A security analyst is evaluating two vulnerability management tools for possible use in an organization. The analyst set up each of the tools according to the respective vendor's instructions and generated a report of vulnerabilities that ran against the same target server. Tool A reported the following: 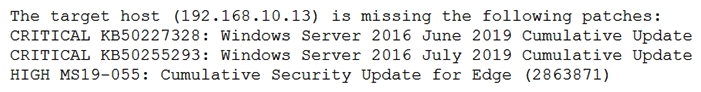 Tool B reported the following:
Tool B reported the following:  Which of the following BEST describes the method used by each tool? (Choose two.)
Which of the following BEST describes the method used by each tool? (Choose two.)
A) Tool A is agent based.
B) Tool A used fuzzing logic to test vulnerabilities.
C) Tool A is unauthenticated.
D) Tool B utilized machine learning technology.
E) Tool B is agent based.
F) Tool B is unauthenticated.
Correct Answer:
Verified
Q147: Which of the following are components of
Q148: A security analyst is investigating a system
Q149: Which of the following session management techniques
Q150: A cyber-incident response analyst is investigating a
Q151: An organization was alerted to a possible
Q153: Which of the following secure coding techniques
Q154: A company is moving from the use
Q155: The help desk provided a security analyst
Q156: A cybersecurity analyst is investigating a potential
Q157: A large amount of confidential data was
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents