Deck 12: Working in the Enterprise: Systems, Certifications, and Careers
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/75
Play
Full screen (f)
Deck 12: Working in the Enterprise: Systems, Certifications, and Careers
1

Following are the matched definitions corresponding to the given terms:
1. Standards: Standards are defined as the set of procedures and rules which must be followed by the employees.
Therefore the term "Standard" matches with definition (a).
2. Scope: Objectives, goals and expectation of the project. If the scope of the project has to be changed than a less comprehensive system will be obtained by the user. Hence it is necessary that everyone in the project team is agreed and aware to the changes made to the system.
Therefore the term "Scope" matches with definition (h).
3. Deliverable can be any tangible item such as diagram, chart, program file or report. Deliverable is used in project management for describing tangible as well as intangible objects which are produced as a result of project intended to deliver to a customer.
Therefore the term "Deliverable" matches with definition (c).
4. JAD sessions: Joint application design sessions are used by system analyst for gathering data and information instead of using one to one interviews. A JAD session can also be called as focus group. JAD session is consist of a series of lengthy and structured group meeting in which IT professionals and users works together for designing and developing an application.
Therefore the term "JAD sessions" matches with definition (j).
5. Project request: A formal request which is called as project request or request for system service is used by larger organization. The project request is the first item in system documentation.
Therefore the term "Project request" matches with definition (e).
6. Feasibility is defined as the measure for determining suitability of system to an organization. It is possible that a project is feasible at a point in system development but not feasible at another point. Hence it is necessary to evaluate the feasibility of the project at various points.
Therefore the term " Feasibility " matches with definition (i).
7. Benchmark test: It is very important to know whether certain volume of transaction can be processed by the software. In this case, a bench mark test is conducted. A benchmark test is done for measuring the performance for the hardware and the software.
Therefore the term "Feasibility" matches with definition (b).
8. Prototype: In software development life cycle, there are certain or various methodologies or approach used for developing the project or system. One of the types or approach used is Prototyping which deals with developing the model before the actual system is installed. This provides the clear understanding about the functional and non-functional capabilities of the new system. Prototyping helps users in determining the functionality and features in the final system.
Therefore the term "Prototype" matches with definition (f).
9. Sandbox is defined as the testing environment which allows the software developer to test their program with fictitious data without affecting other programs, data and information system adversely.
Sandbox is used by both the user and the developer for testing purpose. Sandbox is used by the user for familiarizing themselves with the new program or information system.
Therefore the term "Sandbox" matches with definition (d).
10. Machine language is the first generation of the programming language. Writing instruction in machine language is tedious and time consuming. Operators are not used in machine language. Machine languageis directly understandable to the computer.
Therefore the term "Sandbox" matches with definition (g).
Summary of the terms matched with corresponding definitions.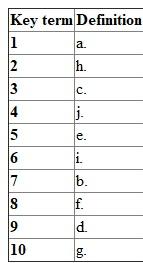
1. Standards: Standards are defined as the set of procedures and rules which must be followed by the employees.
Therefore the term "Standard" matches with definition (a).
2. Scope: Objectives, goals and expectation of the project. If the scope of the project has to be changed than a less comprehensive system will be obtained by the user. Hence it is necessary that everyone in the project team is agreed and aware to the changes made to the system.
Therefore the term "Scope" matches with definition (h).
3. Deliverable can be any tangible item such as diagram, chart, program file or report. Deliverable is used in project management for describing tangible as well as intangible objects which are produced as a result of project intended to deliver to a customer.
Therefore the term "Deliverable" matches with definition (c).
4. JAD sessions: Joint application design sessions are used by system analyst for gathering data and information instead of using one to one interviews. A JAD session can also be called as focus group. JAD session is consist of a series of lengthy and structured group meeting in which IT professionals and users works together for designing and developing an application.
Therefore the term "JAD sessions" matches with definition (j).
5. Project request: A formal request which is called as project request or request for system service is used by larger organization. The project request is the first item in system documentation.
Therefore the term "Project request" matches with definition (e).
6. Feasibility is defined as the measure for determining suitability of system to an organization. It is possible that a project is feasible at a point in system development but not feasible at another point. Hence it is necessary to evaluate the feasibility of the project at various points.
Therefore the term " Feasibility " matches with definition (i).
7. Benchmark test: It is very important to know whether certain volume of transaction can be processed by the software. In this case, a bench mark test is conducted. A benchmark test is done for measuring the performance for the hardware and the software.
Therefore the term "Feasibility" matches with definition (b).
8. Prototype: In software development life cycle, there are certain or various methodologies or approach used for developing the project or system. One of the types or approach used is Prototyping which deals with developing the model before the actual system is installed. This provides the clear understanding about the functional and non-functional capabilities of the new system. Prototyping helps users in determining the functionality and features in the final system.
Therefore the term "Prototype" matches with definition (f).
9. Sandbox is defined as the testing environment which allows the software developer to test their program with fictitious data without affecting other programs, data and information system adversely.
Sandbox is used by both the user and the developer for testing purpose. Sandbox is used by the user for familiarizing themselves with the new program or information system.
Therefore the term "Sandbox" matches with definition (d).
10. Machine language is the first generation of the programming language. Writing instruction in machine language is tedious and time consuming. Operators are not used in machine language. Machine languageis directly understandable to the computer.
Therefore the term "Sandbox" matches with definition (g).
Summary of the terms matched with corresponding definitions.

2
System development activities often are grouped into larger categories called _____.
A) deliverables c. phases
B) standards d. objects
A) deliverables c. phases
B) standards d. objects
Grouping of activities
System development cycle is defined as the set of activities which is used for building an information system. These activities are grouped into larger categories which is called phrases. The collection of phrases is called system development life cycle.
Hence, the correct option is c.
Deliverable can be any tangible item such as diagram, chart, program file or report. Deliverable is used in project management for describing tangible as well as intangible objects which are produced as a result of project intended to deliver to a customer.
Hence, the option 'a' is not correct.
Standards are defined as the set of procedures and rules which must be followed by the employees.
Hence, the option 'b' is not correct.
Objects are real world entities. Object is an entity which can include both procedures and data. A person, place and events can be included in objects.
Hence, the option 'd' is not correct.
System development cycle is defined as the set of activities which is used for building an information system. These activities are grouped into larger categories which is called phrases. The collection of phrases is called system development life cycle.
Hence, the correct option is c.
Deliverable can be any tangible item such as diagram, chart, program file or report. Deliverable is used in project management for describing tangible as well as intangible objects which are produced as a result of project intended to deliver to a customer.
Hence, the option 'a' is not correct.
Standards are defined as the set of procedures and rules which must be followed by the employees.
Hence, the option 'b' is not correct.
Objects are real world entities. Object is an entity which can include both procedures and data. A person, place and events can be included in objects.
Hence, the option 'd' is not correct.
3
Who belongs to a project team? What skills should a systems analyst have?
Participant in project team
In system development, the system analyst works and meets to a variety of people. The designing and developing of an information system is the primary responsibility of the system analyst and he is the primary contact person for the users.
The task performed by the system analyst can vary depending upon the type of task. There can be one system analyst in small organization that is in charge of performing the role of both the software developer and system analyst.
Some organization forms project team. This project team includes system analyst , users and IT professionals.
Skill set of a system analyst
Skills that should be possessed by a system analyst:
• They must have superior technical skills.
• They must be able to solve problems.
• They should be familiar with business operation.
• They should have ability to support and introduce.
• They should possess excellent communication skills.
In system development, the system analyst works and meets to a variety of people. The designing and developing of an information system is the primary responsibility of the system analyst and he is the primary contact person for the users.
The task performed by the system analyst can vary depending upon the type of task. There can be one system analyst in small organization that is in charge of performing the role of both the software developer and system analyst.
Some organization forms project team. This project team includes system analyst , users and IT professionals.
Skill set of a system analyst
Skills that should be possessed by a system analyst:
• They must have superior technical skills.
• They must be able to solve problems.
• They should be familiar with business operation.
• They should have ability to support and introduce.
• They should possess excellent communication skills.
4
Identify the five phases in the SDLC. Name three guidelines for system development.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
5
Activities within phases of the SDLC often interact with one another, making system development a dynamic iterative process.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
6
During system development, the _____ is the users' primary contact.
A) web developer c. steering committee
B) systems analyst d. programmer
A) web developer c. steering committee
B) systems analyst d. programmer

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
7
Differentiate between Gantt charts and PERT charts. What is scope creep?

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
8
Identify who participates in system development. Describe the skill set of a systems analyst.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
9
Detailed analysis sometimes is called logical design.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
10
_____ feasibility measures how well the proposed system will work.
A) Operational c. Technical
B) Schedule d. Economic
A) Operational c. Technical
B) Schedule d. Economic

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
11
What are a CSO's responsibilities? What qualifications should a CSO have?

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
12
Explain positive and negative issues surrounding telecommuting.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
13
A mock-up is more technical than a layout chart and contains programming-like notations.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
14
Which of the following activities is not performed during the planning phase?
A) prototyping
B) prioritizing the project requests
C) allocating resources
D) forming a project development team
A) prototyping
B) prioritizing the project requests
C) allocating resources
D) forming a project development team

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
15
Differentiate between low-level and high-level languages. Differentiate between a compiler and an interpreter.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
16
Define the term, project management. List elements the project leader must identify.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
17
One reason systems fail is because the systems analyst creates or modifies systems with little or no user participation.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
18
With a(n) _____, a vendor selects a product(s) that meets specified requirements and then quotes the price(s).
A) RFP c. RFQ
B) RFI d. VAR
A) RFP c. RFQ
B) RFI d. VAR

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
19
What are HTML5 and CSS? List some uses of JavaScript.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
20
Define these terms: project management software, project plan, and deliverable.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
21
Only the systems analyst and developers should review detailed design specifications before they are given to the programming team.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
22
_____ test verifies that all programs in an application work together properly.
A) acceptance c. unit
B) integration d. systems
A) acceptance c. unit
B) integration d. systems

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
23
Describe how Gantt and PERT charts are used.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
24
The purpose of the implementation phase is to construct the new or modified system and then deliver it to the users.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
25
Which of the following activities is not performed during the support and security phase?
A) converting to the new system
B) performing maintenance
C) monitoring system performance
D) assessing system security
A) converting to the new system
B) performing maintenance
C) monitoring system performance
D) assessing system security

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
26
Define the terms, scope creep and change management.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
27
With a high-level language, each instruction usually equates to a single machine instruction.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
28
Used as the markup language on many smartphones and mobile devices, _____ allows web developers to design pages specifically for microbrowsers.
A) WML c. HTML
B) XML d. ATOM
A) WML c. HTML
B) XML d. ATOM

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
29
Identify tests used to evaluate feasibility of a project.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
30
A procedural language is the only language the computer directly recognizes.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
31
Explain the importance of documentation.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
32
To convert machine language into an assembly language source code, programmers use a program called an assembler.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
33
Describe ways that team members collaborate.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
34
The machine language version that results from compiling a 3GL is called the object program.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
35
Identify data and information gathering techniques. A(n) _____ session also is called a focus group.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
36
One advantage of a compiler is that when it finds errors, it displays feedback immediately.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
37
Identify the contributions of the Wikimedia Foundation and Jimmy Wales.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
38
HTML is not a programming language.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
39
List components of information literacy.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
40
Describe circumstances that can initiate system development.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
41
Explain issues surrounding the effect of digital communications on relationships.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
42
List the four activities of the planning phase. Explain how projects are prioritized.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
43
Name the activities of the analysis phase. Identify questions to ask a user who submits a project request.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
44
List the three activities of the detailed analysis phase. Detailed analysis sometimes is called _____ design.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
45
Describe how a steering committee may decide on a system proposal.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
46
Explain security issues surrounding outsourcing.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
47
List the two activities of the design phase.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
48
Describe how a systems analyst obtains hardware or software.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
49
Differentiate among an RFQ, RFP, and RFI. Describe the roles of VARs and IT consultants when soliciting vendor proposals.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
50
Explain what occurs when vendor proposals are tested and evaluated. A(n) _____ test measures the performance of hardware or software.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
51
Identify circumstances that might influence the decision to accept a vendor proposal.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
52
Explain the activities that occur during the detailed design phase and the people involved in the review.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
53
Describe how systems analysts build relationships with users.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
54
Define the terms, prototype and CASE software.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
55
List the four activities of the implementation phase.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
56
Define the term, program development life cycle. Identify considerations for program logic.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
57
Explain issues surrounding the use of back doors in software development.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
58
Define the term, sandbox.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
59

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
60
Describe the activities that occur during the training phase.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
61
Differentiate among the following conversion strategies: direct, parallel, phased, and pilot.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
62
List the three activities of the support and security phase.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
63
Explain the role of a CSO. Describe the components of a technology security plan.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
64
Define the following terms: programming language, application development tool, and syntax.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
65
Differentiate between low- and high-level programming languages.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
66
Differentiate among machine, assembly, and procedural languages.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
67
Explain issues surrounding colleges that teach students how to hack.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
68
List guidelines to determine whether a program or app is safe to use.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
69
Define the terms, compiler and interpreter.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
70
List benefits of OOP languages. Name three types of OOP languages.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
71
List guidelines to determine which programming language or development tool to use. Explain the RAD method.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
72
Describe the following: 4GLs, classic programming languages, application generators, and macros. Explain how to protect yourself from macro viruses.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
73
List steps to post a webpage. Explain how web developers use HTML, XML, CSS, and JavaScript.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
74
Identify how web developers add interactivity. List guidelines to choose a scripting language.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
75
Explain how the construction industry uses technology.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck



