and noticed this section of the Network Risk Report showing a lot of SSL activity that could be used for evasion. Which action will mitigate this risk?
Refer to the exhibit. An administrator is looking at some of the reporting capabilities for Cisco Firepower and noticed this section of the Network Risk Report showing a lot of SSL activity that could be used for evasion. Which action will mitigate this risk?A) Use SSL decryption to analyze the packets.
B) Use Cisco Tetration to track SSL connections to servers.
C) Use encrypted traffic analytics to detect attacks.
D) Use Cisco AMP for Endpoints to block all SSL connection.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
60
An engineer currently has a Cisco FTD device registered to the Cisco FMC and is assigned the address of 10.10.50.12. The organization is upgrading the addressing schemes and there is a requirement to convert the addresses to a format that provides an adequate amount of addresses on the network. What should the engineer do to ensure that the new addressing takes effect and can be used for the Cisco FTD to Cisco FMC connection?
A) Update the IP addresses from IPv4 to IPv6 without deleting from Cisco FMC.
B) Format and reregister the device to Cisco FMC.
C) Cisco FMC does not support devices that use IPv4 IP addresses.
D) Delete and reregister the device to Cisco FMC.
A) Update the IP addresses from IPv4 to IPv6 without deleting from Cisco FMC.
B) Format and reregister the device to Cisco FMC.
C) Cisco FMC does not support devices that use IPv4 IP addresses.
D) Delete and reregister the device to Cisco FMC.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
61
A network administrator discovers that a user connected to a file server and downloaded a malware file. The Cisco FMC generated an alert for the malware event, however the user still remained connected. Which Cisco AMP file rule action within the Cisco FMC must be set to resolve this issue?
A) Malware Cloud Lookup
B) Reset Connection
C) Detect Files
D) Local Malware Analysis
A) Malware Cloud Lookup
B) Reset Connection
C) Detect Files
D) Local Malware Analysis

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
62
Which two conditions must be met to enable high availability between two Cisco FTD devices? (Choose two.)
A) same flash memory size
B) same NTP configuration
C) same DHCP/PPoE configuration
D) same host name
E) same number of interfaces
A) same flash memory size
B) same NTP configuration
C) same DHCP/PPoE configuration
D) same host name
E) same number of interfaces

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
63
Which feature within the Cisco FMC web interface allows for detecting, analyzing, and blocking malware in network traffic?
A) intrusion and file events
B) Cisco AMP for Networks
C) file policies
D) Cisco AMP for Endpoints
A) intrusion and file events
B) Cisco AMP for Networks
C) file policies
D) Cisco AMP for Endpoints

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
64
An engineer is tasked with deploying an internal perimeter firewall that will support multiple DMZs. Each DMZ has a unique private IP subnet range. How is this requirement satisfied?
A) Deploy the firewall in transparent mode with access control policies
B) Deploy the firewall in routed mode with access control policies
C) Deploy the firewall in routed mode with NAT configured
D) Deploy the firewall in transparent mode with NAT configured
A) Deploy the firewall in transparent mode with access control policies
B) Deploy the firewall in routed mode with access control policies
C) Deploy the firewall in routed mode with NAT configured
D) Deploy the firewall in transparent mode with NAT configured

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
65
Which Cisco AMP for Endpoints policy is used only for monitoring endpoint activity?
A) Windows domain controller
B) audit
C) triage
D) protection
A) Windows domain controller
B) audit
C) triage
D) protection

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
66
An engineer is monitoring network traffic from their sales and product development departments, which are on two separate networks. What must be configured in order to maintain data privacy for both departments?
A) Use passive IDS ports for both departments.
B) Use a dedicated IPS inline set for each department to maintain traffic separation.
C) Use 802.1Q inline set Trunk interfaces with VLANs to maintain logical traffic separation.
D) Use one pair of inline set in TAP mode for both departments.
A) Use passive IDS ports for both departments.
B) Use a dedicated IPS inline set for each department to maintain traffic separation.
C) Use 802.1Q inline set Trunk interfaces with VLANs to maintain logical traffic separation.
D) Use one pair of inline set in TAP mode for both departments.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
67
With Cisco FTD software, which interface mode must be configured to passively receive traffic that passes through the appliance?
A) inline set
B) passive
C) routed
D) inline tap
A) inline set
B) passive
C) routed
D) inline tap

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
68
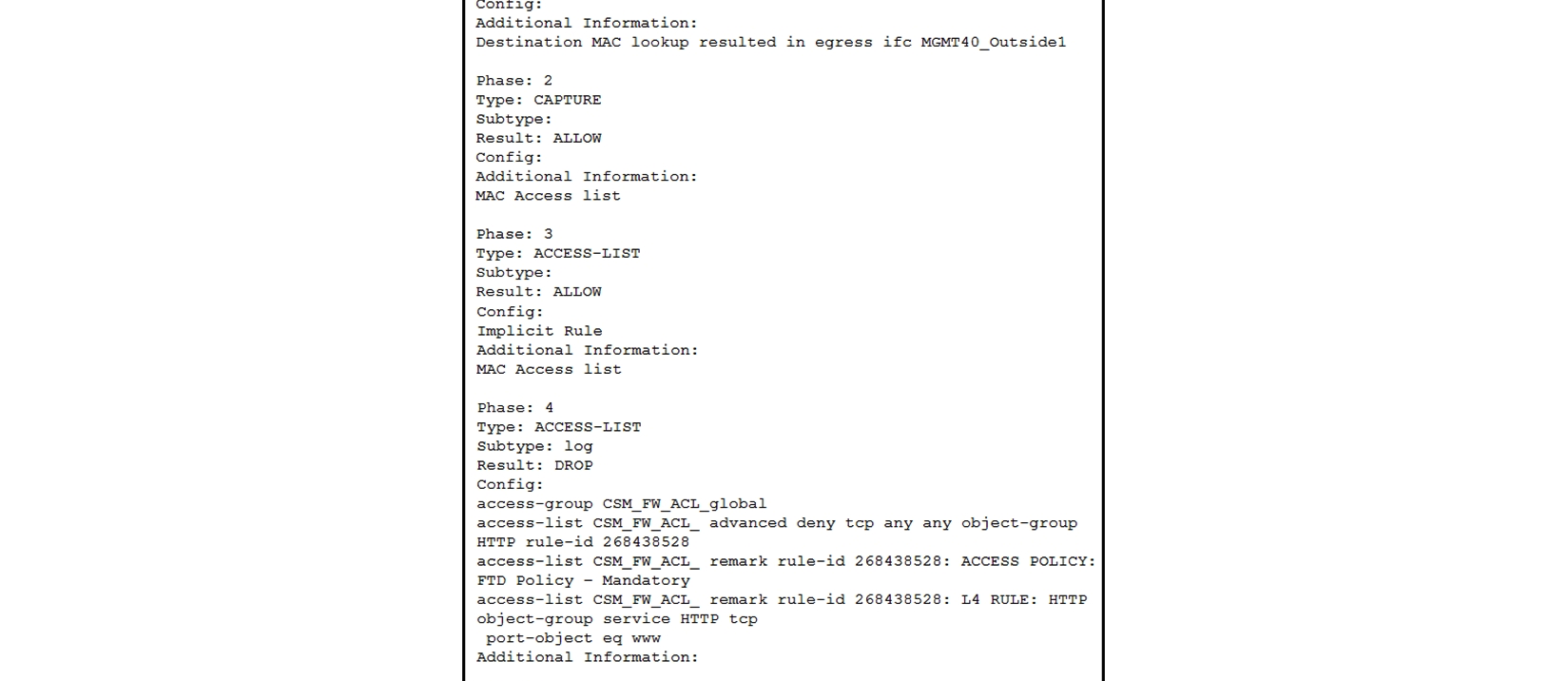 Refer to the exhibit. What must be done to fix access to this website while preventing the same communication to all other websites?
Refer to the exhibit. What must be done to fix access to this website while preventing the same communication to all other websites?A) Create an intrusion policy rule to have Snort allow port 80 to only 172.1.1.50.
B) Create an intrusion policy rule to have Snort allow port 443 to only 172.1.1.50.
C) Create an access control policy rule to allow port 443 to only 172.1.1.50.
D) Create an access control policy rule to allow port 80 to only 172.1.1.50.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
69
An engineer is configuring a Cisco FTD appliance in IPS-only mode and needs to utilize fail-to-wire interfaces. Which interface mode should be used to meet these requirements?
A) passive
B) routed
C) transparent
D) inline set
A) passive
B) routed
C) transparent
D) inline set

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
70
What are the minimum requirements to deploy a managed device inline?
A) inline interfaces, security zones, MTU, and mode
B) passive interface, MTU, and mode
C) inline interfaces, MTU, and mode
D) passive interface, security zone, MTU, and mode
A) inline interfaces, security zones, MTU, and mode
B) passive interface, MTU, and mode
C) inline interfaces, MTU, and mode
D) passive interface, security zone, MTU, and mode

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
71
Which action should you take when Cisco Threat Response notifies you that AMP has identified a file as malware?
A) Add the malicious file to the block list.
B) Send a snapshot to Cisco for technical support.
C) Forward the result of the investigation to an external threat-analysis engine.
D) Wait for Cisco Threat Response to automatically block the malware.
A) Add the malicious file to the block list.
B) Send a snapshot to Cisco for technical support.
C) Forward the result of the investigation to an external threat-analysis engine.
D) Wait for Cisco Threat Response to automatically block the malware.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
72
An organization has a compliance requirement to protect servers from clients, however, the clients and servers all reside on the same Layer 3 network. Without readdressing IP subnets for clients or servers, how is segmentation achieved?
A) Change the IP addresses of the servers, while remaining on the same subnet.
B) Deploy a firewall in routed mode between the clients and servers.
C) Change the IP addresses of the clients, while remaining on the same subnet.
D) Deploy a firewall in transparent mode between the clients and servers.
A) Change the IP addresses of the servers, while remaining on the same subnet.
B) Deploy a firewall in routed mode between the clients and servers.
C) Change the IP addresses of the clients, while remaining on the same subnet.
D) Deploy a firewall in transparent mode between the clients and servers.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
73
An administrator is setting up Cisco FirePower to send data to the Cisco Stealthwatch appliances. The NetFlow_Set_Parameters objet is already created, but NetFlow is not being sent to the flow collector. What must be done to prevent this from occurring?
A) Create a service identifier to enable the NetFlow service.
B) Add the NetFlow_Send_Destination object to the configuration.
C) Create a Security Intelligence object to send the data to Cisco Stealthwatch.
D) Add the NetFlow_Add_Destination object to the configuration.
A) Create a service identifier to enable the NetFlow service.
B) Add the NetFlow_Send_Destination object to the configuration.
C) Create a Security Intelligence object to send the data to Cisco Stealthwatch.
D) Add the NetFlow_Add_Destination object to the configuration.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
74
In a multi-tenant deployment where multiple domains are in use, which update should be applied outside of the Global Domain?
A) minor upgrade
B) local import of intrusion rules
C) Cisco Geolocation Database
D) local import of major upgrade
A) minor upgrade
B) local import of intrusion rules
C) Cisco Geolocation Database
D) local import of major upgrade

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
75
Which two remediation options are available when Cisco FMC is integrated with Cisco ISE? (Choose two.)
A) dynamic null route configured
B) DHCP pool disablement
C) quarantine
D) port shutdown
E) host shutdown
A) dynamic null route configured
B) DHCP pool disablement
C) quarantine
D) port shutdown
E) host shutdown

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
76
An engineer is configuring a second Cisco FMC as a standby device but is unable to register with the active unit. What is causing this issue?
A) The code versions running on the Cisco FMC devices are different.
B) The licensing purchased does not include high availability.
C) The primary FMC currently has devices connected to it.
D) There is only 10 Mbps of bandwidth between the two devices.
A) The code versions running on the Cisco FMC devices are different.
B) The licensing purchased does not include high availability.
C) The primary FMC currently has devices connected to it.
D) There is only 10 Mbps of bandwidth between the two devices.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
77
Which connector is used to integrate Cisco ISE with Cisco FMC for Rapid Threat Containment?
A) pxGrid
B) FTD RTC
C) FMC RTC
D) ISEGrid
A) pxGrid
B) FTD RTC
C) FMC RTC
D) ISEGrid

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
78
What is a result of enabling Cisco FTD clustering?
A) For the dynamic routing feature, if the master unit fails, the newly elected master unit maintains all existing connections.
B) Integrated Routing and Bridging is supported on the master unit.
C) Site-to-site VPN functionality is limited to the master unit, and all VPN connections are dropped if the master unit fails.
D) All Firepower appliances support Cisco FTD clustering.
A) For the dynamic routing feature, if the master unit fails, the newly elected master unit maintains all existing connections.
B) Integrated Routing and Bridging is supported on the master unit.
C) Site-to-site VPN functionality is limited to the master unit, and all VPN connections are dropped if the master unit fails.
D) All Firepower appliances support Cisco FTD clustering.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
79
Which license type is required on Cisco ISE to integrate with Cisco FMC pxGrid?
A) apex
B) plus
C) base
D) mobility
A) apex
B) plus
C) base
D) mobility

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck
80
What is a characteristic of bridge groups on a Cisco FTD?
A) In routed firewall mode, routing between bridge groups is supported.
B) Routing between bridge groups is achieved only with a router-on-a-stick configuration on a connected router.
C) In routed firewall mode, routing between bridge groups must pass through a routed interface.
D) In transparent firewall mode, routing between bridge groups is supported.
A) In routed firewall mode, routing between bridge groups is supported.
B) Routing between bridge groups is achieved only with a router-on-a-stick configuration on a connected router.
C) In routed firewall mode, routing between bridge groups must pass through a routed interface.
D) In transparent firewall mode, routing between bridge groups is supported.

Unlock Deck
Unlock for access to all 130 flashcards in this deck.
Unlock Deck
k this deck



