Deck 7: Procedures for Responding to Attacks on Computers
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Match between columns
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/65
Play
Full screen (f)
Deck 7: Procedures for Responding to Attacks on Computers
1
The FBI defines Cyberterrorism as a violent act that intimidates a government and its citizens.
False
2
Application-layer attacks often use ports that are allowed through a firewall.
True
3
The CERT Coordination Center provides professional information and security awareness services to defense contractors, governments, and industrial security executives.
False
4
RAID also uses a technique called parity to determine whether data has been lost or over-written.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
5
Managing external threats is much easier than managing the risks from inside the organization.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
6
Threats, such as industrial espionage or a malicious act toward a senior staff member, are deliberate .

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
7
Securing a system against intrusion is an immense and difficult task.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
8
The most expensive code attack was the Code Red virus at $8.75 billion.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
9
The explosive growth of networks and Internet connections gives attackers almost limitless opportunities to probe until they find a network with a security flaw they can exploit.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
10
Theft of proprietary information was the source of the most serious financial loss in companies surveyed.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
11
Small systems consist of file servers, applications servers, workstation servers, Web servers, and mainframes.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
12
In the information warfare model, victims are classified as individuals, corporations, or countries .

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
13
If an organization detects and confirms a breach in system security, its next step should be to collect as much information as it can about the intrusion.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
14
Until recently, the Organization for Cooperation and Development has been at the forefront of addressing privacy issues .

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
15
When people or groups use computer technology, software, and networks to attack systems, they launch a malicious code attack .

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
16
The striping technique saves data simultaneously to separate hard drives or drive arrays.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
17
Most disasters result from natural causes.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
18
Most organizations have insurance that covers damage produced by major privacy violations.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
19
Securing systems against direct or indirect attack requires dividing internal and external threats into cohesive and manageable elements early in the business analysis.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
20
An internal threat would originate from any employee who has physical access to equipment and legitimate rights to information within the organization.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
21
The ____ Web site provides data on the hidden cost of downtime from a variety of articles, research reports, and consulting firms.
A)Downtime Central
B)Creative Data Concepts Ltd.
C)Computer Security Products Inc.
D)SANS Institute
A)Downtime Central
B)Creative Data Concepts Ltd.
C)Computer Security Products Inc.
D)SANS Institute

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
22
The ____ Web site provides information on the cost of downtime.
A)SANS Institute
B)Alternative Power Systems
C)Network Security Center
D)Downtime Central
A)SANS Institute
B)Alternative Power Systems
C)Network Security Center
D)Downtime Central

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
23
The ____ Web site provides information that can serve as an introduction to disaster recovery planning.
A)Alternative Power Systems
B)Computer Security Products Inc.
C)DHS
D)FEMA
A)Alternative Power Systems
B)Computer Security Products Inc.
C)DHS
D)FEMA

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
24
Which of the following are all important parts of comprehensive IT security policies and procedures?
A)Access controls
B)Physical security of sensitive systems
C)System audits
D)All of the above
A)Access controls
B)Physical security of sensitive systems
C)System audits
D)All of the above

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
25
____ attacks focus on making a service unavailable for normal use, typically by exhausting some resource within a network, operating system, or application.
A)Application-layer
B)Denial-of-service (DoS)
C)TCP SYN flood
D)IP-spoofing
A)Application-layer
B)Denial-of-service (DoS)
C)TCP SYN flood
D)IP-spoofing

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
26
Which legislation requires financial institutions to disclose their privacy policies to customers?
A)The Gramm-Leach-Bliley Act of 1999
B)Children's Online Privacy Protection Act of 1998
C)Telecommunications Act of 1996
D)Privacy Act of 1974
A)The Gramm-Leach-Bliley Act of 1999
B)Children's Online Privacy Protection Act of 1998
C)Telecommunications Act of 1996
D)Privacy Act of 1974

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
27
What type of threat could originate from any employee who has physical access to equipment and legitimate rights to information within the organization?
A)Internal
B)External
C)Direct
D)Indirect
E)a, c, and d
A)Internal
B)External
C)Direct
D)Indirect
E)a, c, and d

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
28
____ attacks can occur during the client-server "handshake", a sequence of messages required when a client attempts to establish a TCP connection to a server.
A)Denial-of-service (DoS)
B)Ping of death
C)TCP SYN flood
D)Stacheldraht
A)Denial-of-service (DoS)
B)Ping of death
C)TCP SYN flood
D)Stacheldraht

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
29
In the Computer Crime and Security Survey 2002, what was the most frequent point of attack?
A)Denial-of-service
B)Inappropriate e-mail
C)Internet connections
D)Internal attacks
A)Denial-of-service
B)Inappropriate e-mail
C)Internet connections
D)Internal attacks

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
30
Which legislation requires Web site operators and online service providers to obtain parental consent to collect a child's personal information, and requires sites that collect information from children to disclose how they plan to use the data?
A)The Homeland Security Act of 2002
B)Children's Online Privacy Protection Act of 1998
C)The Electronic Communications Privacy Act of 1986
D)Privacy Act of 1974
A)The Homeland Security Act of 2002
B)Children's Online Privacy Protection Act of 1998
C)The Electronic Communications Privacy Act of 1986
D)Privacy Act of 1974

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
31
Which act authorizes sharing of the federal government information-gathering efforts with relevant foreign, state, and local officials?
A)The Electronic Communications Privacy Act of 1986
B)The USA PATRIOT Act of 2001
C)The Gramm-Leach-Bliley Act of 1999
D)The Homeland Security Act of 2002
A)The Electronic Communications Privacy Act of 1986
B)The USA PATRIOT Act of 2001
C)The Gramm-Leach-Bliley Act of 1999
D)The Homeland Security Act of 2002

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
32
Which legislation limits the use and disclosure of customer proprietary network information (CPNI)by telecommunications service providers?
A)Electronic Communications Privacy Act of 1986
B)Communications Policy Act of 1984
C)Telecommunications Act of 1996
D)Video Privacy Protection Act of 1988
A)Electronic Communications Privacy Act of 1986
B)Communications Policy Act of 1984
C)Telecommunications Act of 1996
D)Video Privacy Protection Act of 1988

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
33
____ attacks occur when a hacker inside or outside a network pretends to be a trusted computer.
A)Ping of death
B)IP-spoofing
C)Man-in-the-middle
D)Trojan horse
A)Ping of death
B)IP-spoofing
C)Man-in-the-middle
D)Trojan horse

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
34
____ are programs that allow intruders to scan hundreds of thousands of systems quite quickly.
A)Application-layer attack
B)Autorooters
C)TCP SYN flood
D)Packet sniffers
A)Application-layer attack
B)Autorooters
C)TCP SYN flood
D)Packet sniffers

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
35
Which act was implemented to protect the privacy of people identified in information systems maintained by federal executive branch agencies, and to control the collection, use, and sharing of information?
A)Privacy Act of 1974
B)Telecommunications Act of 1996
C)The Gramm-Leach-Bliley Act of 1999
D)The Electronic Communications Privacy Act of 1986
A)Privacy Act of 1974
B)Telecommunications Act of 1996
C)The Gramm-Leach-Bliley Act of 1999
D)The Electronic Communications Privacy Act of 1986

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
36
With ____ attacks, an intruder takes control of many systems to launch an attack.
A)application-layer
B)TCP SYN flood
C)denial-of-service
D)IP-spoofing
A)application-layer
B)TCP SYN flood
C)denial-of-service
D)IP-spoofing

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
37
In the information warfare model, which of the following is a classification of victim?
A)Personal
B)Country
C)Business
D)Individual
A)Personal
B)Country
C)Business
D)Individual

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
38
____ combines features of several DoS attacks, including TFN.
A)Man-in-the-middle
B)Stacheldraht
C)Trojan horse
D)Trust exploitation
A)Man-in-the-middle
B)Stacheldraht
C)Trojan horse
D)Trust exploitation

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
39
The ____ Web site provides information for protecting computer systems and handling computer security incidents.
A)FEMA
B)NSA
C)CERT Coordination Center
D)FBI
A)FEMA
B)NSA
C)CERT Coordination Center
D)FBI

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
40
The ____ Web site provides training and useful resources.
A)Cisco Systems Inc.
B)Microsoft Corporation
C)SANS Institute
D)FEMA
A)Cisco Systems Inc.
B)Microsoft Corporation
C)SANS Institute
D)FEMA

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
41
One popular model for categorizing threats separates information warfare into three categories. What are they?

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
42
____ attacks are repeated attempts to identify a user account and password.
A)Backdoors
B)Trust exploitation
C)Password attacks
D)Trojan horse
A)Backdoors
B)Trust exploitation
C)Password attacks
D)Trojan horse

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
43
What type of negative economic impact from computer attacks might include damage to systems, the direct costs of repairing or replacing systems, and disrupted business and revenues?
A)Immediate
B)Mid-term
C)Short-term
D)Long-term
A)Immediate
B)Mid-term
C)Short-term
D)Long-term

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
44
What steps can organizations take to cooperate with the DHS cyberspace strategy? (List 5)

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
45
____ attacks refer to malicious software that is attached to another program to execute an unwanted function on a user workstation.
A)Trojan horse
B)Backdoors
C)IP-spoofing
D)Application-layer
A)Trojan horse
B)Backdoors
C)IP-spoofing
D)Application-layer

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
46
What should organizations consider when developing procedures to deal with information warfare threats and damages? (List all 5)

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
47
How many FBI field offices have established an InfraGard chapter?
A)52
B)54
C)56
D)58
A)52
B)54
C)56
D)58

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
48
To protect against cyberattacks and create an appropriate defense plan, organizations need a combination of what 4 things?

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
49
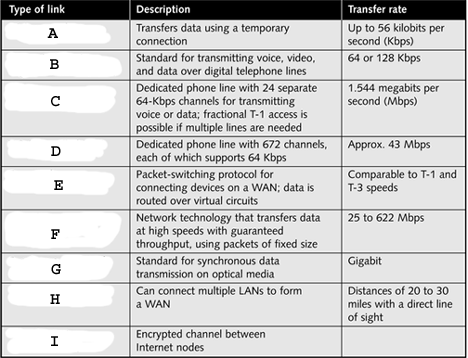 " style="vertical-align: 0px;" width="468px" height="358px In the table above, what does B represent?
" style="vertical-align: 0px;" width="468px" height="358px In the table above, what does B represent?A)Dial-up modem
B)ISDN
C)Frame relay
D)ATM

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
50
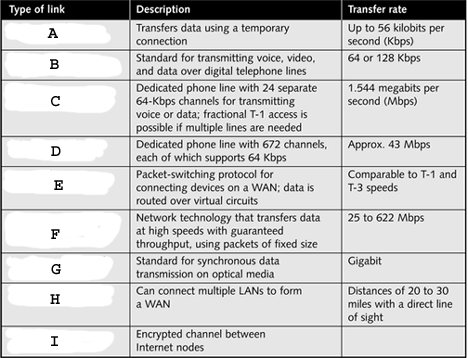 " style="vertical-align: 0px;" width="468px" height="358px In the table above, what does F represent?
" style="vertical-align: 0px;" width="468px" height="358px In the table above, what does F represent?A)Frame relay
B)T-3
C)SONET
D)ATM

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
51
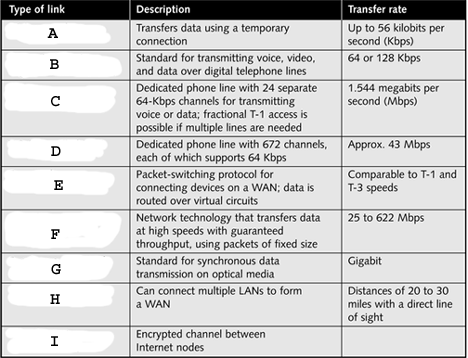 " style="vertical-align: 0px;" width="468px" height="358px In the table above, what does H represent?
" style="vertical-align: 0px;" width="468px" height="358px In the table above, what does H represent?A)T-1
B)Frame relay
C)Wireless LAN bridge
D)VPN

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
52
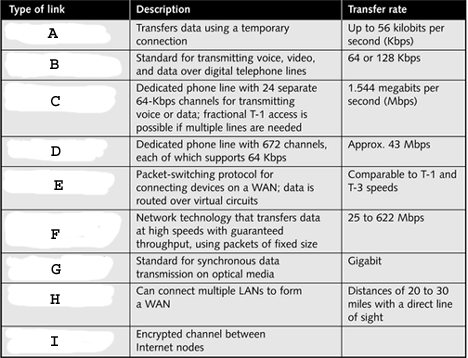 " style="vertical-align: 0px;" width="468px" height="358px In the table above, what does E represent?
" style="vertical-align: 0px;" width="468px" height="358px In the table above, what does E represent?A)T-1
B)T-3
C)ATM
D)Frame relay

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
53
The national InfraGard program provides what 4 basic services to members?

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
54
What type of negative economic impact from computer attacks might include lost contracts, sales, or customers, a tarnished reputation, and problems in developing new business?
A)Immediate
B)Short-term
C)Long-term
D)Mid-term
A)Immediate
B)Short-term
C)Long-term
D)Mid-term

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
55
Which of the following are procedures to follow after a computer attack?
A)Prepare for law enforcement to enter the facility
B)Review system logs for clues about the attackers point of entry
C)Recommend security upgrades or changes
D)All of the above
A)Prepare for law enforcement to enter the facility
B)Review system logs for clues about the attackers point of entry
C)Recommend security upgrades or changes
D)All of the above

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
56
____ are software applications that use a network adapter card in "promiscuous" mode.
A)Trojan horses
B)Application-layer attacks
C)Autorooters
D)Packet sniffers
A)Trojan horses
B)Application-layer attacks
C)Autorooters
D)Packet sniffers

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
57
____ are a type of trust exploitation attack that uses a compromised host to pass traffic through a firewall that would otherwise be dropped.
A)Password
B)IP-spoofing
C)Man-in-the-middle
D)Port redirection
A)Password
B)IP-spoofing
C)Man-in-the-middle
D)Port redirection

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
58
The National Strategy for the Physical Protection of Critical Infrastructures and Key Assets document calls for cooperation among government, industry ,and private citizens to protect which key assets? (List 5)

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
59
What type of negative economic impact from computer attacks might include reduced market valuation, stock prices, investor confidence, and goodwill toward the organization?
A)Immediate
B)Short-term
C)Mid-term
D)Long-term
A)Immediate
B)Short-term
C)Mid-term
D)Long-term

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
60
____ attacks can occur when a hacker has access to packets that come across a network.
A)Trojan horse
B)Man-in-the-middle
C)Port redirection
D)Trust exploitation
A)Trojan horse
B)Man-in-the-middle
C)Port redirection
D)Trust exploitation

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
61
List each of the systems and networks in an organization that require recovery.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
62
Match between columns

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
63
The adverse impact of a hacking attack or intrusion can also be described in terms of what three types of losses?

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
64
List and describe the negative economic effects an organization could endure as a result of computer attacks or intrusions.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
65
What should organizations do to help recover small systems after a computer attack?

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck



