Deck 10: Distributed DBMSs-Advanced Concepts and Object-Oriented DBMSs-Concepts and Design
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/14
العب
ملء الشاشة (f)
Deck 10: Distributed DBMSs-Advanced Concepts and Object-Oriented DBMSs-Concepts and Design
1
The centralized two-phase commit protocol uses a series of timeouts to prevent unnecessary blocking. Discuss the actions for both coordinator and participants when a timeout occurs. Consideration should be given to the various stages of the commit protocol.
See Section 25.4.3.
2
Under the three-phase commit protocol, discuss how the coordinator and participants would recover following a failure. Consideration should be given to the various stages of the commit protocol.
Coordinator Failure
1. Failure in INITIAL state. The coordinator has not yet started the commit procedure. Recovery in this case starts the commit procedure.
2. Failure in WAITING state. The coordinator has sent the prepare message and although has not received all responses, the coordinator has not received an abort response. In this case, recovery restarts the commit procedure.
3. Failure in DECIDED state. The coordinator has instructed the participants to globally abort or commit the transaction. On restart, if the coordinator has received all acknowledgements, it can complete successfully. Otherwise, it has to initiate the termination protocol discussed above.
4. Failure in PRE-COMMITTED state. The coordinator has instructed the participants to pre-commit the transaction. On restart, if the coordinator has received all acknowledgements, it can send the global commit message. Otherwise, it can send the pre-commit message again.
Participant Failure
The objective of the recovery protocol for a participant is to ensure that a participant process on restart performs the same action as all other participants and that this restarting can be done independently (i.e. without the need to consult either the coordinator or the other participants).
1. Failure in INITIAL state. The participant has not yet voted on the transaction. Therefore, on recovery, it can unilaterally abort the transaction, as it would have been impossible for the coordinator to have reached a global commit decision without this participants vote.
2. Failure in PREPARED state. The participant has sent its vote to the coordinator. In this case, recovery is via the termination protocol discussed above.
3. Failure in ABORTED/COMMITTED states. Participant has completed the transaction. Therefore, on restart, no further action is necessary.
4. Failure in PRE-COMMITTED state. Participant informs coordinator and waits for global commit message.
1. Failure in INITIAL state. The coordinator has not yet started the commit procedure. Recovery in this case starts the commit procedure.
2. Failure in WAITING state. The coordinator has sent the prepare message and although has not received all responses, the coordinator has not received an abort response. In this case, recovery restarts the commit procedure.
3. Failure in DECIDED state. The coordinator has instructed the participants to globally abort or commit the transaction. On restart, if the coordinator has received all acknowledgements, it can complete successfully. Otherwise, it has to initiate the termination protocol discussed above.
4. Failure in PRE-COMMITTED state. The coordinator has instructed the participants to pre-commit the transaction. On restart, if the coordinator has received all acknowledgements, it can send the global commit message. Otherwise, it can send the pre-commit message again.
Participant Failure
The objective of the recovery protocol for a participant is to ensure that a participant process on restart performs the same action as all other participants and that this restarting can be done independently (i.e. without the need to consult either the coordinator or the other participants).
1. Failure in INITIAL state. The participant has not yet voted on the transaction. Therefore, on recovery, it can unilaterally abort the transaction, as it would have been impossible for the coordinator to have reached a global commit decision without this participants vote.
2. Failure in PREPARED state. The participant has sent its vote to the coordinator. In this case, recovery is via the termination protocol discussed above.
3. Failure in ABORTED/COMMITTED states. Participant has completed the transaction. Therefore, on restart, no further action is necessary.
4. Failure in PRE-COMMITTED state. Participant informs coordinator and waits for global commit message.
3
Consider six transactions T1, T2, T3, T4, and T5 with:
- T1 initiated at site S1 and spawning an agent at site S2,
- T2 initiated at site S3 and spawning an agent at site S1,
- T3 initiated at site S1 and spawning an agent at site S3,
- T4 initiated at site S2 and spawning an agent at site S3,
- T5 initiated at site S3.
The locking information for these transactions is shown in Table 1. Produce the local wait-for-graphs (WFGs) for each of the sites. What can you conclude from the local WFGs?
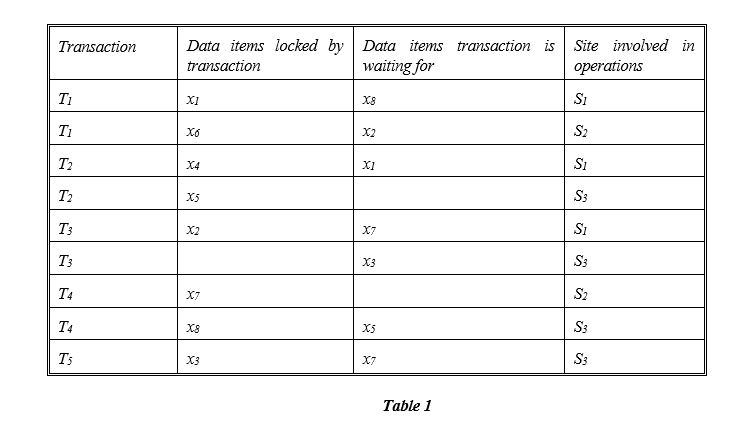
- T1 initiated at site S1 and spawning an agent at site S2,
- T2 initiated at site S3 and spawning an agent at site S1,
- T3 initiated at site S1 and spawning an agent at site S3,
- T4 initiated at site S2 and spawning an agent at site S3,
- T5 initiated at site S3.
The locking information for these transactions is shown in Table 1. Produce the local wait-for-graphs (WFGs) for each of the sites. What can you conclude from the local WFGs?

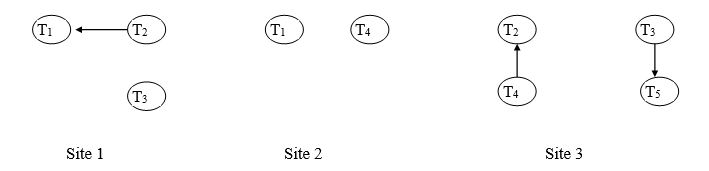
Conclusion: There is no local deadlock at any site.
4
One of the most well-known methods for distributed deadlock detection was developed by Obermarck. Explain how Obermarck's method works and how deadlock is detected and resolved.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 14 في هذه المجموعة.
فتح الحزمة
k this deck
5
Using the above transactions, demonstrate how Obermarck's method for distributed deadlock detection works.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 14 في هذه المجموعة.
فتح الحزمة
k this deck
6
Discuss why traditional transaction management protocols are too restrictive for advanced database applications.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 14 في هذه المجموعة.
فتح الحزمة
k this deck
7
Case Study - Library System
The librarian will access the system to issue books, record reservations, generate return requests for reserved books and record books being returned. Returning a book may involve generating an availability notification if the returned book has been reserved by another member. If an availability notification is generated then the librarian sends it out to the member. When a book is requested to be issued or requested to be reserved then the system validates details on the membership card as well as validating that the requested book is one stocked by the library. If the membership card is invalid or the library does not stock the book then the request is rejected. If a book is requested for issue but is on-loan then that book will be reserved. Members of the library can display details of books stocked. The subscriptions section deals with membership issues e.g. renewing membership cards on an annual basis etc. The purchasing section deals with adding new books to the library.
There may be multiple copies of books held in the library. When a book is borrowed the borrowing date is noted and when the book is returned the return date is noted. The details held about each reservation include who the current borrower(s) is and who has reserved the book.
When a copy of a book arrives from the suppliers, it is held in storage until its details are registered on the system. These details include the number, author and title of the book. Once registered the copy is put in the lending shelf which means that it is available to be borrowed. When a copy is returned, if the book has been reserved then the copy is held in a reservation area otherwise it is returned to the lending shelf. If a copy is reported lost by the borrower then the copy details are deleted from the system by the librarian.
A reservation
Reservation
Number:
Date:
Book
Number:
Title:
Author:
Reserver
Number:
Name:
Address:
Current Borrower
Number:
Name:
Address:
-Produce use case diagrams and a set of associated sequence diagrams for the above case study.
The librarian will access the system to issue books, record reservations, generate return requests for reserved books and record books being returned. Returning a book may involve generating an availability notification if the returned book has been reserved by another member. If an availability notification is generated then the librarian sends it out to the member. When a book is requested to be issued or requested to be reserved then the system validates details on the membership card as well as validating that the requested book is one stocked by the library. If the membership card is invalid or the library does not stock the book then the request is rejected. If a book is requested for issue but is on-loan then that book will be reserved. Members of the library can display details of books stocked. The subscriptions section deals with membership issues e.g. renewing membership cards on an annual basis etc. The purchasing section deals with adding new books to the library.
There may be multiple copies of books held in the library. When a book is borrowed the borrowing date is noted and when the book is returned the return date is noted. The details held about each reservation include who the current borrower(s) is and who has reserved the book.
When a copy of a book arrives from the suppliers, it is held in storage until its details are registered on the system. These details include the number, author and title of the book. Once registered the copy is put in the lending shelf which means that it is available to be borrowed. When a copy is returned, if the book has been reserved then the copy is held in a reservation area otherwise it is returned to the lending shelf. If a copy is reported lost by the borrower then the copy details are deleted from the system by the librarian.
A reservation
Reservation
Number:
Date:
Book
Number:
Title:
Author:
Reserver
Number:
Name:
Address:
Current Borrower
Number:
Name:
Address:
-Produce use case diagrams and a set of associated sequence diagrams for the above case study.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 14 في هذه المجموعة.
فتح الحزمة
k this deck
8
Give your definition of an Object-Oriented Database Management System (OODBMS). Discuss what you consider to be the three most important advantages of a DDBMS over a relational DBMS. Justify your selection of the three advantages.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 14 في هذه المجموعة.
فتح الحزمة
k this deck
9
Despite the superior expressive power of the Object-Oriented Database Management System (OODBMS) in comparison to the established relational systems, the acceptance of the OODBMS will ultimately depend on its performance. The key to this may well lie with how persistent objects are accessed. Discuss the design goals for the incorporation of persistence in a programming language.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 14 في هذه المجموعة.
فتح الحزمة
k this deck
10
Object databases have roots in both programming languages and database management. However, not all aspects of these two technologies blend together easily. One area of potential conflict arises when we try to completely separate persistence and type.
(a) Define the orthogonality of persistence and type.
(b) Discuss this issue for any three of the following subsystems:
(1) Queries
(2) Schemas
(3) Transactions
(4) Existence Semantics.
(a) Define the orthogonality of persistence and type.
(b) Discuss this issue for any three of the following subsystems:
(1) Queries
(2) Schemas
(3) Transactions
(4) Existence Semantics.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 14 في هذه المجموعة.
فتح الحزمة
k this deck
11
Discuss the concept of object identifiers (OIDs) in an object DBMS and discuss four different approaches for the representation of OIDs.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 14 في هذه المجموعة.
فتح الحزمة
k this deck
12
Discuss how OIDs differ from C++ pointers.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 14 في هذه المجموعة.
فتح الحزمة
k this deck
13
(a) 'Pointer swizzling' is a technique that can be used to optimize access to main memory resident persistent objects. Discuss in general terms how pointer swizzling works.(b) Classify and evaluate the different approaches to pointer swizzling.(c) Briefly discuss any alternative approach that could be used to handle persistence in an ODBMS.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 14 في هذه المجموعة.
فتح الحزمة
k this deck
14
(a) Discuss why traditional transaction management protocols are too restrictive for advanced database applications.(b) 'Only Object-Oriented Database Management Systems can support alternative transaction management protocols effectively.' Discuss the validity of this statement.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 14 في هذه المجموعة.
فتح الحزمة
k this deck








