Deck 8: Architecting a Citrix Networking Solution
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/36
العب
ملء الشاشة (f)
Deck 8: Architecting a Citrix Networking Solution
1
Scenario: A Citrix Architect needs to assess an existing NetScaler gateway deployment. During the assessment, the architect collected key requirements for VPN users, as well as the current session profile settings that are applied to those users. Click the Exhibit button to view the information collected by the architect. 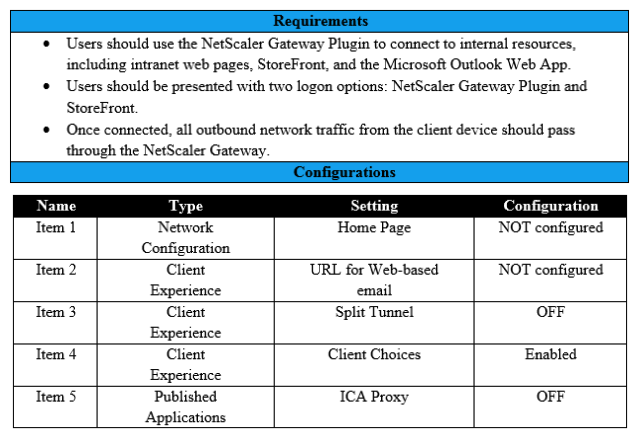 Which configuration should the architect change to meet all the stated requirements?
Which configuration should the architect change to meet all the stated requirements?
A) Item 5
B) Item 1
C) Item 2
D) Item 3
E) Item 4
 Which configuration should the architect change to meet all the stated requirements?
Which configuration should the architect change to meet all the stated requirements?A) Item 5
B) Item 1
C) Item 2
D) Item 3
E) Item 4
Item 5
2
Scenario : A Citrix Architect needs to design a NetScaler deployment in Microsoft Azure. An Active-Passive NetScaler VPX pair will provide load balancing for three distinct web applications. The architect has identified the following requirements: Minimize deployment costs where possible. Provide dedicated bandwidth for each web application. Provide a different public IP address for each web application. For this deployment, the architect should configure each NetScaler VPX machine to have ______ network interface(s) and configure IP address by using ________. (Choose the correct option to complete the sentence).
A) 4; Port Address Translation
B) 1; Network Address Translation
C) 1; Port Address Translation
D) 2; Network Address Translation
E) 4; Network Address Translation
F) 2; Port Address Translation
A) 4; Port Address Translation
B) 1; Network Address Translation
C) 1; Port Address Translation
D) 2; Network Address Translation
E) 4; Network Address Translation
F) 2; Port Address Translation
1; Port Address Translation
3
Scenario : A Citrix Architect needs to deploy three VPX instances on NetScaler SDX 11500 device to meet the following design requirements: Three (3) VPX instances must be provisioned on the SDX device. Instance 1 must be utilized for deploying NetScaler Gateway virtual server. Instance 2 must be utilized for deploying load balancing virtual servers for XML, Director, StoreFront, and Active Directory servers. Separate IP address must be utilized for the communication with XenApp environment and LDAP communication. Instance 3 must be used for deploying the test environment. In the test environment, NetScaler Gateway virtual server, load balancing virtual servers for XML, Director, StoreFront and Active Directory servers must be configured. How many IP addresses will be required to meet these design requirements?
A) 14
B) 20
C) 16
D) 18
A) 14
B) 20
C) 16
D) 18
18
4
Scenario: A Citrix Architect needs to design a hybrid XenApp and XenDesktop environment which will include as well as resource locations in an on-premises datacenter and Microsoft Azure. Organizational details and requirements are as follows: Active XenApp and XenDesktop Service subscription No existing NetScaler deployment Minimization of additional costs All users should correct directly to the resource locations containing the servers which will host HDX sessions Click the Exhibit button to view the conceptual environment architecture. 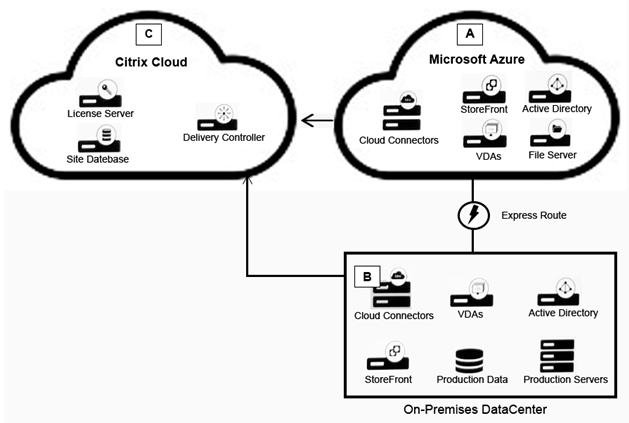 The architect should use___________ in Location A, and should use _______________ in Location B. (Choose the correct option to complete the sentence.)
The architect should use___________ in Location A, and should use _______________ in Location B. (Choose the correct option to complete the sentence.)
A) No NetScaler products; NetScaler ICA Proxy (cloud-licensed)
B) NetScaler Gateway as a Service; NetScaler ICA Proxy (cloud-licensed)
C) NetScaler Gateway as a Service; no NetScaler products
D) No NetScaler products; NetScaler Gateway appliance
E) NetScaler gateway as a Service; NetScaler ADC (BYO)
 The architect should use___________ in Location A, and should use _______________ in Location B. (Choose the correct option to complete the sentence.)
The architect should use___________ in Location A, and should use _______________ in Location B. (Choose the correct option to complete the sentence.)A) No NetScaler products; NetScaler ICA Proxy (cloud-licensed)
B) NetScaler Gateway as a Service; NetScaler ICA Proxy (cloud-licensed)
C) NetScaler Gateway as a Service; no NetScaler products
D) No NetScaler products; NetScaler Gateway appliance
E) NetScaler gateway as a Service; NetScaler ADC (BYO)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
5
Scenario: Based on a discussion between a Citrix Architect and a team of Workspacelab members, the MPX Logical layout for Workspacelab has been created across three (3) sites. The requirements captured during the design discussion held for a NetScaler design project are as follows: Two (2) pairs of NetScaler MPX appliances deployed in the DMZ and internal network. High Availability will be accessible for each NetScaler MPX The external NetScaler MPX appliance will be deployed in multi-arm mode. The internal NetScaler MPX will be deployed in single-arm mode wherein it will be connected to Cisco ACI Fabric. All three (3) Workspacelab sites: Dc, NDR and DR, will have similar NetScaler configurations and design. How many NetScaler MPX appliances should the architect deploy at each site to meet the design requirements above?
A) 4
B) 12
C) 6
D) 2
A) 4
B) 12
C) 6
D) 2

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
6
Scenario: Based on a discussion between a Citrix Architect and a team of Workspacelab members, the MPX Logical layout for Workspacelab has been created across three (3) sites. They captured the following requirements during the design discussion held for a NetScaler design project: All three (3) Workspacelab sites (DC, NDR, and DR) will have similar NetScaler configurations and design. Both external and internal NetScaler MPX appliances will have Global Server Load Balancing (GSLB) configured and deployed in Active/Passive mode. GSLB should resolve both A and AAA DNS queries. In the GSLB deployment, the NDR site will act as backup for the DC site, whereas the DR site will act as backup for the NDR site. When the external NetScaler replies to DNS traffic coming in through Cisco Firepower IPS, the replies should be sent back through the same path. On the internal NetScaler, both the front-end VIP and backend SNIP will be part of the same subnet. The external NetScaler will act as default gateway for the backend servers. All three (3) sites, DC, NDR, and DR, will have two (2) links to the Internet from different service providers configured in Active/Standby mode. Which design decision must the architect make the design requirements above?
A) MAC-based Forwarding must be enabled on the External NetScaler Pair.
B) NSIP of the External NetScaler must be configured as the default gateway on the backend servers.
C) The Internal NetScaler must be deployed in Transparent mode.
D) The ADNS service must be configured with an IPv6 address.
A) MAC-based Forwarding must be enabled on the External NetScaler Pair.
B) NSIP of the External NetScaler must be configured as the default gateway on the backend servers.
C) The Internal NetScaler must be deployed in Transparent mode.
D) The ADNS service must be configured with an IPv6 address.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
7
Which parameter indicates the number of current users logged on to the NetScaler gateway?
A) ICA connections
B) Total Connected Users
C) Active user session
D) Maximum User session
A) ICA connections
B) Total Connected Users
C) Active user session
D) Maximum User session

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
8
Scenario : A Citrix Architect needs to assess an existing NetScaler multi-site deployment. The deployment is using Global Server Load Balancing (GSLB) configured in a parent-child configuration. Click the Exhibit button to view the diagram of the current GSLB configuration and parent-child relationships, as well as the status of the sites and the connectivity between them. 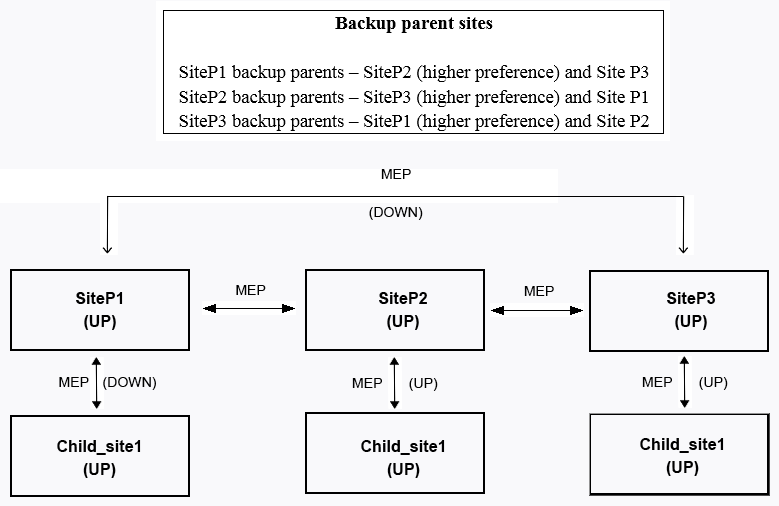 Based on the displayed configuration and status, Chil_site1_______ a connection from _______. (Choose the correct option to complete the sentence.)
Based on the displayed configuration and status, Chil_site1_______ a connection from _______. (Choose the correct option to complete the sentence.)
A) rejects; SiteP2 and SiteP3; remains a child site of SiteP1
B) rejects; SiteP3; remains a child site of SiteP1
C) accepts; SiteP3; becomes its child site
D) accepts; SiteP2; becomes its child site
E) does NOT receive; SiteP2 and SiteP3; remains a child site of SiteP1
F) rejects; SiteP2; remains a child site of SiteP1
 Based on the displayed configuration and status, Chil_site1_______ a connection from _______. (Choose the correct option to complete the sentence.)
Based on the displayed configuration and status, Chil_site1_______ a connection from _______. (Choose the correct option to complete the sentence.)A) rejects; SiteP2 and SiteP3; remains a child site of SiteP1
B) rejects; SiteP3; remains a child site of SiteP1
C) accepts; SiteP3; becomes its child site
D) accepts; SiteP2; becomes its child site
E) does NOT receive; SiteP2 and SiteP3; remains a child site of SiteP1
F) rejects; SiteP2; remains a child site of SiteP1

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
9
Scenario: A Citrix Architect needs to deploy a load balancing for an application server on the NetScaler. The authentication must be performed on the NetScaler. After the authentication, the Single Sign-on with the application servers must be performed using Kerberos impersonation. Which three authentication methods can the Architect utilize to gather the credentials from the user in this scenario? (Choose three.)
A) SAML
B) OTP
C) TACACS
D) WEBAUTH
E) LDAP
A) SAML
B) OTP
C) TACACS
D) WEBAUTH
E) LDAP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
10
Scenario: A Citrix Architect needs to assess an existing on-premises NetScaler deployment which includes Advanced Endpoint Analysis scans. During a previous security audit, the team discovered that certain endpoint devices were able to perform unauthorized actions despite NOT meeting pre-established criteria. The issue was isolated to several endpoint analysis (EPA) scan settings. Click the Exhibit button to view the endpoint security requirements and configured EPA policy settings. 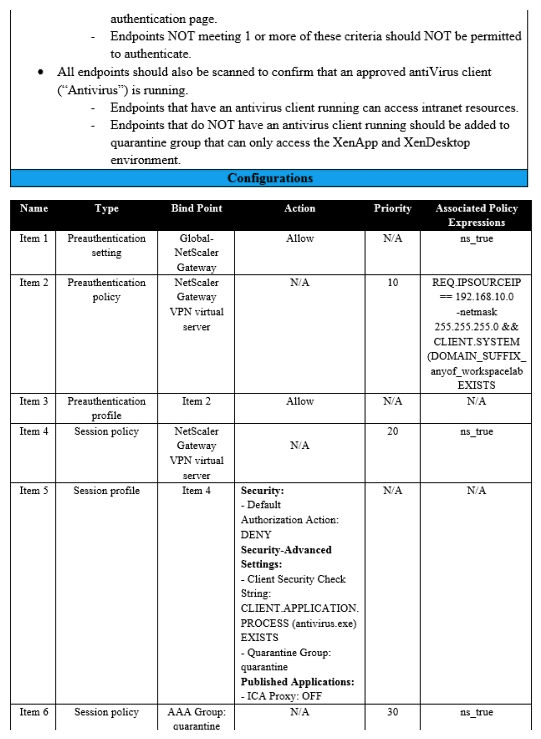 Which setting is preventing the security requirements of the organization from being met?
Which setting is preventing the security requirements of the organization from being met?
A) Item 6
B) Item 7
C) Item 1
D) Item 3
E) Item 5
F) Item 2
G) Item 4
 Which setting is preventing the security requirements of the organization from being met?
Which setting is preventing the security requirements of the organization from being met?A) Item 6
B) Item 7
C) Item 1
D) Item 3
E) Item 5
F) Item 2
G) Item 4

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
11
Scenario: A Citrix Architect needs to deploy SAML integration between NetScaler (Identity Provider) and ShareFile (Service Provider). The design requirements for SAML setup are as follows: NetScaler must be deployed as the Identity Provider (IDP). ShareFile server must be deployed as the SAML Service Provider (SP). The users in domain workspacelab.com must be able to perform Single Sign-on to ShareFile after authenticating at the NetScaler. The User ID must be UserPrincipalName. The User ID and Password must be evaluated by NetScaler against the Active Directory servers SFO-ADS-001 and SFO-ADS-002. After successful authentication, NetScaler creates a SAML Assertion and passes it back to ShareFile. Single Sign-on must be performed. SHA 1 algorithm must be utilized. The verification environment details are as follows: Domain Name: workspacelab.com NetScaler AAA virtual server URL https://auth.workspacelab.com ShareFile URL https://sharefile.workspacelab.com Which SAML IDP action will meet the design requirements?
A) add authentication samIIdPProfile SAMI-IDP -samISPCertName Cert_1 -samIIdPCertName Cert_2 -assertionConsimerServiceURL "https://auth.workspacelab.com/samIIssueName auth.workspacelab.com -signatureAlg RSA-SHA256-digestMethod SHA256-encryptAssertion ON -serviceProviderUD sharefile.workspacelad.com
B) add authentication samIIdPProfile SAMI-IDP -samISPCertName Cert_1 -samIIdPCertName Cert_2 -assertionConsimerServiceURL https://sharefile.workspacelab.com/saml/acs" -samIIssuerName sharefile.workspacelab.com -signatureAlg RSA-SHA256 -digestMethod SHA256 -serviceProviderID sharefile.workspacelab.com
C) add authentication samIIdPProfile SAMI-IDP -samISPCertName Cert_1 -samIIdPCertName Cert_2 -assertionConsimerServiceURL https://sharefile.workspacelab.com/saml/acs" -samIIssuerName auth.workspacelab.com -signatureAlg RSA-SHA1-digestMethod SHA1 -encryptAssertion ON -serviceProviderID sharefile.workspacelab.com
D) add authentication samIIdPProfile SAMI-IDP -samISPCertName Cert_1 -samIIdPCertName Cert_2 -assertionConsimerServiceURL https://sharefile.workspacelab.com/saml/acs" -samIIssuerName sharefile.workspacelab.com -signatureAlg RSA-SHA1 -digestMethod SHA1 -encryptAssertion ON -serviceProviderID sharefile.workspacelab.com
A) add authentication samIIdPProfile SAMI-IDP -samISPCertName Cert_1 -samIIdPCertName Cert_2 -assertionConsimerServiceURL "https://auth.workspacelab.com/samIIssueName auth.workspacelab.com -signatureAlg RSA-SHA256-digestMethod SHA256-encryptAssertion ON -serviceProviderUD sharefile.workspacelad.com
B) add authentication samIIdPProfile SAMI-IDP -samISPCertName Cert_1 -samIIdPCertName Cert_2 -assertionConsimerServiceURL https://sharefile.workspacelab.com/saml/acs" -samIIssuerName sharefile.workspacelab.com -signatureAlg RSA-SHA256 -digestMethod SHA256 -serviceProviderID sharefile.workspacelab.com
C) add authentication samIIdPProfile SAMI-IDP -samISPCertName Cert_1 -samIIdPCertName Cert_2 -assertionConsimerServiceURL https://sharefile.workspacelab.com/saml/acs" -samIIssuerName auth.workspacelab.com -signatureAlg RSA-SHA1-digestMethod SHA1 -encryptAssertion ON -serviceProviderID sharefile.workspacelab.com
D) add authentication samIIdPProfile SAMI-IDP -samISPCertName Cert_1 -samIIdPCertName Cert_2 -assertionConsimerServiceURL https://sharefile.workspacelab.com/saml/acs" -samIIssuerName sharefile.workspacelab.com -signatureAlg RSA-SHA1 -digestMethod SHA1 -encryptAssertion ON -serviceProviderID sharefile.workspacelab.com

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
12
Which two features are supported on LbaaSV1? (Choose two.)
A) Cookie Insertion
B) Layer 7 Load Balancing
C) Certificate Bundle
D) Layer 4 Load balancing
E) Server name Indicator
A) Cookie Insertion
B) Layer 7 Load Balancing
C) Certificate Bundle
D) Layer 4 Load balancing
E) Server name Indicator

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
13
Scenario: A Citrix Architect needs to assess an existing on-premises NetScaler deployment which includes Advanced Endpoint Analysis scans. During a previous security audit, the team discovered that certain endpoint devices were able to perform unauthorized actions despite NOT meeting pre-established criteria. The issue was isolated to several endpoint analysis (EPA) scan settings. Click the Exhibit button to view the endpoint security requirements and configured EPA policy settings. 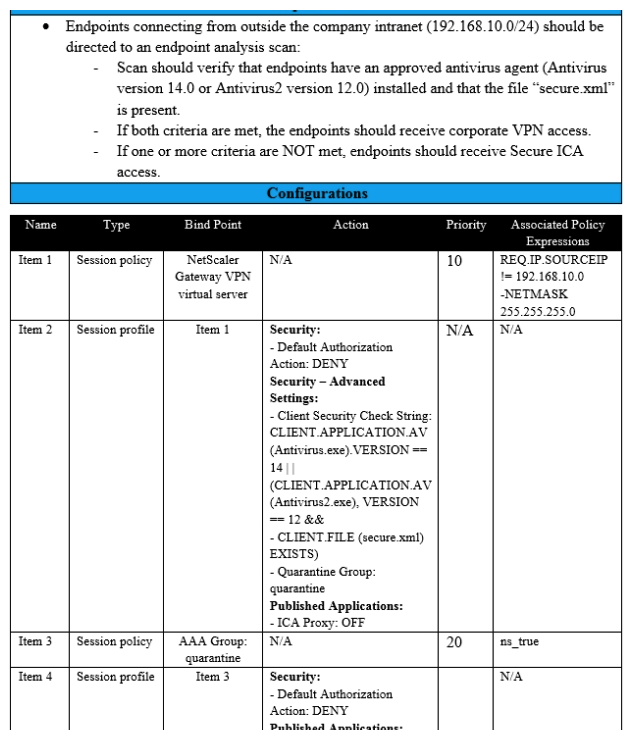 Which setting is preventing the security requirements of the organization from being met?
Which setting is preventing the security requirements of the organization from being met?
A) Item 1
B) Item 4
C) Item 2
D) Item 3
 Which setting is preventing the security requirements of the organization from being met?
Which setting is preventing the security requirements of the organization from being met?A) Item 1
B) Item 4
C) Item 2
D) Item 3

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
14
Scenario: A Citrix Architect needs to assess an existing NetScaler Gateway deployment. During the assessment, the architect collected key requirements for VPN users, as well as the current session profile settings that are applied to those users. Click the Exhibit button to view the information collected by the architect. 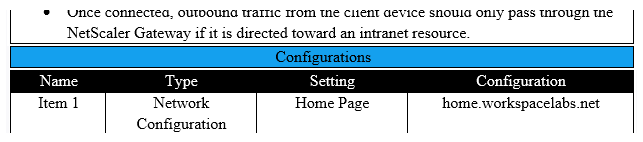 Which configurations should the architect change to meet all the stated requirements?
Which configurations should the architect change to meet all the stated requirements?
A) Item 4
B) Item 3
C) Item 5
D) Item 2
E) Item 1
 Which configurations should the architect change to meet all the stated requirements?
Which configurations should the architect change to meet all the stated requirements?A) Item 4
B) Item 3
C) Item 5
D) Item 2
E) Item 1

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
15
Which encoding type can a Citrix Architect use to encode the StyleBook content, when importing the StyleBook configuration under source attribute?
A) Hex
B) base64
C) URL
D) Unicode
A) Hex
B) base64
C) URL
D) Unicode

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
16
Scenario: A Citrix Architect needs to design a new NetScaler Gateway deployment to provide secure RDP access to backend Windows machines. Click the Exhibit button to view additional requirements collected by the architect during the design discussions. 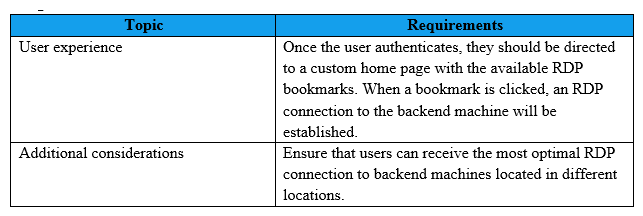 To meet the customer requirements, the architect should deploy the RDP proxy through ______ using a________ solution. (Choose the correct option to complete the sentence.)
To meet the customer requirements, the architect should deploy the RDP proxy through ______ using a________ solution. (Choose the correct option to complete the sentence.)
A) CVPN: single gateway
B) CVPN, stateless gateway
C) ICAProxy: single gateway
D) ICAProxy; stateless gateway
 To meet the customer requirements, the architect should deploy the RDP proxy through ______ using a________ solution. (Choose the correct option to complete the sentence.)
To meet the customer requirements, the architect should deploy the RDP proxy through ______ using a________ solution. (Choose the correct option to complete the sentence.)A) CVPN: single gateway
B) CVPN, stateless gateway
C) ICAProxy: single gateway
D) ICAProxy; stateless gateway

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
17
Scenario: The Workspacelab team has configured their NetScaler Management and Analytics (NMAS) environment. A Citrix Architect needs to log on to the NMAS to check the settings. Which two authentication methods are supported to meet this requirement? (Choose two.)
A) Certificate
B) RADIUS
C) TACACS
D) Director
E) SAML
F) AAA
A) Certificate
B) RADIUS
C) TACACS
D) Director
E) SAML
F) AAA

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
18
Which parameter must a Citrix Architect configure to ensure that HDX Proxy Connection terminates upon AAA Session TimeOut?
A) ICA session timeout in VPN parameters
B) Session timeout(mins) in NetScaler gateway Session Profile.
C) Session timeout(mins) in VPN Parameters
D) ICA session timeout in netScaler Gateway Session Profile.
A) ICA session timeout in VPN parameters
B) Session timeout(mins) in NetScaler gateway Session Profile.
C) Session timeout(mins) in VPN Parameters
D) ICA session timeout in netScaler Gateway Session Profile.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
19
Scenario: A Citrix Architect needs to design a hybrid XenApp and XenDesktop environment which will include Citrix Cloud as well as resource locations in an on-premises datacenter and Microsoft Azure. Organizational details and requirements are as follows: Active XenApp and XenDesktop Service subscription No existing NetScaler deployment Global Server Load Balancing is used to direct connection requests to Location B, if the StoreFront server in Location B fails, connections should be directed to Location A. Click the Exhibit button to view the conceptual environment architecture. 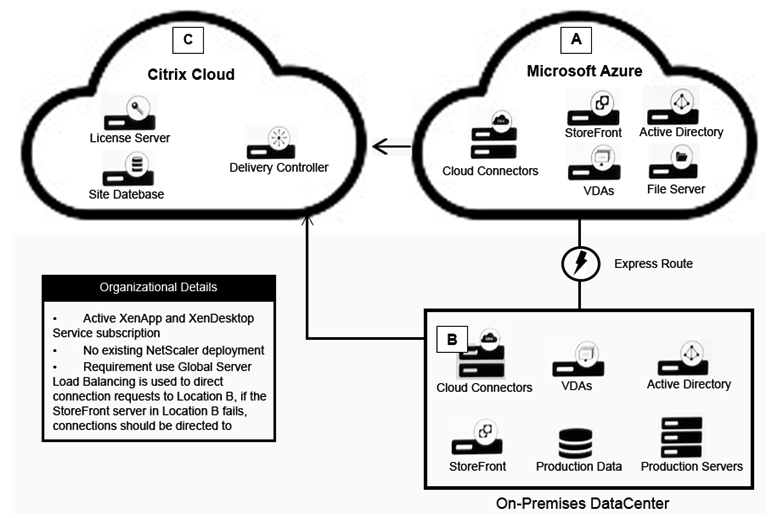 The architect should use _____ in Location A, and should use ________ in Location B. (Choose the correct option to complete the sentence.)
The architect should use _____ in Location A, and should use ________ in Location B. (Choose the correct option to complete the sentence.)
A) NetScaler ADC (BYO); NetScaler gateway appliance
B) NetScaler ADC (BYO); No NetScaler products
C) NetScaler ADC (BYO); NetScaler ADC (BYO)
D) NetScaler Gateway appliance; NetScaler Gateway appliance
E) NetScaler Gateway appliance; NetScaler ADC (BYO)
 The architect should use _____ in Location A, and should use ________ in Location B. (Choose the correct option to complete the sentence.)
The architect should use _____ in Location A, and should use ________ in Location B. (Choose the correct option to complete the sentence.)A) NetScaler ADC (BYO); NetScaler gateway appliance
B) NetScaler ADC (BYO); No NetScaler products
C) NetScaler ADC (BYO); NetScaler ADC (BYO)
D) NetScaler Gateway appliance; NetScaler Gateway appliance
E) NetScaler Gateway appliance; NetScaler ADC (BYO)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
20
Scenario: A Citrix Architect has configured NetScaler Gateway integration with a XenApp environment to provide access to users from two domains: vendorlab.com and workslab.com. The Authentication method used is LDAP. Which two steps are required to achieve Single Sign-on StoreFront using a single store? (Choose two.)
A) Configure Single sign-on domain in Session profile 'userPrincipalName'.
B) Do NOT configure SSO Name attribute in LDAP Profile.
C) Do NOT configure sign-on domain in Session Profile.
D) Configure SSO Name attribute to 'userPrincipalName' in LDAP Profile.
A) Configure Single sign-on domain in Session profile 'userPrincipalName'.
B) Do NOT configure SSO Name attribute in LDAP Profile.
C) Do NOT configure sign-on domain in Session Profile.
D) Configure SSO Name attribute to 'userPrincipalName' in LDAP Profile.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
21
Scenario: A Citrix Architect is asked by management at the Workslab organization to review their existing configuration and make the necessary upgrades. The architect recommends small changes to the pre-existing NetScaler configuration. Currently, the NetScaler MPX devices are configured in a high availability pair, and the outbound traffic is load-balanced between two Internet service providers 9ISPs). However, the failover is NOT happening correctly. The following requirements were discussed during the design requirements phase: The return traffic for a specific flow should be routed through the same path while using Link Load Balancing. The link should fail over if the ISP router is up and intermediary devices to an ISP router are down. Traffic going through one ISP router should fail over to the secondary ISP, and the traffic should NOT flow through both routers simultaneously. What should the architect configure with Link Load balancing (LLB) to meet this requirement?
A) Net Profile
B) Mac-based forwarding option enabled.
C) Resilient deployment mode
D) Backup route
A) Net Profile
B) Mac-based forwarding option enabled.
C) Resilient deployment mode
D) Backup route

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
22
Which step does a Citrix Architect need to ensure during the Define phase when following the Citrix Methodology?
A) Testing steps were integrated.
B) The project manager agrees with road map timelines.
C) A phased roll out was completed.
D) Existing networking infrastructure is ready.
E) The redundancy deployment decision was made.
A) Testing steps were integrated.
B) The project manager agrees with road map timelines.
C) A phased roll out was completed.
D) Existing networking infrastructure is ready.
E) The redundancy deployment decision was made.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
23
Scenario: A Citrix Architect has deployed two MPX devices, 12.0.53.13 nc and MPX 11500 models, in high availability (HA) pair for the Workspace labs team. The deployment method is two-arm and the devices are installed behind a CISCO ASA 5585 Firewall. The architect enabled the following features on the NetScaler devices. Content Switching, SSL Offloading, Load Balancing, NetScaler Gateway, Application Firewall in hybrid security and Appflow. All are enabled to send monitoring information to NMAS 12.0.53.13 nc build. The architect is preparing to configure load balancing for Microsoft Exchange 2016 server. The following requirements were discussed during the implementation: All traffic needs to be segregated based on applications, and the fewest number of IP addresses should be utilized during the configuration All traffic should be secured and any traffic coming into HTTP should be redirected to HTTPS. Single Sign-on should be created for Microsoft Outlook web access (OWA). NetScaler should recognize Uniform Resource Identifier (URl) and close the session to NetScaler when users hit the Logoff button in Microsoft Outlook web access. Users should be able to authenticate using either user principal name (UPN) or sAMAccountName. The Layer 7 monitor should be configured to monitor the Microsoft Outlook web access servers and the monitor probes must be sent on SSL Which monitor will meet these requirements?
A) add lb monitor mon_rpc HTTP-ECV -send "GET /rpc/healthcheck.htm" recv 200 -LRTM DISABLED
B) add lb monitor mon_rpc HTTP-ECV -send "GET /rpc/healthcheck.htm" recv 200 -LRTM ENABLED
C) add lb monitor mon_rpc HTTP -send "GET /rpc/healthcheck.htm" recv 200 -LRTM DISABLED -secure YES
D) add lb monitor mon_rpc HTTP-ECV -send "GET/rpc/healthcheck.htm" recv 200 -LRTM DISABLED -secure YES
A) add lb monitor mon_rpc HTTP-ECV -send "GET /rpc/healthcheck.htm" recv 200 -LRTM DISABLED
B) add lb monitor mon_rpc HTTP-ECV -send "GET /rpc/healthcheck.htm" recv 200 -LRTM ENABLED
C) add lb monitor mon_rpc HTTP -send "GET /rpc/healthcheck.htm" recv 200 -LRTM DISABLED -secure YES
D) add lb monitor mon_rpc HTTP-ECV -send "GET/rpc/healthcheck.htm" recv 200 -LRTM DISABLED -secure YES

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
24
For which three reasons should a Citrix Architect perform a capabilities assessment when designing and deploying a new NetScaler in an existing environment? (Choose three.)
A) Understand the skill set of the company.
B) Assess and identify potential risks for the design and build phase.
C) Establish and prioritize the key drivers behind a project.
D) Determine operating systems and application usage.
E) Identify other planned projects and initiatives that must be integrated with the design and build phase.
A) Understand the skill set of the company.
B) Assess and identify potential risks for the design and build phase.
C) Establish and prioritize the key drivers behind a project.
D) Determine operating systems and application usage.
E) Identify other planned projects and initiatives that must be integrated with the design and build phase.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
25
Scenario: Based on a discussion between a Citrix Architect and team of Workspacelab has been created across three (3) sites. They captured the following requirements during the design discussion held for NetScaler design projects: All three (3) Workspacelab sites (DC, NDR, and DR) will have similar NetScaler configuration and design. Both external and internal NetScaler MPX appliances will have Global Server Load balancing (GSLB) configured and deployed in Active/Passive mode. GSLB should resolve both A and AAA DNS queries. In the GSLB deployment, the NDR site will act as backup for the DC site. whereas the DR site will act as backup for the NDR site. When the external NetScaler replies to DNS traffic coming in through Cisco Firepower IPS, the replies should be sent back through the same path. On the internal NetScaler, both front-end VIP and back-end SNIP will be part of the same subnet. USIP is configured on the DMZ NetScaler appliances. The external NetScaler will act default gateway for back-end servers. All three (3) sites (DC, NDR, and DR) will have two (2) links to the Internet from different service providers configured in Active/Standby mode. Which design decision must the architect make to meet the design requirements above?
A) Interface 0/1 must be used for DNS traffic.
B) The SNIP of the external NetScaler must be configured as default gateway on the back-end servers.
C) ADNS service must be used with IPv6 address.
D) Policy-Based Route with next hop as CISCO IPS must be configured on the external NetScaler.
A) Interface 0/1 must be used for DNS traffic.
B) The SNIP of the external NetScaler must be configured as default gateway on the back-end servers.
C) ADNS service must be used with IPv6 address.
D) Policy-Based Route with next hop as CISCO IPS must be configured on the external NetScaler.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
26
Scenario: A Citrix Architect needs to design a new NetScaler Gateway deployment to provide secure RDP access to backend Windows machines. Click the Exhibit button to view additional requirements collected by the architect during the design discussions. 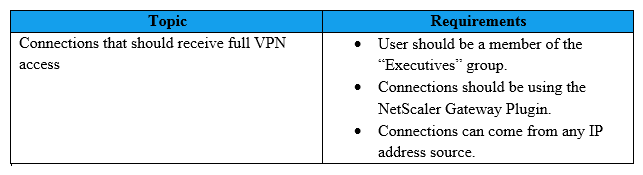 To meet the customer requirements, the architect should deploy the RDP proxy through _______, using a _________ solution. (Choose the correct option to complete the sentence.)
To meet the customer requirements, the architect should deploy the RDP proxy through _______, using a _________ solution. (Choose the correct option to complete the sentence.)
A) ICAProxy, stateless gateway
B) CVPN; single gateway
C) CVPN; stateless gateway
D) ICAProxy; single gateway
 To meet the customer requirements, the architect should deploy the RDP proxy through _______, using a _________ solution. (Choose the correct option to complete the sentence.)
To meet the customer requirements, the architect should deploy the RDP proxy through _______, using a _________ solution. (Choose the correct option to complete the sentence.)A) ICAProxy, stateless gateway
B) CVPN; single gateway
C) CVPN; stateless gateway
D) ICAProxy; single gateway

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
27
Scenario: A Citrix Architect needs to assess an existing NetScaler gateway deployment. During the assessment, the architect collects key requirements for different user groups, as well as the current session profile settings that are applied to those users. Click the Exhibit button to view the information collected by the architect. 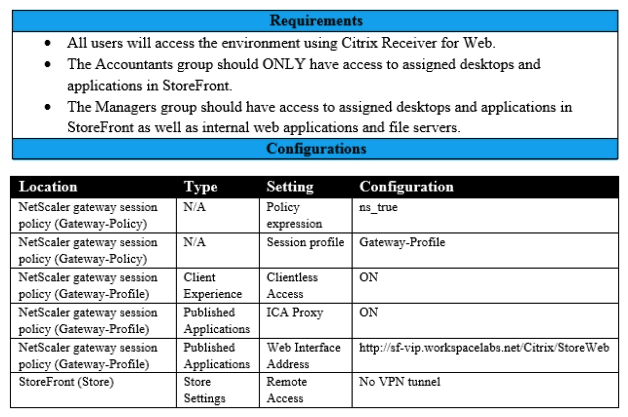 Which configuration should the architect make to meet these requirements?
Which configuration should the architect make to meet these requirements?
A) Change the Clientless Access settings in an existing session profile.
B) Change the remote Access settings in StoreFront.
C) Change ICA proxy settings in an existing session profile.
D) Change the policy expression in an existing session policy.
E) Create a new session profile and policy.
 Which configuration should the architect make to meet these requirements?
Which configuration should the architect make to meet these requirements?A) Change the Clientless Access settings in an existing session profile.
B) Change the remote Access settings in StoreFront.
C) Change ICA proxy settings in an existing session profile.
D) Change the policy expression in an existing session policy.
E) Create a new session profile and policy.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
28
Which two NetScaler cookies indicate the validity of the Authentication, Authorization and Accounting (AAA) session for users? (Choose two.)
A) NSC_WT
B) NSC_TMAS
C) NSC_AAAC
D) NSC_TMAA
A) NSC_WT
B) NSC_TMAS
C) NSC_AAAC
D) NSC_TMAA

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
29
Scenario: A Citrix Architect needs to assess an existing NetScaler configuration. The customer recently found that members of certain administrator groups were receiving permissions on the production NetScaler appliances that do NOT align with the designed security requirements. Click the Exhibit button to view the configured command policies for the production NetScaler deployment. 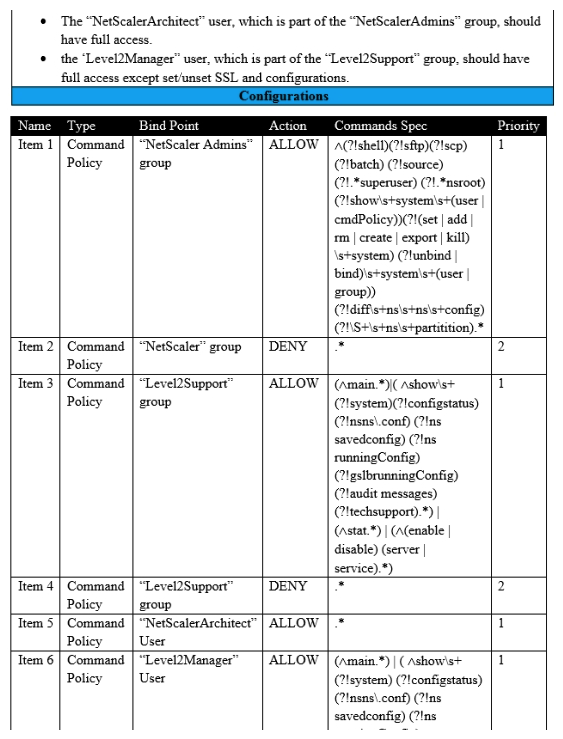 To align the command policy configuration with the security requirements of the organization, the _______ for ______should change. (Choose the correct option to complete the sentence.)
To align the command policy configuration with the security requirements of the organization, the _______ for ______should change. (Choose the correct option to complete the sentence.)
A) command spec; item 3
B) priority; Item 5
C) action; Item 1
D) priority; Item 2
E) action; Item 4
F) command spec; Item 6
 To align the command policy configuration with the security requirements of the organization, the _______ for ______should change. (Choose the correct option to complete the sentence.)
To align the command policy configuration with the security requirements of the organization, the _______ for ______should change. (Choose the correct option to complete the sentence.)A) command spec; item 3
B) priority; Item 5
C) action; Item 1
D) priority; Item 2
E) action; Item 4
F) command spec; Item 6

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
30
Scenario: A Citrix Architect needs to deploy a NetScaler appliance for Workspacelab, which will provide application load balancing services to Partnerlab and Vendorlab. The setup requirements are as follows: A pair of NetScaler MPX appliances will be deployed in the DMZ network. High availability will be accessible on the NetScaler MPX in the DMZ Network. Load balancing should be performed for the mail servers for Partnerlab and Vendorlab. The traffic for both of the organizations must be isolated. Separate Management accounts must be available for each client. The load-balancing IP addresses must be identical. A separate VLAN must be utilized for communication for each client. Which solution can the architect utilize to meet the requirements?
A) Traffic Domain
B) Admin Partition
C) VLAN Filtering
D) VPX or MPX
A) Traffic Domain
B) Admin Partition
C) VLAN Filtering
D) VPX or MPX

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
31
Scenario: A Citrix Architect needs to assess an existing NetScaler configuration. The customer recently found that certain user groups were receiving access to an internal web server with an authorization configuration that does NOT align with the designed security requirements. Click the Exhibit button view the configured authorization settings for the web server. 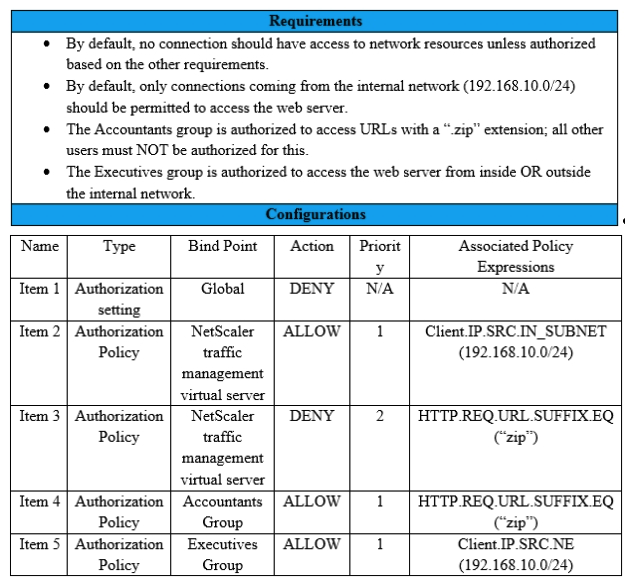 Which item should the architect change or remove to align the authorization configuration with the security requirements of the organization?
Which item should the architect change or remove to align the authorization configuration with the security requirements of the organization?
A) Item 1
B) Item 3
C) Item 4
D) Item 5
E) Item 2
 Which item should the architect change or remove to align the authorization configuration with the security requirements of the organization?
Which item should the architect change or remove to align the authorization configuration with the security requirements of the organization?A) Item 1
B) Item 3
C) Item 4
D) Item 5
E) Item 2

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
32
Scenario: A Citrix Architect has deployed an authentication setup with a ShareFile load-balancing virtual server. The NetScaler is configured as the Service Provider and Portalguard server is utilized as the SAML Identity Provider. While performing the functional testing, the architect finds that after the users enter their credentials on the logon page provided by Portalguard, they get redirected back to the Netscaler Gateway page at uri /cgi/samlauth/ and receive the following error. "SAML Assertion verification failed; Please contact your administrator." The events in the /var/log/ns.log at the time of this issue are as follows: Feb 23 20:35:21 10.148.138.5 23/02/2018:20:35:21 GMT vorsb1 0-PPE-0 : default AAATM Message 3225369 0 : "SAML : ParseAssertion: parsed attribute NameID, value is nameid" Feb 23 20:35:21 10.148.138.5 23/02/2018:20:35:21 GMT vorsb1 0-PPE-0 : default AAATM Message 3225370 0 : "SAML verify digest: algorithms differ, expected SHA1 found SHA256" Feb 23 20:35:44 10.148.138.5 23/02/2018:20:35:44 GMT vorsb1 0-PPE-0 : default AAATM Message 3225373 0 : "SAML : ParseAssertion: parsed attribute NameID, value is named Feb 23 20:35:44 10.148.138.5 23/02/2018:20:35:44 GMT vorsb1 0-PPE-0 : default AAATM Message 3225374 0 : "SAML verify digest: Feb 23 20:37:55 10.148.138.5 23/02/2018:20:37:55 GMT vorsb1 0-PPE-0 : default AAATM Message 3225378 0 : "SAML : ParseAssertion: Feb 23 20:37:55 10.148.138.5 23/02/2018:20:37:55 GMT vorsb1 0-PPE-0 : default AAATM Message 3225379 0 : "SAML verify digest: What should the architect change in the SAML action to resolve this issue?
A) Signature Algorithm to SHA 256
B) The Digest Method to SHA 256
C) The Digest Method to SHA 1
D) Signature Algorithm to SHA 1
A) Signature Algorithm to SHA 256
B) The Digest Method to SHA 256
C) The Digest Method to SHA 1
D) Signature Algorithm to SHA 1

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
33
Scenario: A Citrix Architect has deployed Authentication for the SharePoint server through NetScaler. In order to ensure that users are able to edit or upload documents, the architect has configured persistent cookies on the NetScaler profile. Which action should the architect take to ensure that cookies are shared between the browser and non-browser applications?
A) The time zone should be the same on the NetScaler, client, and SharePoint server.
B) The SharePoint load-balancing VIP FQDN and the AAA VIP FQDN should be in the trusted site of the client browser.
C) The Secure flag must be enabled on the cookie.
D) The cookie type should be HttpOnly.
A) The time zone should be the same on the NetScaler, client, and SharePoint server.
B) The SharePoint load-balancing VIP FQDN and the AAA VIP FQDN should be in the trusted site of the client browser.
C) The Secure flag must be enabled on the cookie.
D) The cookie type should be HttpOnly.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
34
Scenario: A Citrix Architect has set up NetScaler MPX devices in high availability mode with version 12.0.53.13 nc. These are placed behind a Cisco ASA 5505 Firewall. The Cisco ASA Firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall. The following requirements were captured by the architect during the discussion held as part of the NetScaler security implementation project with the customer's security team: The NetScaler MPX device: should monitor the rate of traffic either on a specific virtual entity or on the device. It should be able to mitigate the attacks from a hostile client sending a flood of requests. The NetScaler device should be able to stop the HTTP, TCP, and DNS based requests. needs to protect backend servers from overloading. needs to queue all the incoming requests on the virtual server level instead of the service level. should provide protection against well-known Windows exploits, virus-infected personal computers, centrally managed automated botnets, compromised webservers, known spammers/hackers, and phishing proxies. should provide flexibility to enforce the decided level of security check inspections for the requests originating from a specific geolocation database. should block the traffic based on a pre-determined header length, URL length, and cookie length. The device should ensure that characters such as a single straight quote ("); backslash (\); and semicolon (;) are either blocked, transformed, or dropped while being sent to the backend server. Which security feature should the architect configure to meet these requirements?
A) Global Server Load balancing with Dynamic RTT
B) Global Server Load Balancing with DNS views
C) Geolocation-based blocking using Application Firewall
D) geolocation-based blocking using Responder policies
A) Global Server Load balancing with Dynamic RTT
B) Global Server Load Balancing with DNS views
C) Geolocation-based blocking using Application Firewall
D) geolocation-based blocking using Responder policies

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
35
Scenario: A Citrix Architect has sent the following request to the NetScaler: 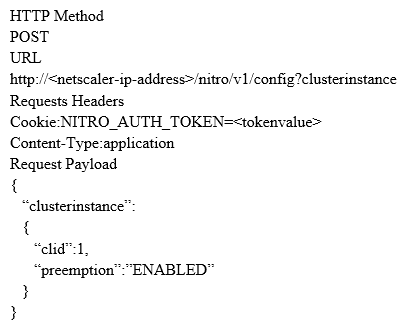 Which response would indicate the successful execution of the NITRO command?
Which response would indicate the successful execution of the NITRO command?
A) 302
B) 201
C) 202
D) 200
 Which response would indicate the successful execution of the NITRO command?
Which response would indicate the successful execution of the NITRO command?A) 302
B) 201
C) 202
D) 200

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck
36
Which four load-balancing methods support NetScaler Virtual Server-Level Slow Start? (Choose four.)
A) URLHash
B) Least response time
C) Least Packets
D) Least Connection
E) Token
F) Least bandwidth
G) SRCIPSRCPORTHash
A) URLHash
B) Least response time
C) Least Packets
D) Least Connection
E) Token
F) Least bandwidth
G) SRCIPSRCPORTHash

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 36 في هذه المجموعة.
فتح الحزمة
k this deck








