Deck 10: Service Provider Routing and Switching, Specialist
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/78
Play
Full screen (f)
Deck 10: Service Provider Routing and Switching, Specialist
1
Click the Exhibit button. 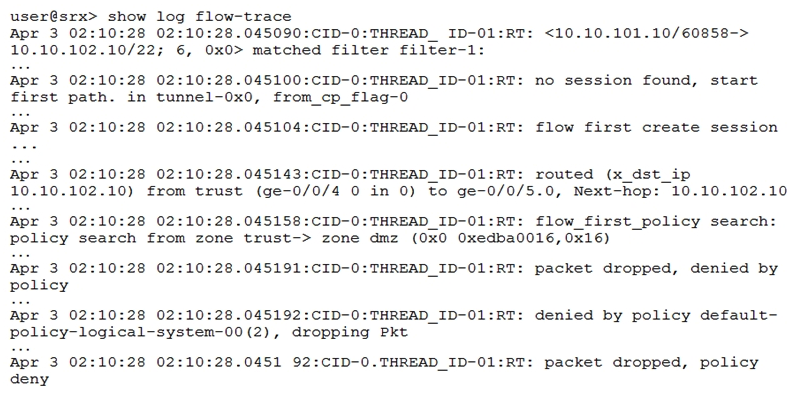 The exhibit shows a snippet of a security flow trace. A user cannot open an SSH session to a server. Which action will solve the problem?
The exhibit shows a snippet of a security flow trace. A user cannot open an SSH session to a server. Which action will solve the problem?
A) Create a security policy that matches the traffic parameters
B) Edit the source NAT to correct the translated address
C) Create a route entry to direct traffic into the configured tunnel
D) Create a route to the desired server
 The exhibit shows a snippet of a security flow trace. A user cannot open an SSH session to a server. Which action will solve the problem?
The exhibit shows a snippet of a security flow trace. A user cannot open an SSH session to a server. Which action will solve the problem?A) Create a security policy that matches the traffic parameters
B) Edit the source NAT to correct the translated address
C) Create a route entry to direct traffic into the configured tunnel
D) Create a route to the desired server
Create a security policy that matches the traffic parameters
2
Click the Exhibit button. 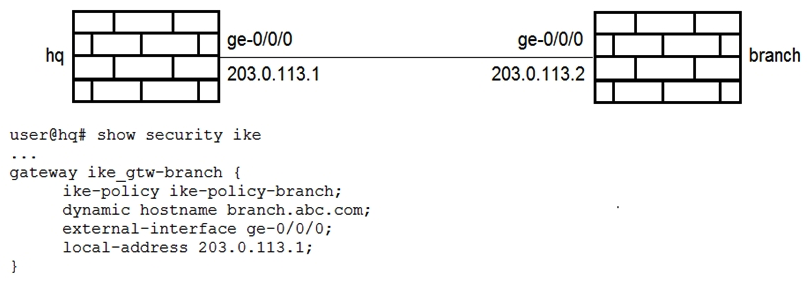 The IKE policy and proposal are configured properly on both devices as shown in the exhibit. Which configuration snippet will complete the IKE configuration on the branch SRX Series device?
The IKE policy and proposal are configured properly on both devices as shown in the exhibit. Which configuration snippet will complete the IKE configuration on the branch SRX Series device?
A)
B)
C)
D)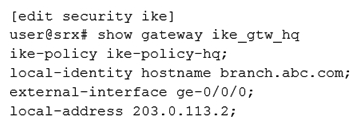
 The IKE policy and proposal are configured properly on both devices as shown in the exhibit. Which configuration snippet will complete the IKE configuration on the branch SRX Series device?
The IKE policy and proposal are configured properly on both devices as shown in the exhibit. Which configuration snippet will complete the IKE configuration on the branch SRX Series device?A)

B)

C)

D)


3
Which feature of Sky ATP is deployed with Policy Enforcer?
A) zero-day threat mitigation
B) software image snapshot support
C) device inventory management
D) service redundancy daemon configuration support
A) zero-day threat mitigation
B) software image snapshot support
C) device inventory management
D) service redundancy daemon configuration support
zero-day threat mitigation
4
Which three types of peer devices are supported for CoS-based IPsec VPNs? (Choose three.)
A) branch SRX Series device
B) third-party device
C) cSRX
D) high-end SRX Series device
E) vSRX
A) branch SRX Series device
B) third-party device
C) cSRX
D) high-end SRX Series device
E) vSRX

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
5
Click the Exhibit button.  While configuring the SRX345, you review the MACsec connection between devices and note that it is not working. Referring to the exhibit, which action would you use to identify problem?
While configuring the SRX345, you review the MACsec connection between devices and note that it is not working. Referring to the exhibit, which action would you use to identify problem?
A) Verify that the formatting settings are correct between the devices and that the software supports the version of MACsec in use
B) Verify that the connectivity association key and the connectivity association key name match on both devices
C) Verify that the transmission path is not replicating packets or correcting frame check sequence error packets
D) Verify that the interface between the two devices is up and not experiencing errors
 While configuring the SRX345, you review the MACsec connection between devices and note that it is not working. Referring to the exhibit, which action would you use to identify problem?
While configuring the SRX345, you review the MACsec connection between devices and note that it is not working. Referring to the exhibit, which action would you use to identify problem?A) Verify that the formatting settings are correct between the devices and that the software supports the version of MACsec in use
B) Verify that the connectivity association key and the connectivity association key name match on both devices
C) Verify that the transmission path is not replicating packets or correcting frame check sequence error packets
D) Verify that the interface between the two devices is up and not experiencing errors

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
6
Which three roles or protocols are required when configuring an ADVPN? (Choose three.)
A) OSPF
B) shortcut partner
C) shortcut suggester
D) IKEv1
E) BGP
A) OSPF
B) shortcut partner
C) shortcut suggester
D) IKEv1
E) BGP

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
7
Click the Exhibit button. 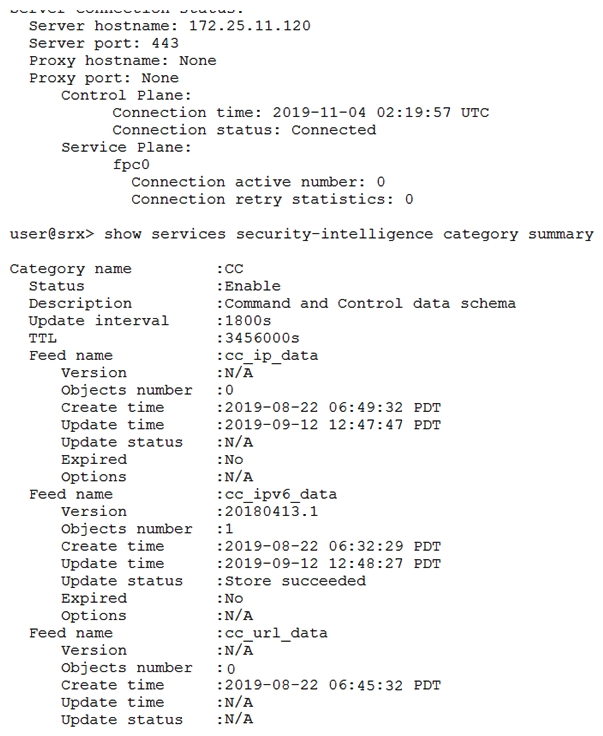 Referring to the exhibit, which two statements are true? (Choose two.)
Referring to the exhibit, which two statements are true? (Choose two.)
A) The SRX Series device is enrolled and communicating with a JATP Appliance
B) The JATP Appliance cannot download the security feeds from the GSS servers
C) The SRX Series device cannot download the security feeds from the JATP Appliance
D) The SRX Series device is not enrolled but can communicate with the JATP Appliance
 Referring to the exhibit, which two statements are true? (Choose two.)
Referring to the exhibit, which two statements are true? (Choose two.)A) The SRX Series device is enrolled and communicating with a JATP Appliance
B) The JATP Appliance cannot download the security feeds from the GSS servers
C) The SRX Series device cannot download the security feeds from the JATP Appliance
D) The SRX Series device is not enrolled but can communicate with the JATP Appliance

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
8
Click the Exhibit button. 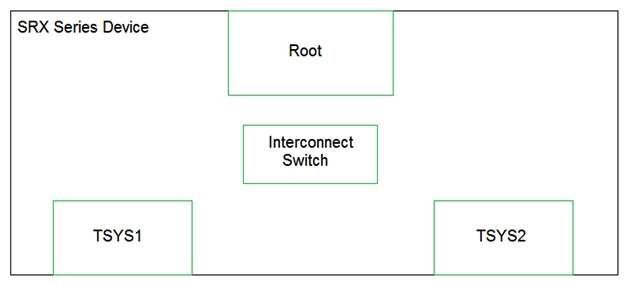 You have configured tenant systems on your SRX Series device. Referring to the exhibit, which two actions should you take to facilitate inter-TSYS communication? (Choose two.)
You have configured tenant systems on your SRX Series device. Referring to the exhibit, which two actions should you take to facilitate inter-TSYS communication? (Choose two.)
A) Place the logical tunnel interfaces in a virtual router routing instance in the interconnect switch
B) Place the logical tunnel interfaces in a VPLS routing instance in the interconnect switch
C) Connect each TSYS with the interconnect switch by configuring INET configured logical tunnel interfaces in the interconnect switch
D) Connect each TSYS with the interconnect switch by configuring Ethernet VPLS configured logical tunnel interfaces in the interconnect switch
 You have configured tenant systems on your SRX Series device. Referring to the exhibit, which two actions should you take to facilitate inter-TSYS communication? (Choose two.)
You have configured tenant systems on your SRX Series device. Referring to the exhibit, which two actions should you take to facilitate inter-TSYS communication? (Choose two.)A) Place the logical tunnel interfaces in a virtual router routing instance in the interconnect switch
B) Place the logical tunnel interfaces in a VPLS routing instance in the interconnect switch
C) Connect each TSYS with the interconnect switch by configuring INET configured logical tunnel interfaces in the interconnect switch
D) Connect each TSYS with the interconnect switch by configuring Ethernet VPLS configured logical tunnel interfaces in the interconnect switch

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
9
Which interface family is required for Layer 2 transparent mode on SRX Series devices?
A) LLDP
B) Ethernet switching
C) inet
D) VPLS
A) LLDP
B) Ethernet switching
C) inet
D) VPLS

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
10
Click the Exhibit button. ![<strong>Click the Exhibit button. You deployed a site-to-site IPsec VPN connecting two data centers together using SRX5800s. After examining the performance of the IPsec VPN, you decide to enable IPsec performance acceleration to increase the rate of traffic that can be sent through the tunnel. Referring to the exhibit, which two statements should you add to the configuration to accomplish this task? (Choose two.)</strong> A) [edit security flow] user@srx# set tcp-mss ipsec-vpn mss 65535 B) user@srx# set ipsec-performance-acceleration C) user@srx# set power-mode-ipsec D) user@srx# set load-distribution session-affinity ipsec](https://d2lvgg3v3hfg70.cloudfront.net/C1585/11ec5107_4632_fc49_b560_8f5351039a35_C1585_00.jpg) You deployed a site-to-site IPsec VPN connecting two data centers together using SRX5800s. After examining the performance of the IPsec VPN, you decide to enable IPsec performance acceleration to increase the rate of traffic that can be sent through the tunnel. Referring to the exhibit, which two statements should you add to the configuration to accomplish this task? (Choose two.)
You deployed a site-to-site IPsec VPN connecting two data centers together using SRX5800s. After examining the performance of the IPsec VPN, you decide to enable IPsec performance acceleration to increase the rate of traffic that can be sent through the tunnel. Referring to the exhibit, which two statements should you add to the configuration to accomplish this task? (Choose two.)
A) [edit security flow] user@srx# set tcp-mss ipsec-vpn mss 65535
B) user@srx# set ipsec-performance-acceleration
C) user@srx# set power-mode-ipsec
D) user@srx# set load-distribution session-affinity ipsec
![<strong>Click the Exhibit button. You deployed a site-to-site IPsec VPN connecting two data centers together using SRX5800s. After examining the performance of the IPsec VPN, you decide to enable IPsec performance acceleration to increase the rate of traffic that can be sent through the tunnel. Referring to the exhibit, which two statements should you add to the configuration to accomplish this task? (Choose two.)</strong> A) [edit security flow] user@srx# set tcp-mss ipsec-vpn mss 65535 B) user@srx# set ipsec-performance-acceleration C) user@srx# set power-mode-ipsec D) user@srx# set load-distribution session-affinity ipsec](https://d2lvgg3v3hfg70.cloudfront.net/C1585/11ec5107_4632_fc49_b560_8f5351039a35_C1585_00.jpg) You deployed a site-to-site IPsec VPN connecting two data centers together using SRX5800s. After examining the performance of the IPsec VPN, you decide to enable IPsec performance acceleration to increase the rate of traffic that can be sent through the tunnel. Referring to the exhibit, which two statements should you add to the configuration to accomplish this task? (Choose two.)
You deployed a site-to-site IPsec VPN connecting two data centers together using SRX5800s. After examining the performance of the IPsec VPN, you decide to enable IPsec performance acceleration to increase the rate of traffic that can be sent through the tunnel. Referring to the exhibit, which two statements should you add to the configuration to accomplish this task? (Choose two.)A) [edit security flow] user@srx# set tcp-mss ipsec-vpn mss 65535
B) user@srx# set ipsec-performance-acceleration
C) user@srx# set power-mode-ipsec
D) user@srx# set load-distribution session-affinity ipsec

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
11
When would you use the port-overloading-factor 1 setting?
A) to enable the port-overloading
B) to disable the port-overloading
C) to map ports with 1:1 ratio for port-overloading
D) to set the maximum port-overloading capacity to 65,536
A) to enable the port-overloading
B) to disable the port-overloading
C) to map ports with 1:1 ratio for port-overloading
D) to set the maximum port-overloading capacity to 65,536

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
12
You are asked to implement the session cache feature on an SRX5400. In this scenario, what information does a session cache entry record? (Choose two.)
A) The type of processing to do for ingress traffic
B) The type of processing to do for egress traffic
C) To which SPU the traffic of the session should be forwarded
D) To which NPU the traffic of the session should be forwarded
A) The type of processing to do for ingress traffic
B) The type of processing to do for egress traffic
C) To which SPU the traffic of the session should be forwarded
D) To which NPU the traffic of the session should be forwarded

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
13
Click the Exhibit button. 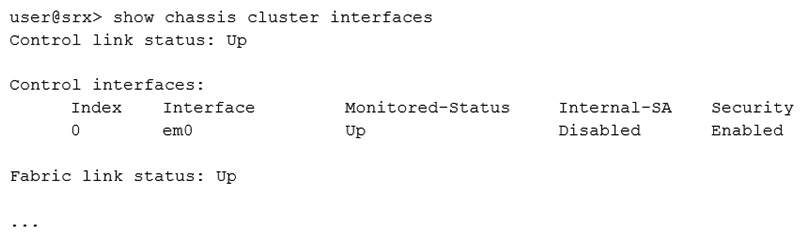 Referring to the exhibit, which statement is true?
Referring to the exhibit, which statement is true?
A) ARP security is securing data across the control interface
B) IPsec is securing data across the control interface
C) SSH is securing data across the control interface
D) MACsec is securing data across the control interface
 Referring to the exhibit, which statement is true?
Referring to the exhibit, which statement is true?A) ARP security is securing data across the control interface
B) IPsec is securing data across the control interface
C) SSH is securing data across the control interface
D) MACsec is securing data across the control interface

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
14
You have set up Security Director with Policy Enforcer and have configured 12 third-party feeds and a Sky ATP feed. You are also injecting 16 feeds using the available open API. You want to add another compatible feed using the available open API, but Policy Enforcer is not receiving the new feed. What is the problem in this scenario?
A) You must wait 48 hours for the feed to update
B) You cannot add more than 16 feeds through the available open API
C) You have reached the maximum limit of 29 total feeds
D) You cannot add more than 16 feeds with the available open API
A) You must wait 48 hours for the feed to update
B) You cannot add more than 16 feeds through the available open API
C) You have reached the maximum limit of 29 total feeds
D) You cannot add more than 16 feeds with the available open API

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
15
Click the Exhibit button.  You are implementing a new branch site and want to ensure Internet traffic is sent directly to your ISP and other traffic is sent to your company headquarters. You have configured filter-based forwarding to accomplish this objective. You verify proper functionality using the outputs shown in the exhibit. Which two statements are true in this scenario? (Choose two.)
You are implementing a new branch site and want to ensure Internet traffic is sent directly to your ISP and other traffic is sent to your company headquarters. You have configured filter-based forwarding to accomplish this objective. You verify proper functionality using the outputs shown in the exhibit. Which two statements are true in this scenario? (Choose two.)
A) The session utilizes one routing instance
B) The ge-0/0/5 and ge-0/0/1 interfaces must reside in a single security zone
C) The ge-0/0/5 and ge-0/0/1 interfaces can reside in different security zones
D) The session utilizes two routing instances
 You are implementing a new branch site and want to ensure Internet traffic is sent directly to your ISP and other traffic is sent to your company headquarters. You have configured filter-based forwarding to accomplish this objective. You verify proper functionality using the outputs shown in the exhibit. Which two statements are true in this scenario? (Choose two.)
You are implementing a new branch site and want to ensure Internet traffic is sent directly to your ISP and other traffic is sent to your company headquarters. You have configured filter-based forwarding to accomplish this objective. You verify proper functionality using the outputs shown in the exhibit. Which two statements are true in this scenario? (Choose two.)A) The session utilizes one routing instance
B) The ge-0/0/5 and ge-0/0/1 interfaces must reside in a single security zone
C) The ge-0/0/5 and ge-0/0/1 interfaces can reside in different security zones
D) The session utilizes two routing instances

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
16
Click the Exhibit button. 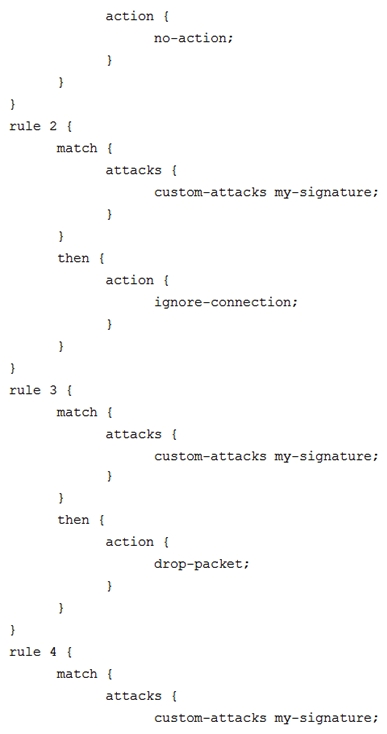 You have recently committed the IPS policy shown in the exhibit. When evaluating the expected behavior, you notice that you have a session that matches all the rules in your IPS policy. In this scenario, which action would be taken?
You have recently committed the IPS policy shown in the exhibit. When evaluating the expected behavior, you notice that you have a session that matches all the rules in your IPS policy. In this scenario, which action would be taken?
A) drop packet
B) no-action
C) close-client-and-server
D) ignore-connection
 You have recently committed the IPS policy shown in the exhibit. When evaluating the expected behavior, you notice that you have a session that matches all the rules in your IPS policy. In this scenario, which action would be taken?
You have recently committed the IPS policy shown in the exhibit. When evaluating the expected behavior, you notice that you have a session that matches all the rules in your IPS policy. In this scenario, which action would be taken?A) drop packet
B) no-action
C) close-client-and-server
D) ignore-connection

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
17
You are asked to configure a new SRX Series CPE device at a remote office. The device must participate in forwarding MPLS and IPsec traffic. Which two statements are true regarding this implementation? (Choose two.)
A) Host inbound traffic must not be processed by the flow module
B) Host inbound traffic must be processed by the flow module
C) The SRX Series device can process both MPLS and IPsec with default traffic handling
D) A firewall filter must be configured to enable packet mode forwarding
A) Host inbound traffic must not be processed by the flow module
B) Host inbound traffic must be processed by the flow module
C) The SRX Series device can process both MPLS and IPsec with default traffic handling
D) A firewall filter must be configured to enable packet mode forwarding

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
18
You have configured three logical tunnel interfaces in a tenant system on an SRX1500 device. When committing the configuration, the commit fails. In this scenario, what would cause this problem?
A) There is no GRE tunnel between the tenant system and master system allowing SSH traffic
B) There is no VPLS switch on the tenant system containing a peer It-0/0/0 interface
C) The SRX1500 device does not support more than two logical interfaces per tenant system
D) The SRX1500 device requires a tunnel PIC to allow for logical tunnel interfaces
A) There is no GRE tunnel between the tenant system and master system allowing SSH traffic
B) There is no VPLS switch on the tenant system containing a peer It-0/0/0 interface
C) The SRX1500 device does not support more than two logical interfaces per tenant system
D) The SRX1500 device requires a tunnel PIC to allow for logical tunnel interfaces

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
19
You are asked to merge to corporate network with the network from a recently acquired company. Both networks use the same private IPv4 address space (172.25.126.0/24). An SRX Series device servers as the gateway for each network. Which solution allows you to merge the two networks without modifying the current address assignments?
A) persistent NAT
B) NAT46
C) source NAT
D) double NAT
A) persistent NAT
B) NAT46
C) source NAT
D) double NAT

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
20
You are asked to secure your network against TOR network traffic. Which two Juniper products would accomplish this task? (Choose two.)
A) Contrail Edge
B) Contrail Insights
C) Juniper Sky ATP
D) Juniper ATP Appliance
A) Contrail Edge
B) Contrail Insights
C) Juniper Sky ATP
D) Juniper ATP Appliance

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
21
Click the Exhibit button. 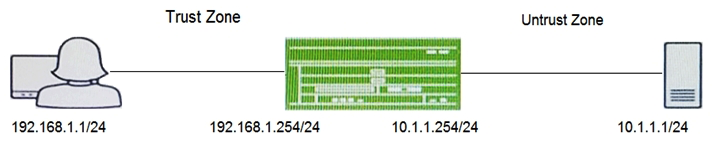 A user reports trouble when using SSH to a server outside your organization. The traffic traverses an SRX Series device that is performing NAT and applying security policies. Referring to the exhibit, which configuration will allow you to see the bidirectional flow through the SRX Series device?
A user reports trouble when using SSH to a server outside your organization. The traffic traverses an SRX Series device that is performing NAT and applying security policies. Referring to the exhibit, which configuration will allow you to see the bidirectional flow through the SRX Series device?
A)
B)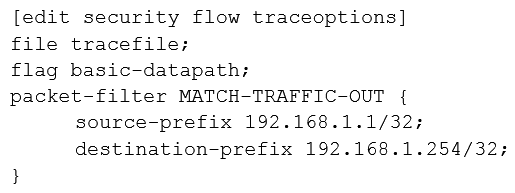
C)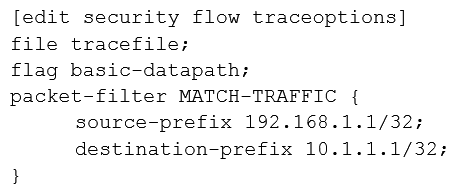
D)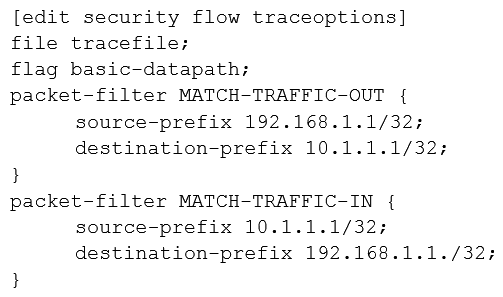
 A user reports trouble when using SSH to a server outside your organization. The traffic traverses an SRX Series device that is performing NAT and applying security policies. Referring to the exhibit, which configuration will allow you to see the bidirectional flow through the SRX Series device?
A user reports trouble when using SSH to a server outside your organization. The traffic traverses an SRX Series device that is performing NAT and applying security policies. Referring to the exhibit, which configuration will allow you to see the bidirectional flow through the SRX Series device?A)

B)

C)

D)


Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
22
Which two statements are true about ADVPN members? (Choose two.)
A) ADVPN members are authenticated using pre-shared keys
B) ADVPN members are authenticated using certificates
C) ADVPN members can use IKEv2
D) ADVPN members can use IKEv1
A) ADVPN members are authenticated using pre-shared keys
B) ADVPN members are authenticated using certificates
C) ADVPN members can use IKEv2
D) ADVPN members can use IKEv1

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
23
How does secure wire mode differ from transparent mode?
A) In secure wire mode, no switching lookup takes place to forward traffic
B) In secure wire mode, traffic can be modified using source NAT
C) In secure wire mode, IRB interfaces can be configured to route inter-VLAN traffic
D) In secure wire mode, security policies cannot be used to secure intra-VLAN traffic
A) In secure wire mode, no switching lookup takes place to forward traffic
B) In secure wire mode, traffic can be modified using source NAT
C) In secure wire mode, IRB interfaces can be configured to route inter-VLAN traffic
D) In secure wire mode, security policies cannot be used to secure intra-VLAN traffic

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
24
An administrator wants to implement persistent NAT for an internal resource so that external hosts are able to initiate communications to the resource, with the internal resource having previously sent packets to the external hosts. Which configuration setting is used to accomplish this goal?
A) persistent-nat permit any-remote-host
B) persistent-nat permit target-host-port
C) address-persistent
D) persistent-nat permit target-host
A) persistent-nat permit any-remote-host
B) persistent-nat permit target-host-port
C) address-persistent
D) persistent-nat permit target-host

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
25
Which two modes are supported on Juniper Sky ATP? (Choose two.)
A) private mode
B) global mode
C) tap mode
D) secure wire mode
A) private mode
B) global mode
C) tap mode
D) secure wire mode

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
26
Click the Exhibit button. 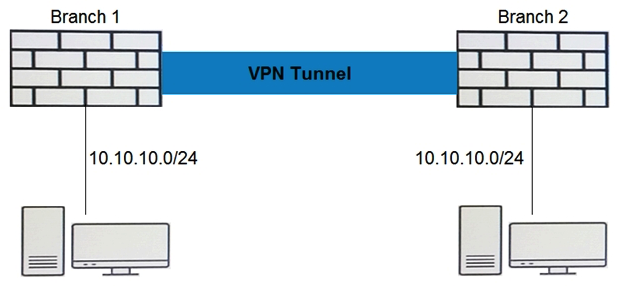 Branch 1 and Branch 2 have an active VPN tunnel configured, but internal hosts cannot communicate with each other. Referring to the exhibit, which type of configuration should be applied to solve the problem?
Branch 1 and Branch 2 have an active VPN tunnel configured, but internal hosts cannot communicate with each other. Referring to the exhibit, which type of configuration should be applied to solve the problem?
A) Configure destination NAT on both Branch 1 and Branch 2
B) Configure source NAT on Branch 1
C) Configure destination NAT on Branch 2 only
D) Configure static NAT on both Branch 1 and Branch 2
 Branch 1 and Branch 2 have an active VPN tunnel configured, but internal hosts cannot communicate with each other. Referring to the exhibit, which type of configuration should be applied to solve the problem?
Branch 1 and Branch 2 have an active VPN tunnel configured, but internal hosts cannot communicate with each other. Referring to the exhibit, which type of configuration should be applied to solve the problem?A) Configure destination NAT on both Branch 1 and Branch 2
B) Configure source NAT on Branch 1
C) Configure destination NAT on Branch 2 only
D) Configure static NAT on both Branch 1 and Branch 2

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
27
Click the Exhibit button. 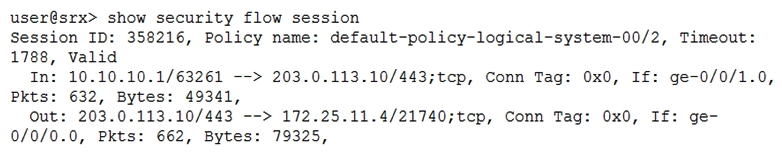 Referring to the exhibit, which statement is true?
Referring to the exhibit, which statement is true?
A) Source NAT with PAT is occurring
B) Destination NAT is occurring
C) Static NAT without PAT is occurring
D) Source NAT without PAT is occurring
 Referring to the exhibit, which statement is true?
Referring to the exhibit, which statement is true?A) Source NAT with PAT is occurring
B) Destination NAT is occurring
C) Static NAT without PAT is occurring
D) Source NAT without PAT is occurring

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
28
In which two ways are tenant systems different from logical systems? (Choose two.)
A) Tenant systems have higher scalability than logical systems
B) Tenant systems have less scalability than logical systems
C) Tenant systems have fewer routing features than logical systems
D) Tenant systems have more routing features than logical systems
A) Tenant systems have higher scalability than logical systems
B) Tenant systems have less scalability than logical systems
C) Tenant systems have fewer routing features than logical systems
D) Tenant systems have more routing features than logical systems

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
29
Click the Exhibit button. 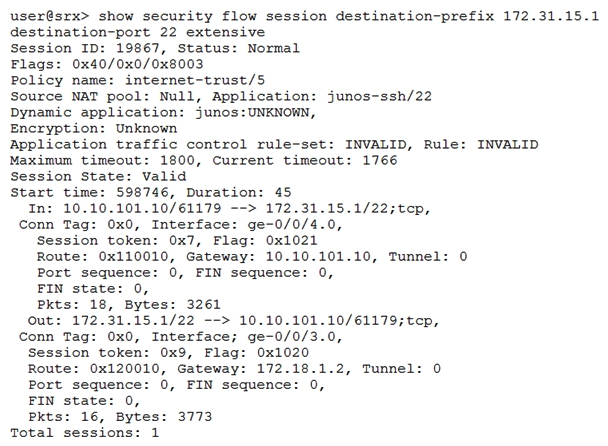 Given the command output shown in the exhibit, which two statements are true? (Choose two.)
Given the command output shown in the exhibit, which two statements are true? (Choose two.)
A) The host 172.31.15.1 is directly connected to interface ge-0/0/3.0
B) Traffic matching this session has been received since the session was established
C) The host 10.10.101.10 is directly connected to interface ge-0/0/4.0
D) Network Address Translation is applied to this session
 Given the command output shown in the exhibit, which two statements are true? (Choose two.)
Given the command output shown in the exhibit, which two statements are true? (Choose two.)A) The host 172.31.15.1 is directly connected to interface ge-0/0/3.0
B) Traffic matching this session has been received since the session was established
C) The host 10.10.101.10 is directly connected to interface ge-0/0/4.0
D) Network Address Translation is applied to this session

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
30
Which two VPN features are supported with CoS-based IPsec VPNs? (Choose two.)
A) IKEv2
B) VPN monitoring
C) dead peer detection
D) IKEv1
A) IKEv2
B) VPN monitoring
C) dead peer detection
D) IKEv1

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
31
You have a remote access VPN where the remote users are using the NCP client. The remote users can access the internal corporate resources as intended; however, traffic that is destined to all other Internet sites is going through the remote access VPN. You want to ensure that only traffic that is destined to the internal corporate resources use the remote access VPN. Which two actions should you take to accomplish this task? (Choose two.)
A) Enable the split tunneling feature within the VPN configuration on the SRX Series device
B) Enable IKEv2 within the VPN configuration on the SRX Series device
C) Configure the necessary traffic selectors within the VPN configuration on the SRX Series device
D) Configure split tunneling on the NCP profile on the remote client
A) Enable the split tunneling feature within the VPN configuration on the SRX Series device
B) Enable IKEv2 within the VPN configuration on the SRX Series device
C) Configure the necessary traffic selectors within the VPN configuration on the SRX Series device
D) Configure split tunneling on the NCP profile on the remote client

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
32
You are asked to set up notifications if one of your collector traffic feeds drops below 100 kbps. Which two configuration parameters must be set to accomplish this task? (Choose two.)
A) Set a traffic SNMP trap on the JATP appliance
B) Set a logging notification on the JATP appliance
C) Set a general triggered notification on the JATP appliance
D) Set a traffic system alert on the JATP appliance
A) Set a traffic SNMP trap on the JATP appliance
B) Set a logging notification on the JATP appliance
C) Set a general triggered notification on the JATP appliance
D) Set a traffic system alert on the JATP appliance

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
33
Click the Exhibit button. 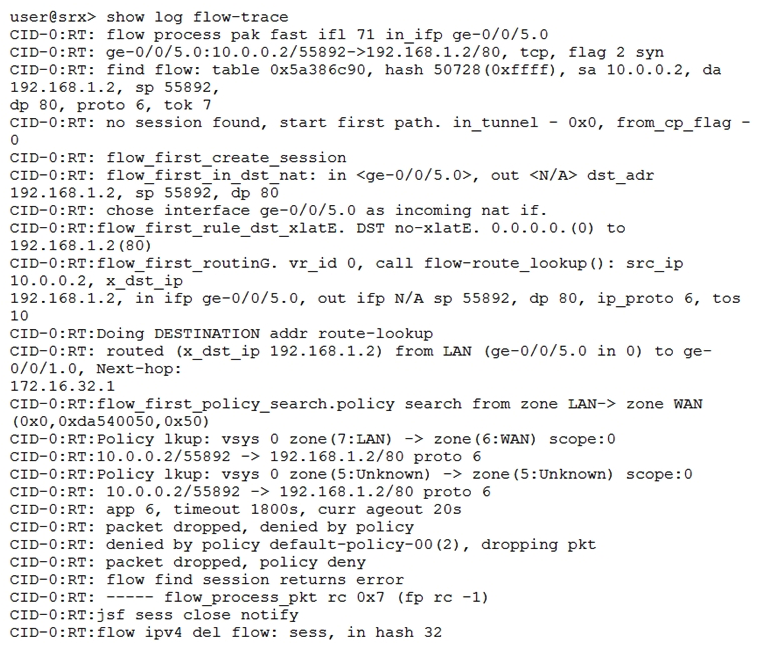 A host is unable to communicate with a webserver. Referring to the exhibit, which statement is correct?
A host is unable to communicate with a webserver. Referring to the exhibit, which statement is correct?
A) The webserver is not listening for traffic on port 80
B) A policy is denying the traffic between these two hosts
C) A session is created for this flow
D) The session table is running out of resources
 A host is unable to communicate with a webserver. Referring to the exhibit, which statement is correct?
A host is unable to communicate with a webserver. Referring to the exhibit, which statement is correct?A) The webserver is not listening for traffic on port 80
B) A policy is denying the traffic between these two hosts
C) A session is created for this flow
D) The session table is running out of resources

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
34
Click the Exhibit button. 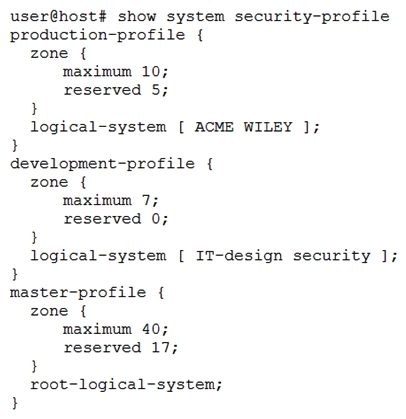 Referring to the exhibit, what is the maximum number of zones that are able to be created within all logical systems?
Referring to the exhibit, what is the maximum number of zones that are able to be created within all logical systems?
A) 74
B) 34
C) 40
D) 17
 Referring to the exhibit, what is the maximum number of zones that are able to be created within all logical systems?
Referring to the exhibit, what is the maximum number of zones that are able to be created within all logical systems?A) 74
B) 34
C) 40
D) 17

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
35
Your SRX Series device does not see the SYN packet. What is the default action in this scenario?
A) The device will forward the subsequent packets and the session will be established
B) The device will forward the subsequent packets and the session will not be established
C) The device will drop the subsequent packets and the session will not be established
D) The device will drop the subsequent packets and the session will be established
A) The device will forward the subsequent packets and the session will be established
B) The device will forward the subsequent packets and the session will not be established
C) The device will drop the subsequent packets and the session will not be established
D) The device will drop the subsequent packets and the session will be established

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
36
Click the Exhibit button. 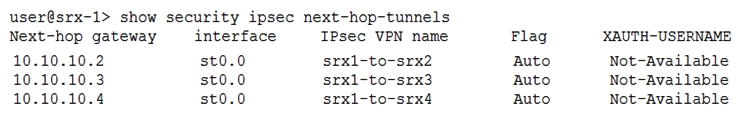 Which statement is correct regarding the information show in the exhibit?
Which statement is correct regarding the information show in the exhibit?
A) The tunnel binding was discovered automatically
B) The output is for an ADVPN
C) The tunnel gateway address was automatically discovered
D) The tunnel is not encrypting the traffic
 Which statement is correct regarding the information show in the exhibit?
Which statement is correct regarding the information show in the exhibit?A) The tunnel binding was discovered automatically
B) The output is for an ADVPN
C) The tunnel gateway address was automatically discovered
D) The tunnel is not encrypting the traffic

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
37
Click the Exhibit button. 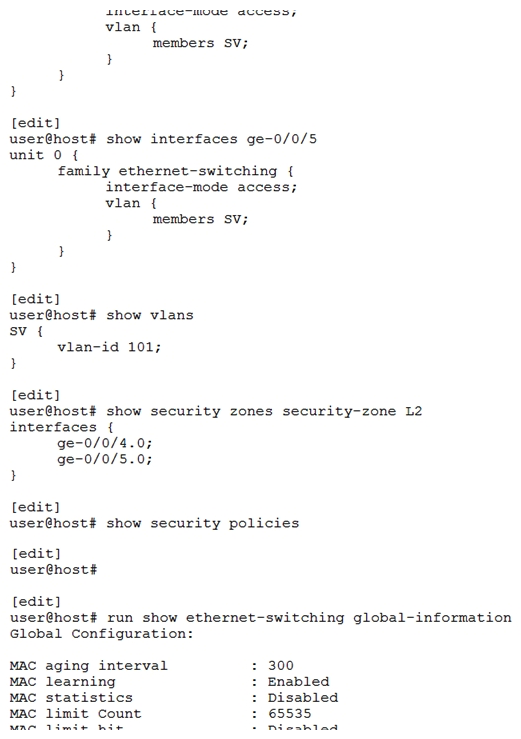 You have two hosts on the same subnet connecting to an SRX340 on interfaces ge-0/0/4 and ge-0/0/5. However, the two hosts cannot communicate with each other. Referring to the exhibit, what are two actions that would solve this problem? (Choose two.)
You have two hosts on the same subnet connecting to an SRX340 on interfaces ge-0/0/4 and ge-0/0/5. However, the two hosts cannot communicate with each other. Referring to the exhibit, what are two actions that would solve this problem? (Choose two.)
A) Set the SRX340 to Ethernet switching mode and reboot
B) Add an IRB interface to the VLAN
C) Put the ge-0/0/4 and ge-0/0/5 interfaces in different VLANs
D) Remove the ge-0/0/4 and ge-0/0/5 interfaces from the L2 security zone
 You have two hosts on the same subnet connecting to an SRX340 on interfaces ge-0/0/4 and ge-0/0/5. However, the two hosts cannot communicate with each other. Referring to the exhibit, what are two actions that would solve this problem? (Choose two.)
You have two hosts on the same subnet connecting to an SRX340 on interfaces ge-0/0/4 and ge-0/0/5. However, the two hosts cannot communicate with each other. Referring to the exhibit, what are two actions that would solve this problem? (Choose two.)A) Set the SRX340 to Ethernet switching mode and reboot
B) Add an IRB interface to the VLAN
C) Put the ge-0/0/4 and ge-0/0/5 interfaces in different VLANs
D) Remove the ge-0/0/4 and ge-0/0/5 interfaces from the L2 security zone

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
38
Click the Exhibit button. 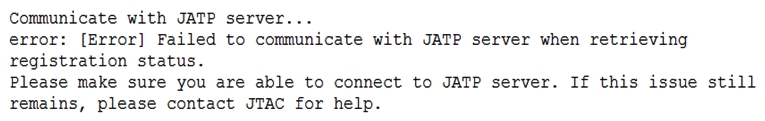 When attempting to enroll an SRX Series device to JATP, you receive the error shown in the exhibit. What is the cause of the error?
When attempting to enroll an SRX Series device to JATP, you receive the error shown in the exhibit. What is the cause of the error?
A) The fxp0 IP address is not routable
B) The SRX Series device certificate does not match the JATP certificate
C) The SRX Series device does not have an IP address assigned to the interface that accesses JATP
D) A firewall is blocking HTTPS on fxp0
 When attempting to enroll an SRX Series device to JATP, you receive the error shown in the exhibit. What is the cause of the error?
When attempting to enroll an SRX Series device to JATP, you receive the error shown in the exhibit. What is the cause of the error?A) The fxp0 IP address is not routable
B) The SRX Series device certificate does not match the JATP certificate
C) The SRX Series device does not have an IP address assigned to the interface that accesses JATP
D) A firewall is blocking HTTPS on fxp0

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
39
A user is unable to reach a necessary resource. You discover the path through the SRX Series device includes several security features. The traffic is not being evaluated by any security policies. In this scenario, which two components within the flow module would affect the traffic? (Choose two.)
A) services/ALG
B) destination NAT
C) source NAT
D) route lookup
A) services/ALG
B) destination NAT
C) source NAT
D) route lookup

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
40
In a Juniper ATP Appliance, what would be a reason for the mitigation rule to be in the failed-remove state?
A) The Juniper ATP Appliance received a commit error message from the SRX Series device
B) The Juniper ATP Appliance received an unknown error message from the SRX Series device
C) The Juniper ATP Appliance was not able to communicate with the SRX Series device
D) The Juniper ATP Appliance was not able to obtain the config lock
A) The Juniper ATP Appliance received a commit error message from the SRX Series device
B) The Juniper ATP Appliance received an unknown error message from the SRX Series device
C) The Juniper ATP Appliance was not able to communicate with the SRX Series device
D) The Juniper ATP Appliance was not able to obtain the config lock

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
41
You are trying to get a SSH honeypot set up on a Juniper ATP Appliance collector. The collector is running on hardware with two physical interfaces and two physical CPU cores. The honeypot feature is not working. Which statement is true in this scenario?
A) The collector must have at least three physical interfaces
B) The collector must have at least four physical cores
C) The collector must have at least four physical interfaces
D) The collector must have at least six physical cores
A) The collector must have at least three physical interfaces
B) The collector must have at least four physical cores
C) The collector must have at least four physical interfaces
D) The collector must have at least six physical cores

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
42
Click the Exhibit button. 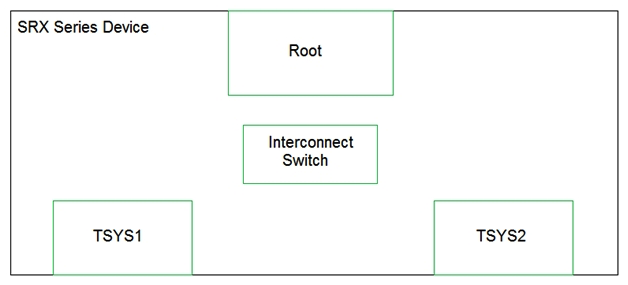 You have configured tenant systems on your SRX Series device. Referring to the exhibit, which two actions should you take to facilitate inter-TSYS communication? (Choose two.)
You have configured tenant systems on your SRX Series device. Referring to the exhibit, which two actions should you take to facilitate inter-TSYS communication? (Choose two.)
A) Place the logical tunnel interfaces in a virtual router routing instance in the interconnect switch
B) Place the logical tunnel interfaces in a VPLS routing instance in the interconnect switch
C) Connect each TSYS with the interconnect switch by configuring INET configured logical tunnel interfaces in the interconnect switch
D) Connect each TSYS with the interconnect switch by configuring Ethernet VPLS configured logical tunnel interfaces in the interconnect switch
 You have configured tenant systems on your SRX Series device. Referring to the exhibit, which two actions should you take to facilitate inter-TSYS communication? (Choose two.)
You have configured tenant systems on your SRX Series device. Referring to the exhibit, which two actions should you take to facilitate inter-TSYS communication? (Choose two.)A) Place the logical tunnel interfaces in a virtual router routing instance in the interconnect switch
B) Place the logical tunnel interfaces in a VPLS routing instance in the interconnect switch
C) Connect each TSYS with the interconnect switch by configuring INET configured logical tunnel interfaces in the interconnect switch
D) Connect each TSYS with the interconnect switch by configuring Ethernet VPLS configured logical tunnel interfaces in the interconnect switch

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
43
Which interface family is required for Layer 2 transparent mode on SRX Series devices?
A) LLDP
B) Ethernet switching
C) inet
D) VPLS
A) LLDP
B) Ethernet switching
C) inet
D) VPLS

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
44
Click the Exhibit button. 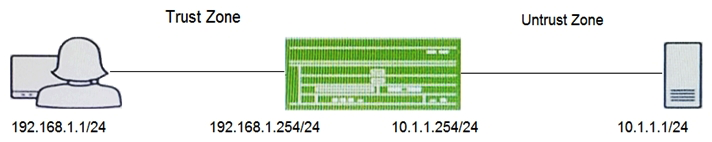 A user reports trouble when using SSH to a server outside your organization. The traffic traverses an SRX Series device that is performing NAT and applying security policies. Referring to the exhibit, which configuration will allow you to see the bidirectional flow through the SRX Series device?
A user reports trouble when using SSH to a server outside your organization. The traffic traverses an SRX Series device that is performing NAT and applying security policies. Referring to the exhibit, which configuration will allow you to see the bidirectional flow through the SRX Series device?
A)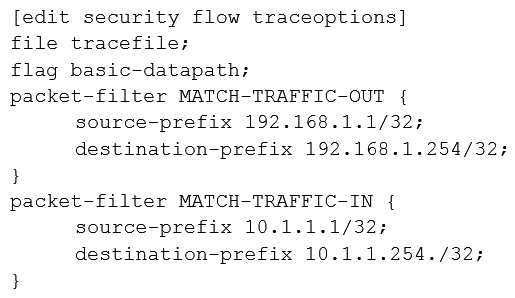
B)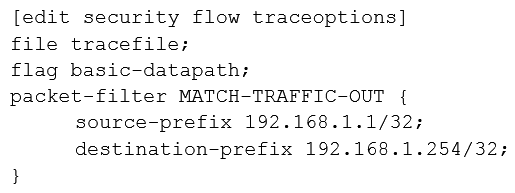
C)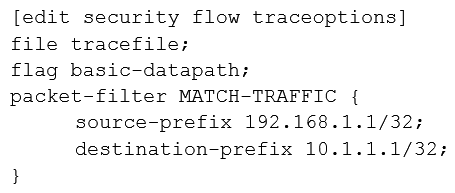
D)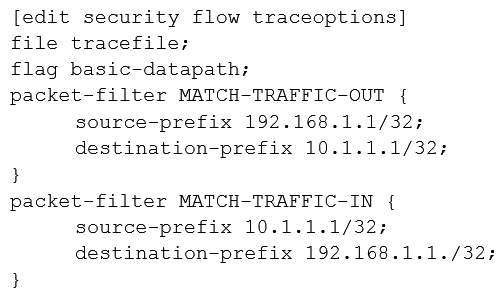
 A user reports trouble when using SSH to a server outside your organization. The traffic traverses an SRX Series device that is performing NAT and applying security policies. Referring to the exhibit, which configuration will allow you to see the bidirectional flow through the SRX Series device?
A user reports trouble when using SSH to a server outside your organization. The traffic traverses an SRX Series device that is performing NAT and applying security policies. Referring to the exhibit, which configuration will allow you to see the bidirectional flow through the SRX Series device?A)

B)

C)

D)


Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
45
Click the Exhibit button. 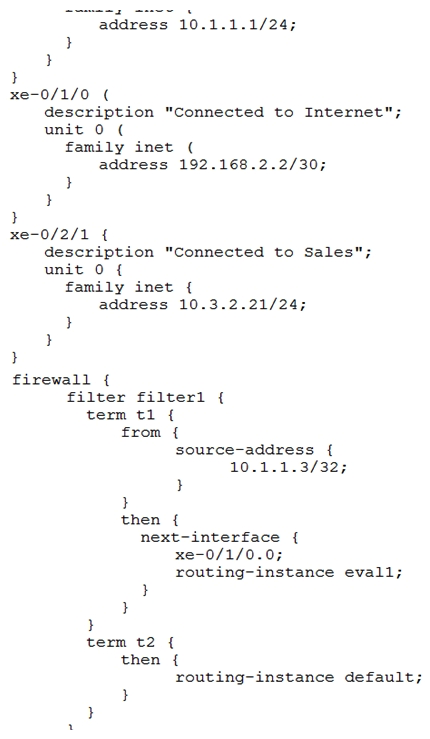 You are asked to look at a configuration that is designed to take all traffic with a specific source IP address and forward the traffic to a traffic analysis server for further evaluation. The configuration is not working as intended. Referring to the exhibit, which change must be made to correct the configuration?
You are asked to look at a configuration that is designed to take all traffic with a specific source IP address and forward the traffic to a traffic analysis server for further evaluation. The configuration is not working as intended. Referring to the exhibit, which change must be made to correct the configuration?
A) Apply the filter as an input filter on interface xe-0/2/1.0
B) Create a routing instance named default
C) Apply the filter as an input filter on interface xe-0/0/1.0
D) Apply the filter as an output filter on interface xe-0/1/0.0
 You are asked to look at a configuration that is designed to take all traffic with a specific source IP address and forward the traffic to a traffic analysis server for further evaluation. The configuration is not working as intended. Referring to the exhibit, which change must be made to correct the configuration?
You are asked to look at a configuration that is designed to take all traffic with a specific source IP address and forward the traffic to a traffic analysis server for further evaluation. The configuration is not working as intended. Referring to the exhibit, which change must be made to correct the configuration?A) Apply the filter as an input filter on interface xe-0/2/1.0
B) Create a routing instance named default
C) Apply the filter as an input filter on interface xe-0/0/1.0
D) Apply the filter as an output filter on interface xe-0/1/0.0

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
46
You have configured three logical tunnel interfaces in a tenant system on an SRX1500 device. When committing the configuration, the commit fails. In this scenario, what would cause this problem?
A) There is no GRE tunnel between the tenant system and master system allowing SSH traffic
B) There is no VPLS switch on the tenant system containing a peer It-0/0/0 interface
C) The SRX1500 device does not support more than two logical interfaces per tenant system
D) The SRX1500 device requires a tunnel PIC to allow for logical tunnel interfaces
A) There is no GRE tunnel between the tenant system and master system allowing SSH traffic
B) There is no VPLS switch on the tenant system containing a peer It-0/0/0 interface
C) The SRX1500 device does not support more than two logical interfaces per tenant system
D) The SRX1500 device requires a tunnel PIC to allow for logical tunnel interfaces

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
47
Click the Exhibit button. 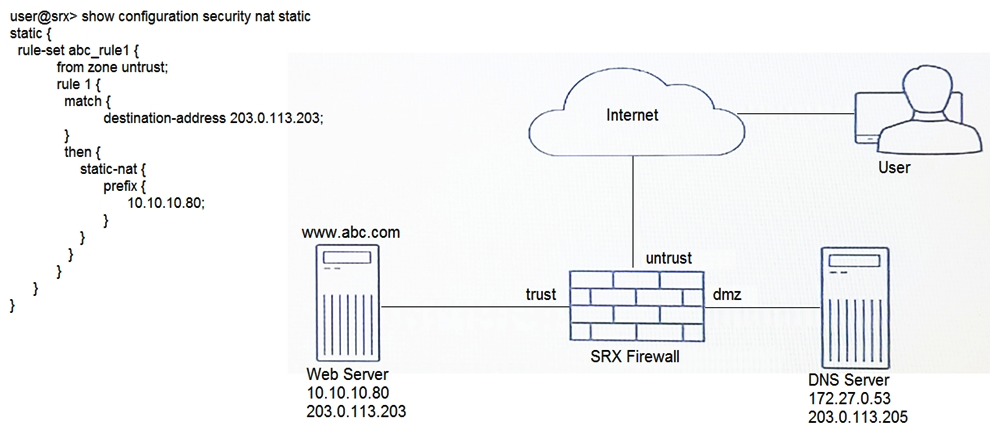 A user is trying to reach a company's website, but the connection errors out. The security policies are configured correctly. Referring to the exhibit, what is the problem?
A user is trying to reach a company's website, but the connection errors out. The security policies are configured correctly. Referring to the exhibit, what is the problem?
A) Persistent NAT must be enabled
B) The action for rule 1 must change to static-nat inet The action for rule 1 must change to static-nat inet
C) DNS ALG must be disabled
D) Static NAT is missing a rule for DNS server
 A user is trying to reach a company's website, but the connection errors out. The security policies are configured correctly. Referring to the exhibit, what is the problem?
A user is trying to reach a company's website, but the connection errors out. The security policies are configured correctly. Referring to the exhibit, what is the problem?A) Persistent NAT must be enabled
B) The action for rule 1 must change to static-nat inet The action for rule 1 must change to static-nat inet
C) DNS ALG must be disabled
D) Static NAT is missing a rule for DNS server

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
48
Click the Exhibit button. 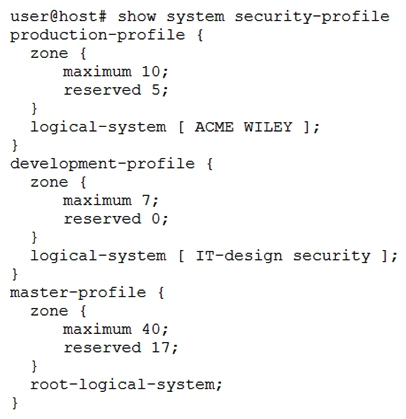 Referring to the exhibit, what is the maximum number of zones that are able to be created within all logical systems?
Referring to the exhibit, what is the maximum number of zones that are able to be created within all logical systems?
A) 74
B) 34
C) 40
D) 17
 Referring to the exhibit, what is the maximum number of zones that are able to be created within all logical systems?
Referring to the exhibit, what is the maximum number of zones that are able to be created within all logical systems?A) 74
B) 34
C) 40
D) 17

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
49
You are asked to configure an SRX Series device to bypass all security features for IP traffic from the engineering department. Which firewall filter will accomplish this task?
A)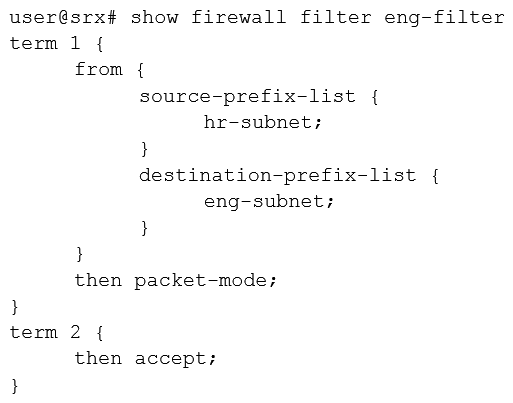
B)
C)
D)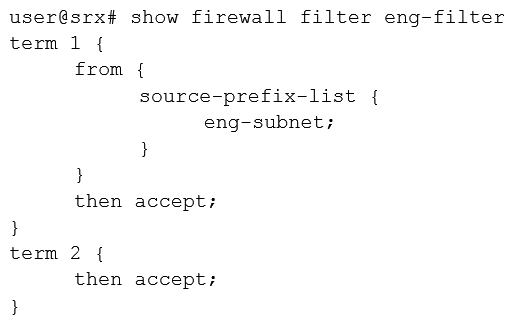
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
50
You are asked to configure a new SRX Series CPE device at a remote office. The device must participate in forwarding MPLS and IPsec traffic. Which two statements are true regarding this implementation? (Choose two.)
A) Host inbound traffic must not be processed by the flow module
B) Host inbound traffic must be processed by the flow module
C) The SRX Series device can process both MPLS and IPsec with default traffic handling
D) A firewall filter must be configured to enable packet mode forwarding
A) Host inbound traffic must not be processed by the flow module
B) Host inbound traffic must be processed by the flow module
C) The SRX Series device can process both MPLS and IPsec with default traffic handling
D) A firewall filter must be configured to enable packet mode forwarding

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
51
Click the Exhibit button.  Referring to the exhibit, which two statements are true? (Choose two.)
Referring to the exhibit, which two statements are true? (Choose two.)
A) You can secure intra-VLAN traffic with a security policy on this device
B) You can secure inter-VLAN traffic with a security policy on this device
C) The device can pass Layer 2 and Layer 3 traffic at the same time
D) The device cannot pass Layer 2 and Layer 3 traffic at the same time
 Referring to the exhibit, which two statements are true? (Choose two.)
Referring to the exhibit, which two statements are true? (Choose two.)A) You can secure intra-VLAN traffic with a security policy on this device
B) You can secure inter-VLAN traffic with a security policy on this device
C) The device can pass Layer 2 and Layer 3 traffic at the same time
D) The device cannot pass Layer 2 and Layer 3 traffic at the same time

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
52
Click the Exhibit button. ![<strong>Click the Exhibit button. You deployed a site-to-site IPsec VPN connecting two data centers together using SRX5800s. After examining the performance of the IPsec VPN, you decide to enable IPsec performance acceleration to increase the rate of traffic that can be sent through the tunnel. Referring to the exhibit, which two statements should you add to the configuration to accomplish this task? (Choose two.)</strong> A) [edit security flow] user@srx# set tcp-mss ipsec-vpn mss 65535 B) user@srx# set ipsec-performance-acceleration C) user@srx# set power-mode-ipsec D) user@srx# set load-distribution session-affinity ipsec](https://d2lvgg3v3hfg70.cloudfront.net/C1585/11ec5107_4634_f82e_b560_e1634b498d15_C1585_00.jpg) You deployed a site-to-site IPsec VPN connecting two data centers together using SRX5800s. After examining the performance of the IPsec VPN, you decide to enable IPsec performance acceleration to increase the rate of traffic that can be sent through the tunnel. Referring to the exhibit, which two statements should you add to the configuration to accomplish this task? (Choose two.)
You deployed a site-to-site IPsec VPN connecting two data centers together using SRX5800s. After examining the performance of the IPsec VPN, you decide to enable IPsec performance acceleration to increase the rate of traffic that can be sent through the tunnel. Referring to the exhibit, which two statements should you add to the configuration to accomplish this task? (Choose two.)
A) [edit security flow] user@srx# set tcp-mss ipsec-vpn mss 65535
B) user@srx# set ipsec-performance-acceleration
C) user@srx# set power-mode-ipsec
D) user@srx# set load-distribution session-affinity ipsec
![<strong>Click the Exhibit button. You deployed a site-to-site IPsec VPN connecting two data centers together using SRX5800s. After examining the performance of the IPsec VPN, you decide to enable IPsec performance acceleration to increase the rate of traffic that can be sent through the tunnel. Referring to the exhibit, which two statements should you add to the configuration to accomplish this task? (Choose two.)</strong> A) [edit security flow] user@srx# set tcp-mss ipsec-vpn mss 65535 B) user@srx# set ipsec-performance-acceleration C) user@srx# set power-mode-ipsec D) user@srx# set load-distribution session-affinity ipsec](https://d2lvgg3v3hfg70.cloudfront.net/C1585/11ec5107_4634_f82e_b560_e1634b498d15_C1585_00.jpg) You deployed a site-to-site IPsec VPN connecting two data centers together using SRX5800s. After examining the performance of the IPsec VPN, you decide to enable IPsec performance acceleration to increase the rate of traffic that can be sent through the tunnel. Referring to the exhibit, which two statements should you add to the configuration to accomplish this task? (Choose two.)
You deployed a site-to-site IPsec VPN connecting two data centers together using SRX5800s. After examining the performance of the IPsec VPN, you decide to enable IPsec performance acceleration to increase the rate of traffic that can be sent through the tunnel. Referring to the exhibit, which two statements should you add to the configuration to accomplish this task? (Choose two.)A) [edit security flow] user@srx# set tcp-mss ipsec-vpn mss 65535
B) user@srx# set ipsec-performance-acceleration
C) user@srx# set power-mode-ipsec
D) user@srx# set load-distribution session-affinity ipsec

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
53
Which three roles or protocols are required when configuring an ADVPN? (Choose three.)
A) OSPF
B) shortcut partner
C) shortcut suggester
D) IKEv1
E) BGP
A) OSPF
B) shortcut partner
C) shortcut suggester
D) IKEv1
E) BGP

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
54
You are asked to merge to corporate network with the network from a recently acquired company. Both networks use the same private IPv4 address space (172.25.126.0/24). An SRX Series device servers as the gateway for each network. Which solution allows you to merge the two networks without modifying the current address assignments?
A) persistent NAT
B) NAT46
C) source NAT
D) double NAT
A) persistent NAT
B) NAT46
C) source NAT
D) double NAT

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
55
Which feature of Sky ATP is deployed with Policy Enforcer?
A) zero-day threat mitigation
B) software image snapshot support
C) device inventory management
D) service redundancy daemon configuration support
A) zero-day threat mitigation
B) software image snapshot support
C) device inventory management
D) service redundancy daemon configuration support

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
56
When would you use the port-overloading-factor 1 setting?
A) to enable the port-overloading
B) to disable the port-overloading
C) to map ports with 1:1 ratio for port-overloading
D) to set the maximum port-overloading capacity to 65,536
A) to enable the port-overloading
B) to disable the port-overloading
C) to map ports with 1:1 ratio for port-overloading
D) to set the maximum port-overloading capacity to 65,536

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
57
Click the Exhibit button. 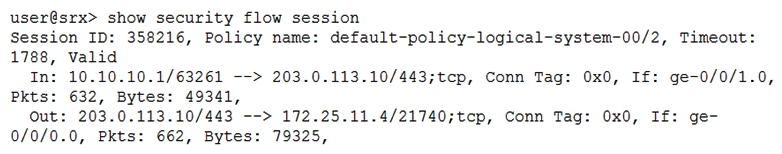 Referring to the exhibit, which statement is true?
Referring to the exhibit, which statement is true?
A) Source NAT with PAT is occurring
B) Destination NAT is occurring
C) Static NAT without PAT is occurring
D) Source NAT without PAT is occurring
 Referring to the exhibit, which statement is true?
Referring to the exhibit, which statement is true?A) Source NAT with PAT is occurring
B) Destination NAT is occurring
C) Static NAT without PAT is occurring
D) Source NAT without PAT is occurring

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
58
You are asked to implement the session cache feature on an SRX5400. In this scenario, what information does a session cache entry record? (Choose two.)
A) The type of processing to do for ingress traffic
B) The type of processing to do for egress traffic
C) To which SPU the traffic of the session should be forwarded
D) To which NPU the traffic of the session should be forwarded
A) The type of processing to do for ingress traffic
B) The type of processing to do for egress traffic
C) To which SPU the traffic of the session should be forwarded
D) To which NPU the traffic of the session should be forwarded

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
59
You are asked to configure an IPsec VPN between two SRX Series devices that allows for processing of CoS on the intermediate routers. What will satisfy this requirement?
A) route-based VPN
B) OpenVPN
C) remote access VPN
D) policy-based VPN
A) route-based VPN
B) OpenVPN
C) remote access VPN
D) policy-based VPN

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
60
You must troubleshoot ongoing problems with IPsec tunnels and security policy processing. Your network consists of SRX340s and SRX5600s. In this scenario, which two statements are true? (Choose two.)
A) IPsec logs are written to the kmd log file by default
B) IKE logs are written to the messages log file by default
C) You must enable data plane logging on the SRX340 devices to generate security policy logs
D) You must enable data plane logging on the SRX5600 devices to generate security policy logs
A) IPsec logs are written to the kmd log file by default
B) IKE logs are written to the messages log file by default
C) You must enable data plane logging on the SRX340 devices to generate security policy logs
D) You must enable data plane logging on the SRX5600 devices to generate security policy logs

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
61
A user is unable to reach a necessary resource. You discover the path through the SRX Series device includes several security features. The traffic is not being evaluated by any security policies. In this scenario, which two components within the flow module would affect the traffic? (Choose two.)
A) services/ALG
B) destination NAT
C) source NAT
D) route lookup
A) services/ALG
B) destination NAT
C) source NAT
D) route lookup

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
62
Click the Exhibit button. ![<strong>Click the Exhibit button. You have configured an ADVPN that is operational. However, OSPF will not establish correctly across the ADVPN tunnels. Referring to the exhibit, which two commands will solve the problem? (Choose two.)</strong> A) [edit protocols ospf area 0.0.0.0] user@srx# set interface st0.0 dynamic-neighbors B) user@srx# set interface st0.0 topology advpn C) user@srx# set interface st0.0 interface-type nbma D) user@srx# set interface st0.0 demand-circuit](https://d2lvgg3v3hfg70.cloudfront.net/C1585/11ec5107_4635_e29c_b560_6322c64116e8_C1585_00.jpg) You have configured an ADVPN that is operational. However, OSPF will not establish correctly across the ADVPN tunnels. Referring to the exhibit, which two commands will solve the problem? (Choose two.)
You have configured an ADVPN that is operational. However, OSPF will not establish correctly across the ADVPN tunnels. Referring to the exhibit, which two commands will solve the problem? (Choose two.)
A) [edit protocols ospf area 0.0.0.0] user@srx# set interface st0.0 dynamic-neighbors
B) user@srx# set interface st0.0 topology advpn
C) user@srx# set interface st0.0 interface-type nbma
D) user@srx# set interface st0.0 demand-circuit
![<strong>Click the Exhibit button. You have configured an ADVPN that is operational. However, OSPF will not establish correctly across the ADVPN tunnels. Referring to the exhibit, which two commands will solve the problem? (Choose two.)</strong> A) [edit protocols ospf area 0.0.0.0] user@srx# set interface st0.0 dynamic-neighbors B) user@srx# set interface st0.0 topology advpn C) user@srx# set interface st0.0 interface-type nbma D) user@srx# set interface st0.0 demand-circuit](https://d2lvgg3v3hfg70.cloudfront.net/C1585/11ec5107_4635_e29c_b560_6322c64116e8_C1585_00.jpg) You have configured an ADVPN that is operational. However, OSPF will not establish correctly across the ADVPN tunnels. Referring to the exhibit, which two commands will solve the problem? (Choose two.)
You have configured an ADVPN that is operational. However, OSPF will not establish correctly across the ADVPN tunnels. Referring to the exhibit, which two commands will solve the problem? (Choose two.)A) [edit protocols ospf area 0.0.0.0] user@srx# set interface st0.0 dynamic-neighbors
B) user@srx# set interface st0.0 topology advpn
C) user@srx# set interface st0.0 interface-type nbma
D) user@srx# set interface st0.0 demand-circuit

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
63
Which two VPN features are supported with CoS-based IPsec VPNs? (Choose two.)
A) IKEv2
B) VPN monitoring
C) dead peer detection
D) IKEv1
A) IKEv2
B) VPN monitoring
C) dead peer detection
D) IKEv1

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
64
You have a remote access VPN where the remote users are using the NCP client. The remote users can access the internal corporate resources as intended; however, traffic that is destined to all other Internet sites is going through the remote access VPN. You want to ensure that only traffic that is destined to the internal corporate resources use the remote access VPN. Which two actions should you take to accomplish this task? (Choose two.)
A) Enable the split tunneling feature within the VPN configuration on the SRX Series device
B) Enable IKEv2 within the VPN configuration on the SRX Series device
C) Configure the necessary traffic selectors within the VPN configuration on the SRX Series device
D) Configure split tunneling on the NCP profile on the remote client
A) Enable the split tunneling feature within the VPN configuration on the SRX Series device
B) Enable IKEv2 within the VPN configuration on the SRX Series device
C) Configure the necessary traffic selectors within the VPN configuration on the SRX Series device
D) Configure split tunneling on the NCP profile on the remote client

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
65
You configured a security policy permitting traffic from the trust zone to the DMZ zone, inserted the new policy at the top of the list, and successfully committed it to the SRX Series device. Upon monitoring, you notice that the hit count does not increase on the newly configured policy. In this scenario, which two commands would help you to identify the problem? (Choose two.)
A) user@srx> show security zones trust detail
B) user@srx> show security shadow-policies from zone trust to zone DMZ
C) user@srx> show security match-policies from-zone trust to-zone DMZ source-ip 192.168.10.100/32 destination-ip 10.10.10.80/32 protocol tcp source-port 5806 destination-port 443
D) destination-ip 10.10.10.80/32 protocol tcp source-port 5806 destination-port 443 result-count 10
A) user@srx> show security zones trust detail
B) user@srx> show security shadow-policies from zone trust to zone DMZ
C) user@srx> show security match-policies from-zone trust to-zone DMZ source-ip 192.168.10.100/32 destination-ip 10.10.10.80/32 protocol tcp source-port 5806 destination-port 443
D) destination-ip 10.10.10.80/32 protocol tcp source-port 5806 destination-port 443 result-count 10

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
66
Click the Exhibit button. 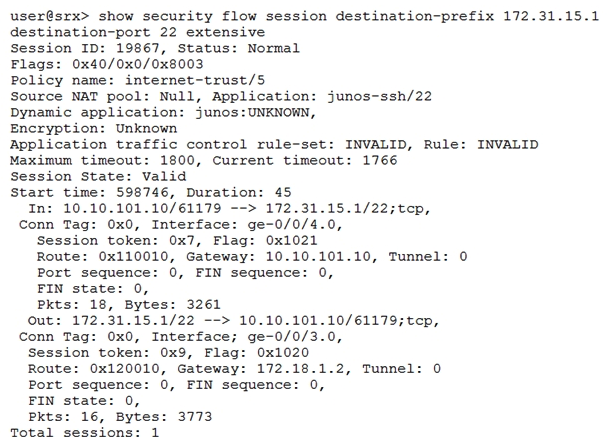 Given the command output shown in the exhibit, which two statements are true? (Choose two.)
Given the command output shown in the exhibit, which two statements are true? (Choose two.)
A) The host 172.31.15.1 is directly connected to interface ge-0/0/3.0
B) Traffic matching this session has been received since the session was established
C) The host 10.10.101.10 is directly connected to interface ge-0/0/4.0
D) Network Address Translation is applied to this session
 Given the command output shown in the exhibit, which two statements are true? (Choose two.)
Given the command output shown in the exhibit, which two statements are true? (Choose two.)A) The host 172.31.15.1 is directly connected to interface ge-0/0/3.0
B) Traffic matching this session has been received since the session was established
C) The host 10.10.101.10 is directly connected to interface ge-0/0/4.0
D) Network Address Translation is applied to this session

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
67
Click the Exhibit button. 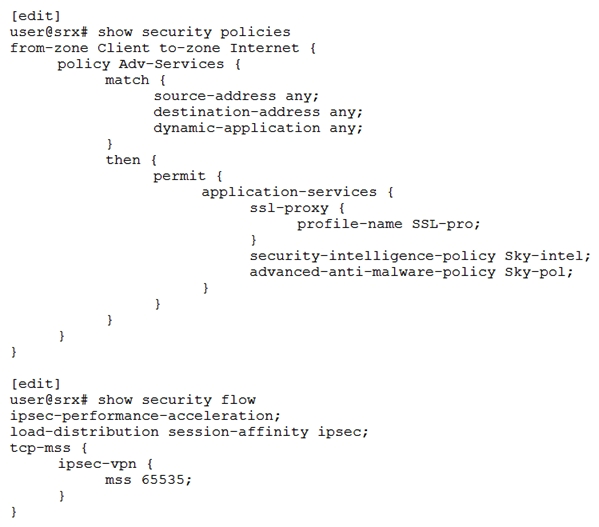 Referring to the exhibit, you are attempting to enable IPsec power mode to improve IPsec VPN performance. However, you are unable to use IPsec power mode. What is the problem?
Referring to the exhibit, you are attempting to enable IPsec power mode to improve IPsec VPN performance. However, you are unable to use IPsec power mode. What is the problem?
A) IPsec power mode cannot be used with IPsec performance acceleration
B) IPsec power mode cannot be used with high IPsec maximum segment size values
C) IPsec power mode cannot be used with advanced services
D) IPsec power mode requires that you configure a policy-based VPN
 Referring to the exhibit, you are attempting to enable IPsec power mode to improve IPsec VPN performance. However, you are unable to use IPsec power mode. What is the problem?
Referring to the exhibit, you are attempting to enable IPsec power mode to improve IPsec VPN performance. However, you are unable to use IPsec power mode. What is the problem?A) IPsec power mode cannot be used with IPsec performance acceleration
B) IPsec power mode cannot be used with high IPsec maximum segment size values
C) IPsec power mode cannot be used with advanced services
D) IPsec power mode requires that you configure a policy-based VPN

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
68
You are configuring transparent mode on an SRX Series device. You must permit IP-based traffic only, and BPDUs must be restricted to the VLANs from which they originate. Which configuration accomplishes these objectives?
A)
B)
C)
D)
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
69
Which two statements are true about ADVPN members? (Choose two.)
A) ADVPN members are authenticated using pre-shared keys
B) ADVPN members are authenticated using certificates
C) ADVPN members can use IKEv2
D) ADVPN members can use IKEv1
A) ADVPN members are authenticated using pre-shared keys
B) ADVPN members are authenticated using certificates
C) ADVPN members can use IKEv2
D) ADVPN members can use IKEv1

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
70
Which two modes are supported on Juniper Sky ATP? (Choose two.)
A) private mode
B) global mode
C) tap mode
D) secure wire mode
A) private mode
B) global mode
C) tap mode
D) secure wire mode

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
71
Your SRX Series device does not see the SYN packet. What is the default action in this scenario?
A) The device will forward the subsequent packets and the session will be established
B) The device will forward the subsequent packets and the session will not be established
C) The device will drop the subsequent packets and the session will not be established
D) The device will drop the subsequent packets and the session will be established
A) The device will forward the subsequent packets and the session will be established
B) The device will forward the subsequent packets and the session will not be established
C) The device will drop the subsequent packets and the session will not be established
D) The device will drop the subsequent packets and the session will be established

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
72
Click the Exhibit button. 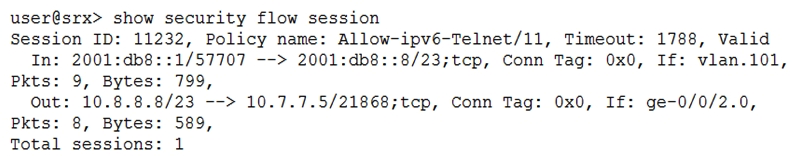 Which type of NAT is shown in the exhibit?
Which type of NAT is shown in the exhibit?
A) NAT46
B) NAT64
C) persistent NAT
D) DS-Lite
 Which type of NAT is shown in the exhibit?
Which type of NAT is shown in the exhibit?A) NAT46
B) NAT64
C) persistent NAT
D) DS-Lite

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
73
How does secure wire mode differ from transparent mode?
A) In secure wire mode, no switching lookup takes place to forward traffic
B) In secure wire mode, traffic can be modified using source NAT
C) In secure wire mode, IRB interfaces can be configured to route inter-VLAN traffic
D) In secure wire mode, security policies cannot be used to secure intra-VLAN traffic
A) In secure wire mode, no switching lookup takes place to forward traffic
B) In secure wire mode, traffic can be modified using source NAT
C) In secure wire mode, IRB interfaces can be configured to route inter-VLAN traffic
D) In secure wire mode, security policies cannot be used to secure intra-VLAN traffic

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
74
Click the Exhibit button. 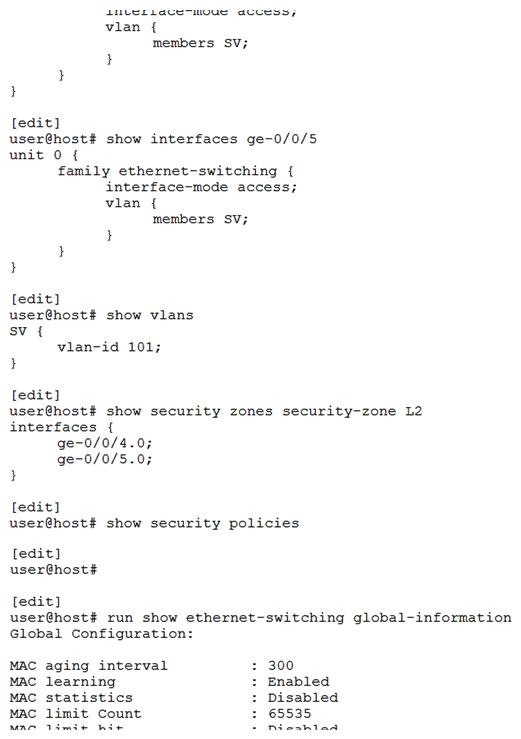 You have two hosts on the same subnet connecting to an SRX340 on interfaces ge-0/0/4 and ge-0/0/5. However, the two hosts cannot communicate with each other. Referring to the exhibit, what are two actions that would solve this problem? (Choose two.)
You have two hosts on the same subnet connecting to an SRX340 on interfaces ge-0/0/4 and ge-0/0/5. However, the two hosts cannot communicate with each other. Referring to the exhibit, what are two actions that would solve this problem? (Choose two.)
A) Set the SRX340 to Ethernet switching mode and reboot
B) Add an IRB interface to the VLAN
C) Put the ge-0/0/4 and ge-0/0/5 interfaces in different VLANs
D) Remove the ge-0/0/4 and ge-0/0/5 interfaces from the L2 security zone
 You have two hosts on the same subnet connecting to an SRX340 on interfaces ge-0/0/4 and ge-0/0/5. However, the two hosts cannot communicate with each other. Referring to the exhibit, what are two actions that would solve this problem? (Choose two.)
You have two hosts on the same subnet connecting to an SRX340 on interfaces ge-0/0/4 and ge-0/0/5. However, the two hosts cannot communicate with each other. Referring to the exhibit, what are two actions that would solve this problem? (Choose two.)A) Set the SRX340 to Ethernet switching mode and reboot
B) Add an IRB interface to the VLAN
C) Put the ge-0/0/4 and ge-0/0/5 interfaces in different VLANs
D) Remove the ge-0/0/4 and ge-0/0/5 interfaces from the L2 security zone

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
75
In which two ways are tenant systems different from logical systems? (Choose two.)
A) Tenant systems have higher scalability than logical systems
B) Tenant systems have less scalability than logical systems
C) Tenant systems have fewer routing features than logical systems
D) Tenant systems have more routing features than logical systems
A) Tenant systems have higher scalability than logical systems
B) Tenant systems have less scalability than logical systems
C) Tenant systems have fewer routing features than logical systems
D) Tenant systems have more routing features than logical systems

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
76
Click the Exhibit button. 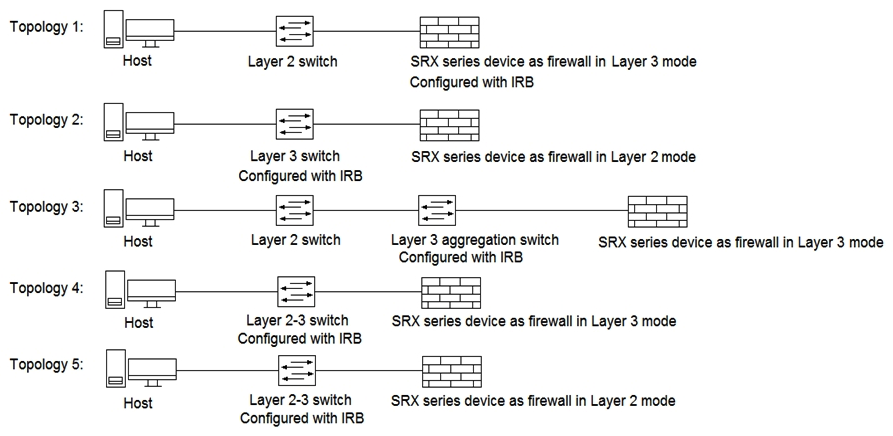 Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)
Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)
A) Topology 3
B) Topology 5
C) Topology 2
D) Topology 4
E) Topology 1
 Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)
Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)A) Topology 3
B) Topology 5
C) Topology 2
D) Topology 4
E) Topology 1

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
77
Click the Exhibit button. 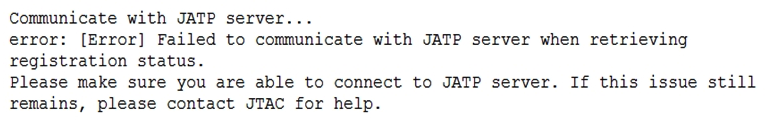 When attempting to enroll an SRX Series device to JATP, you receive the error shown in the exhibit. What is the cause of the error?
When attempting to enroll an SRX Series device to JATP, you receive the error shown in the exhibit. What is the cause of the error?
A) The fxp0 IP address is not routable
B) The SRX Series device certificate does not match the JATP certificate
C) The SRX Series device does not have an IP address assigned to the interface that accesses JATP
D) A firewall is blocking HTTPS on fxp0
 When attempting to enroll an SRX Series device to JATP, you receive the error shown in the exhibit. What is the cause of the error?
When attempting to enroll an SRX Series device to JATP, you receive the error shown in the exhibit. What is the cause of the error?A) The fxp0 IP address is not routable
B) The SRX Series device certificate does not match the JATP certificate
C) The SRX Series device does not have an IP address assigned to the interface that accesses JATP
D) A firewall is blocking HTTPS on fxp0

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck
78
Click the Exhibit button.  Referring to the exhibit, which IPS deployment mode is running on the SRX5800 device?
Referring to the exhibit, which IPS deployment mode is running on the SRX5800 device?
A) sniffer mode
B) integrated mode
C) monitor mode
D) in-line tap mode
 Referring to the exhibit, which IPS deployment mode is running on the SRX5800 device?
Referring to the exhibit, which IPS deployment mode is running on the SRX5800 device?A) sniffer mode
B) integrated mode
C) monitor mode
D) in-line tap mode

Unlock Deck
Unlock for access to all 78 flashcards in this deck.
Unlock Deck
k this deck



