Deck 5: LPI Level 1 Exam 102, Junior Level Linux Certification, Part 2 of 2
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/106
العب
ملء الشاشة (f)
Deck 5: LPI Level 1 Exam 102, Junior Level Linux Certification, Part 2 of 2
1
Which of the following commands lists all defined variables and functions within Bash?
A) env
B) set
C) env -a
D) echo $ENV
A) env
B) set
C) env -a
D) echo $ENV
set
2
Which of the following fields are available in both the global /etc/crontab file as well as in user-specific crontab files?
A) Year
B) Minute
C) Username
D) Command
A) Year
B) Minute
C) Username
D) Command
Minute
Command
Command
3
Which file used by XDM specifies the default wallpaper?
A) /etc/X11/xdm/Xsetup
B) /etc/X11/xdm.conf
C) /etc/X11/xdm/Defaults
D) /etc/X11/defaults.conf
A) /etc/X11/xdm/Xsetup
B) /etc/X11/xdm.conf
C) /etc/X11/xdm/Defaults
D) /etc/X11/defaults.conf
/etc/X11/xdm/Xsetup
4
What output will the command seq 10 produce?
A) A continuous stream of numbers increasing in increments of 10 until stopped.
B) The numbers 1 through 10 with one number per line.
C) The numbers 0 through 9 with one number per line.
D) The number 10 to standard output.
A) A continuous stream of numbers increasing in increments of 10 until stopped.
B) The numbers 1 through 10 with one number per line.
C) The numbers 0 through 9 with one number per line.
D) The number 10 to standard output.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
5
Which of the following are tasks handled by a display manager like XDM or KDM?
A) Start and prepare the desktop environment for the user.
B) Configure additional devices like new monitors or projectors when they are attached.
C) Handle the login of a user.
D) Lock the screen when the user was inactive for a configurable amount of time.
E) Create an X11 configuration file for the current graphic devices and monitors.
A) Start and prepare the desktop environment for the user.
B) Configure additional devices like new monitors or projectors when they are attached.
C) Handle the login of a user.
D) Lock the screen when the user was inactive for a configurable amount of time.
E) Create an X11 configuration file for the current graphic devices and monitors.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
6
Which command makes the shell variable named VARIABLE visible to subshells?
A) export $VARIABLE
B) export VARIABLE
C) set $VARIABLE
D) set VARIABLE
E) env VARIABLE
A) export $VARIABLE
B) export VARIABLE
C) set $VARIABLE
D) set VARIABLE
E) env VARIABLE

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
7
After issuing: function myfunction { echo $1 $2 ; } in Bash, which output does: myfunction A B C produce?
A) A B
B) A B C
C) A C
D) B C
E) C B A
A) A B
B) A B C
C) A C
D) B C
E) C B A

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
8
Which of the following commands puts the output of the command date into the shell variable mydate ?
A) mydate="$(date)"
B) mydate="exec date"
C) mydate="$((date))"
D) mydate="date"
E) mydate="${date}"
A) mydate="$(date)"
B) mydate="exec date"
C) mydate="$((date))"
D) mydate="date"
E) mydate="${date}"

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
9
What is the purpose of a screen reader?
A) It reads text displayed on the screen to blind or visually impaired people.
B) It reads the parameters of the attached monitors and creates an appropriate X11 configuration.
C) It displays lines and markers to help people use speed reading techniques.
D) It manages and displays files that contain e-books.
A) It reads text displayed on the screen to blind or visually impaired people.
B) It reads the parameters of the attached monitors and creates an appropriate X11 configuration.
C) It displays lines and markers to help people use speed reading techniques.
D) It manages and displays files that contain e-books.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
10
Which character in the password field of /etc/passwd is used to indicate that the encrypted password is stored in /etc/shadow ?
A) *
B) -
C) s
D) x
A) *
B) -
C) s
D) x

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
11
What is the difference between the commands test -e path and test -f path?
A) They are equivalent options with the same behaviour.
B) The -f option tests for a regular file. The -e option tests for an empty file.
C) Both options check the existence of the path. The -f option also confirms that it is a regular file.
D) The -f option tests for a regular file. The -e option tests for an executable file.
A) They are equivalent options with the same behaviour.
B) The -f option tests for a regular file. The -e option tests for an empty file.
C) Both options check the existence of the path. The -f option also confirms that it is a regular file.
D) The -f option tests for a regular file. The -e option tests for an executable file.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
12
Which of the following commands shows the current color depth of the X Server?
A) xcd
B) xcdepth
C) xwininfo
D) xcolordepth
E) cat /etc/X11
A) xcd
B) xcdepth
C) xwininfo
D) xcolordepth
E) cat /etc/X11

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
13
Which of the following steps prevents a user from obtaining an interactive login session?
A) Run the command chsh -s /bin/false with the user name. Run the command chsh -s /bin/false with the user name.
B) Set the UID for the user to 0.
C) Remove the user from the group staff.
D) Add the user to /etc/noaccess . Add the user to /etc/noaccess .
E) Create a .nologin file in the user's home directory. Create a .nologin file in the user's home directory.
A) Run the command chsh -s /bin/false with the user name. Run the command chsh -s /bin/false with the user name.
B) Set the UID for the user to 0.
C) Remove the user from the group staff.
D) Add the user to /etc/noaccess . Add the user to /etc/noaccess .
E) Create a .nologin file in the user's home directory. Create a .nologin file in the user's home directory.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
14
What is the purpose of the iconv command?
A) It converts bitmap images from one format to another such as PNG to JPEG.
B) It verifies that the root directory tree complies to all conventions from the Filesystem Hierarchy Standard (FHS).
C) It displays additional meta information from icon files ending in .ico.
D) It changes the mode of an inode in the ext4 file system.
E) It converts files from one character encoding to another.
A) It converts bitmap images from one format to another such as PNG to JPEG.
B) It verifies that the root directory tree complies to all conventions from the Filesystem Hierarchy Standard (FHS).
C) It displays additional meta information from icon files ending in .ico.
D) It changes the mode of an inode in the ext4 file system.
E) It converts files from one character encoding to another.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
15
What is the purpose of the file /etc/profile ?
A) It contains the welcome message that is displayed after login.
B) It contains security profiles defining which users are allowed to log in.
C) It contains environment variables that are set when a user logs in.
D) It contains default application profiles for users that run an application for the first time.
A) It contains the welcome message that is displayed after login.
B) It contains security profiles defining which users are allowed to log in.
C) It contains environment variables that are set when a user logs in.
D) It contains default application profiles for users that run an application for the first time.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
16
How is a display manager started?
A) It is started by a user using the command startx.
B) It is started like any other system service by the init system.
C) It is started by inetd when a remote hosts connects to the X11 port.
D) It is started automatically when a X11 user logs in to the system console.
A) It is started by a user using the command startx.
B) It is started like any other system service by the init system.
C) It is started by inetd when a remote hosts connects to the X11 port.
D) It is started automatically when a X11 user logs in to the system console.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
17
When the command echo $$ outputs 12942 , what is the meaning of 12942?
A) It is the process ID of the echo command.
B) It is the process ID of the current shell.
C) It is the process ID of the last command executed.
D) It is the process ID of the last command which has been placed in the background.
A) It is the process ID of the echo command.
B) It is the process ID of the current shell.
C) It is the process ID of the last command executed.
D) It is the process ID of the last command which has been placed in the background.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
18
Which command can be used to delete a group from a Linux system?
A) groupdel
B) groupmod
C) groups
D) groupedit
A) groupdel
B) groupmod
C) groups
D) groupedit

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
19
The X11 configuration file xorg.conf is grouped into sections. How is the content of the section SectionName associated with that section?
A) It is placed in curly brackets as in Section SectionName { ... }. It is placed in curly brackets as in Section SectionName { ... }.
B) It is placed between a line containing Section "SectionName " and a line containing EndSection . It is placed between a line containing Section "SectionName " and a line containing EndSection .
C) It is placed between the tags and It is placed between the tags and
D) It is placed after the row [SectionName] . It is placed after the row [SectionName]
E) It is placed after an initial unindented Section " SectionName" and must be indented by exactly one tab character. It is placed after an initial unindented Section " SectionName" and must be indented by exactly one tab character.
A) It is placed in curly brackets as in Section SectionName { ... }. It is placed in curly brackets as in Section SectionName { ... }.
B) It is placed between a line containing Section "SectionName " and a line containing EndSection . It is placed between a line containing Section "SectionName " and a line containing EndSection .
C) It is placed between the tags
D) It is placed after the row [SectionName] . It is placed after the row [SectionName]
E) It is placed after an initial unindented Section " SectionName" and must be indented by exactly one tab character. It is placed after an initial unindented Section " SectionName" and must be indented by exactly one tab character.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
20
Which of the following are requirements in order to run a shell script like a regular command from anywhere in the filesystem?
A) The user issuing the command must be in the group script.
B) The script file must be found in the $PATH.
C) The script file must have the executable permission bit set.
D) The script must begin with a shebang-line (#!) that points to the correct interpreter.
E) The file system on which the script resides must be mounted with the option scripts.
A) The user issuing the command must be in the group script.
B) The script file must be found in the $PATH.
C) The script file must have the executable permission bit set.
D) The script must begin with a shebang-line (#!) that points to the correct interpreter.
E) The file system on which the script resides must be mounted with the option scripts.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
21
Which commands can be used to change a user's account aging information?
A) usermod
B) passwd
C) chattr
D) chage
E) chsh
A) usermod
B) passwd
C) chattr
D) chage
E) chsh

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
22
What is NOT contained in the locale setting of the operating system?
A) currency symbol
B) language
C) timezone
D) thousands separator
A) currency symbol
B) language
C) timezone
D) thousands separator

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
23
Each entry in a crontab must end with what character?
A) Tab
B) Space
C) Backslash
D) Newline
A) Tab
B) Space
C) Backslash
D) Newline

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
24
To prevent a specific user from scheduling tasks with at, what should the administrator do?
A) Add the specific user to /etc/at.allow file. Add the specific user to /etc/at.allow file.
B) Add the specific user to [deny] section in the /etc/atd.conf file . [deny] section in the /etc/atd.conf file .
C) Add the specific user to /etc/at.deny file . /etc/at.deny file
D) Add the specific user to nojobs group . nojobs group
E) Run the following: atd --deny [user]. Run the following: atd --deny [user].
A) Add the specific user to /etc/at.allow file. Add the specific user to /etc/at.allow file.
B) Add the specific user to [deny] section in the /etc/atd.conf file . [deny] section in the /etc/atd.conf file .
C) Add the specific user to /etc/at.deny file . /etc/at.deny file
D) Add the specific user to nojobs group . nojobs group
E) Run the following: atd --deny [user]. Run the following: atd --deny [user].

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
25
Why is the correct configuration of a system's time zone important?
A) Because the conversion of Unix timestamps to local time relies on the time zone configuration.
B) Because the time zone is saved as part of the modification times of files and cannot be changed after a file is created.
C) Because the environment variables LANG and LC_MESSAGES are, by default, set according to the time zone.
D) Because NTP chooses servers nearby based on the configured time zone.
A) Because the conversion of Unix timestamps to local time relies on the time zone configuration.
B) Because the time zone is saved as part of the modification times of files and cannot be changed after a file is created.
C) Because the environment variables LANG and LC_MESSAGES are, by default, set according to the time zone.
D) Because NTP chooses servers nearby based on the configured time zone.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
26
Where are user specific crontabs stored?
A) In the database file /etc/crontab.db which is shared by all users. In the database file /etc/crontab.db which is shared by all users.
B) As individual per-user files within /var/spool/cron . As individual per-user files within /var/spool/cron .
C) As individual per-user files in /etc/cron.user.d . As individual per-user files in /etc/cron.user.d
D) In the . crontab file in the user's home directory. In the . crontab file in the user's home directory.
E) In the file /var/cron/ user-crontab which is shared by all users. In the file /var/cron/ user-crontab
A) In the database file /etc/crontab.db which is shared by all users. In the database file /etc/crontab.db which is shared by all users.
B) As individual per-user files within /var/spool/cron . As individual per-user files within /var/spool/cron .
C) As individual per-user files in /etc/cron.user.d . As individual per-user files in /etc/cron.user.d
D) In the . crontab file in the user's home directory. In the . crontab file in the user's home directory.
E) In the file /var/cron/ user-crontab which is shared by all users. In the file /var/cron/ user-crontab

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
27
Which of the following is a legacy program provided by CUPS for sending files to the printer queues on the command line?
A) lpd
B) lpp
C) lpq
D) lpr
A) lpd
B) lpp
C) lpq
D) lpr

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
28
Which of the following tasks can be accomplished using the command date?
A) Synchronize the hardware and system clocks.
B) Output date and time in different formats.
C) Set the system clock.
D) Set the hardware clock.
E) Update the time via NTP.
A) Synchronize the hardware and system clocks.
B) Output date and time in different formats.
C) Set the system clock.
D) Set the hardware clock.
E) Update the time via NTP.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
29
Which of the following files assigns a user to its primary group?
A) /etc/pgroup
B) /etc/shadow
C) /etc/group
D) /etc/passwd
E) /etc/gshadow
A) /etc/pgroup
B) /etc/shadow
C) /etc/group
D) /etc/passwd
E) /etc/gshadow

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
30
Which of the following are commonly used Mail Transfer Agent (MTA) applications?
A) Postfix
B) Procmail
C) Sendmail
D) Exim
E) SMTPd
A) Postfix
B) Procmail
C) Sendmail
D) Exim
E) SMTPd

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
31
Which of the following fields can be found in the /etc/group file?
A) The list of users that belong to the group.
B) The home directory of the group.
C) The name of the group.
D) The description of the group.
E) The password of the group.
A) The list of users that belong to the group.
B) The home directory of the group.
C) The name of the group.
D) The description of the group.
E) The password of the group.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
32
Which of the following are syslog facilities?
A) local7
B) mail
C) advanced
D) postmaster
E) remote
A) local7
B) mail
C) advanced
D) postmaster
E) remote

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
33
What is the purpose of the command mailq ?
A) It fetches new emails from a remote server using POP3 or IMAP.
B) It is a multi-user mailing list manager.
C) It is a proprietary tool contained only in the qmail MTA.
D) It queries the mail queue of the local MTA.
E) It is a command-line based tool for reading and writing emails.
A) It fetches new emails from a remote server using POP3 or IMAP.
B) It is a multi-user mailing list manager.
C) It is a proprietary tool contained only in the qmail MTA.
D) It queries the mail queue of the local MTA.
E) It is a command-line based tool for reading and writing emails.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
34
Which of the following parameters are used for journalctl to limit the time frame of the output?
A) --from=
B) --since=
C) --until=
D) --upto=
E) --date=
A) --from=
B) --since=
C) --until=
D) --upto=
E) --date=

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
35
In case neither cron.allow nor cron.deny exist in /etc/ , which of the following is true?
A) Without additional configuration, no users may have user specific crontabs.
B) Without additional configuration, all users may have user specific crontabs.
C) The cron daemon will refuse to start and report missing files in the system's logfile.
D) When a user creates a user specific crontab the system administrator must approve it explicitly.
A) Without additional configuration, no users may have user specific crontabs.
B) Without additional configuration, all users may have user specific crontabs.
C) The cron daemon will refuse to start and report missing files in the system's logfile.
D) When a user creates a user specific crontab the system administrator must approve it explicitly.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
36
Which of the following commands should be added to /etc/bash_profile in order to change the language of messages for an internationalized program to Portuguese (pt)?
A) export LANGUAGE="pt"
B) export MESSAGE="pt"
C) export UI_MESSAGES="pt"
D) export LC_MESSAGES="pt"
E) export ALL_MESSAGES="pt"
A) export LANGUAGE="pt"
B) export MESSAGE="pt"
C) export UI_MESSAGES="pt"
D) export LC_MESSAGES="pt"
E) export ALL_MESSAGES="pt"

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
37
What is true regarding the command userdel --force --remove bob ?
A) The user bob is removed from the system's user database.
B) The user bob's home directory is removed.
C) The locate database is updated to drop files owned by bob.
D) All files owned by bob are remove from all mounted filesystems.
E) In case bob was the last member of a group, that group is deleted.
A) The user bob is removed from the system's user database.
B) The user bob's home directory is removed.
C) The locate database is updated to drop files owned by bob.
D) All files owned by bob are remove from all mounted filesystems.
E) In case bob was the last member of a group, that group is deleted.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
38
Which file contains the date of the last change of a user's password?
A) /etc/gshadow
B) /etc/passwd
C) /etc/pwdlog
D) /etc/shadow
E) /var/log/shadow
A) /etc/gshadow
B) /etc/passwd
C) /etc/pwdlog
D) /etc/shadow
E) /var/log/shadow

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
39
Which of the following is observed and corrected by a NTP client?
A) The skew in time between the system clock and the hardware clock.
B) The skew in time between the system clock and the reference clock.
C) Changes in the time zone of the current computer's location.
D) Adjustments needed to support Daylight Saving Time.
A) The skew in time between the system clock and the hardware clock.
B) The skew in time between the system clock and the reference clock.
C) Changes in the time zone of the current computer's location.
D) Adjustments needed to support Daylight Saving Time.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
40
Which of the following commands can remove a user from a group?
A) grouprm
B) groupmod
C) passwd
D) usergroups
E) usermod
A) grouprm
B) groupmod
C) passwd
D) usergroups
E) usermod

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
41
Given the following routing table: 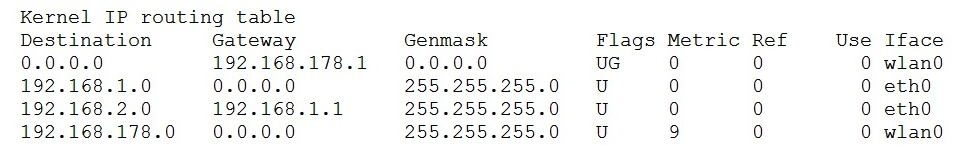 How would an outgoing packet to the destination 192.168.2.150 be handled?
How would an outgoing packet to the destination 192.168.2.150 be handled?
A) It would be passed to the default router 192.168.178.1 on wlan0.
B) It would be directly transmitted on the device eth0.
C) It would be passed to the default router 255.255.255.0 on eth0.
D) It would be directly transmitted on the device wlan0.
E) It would be passed to the router 192.168.1.1 on eth0.
 How would an outgoing packet to the destination 192.168.2.150 be handled?
How would an outgoing packet to the destination 192.168.2.150 be handled?A) It would be passed to the default router 192.168.178.1 on wlan0.
B) It would be directly transmitted on the device eth0.
C) It would be passed to the default router 255.255.255.0 on eth0.
D) It would be directly transmitted on the device wlan0.
E) It would be passed to the router 192.168.1.1 on eth0.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
42
Which of the following programs can be used to determine the routing path to a given destination?
A) dig
B) netstat
C) ping
D) route
E) traceroute
A) dig
B) netstat
C) ping
D) route
E) traceroute

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
43
Which of the following IPv4 networks are reserved by IANA for private address assignment and private routing?
A) 127.0.0.0/8
B) 10.0.0.0/8
C) 169.255.0.0/16
D) 172.16.0.0/12
E) 192.168.0.0/16
A) 127.0.0.0/8
B) 10.0.0.0/8
C) 169.255.0.0/16
D) 172.16.0.0/12
E) 192.168.0.0/16

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
44
Which configuration file would be edited to change the default options for outbound SSH sessions?
A) /etc/ssh/sshd_config
B) /etc/ssh/ssh
C) /etc/ssh/client
D) /etc/ssh/ssh_config
E) /etc/ssh/ssh_client
A) /etc/ssh/sshd_config
B) /etc/ssh/ssh
C) /etc/ssh/client
D) /etc/ssh/ssh_config
E) /etc/ssh/ssh_client

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
45
What is the purpose of the nsswitch.conf file?
A) It is used to configure where the C library looks for system information such as host names and user passwords.
B) It is used to configure network protocol port numbers such as for HTTP or SMTP.
C) It is used to configure LDAP authentication services for the local system.
D) It is used to configure which network services will be turned on during the next system boot.
A) It is used to configure where the C library looks for system information such as host names and user passwords.
B) It is used to configure network protocol port numbers such as for HTTP or SMTP.
C) It is used to configure LDAP authentication services for the local system.
D) It is used to configure which network services will be turned on during the next system boot.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
46
Which of the following details is NOT provided in any output from the netstat utility?
A) broadcast services
B) interface statistics
C) masquerading connections
D) network connections
E) routing tables
A) broadcast services
B) interface statistics
C) masquerading connections
D) network connections
E) routing tables

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
47
Which of the following is true about IPv6?
A) With IPv6, the TCP port numbers of most services have changed.
B) IPv6 no longer supports broadcast addresses.
C) IPv4 addresses can be used without any change with IPv6.
D) IPv6 no longer supports multicast addresses.
E) For IPv6, UDP and TCP have been replaced by the Rapid Transmission Protocol RTP.
A) With IPv6, the TCP port numbers of most services have changed.
B) IPv6 no longer supports broadcast addresses.
C) IPv4 addresses can be used without any change with IPv6.
D) IPv6 no longer supports multicast addresses.
E) For IPv6, UDP and TCP have been replaced by the Rapid Transmission Protocol RTP.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
48
What is true regarding a default route?
A) The default route is always used first. When the default route is not available more specific routes are tried.
B) When a default route is set, all other routes are disabled until the default route is deleted.
C) The default route is only used if there is not a more specific route to a destination host or network.
D) Without a default route, no network communication even in directly attached networks is possible.
A) The default route is always used first. When the default route is not available more specific routes are tried.
B) When a default route is set, all other routes are disabled until the default route is deleted.
C) The default route is only used if there is not a more specific route to a destination host or network.
D) Without a default route, no network communication even in directly attached networks is possible.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
49
Which of the following commands is used to rotate, compress, and mail system logs?
A) rotatelog
B) striplog
C) syslogd --rotate
D) logrotate
E) logger
A) rotatelog
B) striplog
C) syslogd --rotate
D) logrotate
E) logger

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
50
What is true about the ntpdate command?
A) It is the primary management command for the NTP time server.
B) It updates the local system's date (i.e. day, month and year) but not the time (i.e. hours, minutes, seconds).
C) It queries one or more NTP time servers and adjusts the system time accordingly.
D) It sends the local system time to one or many remote NTP time servers for redistribution.
E) It can be used by any user to set the user clock independently of the system clock.
A) It is the primary management command for the NTP time server.
B) It updates the local system's date (i.e. day, month and year) but not the time (i.e. hours, minutes, seconds).
C) It queries one or more NTP time servers and adjusts the system time accordingly.
D) It sends the local system time to one or many remote NTP time servers for redistribution.
E) It can be used by any user to set the user clock independently of the system clock.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
51
Which command is used to set restrictions on the size of a core file that is created for a user when a program crashes?
A) core
B) edquota
C) ulimit
D) quota
A) core
B) edquota
C) ulimit
D) quota

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
52
Which of the following may occur as a consequence of using the command ifconfig ?
A) New name servers may be added to the resolver configuration.
B) Network interfaces may become active or inactive.
C) The routing table may change.
D) IP addresses may change.
E) The system's host name may change.
A) New name servers may be added to the resolver configuration.
B) Network interfaces may become active or inactive.
C) The routing table may change.
D) IP addresses may change.
E) The system's host name may change.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
53
Which of the following commands can be used to display the local routing table?
A) ifconfig
B) dig
C) netstat
D) route
E) trackroute
A) ifconfig
B) dig
C) netstat
D) route
E) trackroute

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
54
What is true regarding TCP port 23?
A) Port 23 is the well known port for the telnet service which is a plain text protocol that should no longer be used.
B) Port 23 is the well known port for the SSH service which provides secure logins.
C) Port 23 is the well known port for the rlogin service which is SSL secured by default.
D) Port 23 is the well known port for the system login services which are encrypted when the user runs the starttls command in his login shell.
A) Port 23 is the well known port for the telnet service which is a plain text protocol that should no longer be used.
B) Port 23 is the well known port for the SSH service which provides secure logins.
C) Port 23 is the well known port for the rlogin service which is SSL secured by default.
D) Port 23 is the well known port for the system login services which are encrypted when the user runs the starttls command in his login shell.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
55
Which of the following tools used for DNS debugging, reports not only the response from the name server but also details about the query?
A) dnsq
B) dig
C) hostname
D) dnslookup
E) zoneinfo
A) dnsq
B) dig
C) hostname
D) dnslookup
E) zoneinfo

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
56
Which of the following is a valid IPv6 address?
A) 2001:db8:3241::1
B) 2001::db8:4581::1
C) 2001:db8:0g41::1
D) 2001%db8%9990%%1
E) 2001.db8.819f..1
A) 2001:db8:3241::1
B) 2001::db8:4581::1
C) 2001:db8:0g41::1
D) 2001%db8%9990%%1
E) 2001.db8.819f..1

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
57
Which of the following statements is valid in the file /etc/nsswitch.conf ?
A) multi on
B) 192.168.168.4 dns-server
C) hosts: files dns
D) include /etc/nsswitch.d/
A) multi on
B) 192.168.168.4 dns-server
C) hosts: files dns
D) include /etc/nsswitch.d/

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
58
Which of the following keywords can be used in the file /etc/resolv.conf ?
A) substitute
B) nameserver
C) search
D) lookup
E) method
A) substitute
B) nameserver
C) search
D) lookup
E) method

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
59
Which of the following lines are valid in the file /etc/hosts ?
A) 2001:db8::15 www.example.com www
B) www.example.com www 203.0.13.15
C) 203.0.113.15 www.example.com www
D) www.example.com,www 203.0.13.15,2001:db8::15
E) 2003.0.113.15,2001:db8::15 www.example.com www
A) 2001:db8::15 www.example.com www
B) www.example.com www 203.0.13.15
C) 203.0.113.15 www.example.com www
D) www.example.com,www 203.0.13.15,2001:db8::15
E) 2003.0.113.15,2001:db8::15 www.example.com www

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
60
On a regular users workstation the route command takes a long time before printing out the routing table. Which of the following errors does that indicate?
A) The local routing information may be corrupted and must be re-validated using a routing protocol.
B) One of the routers in the routing table is not available which causes the automatic router failure detection mechanism (ARF-D) to wait for a timeout.
C) There may accidentally be more than one default router in which case a default router election has to be done on the network in order to choose one router as the default.
D) DNS resolution may not be working as route by default tries to resolve names of routers and destinations and may run into a timeout.
A) The local routing information may be corrupted and must be re-validated using a routing protocol.
B) One of the routers in the routing table is not available which causes the automatic router failure detection mechanism (ARF-D) to wait for a timeout.
C) There may accidentally be more than one default router in which case a default router election has to be done on the network in order to choose one router as the default.
D) DNS resolution may not be working as route by default tries to resolve names of routers and destinations and may run into a timeout.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
61
What is a purpose of an SSH host key?
A) It must be sent by any SSH client in addition to a user key in order to identify the client's host.
B) It provides the server's identity information to connecting SSH clients.
C) It is the root key by which all user SSH keys must be signed.
D) It authenticates any user that logs into a remote machine from the key's host.
E) It is used by system services like cron, syslog or a backup job to automatically connect to remote hosts.
A) It must be sent by any SSH client in addition to a user key in order to identify the client's host.
B) It provides the server's identity information to connecting SSH clients.
C) It is the root key by which all user SSH keys must be signed.
D) It authenticates any user that logs into a remote machine from the key's host.
E) It is used by system services like cron, syslog or a backup job to automatically connect to remote hosts.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
62
When the command echo $ outputs 1, which of the following statements is true?
A) It is the process ID of the echo command.
B) It is the process ID of the current shell.
C) It is the exit value of the command executed immediately before echo.
D) It is the exit value of the echo command.
A) It is the process ID of the echo command.
B) It is the process ID of the current shell.
C) It is the exit value of the command executed immediately before echo.
D) It is the exit value of the echo command.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
63
SIMULATION What word is missing from the following SQL statement? __________ count(*) from tablename; (Please specify the missing word using lower-case letters only.)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
64
The X11 configuration file xorg.conf is grouped into sections. How is the content of the section SectionName associated with that section?
A) It is placed in curly brackets as in Section SectionName { ... }.
B) It is placed between a line containing Section "SectionName" and a line containing EndSection.
C) It is placed between the tags and
D) It is placed after the row [SectionName].
E) It is placed after an initial unindented Section "SectionName" and must be indented by exactly one tab character.
A) It is placed in curly brackets as in Section SectionName { ... }.
B) It is placed between a line containing Section "SectionName" and a line containing EndSection.
C) It is placed between the tags
D) It is placed after the row [SectionName].
E) It is placed after an initial unindented Section "SectionName" and must be indented by exactly one tab character.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
65
For accessibility assistance, which of the following programs is an on-screen keyboard?
A) xkb
B) atkb
C) GOK
D) xOSK
A) xkb
B) atkb
C) GOK
D) xOSK

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
66
Which configuration file would be edited to change default options for the OpenSSH server?
A) /etc/ssh/sshd_config
B) /etc/ssh/ssh
C) /etc/ssh/server
D) /etc/ssh/ssh_config
E) /etc/ssh/ssh_server
A) /etc/ssh/sshd_config
B) /etc/ssh/ssh
C) /etc/ssh/server
D) /etc/ssh/ssh_config
E) /etc/ssh/ssh_server

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
67
When trying to unmount a device it is reported as being busy. Which of the following commands could be used to determine which process is causing this?
A) debug
B) lsof
C) nessus
D) strace
E) traceroute
A) debug
B) lsof
C) nessus
D) strace
E) traceroute

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
68
Which of the following are requirements in order to run a shell script like a regular command from anywhere in the filesystem?
A) The user issuing the command must be in the group script.
B) The script file must be found in the $PATH.
C) The script file must have the executable permission bit set.
D) The script must begin with a shebang-line (#!) that points to the correct interpreter.
E) The file system on which the script resides must be mounted with the option scripts.
A) The user issuing the command must be in the group script.
B) The script file must be found in the $PATH.
C) The script file must have the executable permission bit set.
D) The script must begin with a shebang-line (#!) that points to the correct interpreter.
E) The file system on which the script resides must be mounted with the option scripts.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
69
SIMULATION Which command can be used to investigate the properties for a particular window in X by clicking that window? (Specify ONLY the command without any path or parameters.)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
70
Which of the following are tasks handled by a display manager like XDM or KDM?
A) Start and prepare the desktop environment for the user.
B) Configure additional devices like new monitors or projectors when they are attached.
C) Handle the login of a user.
D) Lock the screen when the user was inactive for a configurable amount of time.
E) Create an X11 configuration file for the current graphic devices and monitors.
A) Start and prepare the desktop environment for the user.
B) Configure additional devices like new monitors or projectors when they are attached.
C) Handle the login of a user.
D) Lock the screen when the user was inactive for a configurable amount of time.
E) Create an X11 configuration file for the current graphic devices and monitors.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
71
SIMULATION What is the name of the simple graphical login manager that comes with a vanilla X11 installation? (Specify ONLY the command without any path or parameters.)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
72
Which of the following SQL queries counts the number of occurrences for each value of the field order_type in the table orders?
A) SELECT order_type,COUNT(*) FROM orders WHERE order_type=order_type;
B) SELECT order_type,COUNT(*) FROM orders GROUP BY order_type;
C) COUNT(SELECT order_type FROM orders);
D) SELECT COUNT(*) FROM orders ORDER BY order_type;
E) SELECT AUTO_COUNT FROM orders COUNT order_type;
A) SELECT order_type,COUNT(*) FROM orders WHERE order_type=order_type;
B) SELECT order_type,COUNT(*) FROM orders GROUP BY order_type;
C) COUNT(SELECT order_type FROM orders);
D) SELECT COUNT(*) FROM orders ORDER BY order_type;
E) SELECT AUTO_COUNT FROM orders COUNT order_type;

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
73
SIMULATION What word is missing from the following SQL statement? insert into tablename ________(909, 'text'); (Please specify the missing word using lower-case letters only.)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
74
SIMULATION By default, the contents of which directory will be copied to a new user's home directory when the account is created by passing the -m option to the useradd command? (Specify the full path to the directory.)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
75
Which of the following files, when existing, affect the behavior of the Bash shell?
A) ~/.bashconf
B) ~/.bashrc
C) ~/.bashdefaults
D) ~/.bash_etc
E) ~/.bash_profile
A) ~/.bashconf
B) ~/.bashrc
C) ~/.bashdefaults
D) ~/.bash_etc
E) ~/.bash_profile

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
76
SIMULATION What command displays all aliases defined in the current shell? (Specify the command without any path information)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
77
SIMULATION What is the default name of the configuration file for the Xorg X11 server? (Specify the file name only without any path.)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
78
Which of the following commands can be used to limit the amount of memory a user may use?
A) umask
B) usermod
C) ulimit
D) passwd
E) chage
A) umask
B) usermod
C) ulimit
D) passwd
E) chage

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
79
Which of the following words is used to restrict the records that are returned from a SELECT SQL query based on a supplied criteria for the values in the records?
A) CASE
B) FROM
C) WHERE
D) IF
A) CASE
B) FROM
C) WHERE
D) IF

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck
80
How can the existing environment variable FOOBAR be suppressed for the execution of the script./myscript only?
A) unset -v FOOBAR;./myscript
B) set -a FOOBAR="";./myscript
C) env -u FOOBAR./myscript
D) env -i FOOBAR./myscript
A) unset -v FOOBAR;./myscript
B) set -a FOOBAR="";./myscript
C) env -u FOOBAR./myscript
D) env -i FOOBAR./myscript

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 106 في هذه المجموعة.
فتح الحزمة
k this deck








