Deck 14: Databases and Database Management Systems
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/100
العب
ملء الشاشة (f)
Deck 14: Databases and Database Management Systems
1
Repairing or restoring data that has become corrupt,perhaps as the result of a storage media error or computer virus,is a database analysis activity.
False
2
If a field needs to store decimal places,the Long Integer field size can be used.
False
3
Arranging data for efficient retrieval is called data organization.
True
4
Data accessibility refers to protecting data against destruction and misuse-both intentionally and accidentally.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
5
Most databases created today do not use the hierarchical or network models;these models are generally used with legacy systems that are still operational and must be maintained.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
6
At the top of the data hierarchy is the database,which consists of a group of related tables.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
7
Normalization is usually viewed as a multistep process,from first normal form (1NF)to usually fifth normal form (5NF).

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
8
The data dictionary includes data located in the database tables.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
9
To protect against data loss caused by a database failure,accidental deletion,or other problem that renders the main copy of a database unusable,stringent backup procedures should be implemented.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
10
Typically,in hierarchical database management systems,a one-to-one relationship exists between data entities.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
11
With HOLAP (Hybrid OLAP),a combination of MOLAP and ROLAP technologies are used.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
12
In some systems,data integrity is enforced on a per transaction basis.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
13
Multidimensional databases are appropriate when a variety of types of objects need to be stored and retrieved.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
14
IBM's DB2 9 program contains a hybrid XML/relational database server.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
15
Hashing procedures usually result in two or more records being assigned the same storage address,an event known as a collision.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
16
N-tier database systems provide a great deal of flexibility and scalability,allowing the system to be modified as new needs and opportunities arise.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
17
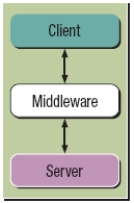
The figure above shows an n-tier database model.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
18
Views need to be designed to extract the needed information in as efficient a manner as possible.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
19
Many-to-many entity relationships exist when one entity can be related to more than one other entity,and those entities can be related to multiple entities of the same type as the original entity.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
20
Data integrity refers to the accuracy of data.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
21
At the lowest level,words are entered into database fields/columns,which hold single pieces of data in the database,such as product names or quantities.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
22
Primary keys can be a combination of two key fields (called composite primary keys),but single primary keys are more typical in simple databases.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
23
In determining the location where specific data is to be stored in a(n)centralized DBMS,factors such as communications cost,response time,storage cost,and security are key considerations.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
24
Structured query language (SQL)is recognized as the standard query language for relational databases.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
25
One emerging data security risk is the exploitation of known but unpatched vulnerabilities by hackers.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
26
A ____ holds a single category of data (such as customer names or employee telephone numbers)that will be stored in a database.
A)cell
B)field
C)table
D)record
A)cell
B)field
C)table
D)record

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
27
With MOLAP (Multidimensional OLAP),the multidimensional information is stored in an existing relational database using tables to store the summary information.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
28
The finished specifications for a table are commonly referred to as the table format.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
29
Software that connects two otherwise separate applications-such as a Web server and a DBMS-is referred to as interware

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
30
A ____ is a collection of related fields.
A)table
B)field
C)column
D)record
A)table
B)field
C)column
D)record

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
31
Web databases allow Web pages to be static Web pages; that is, Web pages in which the appearance or content of the pages change based on the user’s input.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
32
A record is also called a ____.
A)field
B)report
C)row
D)table
A)field
B)report
C)row
D)table

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
33
After all the tables in a database application have been created and their primary keys designated,the tables can be related to one another via their primary key so that a primary key for one table can be used to extract data from other tables as needed.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
34
A(n)file management system is a program that allows the creation of individual database tables,each of which is stored in its own physical file and is not related to any other file.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
35
As part of its disaster-recovery plan,some firms maintain a(n)hot site-an alternate location equipped with identical hardware and software that can be used to resume operations quickly in case of a major disaster.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
36
One advantage of the n-tier architecture is that it allows the program code used to access the database to be separate from the database,and the code can be divided into any number of logical components.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
37
Objects stored in an OODBMS can be retrieved using queries,such as with a(n)object query language (OQL)-an object-oriented version of SQL.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
38
Most DBMSs come bundled with a set of tools to perform a variety of necessary tasks,such as building user interfaces,creating forms and reports,and interfacing with query languages and ____ for complex applications.
A)query wizards
B)programming languages
C)report generators
D)form screens
A)query wizards
B)programming languages
C)report generators
D)form screens

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
39
Database developers are the people responsible for managing the databases within an organization.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
40
A field is also called a ____.
A)column
B)row
C)table
D)record
A)column
B)row
C)table
D)record

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
41
One of the properties that can be assigned to a field is a(n)____ to specify the format (such as letters,numbers,or symbols)that must be entered into a field.
A)format structure
B)input mask
C)data mask
D)data filter
A)format structure
B)input mask
C)data mask
D)data filter

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
42
Individual database tables are often referred to as ____.
A)low files
B)base files
C)flat files
D)clear files
A)low files
B)base files
C)flat files
D)clear files

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
43
The ____ contains all data definitions for a database,including table structures,security information,relationships between the tables in the database,and so on.
A)database book
B)data dictionary
C)data box
D)data book
A)database book
B)data dictionary
C)data box
D)data book

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
44
____ is a growing concern because of the vast amounts of personal data stored in databases today and the many breaches that have occurred in the recent past.
A)Data privacy
B)Data integrity
C)Data accessibility
D)Data legibility
A)Data privacy
B)Data integrity
C)Data accessibility
D)Data legibility

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
45
In a typical client-server database application,the client is called the ____.
A)back end
B)rear end
C)portal
D)front end
A)back end
B)rear end
C)portal
D)front end

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
46
The characteristics of an entity are called ____.
A)attributes
B)variables
C)traits
D)fields
A)attributes
B)variables
C)traits
D)fields

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
47
With a ____,a database is located in its entirety on a single computer,such as a server or mainframe computer.
A)distributed database system
B)star database system
C)centralized database system
D)ring database system
A)distributed database system
B)star database system
C)centralized database system
D)ring database system

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
48
In ____,the table field involved in the changes is locked until the changes to that field have been completed.
A)column-level locking
B)database locking
C)row-level locking
D)record-level locking
A)column-level locking
B)database locking
C)row-level locking
D)record-level locking

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
49
A(n)____ is a small table consisting only of a list of the primary key field for each record in a table along with location information for that record.
A)tablet
B)keyword
C)index
D)main table
A)tablet
B)keyword
C)index
D)main table

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
50
____ are made up of related records.
A)Rows
B)Fields
C)Columns
D)Tables
A)Rows
B)Fields
C)Columns
D)Tables

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
51
One of the simplest hashing algorithms involves dividing the primary key field by a particular ____.
A)power of two
B)prime number
C)irrational number
D)transcendental number
A)power of two
B)prime number
C)irrational number
D)transcendental number

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
52
____ actually create the database,based on the design generated by the database designer,and get it ready for data entry.
A)Database developers
B)Database administrators (DBAs)
C)Database security officers
D)Database analysts
A)Database developers
B)Database administrators (DBAs)
C)Database security officers
D)Database analysts

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
53
With ____,the computer uses each record's primary key field and a mathematical formula called a hashing algorithm to determine a unique address that identifies where the record is physically stored in the database file.
A)real-time organization
B)indexed organization
C)sequenced organization
D)direct organization
A)real-time organization
B)indexed organization
C)sequenced organization
D)direct organization

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
54
Virtually all DBMSs include a ____ for easy data input,modification,and retrieval.
A)user interface
B)line interface
C)command interface
D)device interface
A)user interface
B)line interface
C)command interface
D)device interface

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
55
DBMSs available for use on personal computers include ____ and Corel Paradox.
A)IBM DB2
B)Microsoft Access
C)Adobe Acrobat
D)Adobe Fireworks
A)IBM DB2
B)Microsoft Access
C)Adobe Acrobat
D)Adobe Fireworks

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
56
Data definition involves describing the properties of the data that go into each database table,specifically the ____ that make up the database.
A)records
B)rows
C)fields
D)characters
A)records
B)rows
C)fields
D)characters

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
57
The process of evaluating and correcting the structures of the tables in a database to minimize data redundancy is called ____.
A)normalization
B)cyclic redundancy check
C)zeroing
D)zonification
A)normalization
B)cyclic redundancy check
C)zeroing
D)zonification

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
58
The field in a table that is used to relate that table to other tables is called the ____.
A)composite key
B)secondary key
C)primary key
D)primary field
A)composite key
B)secondary key
C)primary key
D)primary field

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
59
The ____ is the most widely used database model today.
A)hierarchical database management system
B)relational database management system (RDBMS)
C)network database management system
D)database management system (DBMS)
A)hierarchical database management system
B)relational database management system (RDBMS)
C)network database management system
D)database management system (DBMS)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
60
If a new database is to be used with existing data,the data needs to be transferred from its existing form into the new system-a process called ____.
A)migration
B)conversion
C)normalization
D)accommodation
A)migration
B)conversion
C)normalization
D)accommodation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
61
Case 14-2
The JL Group is a political think tank that is incorporating new media into their analyses.
The JL Group has gathered data on voting habits.In order to make sure that respondents cannot claim to have voted in more elections than is possible given their age,____ rules can be assigned to the database tables.
A)index validation
B)record validation
C)DBA validation
D)dynamic
The JL Group is a political think tank that is incorporating new media into their analyses.
The JL Group has gathered data on voting habits.In order to make sure that respondents cannot claim to have voted in more elections than is possible given their age,____ rules can be assigned to the database tables.
A)index validation
B)record validation
C)DBA validation
D)dynamic

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
62
Case 14-2
The JL Group is a political think tank that is incorporating new media into their analyses.
The employees of JL Group who use the database of the company for their daily work,without having knowledge of how the underlying database is structured,interact with the database ____.
A)using the database script
B)through the database designer
C)through the database programmer
D)using the user interface
The JL Group is a political think tank that is incorporating new media into their analyses.
The employees of JL Group who use the database of the company for their daily work,without having knowledge of how the underlying database is structured,interact with the database ____.
A)using the database script
B)through the database designer
C)through the database programmer
D)using the user interface

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
63
Case 14-1
James is a recent college graduate and has six months of IT experience.He is thinking about pursuing a certification program in order to demonstrate that he is serious about IT.
James is most interested in becoming a database designer.Another name for this career choice is database ____.
A)architect
B)developer
C)programmer
D)administrator
James is a recent college graduate and has six months of IT experience.He is thinking about pursuing a certification program in order to demonstrate that he is serious about IT.
James is most interested in becoming a database designer.Another name for this career choice is database ____.
A)architect
B)developer
C)programmer
D)administrator

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
64
The key characteristics for an OODBMS (including objects,attributes,methods,____,and inheritance)are similar to object-oriented programming principles.
A)pages
B)scripting
C)conversion
D)classes
A)pages
B)scripting
C)conversion
D)classes

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
65
In ASPs,the code to tie the database to the Web site is typically written in JavaScript or ____.
A)VBScript
B)CGI
C)PHP
D)BasicScript
A)VBScript
B)CGI
C)PHP
D)BasicScript

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
66
A(n)____________________ is a specific field in a database table that uniquely identifies the records in that table.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
67
Continuing to evaluate and improve the security measured used with the database is a database ____ activity.
A)programming
B)design
C)implementation
D)maintenance
A)programming
B)design
C)implementation
D)maintenance

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
68
To create a query,users can either type a query using SQL or,more commonly,use the query tools built into the DBMS (such as a query design screen or query ____)to create a query object.
A)command
B)line
C)wizard
D)key
A)command
B)line
C)wizard
D)key

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
69
The ____________________ in a database system are the ones who enter data,update data,and retrieve information from the database when necessary.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
70
The JL Group is in the process of creating dynamic Web pages to poll politically aware young adults. They are interested in creating scripts that are compatible with many types of databases, so they are using the ____ language.
A)CGI
B)API
C)COBOL
D)PHP
A)CGI
B)API
C)COBOL
D)PHP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
71
Web-based database requests are received by the Web server,which then converts the request into a database query and passes it on to the database server with the help of software called ____.
A)middleware
B)capsules
C)macros
D)applets
A)middleware
B)capsules
C)macros
D)applets

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
72
A ____ extracts specific information from a database by specifying particular conditions (called criteria)about the data you would like to retrieve.
A)form
B)query
C)macro
D)view
A)form
B)query
C)macro
D)view

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
73
____ databases are designed to store a collection of summarized data for quick and easy data analysis.
A)Relational
B)Object-oriented
C)Analytical
D)Multidimensional
A)Relational
B)Object-oriented
C)Analytical
D)Multidimensional

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
74
With ____,data is stored in single multidimensional database structures (sometimes called data cubes).
A)Online Analytical Processing (OLAP)
B)ROLAP (Relational OLAP)
C)MOLAP (Multidimensional OLAP)
D)HOLAP (Hybrid OLAP)
A)Online Analytical Processing (OLAP)
B)ROLAP (Relational OLAP)
C)MOLAP (Multidimensional OLAP)
D)HOLAP (Hybrid OLAP)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
75
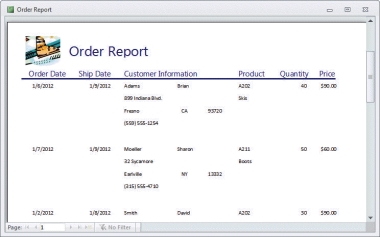
The figure above illustrates a ____,created from data contained in a database.
A)report
B)query
C)form
D)table

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
76
____________________ entity relationships exist when one entity is related to only one other entity of a particular type.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
77
Case 14-1
James is a recent college graduate and has six months of IT experience.He is thinking about pursuing a certification program in order to demonstrate that he is serious about IT.
Database designers work with systems analysts and other individuals involved in ____.
A)CCP
B)DBMS
C)SDLC
D)CDMP
James is a recent college graduate and has six months of IT experience.He is thinking about pursuing a certification program in order to demonstrate that he is serious about IT.
Database designers work with systems analysts and other individuals involved in ____.
A)CCP
B)DBMS
C)SDLC
D)CDMP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
78
Middleware for Web database applications is commonly written as ____-short sections of code written in a programming or scripting language that are executed by another program.
A)scripts
B)JavaScripts
C)applets
D)utilities
A)scripts
B)JavaScripts
C)applets
D)utilities

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
79
To ensure the uniqueness of the ____________________,it usually consists of an identifying number,such as a student ID number,customer number,or product number.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
80
A database typically consists of interrelated ____________________ consisting of fields and records.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck








