Deck 1: Introduction to the World of Computers
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/100
Play
Full screen (f)
Deck 1: Introduction to the World of Computers
1
Satellite communication (more commonly called s-com) is the process of exchanging electronic messages between computers over a network-usually the Internet.
False
2
Once you have an Internet connection, you are ready to begin programming the Web-that is, using a Web browser to view Web pages.
False
3
Just as you can learn to drive a car without knowing much about car engines, you can learn to use a computer without understanding the technical details of how a computer works.
True
4
To begin to use a computer, the user first turns on the power by pressing the power button, and then the computer displays a prompt for the user to decide the next course of action.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
5
The slide rule is considered by many to be the earliest recorded calculating device.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
6
 The accompanying figure shows a notebook computer.
The accompanying figure shows a notebook computer.
Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
7
Fourth-generation computers witnessed the development of computer networks, wireless technologies, and the Internet.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
8
Tablet PCs can use either a slate or a convertible tablet PC design.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
9
Systems analysts design computer systems to be used within their companies.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
10
In addition to hardware, software, data, and procedures, the fifth major component of a computer system are codes.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
11
Notebook computers (also called laptops) are fully functioning computers that open to reveal a screen and keyboard.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
12
Storage devices are hardware used to store data on or access data from storage media, such as CD discs, DVD discs, or flash memory cards.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
13
Web browsers maintain a History list, which is a record of all Web pages visited during the period of time specified in the browser settings.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
14
A mainframe computer is the standard choice for large organizations that need to manage large amounts of centralized data.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
15
Computer literacy is knowing about and understanding computers and their uses.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
16
Small office networks enable workers to access company records stored on a network server.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
17
There are application programs that help users write their own programs using a programming language.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
18
A computer does not always do whatever the instructions, or program, tell it to do.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
19
The external hardware components are located inside the main box or system unit of the computer.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
20
Information processing is a vital activity today because the success of many businesses depends heavily on the wise use of information.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
21
Dr. Herman Hollerith's Punch Card Tabulating Machine and Sorter was the first electromechanical machine that could read slide rules .

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
22
Computer programmers are the people who use a computer to obtain information.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
23
 As shown in the accompanying figure, the computer is used extensively for access control at many organizations, such as ____ that allow individuals to enter the office building, punch in or out of work, or access the company network by providing the proper credentials or being authenticated via a fingerprint or hand scan.
As shown in the accompanying figure, the computer is used extensively for access control at many organizations, such as ____ that allow individuals to enter the office building, punch in or out of work, or access the company network by providing the proper credentials or being authenticated via a fingerprint or hand scan.A) bar codes
B) virtual reality glasses
C) collaboration systems
D) authentication systems

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
24
Fourth-generation computers typically use a keyboard and mouse for input, a monitor and printer for output, and hard drives, flash memory media, and optical discs for storage.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
25
A user inputs data into a computer, and then the computer processes it.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
26
In the early 1980s, things began to change. ____ were invented and computer use increased dramatically.
A) Printers
B) Networks
C) Microcomputers
D) Computers
A) Printers
B) Networks
C) Microcomputers
D) Computers

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
27
Multiple computing typically refers to accessing Web-based applications and data using a personal computer, mobile phone, or any other Internet-enabled device.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
28
Abbreviations or acronyms, such as BTW for " between the words ," are commonly used to save time in all types of communications today.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
29
In cloud worlds, online users can explore anonymously.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
30
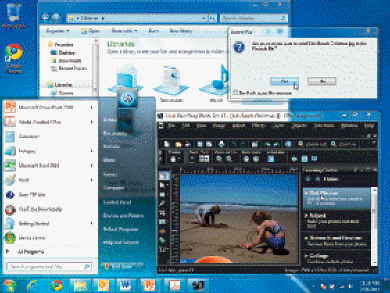 The Start button is used to open the Start menu -shown in the accompanying figure-which is used to launch programs.
The Start button is used to open the Start menu -shown in the accompanying figure-which is used to launch programs.
Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
31
A(n) display screen can be defined as a programmable, electronic device that accepts data, performs operations on that data, presents the results, and can store the data or results as needed.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
32
Fifty years ago, computers were used primarily by researchers and ____.
A) musicians
B) scientists
C) writers
D) designers
A) musicians
B) scientists
C) writers
D) designers

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
33
An e-mail address consists of a(n) username , followed by the @ symbol, followed by the domain name for the computer that will be handling that person's e-mail (called a mail server).

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
34
Wireless networking allows the use of computers in virtually any location.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
35
Communications hardware includes modems, which are used to connect a computer to the Internet and network projectors , which are used to connect a computer to a computer network.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
36
Computing technologies make it possible to have ____, traditional appliances with some type of built-in computer or communications technology.
A) design appliances
B) smart computers
C) home computers
D) smart appliances
A) design appliances
B) smart computers
C) home computers
D) smart appliances

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
37
A growing number of college campuses have wireless ____ on campus that allow students to use their PCs to connect wirelessly to the college network and the Internet from anywhere on campus.
A) hotspots
B) hotpoints
C) com spots
D) com points
A) hotspots
B) hotpoints
C) com spots
D) com points

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
38
In piracy , identity thieves send fraudulent e-mails to people masquerading as legitimate businesses to obtain social security numbers or other information needed for identity theft.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
39
IP addresses and their corresponding domain names are used to identify computers available through the Internet.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
40
The ISP is the largest and most well-known computer network in the world.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
41
A(n) ____ is a medium-sized computer used to host programs and data for a small network.
A) mainframe computer
B) super server
C) midrange server
D) Internet server
A) mainframe computer
B) super server
C) midrange server
D) Internet server

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
42
 The accompanying figure corresponds to the ____ style for desktop PCs.
The accompanying figure corresponds to the ____ style for desktop PCs.A) all-in-one case
B) tower case
C) desktop case
D) sub case

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
43
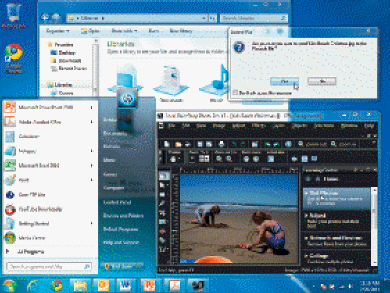 The Windows ____ shown in the figure above contains the following objects: Windows, Icons, Menus, Toolbars, Taskbar, Hyperlinks, Sizing buttons, and a Dialog box.
The Windows ____ shown in the figure above contains the following objects: Windows, Icons, Menus, Toolbars, Taskbar, Hyperlinks, Sizing buttons, and a Dialog box.A) command
B) toolbox
C) general menu
D) desktop

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
44
____ occurs when data is entered into the computer.
A) Output
B) Processing
C) Input
D) Storage
A) Output
B) Processing
C) Input
D) Storage

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
45
Two of the most common types of communications hardware are ____ and network adapters.
A) ports
B) slide rules
C) monitors
D) modems
A) ports
B) slide rules
C) monitors
D) modems

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
46
____ consists of programs designed to allow people to perform specific tasks using a computer, such as creating letters, preparing budgets, and managing inventory.
A) Cloud storage
B) HTML
C) Java Script
D) Application software
A) Cloud storage
B) HTML
C) Java Script
D) Application software

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
47
When data is processed into a meaningful form, it becomes ____.
A) information
B) code
C) a program
D) a database
A) information
B) code
C) a program
D) a database

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
48
Ultra-mobile PCs are also called ____.
A) mini computers
B) handheld computers
C) range computers
D) frame computers
A) mini computers
B) handheld computers
C) range computers
D) frame computers

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
49
A ____ is a collection of hardware and other devices that are connected together so that users can share hardware, software, and data, as well as electronically communicate with each other.
A) computer bank
B) database
C) data bank
D) computer network
A) computer bank
B) database
C) data bank
D) computer network

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
50
Common input devices include the keyboard and ____.
A) printer
B) mouse
C) speaker
D) monitor
A) printer
B) mouse
C) speaker
D) monitor

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
51
Conventional PCs are often referred to as ____ because the complete computer system fits on or next to a desk.
A) desktop computers
B) laptop computers
C) super computers
D) processor computers
A) desktop computers
B) laptop computers
C) super computers
D) processor computers

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
52
A ____ is loosely defined as a very small device that has some built-in computing or Internet capability.
A) mainframe computer
B) midrange server
C) mobile device
D) personal computer
A) mainframe computer
B) midrange server
C) mobile device
D) personal computer

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
53
Hollerith's machine was used to process the 1890 U.S. Census data and was able to complete the task in ____, instead of the decade it usually took to process the data by hand.
A) two and a half years
B) three and a half years
C) four and a half years
D) five and a half years
A) two and a half years
B) three and a half years
C) four and a half years
D) five and a half years

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
54
The term ____ refers to the programs or instructions used to tell the computer hardware what to do.
A) hardware
B) port
C) software
D) adapter
A) hardware
B) port
C) software
D) adapter

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
55
In addition to the four primary computer operations, today's computers typically also perform ____ functions.
A) calculations
B) communications
C) sorting
D) programming
A) calculations
B) communications
C) sorting
D) programming

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
56
Integrated circuits incorporate many transistors and electronic circuits on a single tiny silicon chip, allowing ____ to be even smaller and more reliable than earlier computers.
A) second-generation computers
B) third-generation computers
C) fourth-generation computers
D) fifth-generation computers
A) second-generation computers
B) third-generation computers
C) fourth-generation computers
D) fifth-generation computers

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
57
Most notebooks follow the traditional ____ design in which the monitor is on the inside top half of the PC, and the keyboard and touch pad are on the inside bottom half.
A) clamshell
B) Microsoft
C) IBM
D) book
A) clamshell
B) Microsoft
C) IBM
D) book

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
58
Programming languages come in many varieties-for example, BASIC, Visual Basic, Pascal, COBOL, C++, and ____.
A) TCP/IP
B) Rextore
C) PDF
D) Java
A) TCP/IP
B) Rextore
C) PDF
D) Java

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
59
____ are unique numeric or text-based addresses used to identify resources accessible through the Internet, such as computers, Web pages, and people.
A) Computer addresses
B) Machine IDs
C) Domain IDs
D) Internet addresses
A) Computer addresses
B) Machine IDs
C) Domain IDs
D) Internet addresses

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
60
A personal computer (PC) or ____ is a small computer system designed to be used by one person at a time.
A) processor
B) microcomputer
C) microchip
D) small processor
A) processor
B) microcomputer
C) microchip
D) small processor

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
61
Case-Based Critical Thinking Questions Case 1-1 Sarah is a very active real estate agent. She is looking to purchase a new computer and software so she can keep track of her client's accounts, access the Internet from anywhere in the city, and touch-up photos of real estate properties. Sarah has hired a programmer to create a Web page for her business. What type of programming language will the programmer use?
A) Python
B) COBAL
C) XHTML
D) BASIC
A) Python
B) COBAL
C) XHTML
D) BASIC

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
62
____ is typically free and provided by virtually all ISPs used with personal computers.
A) Short Message mail
B) Web-based e-mail
C) Web-com
D) Program-based e-mail
A) Short Message mail
B) Web-based e-mail
C) Web-com
D) Program-based e-mail

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
63
____________________ are regular appliances with some type of built-in computer technology.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
64
____ refers to typing your entire e-mail message or discussion group post using only capital letters.
A) Spamming
B) Phishing
C) Calling
D) Shouting
A) Spamming
B) Phishing
C) Calling
D) Shouting

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
65
Consumer ____________________ are small self-service computer-based stations, such as ATM machines, bridal registries, and ticketing systems.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
66
____ refers to guidelines for online behavior.
A) Net rules
B) Web etiquette
C) Internet Rules
D) Netiquette
A) Net rules
B) Web etiquette
C) Internet Rules
D) Netiquette

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
67
Computers and traditional devices we use everyday have begun to ____________________ into single units with multiple capabilities.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
68
There are independent Web sites (such as the ____ Web site) that report on the validity of current online rumors and stories.
A) Spammer
B) Snopes
C) Phisher
D) Identifier
A) Spammer
B) Snopes
C) Phisher
D) Identifier

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
69
To contact people using the Internet, you most often use their ____.
A) domain names
B) e-mail addresses
C) usernames
D) passwords
A) domain names
B) e-mail addresses
C) usernames
D) passwords

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
70
To navigate to a new Web page for which you know the URL, type that URL in the browser's ____ and press Enter.
A) Address bar
B) Domain bar
C) Address button
D) Name button
A) Address bar
B) Domain bar
C) Address button
D) Name button

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
71
Case-Based Critical Thinking Questions Case 1-1 Sarah is a very active real estate agent. She is looking to purchase a new computer and software so she can keep track of her client's accounts, access the Internet from anywhere in the city, and touch-up photos of real estate properties. What kind of computer would most likely fit Sarah's needs?
A) midrange server
B) embedded
C) notebook
D) docking station
A) midrange server
B) embedded
C) notebook
D) docking station

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
72
An emerging payment option is the use of ____________________ payment systems-systems that allow individuals to pay for products and services via a mobile phone or other portable device.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
73
There are a number of special Web pages, called ____, available to help you locate what you are looking for on the Internet.
A) search sites
B) domain identifications
C) domain sites
D) Internet repositories
A) search sites
B) domain identifications
C) domain sites
D) Internet repositories

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
74
Case-Based Critical Thinking Questions Case 1-2 Jamie is interested in pursuing computers as a career. He is very comfortable working with PCs and has a broad knowledge of the typical systems and applications software that people use. He has always enjoyed working closely with people and has a good facility for explaining how technical systems work. What type of computer-related job would Jamie probably enjoy the most?
A) hardware designer
B) computer operations personnel
C) systems analyst
D) end user
A) hardware designer
B) computer operations personnel
C) systems analyst
D) end user

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
75
____ are illustrations of faces showing smiles, frowns, and other expressions that are created with keyboard symbols.
A) Spams
B) Phishes
C) Emoticons
D) Trojan horses
A) Spams
B) Phishes
C) Emoticons
D) Trojan horses

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
76
Case-Based Critical Thinking Questions Case 1-2 Jamie is interested in pursuing computers as a career. He is very comfortable working with PCs and has a broad knowledge of the typical systems and applications software that people use. He has always enjoyed working closely with people and has a good facility for explaining how technical systems work. Jamie's mother is a computer programmer and would like Jamie to follow in her footsteps. What course would she most likely suggest that Jamie take in college?
A) systems analysis
B) history of computing
C) computer literacy
D) Java
A) systems analysis
B) history of computing
C) computer literacy
D) Java

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
77
One online security problem is ____, in which someone else uses your identity, typically to purchase goods or services.
A) identity duplication
B) domain theft
C) identity theft
D) phishing
A) identity duplication
B) domain theft
C) identity theft
D) phishing

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
78
____________________ is a common alternative to traditional classroom learning that allows students to participate from their current location, instead of physically going to the educational institution.

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
79
Case-Based Critical Thinking Questions Case 1-1 Sarah is a very active real estate agent. She is looking to purchase a new computer and software so she can keep track of her client's accounts, access the Internet from anywhere in the city, and touch-up photos of real estate properties. Sarah needs to store digital photographs of houses she is previewing. She needs to be able to copy these to the computer at her office. What type of storage device should she use?
A) data projector
B) firewire port
C) scanner
D) USB flash drive
A) data projector
B) firewire port
C) scanner
D) USB flash drive

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck
80
Similar to the way an IP address or domain name uniquely identifies a computer on the Internet, a ____ uniquely identifies a Web page.
A) universal resource identifier (URI)
B) Web ID (WID)
C) uniform resource locator (URL)
D) Web resource identifier (WRI)
A) universal resource identifier (URI)
B) Web ID (WID)
C) uniform resource locator (URL)
D) Web resource identifier (WRI)

Unlock Deck
Unlock for access to all 100 flashcards in this deck.
Unlock Deck
k this deck



