Deck 19: Concepts Unit A: Understanding Essential Computer Concepts
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
Match between columns
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/66
العب
ملء الشاشة (f)
Deck 19: Concepts Unit A: Understanding Essential Computer Concepts
1
The physical components of a computer are referred to as ____.
A) software
B) hardware
C) configurations
D) specifications
A) software
B) hardware
C) configurations
D) specifications
B
2
A file that tells a computer how to perform a specific task is called a(n) ____ file.
A) executable
B) instruction
C) data
D) configuration
A) executable
B) instruction
C) data
D) configuration
A
3
A hard copy of a file you created on your computer would be ____.
A) saved on a floppy disk
B) printed on a printer
C) backed up on a tape drive
D) sent as an e-mail
A) saved on a floppy disk
B) printed on a printer
C) backed up on a tape drive
D) sent as an e-mail
B
4


 Which of the following is NOT shown in the figure above?
Which of the following is NOT shown in the figure above?A) keyboard
B) mouse
C) touch pad
D) trackball

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
5
 Another name for the CPU pictured above is ____.
Another name for the CPU pictured above is ____.A) microprocessor
B) RAM cache
C) clock speed
D) megahertz

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
6
An example of an output device is a ____.
A) keyboard
B) monitor
C) mouse
D) touch pad
A) keyboard
B) monitor
C) mouse
D) touch pad

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
7
Special high-speed memory reserved for the microprocessor's use is called ____.
A) ROM
B) storage
C) virtual memory
D) cache memory
A) ROM
B) storage
C) virtual memory
D) cache memory

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
8
Megahertz is a measurement of ____.
A) the amount of memory
B) the amount of RAM
C) the speed of the microprocessor
D) cache memory
A) the amount of memory
B) the amount of RAM
C) the speed of the microprocessor
D) cache memory

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
9
Where is program and data that is being used temporarily stored by your computer?
A) cache
B) RAM
C) ROM
D) CMOS
A) cache
B) RAM
C) ROM
D) CMOS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
10
Processing tasks occur on the ____.
A) motherboard
B) keyboard
C) control panel
D) operating system
A) motherboard
B) keyboard
C) control panel
D) operating system

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
11
The speed of a laser printer is measured in ____.
A) pages per minute
B) pages per second
C) characters per minute
D) characters per second
A) pages per minute
B) pages per second
C) characters per minute
D) characters per second

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
12
Personal computers commonly use the ____ code system to represent character data.
A) KB
B) LAN
C) ASCII
D) COBOL
A) KB
B) LAN
C) ASCII
D) COBOL

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
13
The computer needs additional components called ____ to accomplish its input, output, and storage functions.
A) mice
B) specifications
C) architecture
D) peripheral devices
A) mice
B) specifications
C) architecture
D) peripheral devices

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
14
Which of the following dot pitches gives you the sharpest picture?
A) .26
B) .32
C) .38
D) .45
A) .26
B) .32
C) .38
D) .45

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
15
Resolution is the ____.
A) number of pixels a monitor displays
B) distance between pixels in a graphics display
C) number of rectangles in a character-based display grid
D) dot pitch in a graphics display
A) number of pixels a monitor displays
B) distance between pixels in a graphics display
C) number of rectangles in a character-based display grid
D) dot pitch in a graphics display

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
16
You are running two programs at once that require 8 megabytes each on a computer that only has 12 megabytes of RAM. What makes this possible?
A) virtual memory
B) ROM
C) cache
D) CMOS
A) virtual memory
B) ROM
C) cache
D) CMOS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
17


 The devices shown in the figure above are all ____ devices.
The devices shown in the figure above are all ____ devices.A) input
B) pointing
C) storage
D) all of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
18
Which of the following is the largest unit of measurement?
A) a terabyte
B) a gigabyte
C) a megabyte
D) a kilobyte
A) a terabyte
B) a gigabyte
C) a megabyte
D) a kilobyte

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
19
Which of the following is NOT a personal computer?
A) desktop
B) laptop
C) notebook
D) mainframe
A) desktop
B) laptop
C) notebook
D) mainframe

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
20
Which of the following is a personal computer?
A) desktop
B) mainframe
C) terminal
D) all of the above
A) desktop
B) mainframe
C) terminal
D) all of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
21
Expansion cards plug into electrical connectors on the motherboard called ____.
A) ports
B) cables
C) slots
D) buses
A) ports
B) cables
C) slots
D) buses

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
22
A network with a file server is called a client/server network.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
23
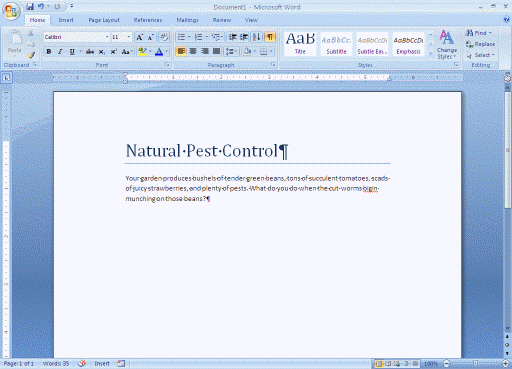 (a)
(a) 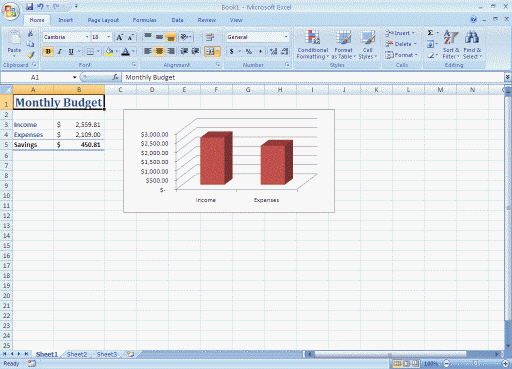 (b)
(b)  (c)
(c)  (d) In the above figure, which screen shows software used for numerical analysis?
(d) In the above figure, which screen shows software used for numerical analysis?A) a
B) b
C) c
D) d

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
24
The seamless nature of OLE among some applications is referred to as ____.
A) operation success
B) source symmetry
C) GUI
D) integration
A) operation success
B) source symmetry
C) GUI
D) integration

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
25
A device driver is a computer program that makes communication possible between your computer and one of its peripherals.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
26
A tape drive is a type of magnetic storage device.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
27
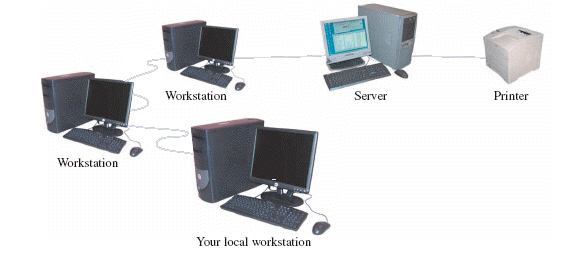 The network shown in the figure above is a ____ network.
The network shown in the figure above is a ____ network.A) peer-to-peer
B) client/server
C) wireless
D) Bluetooth

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
28
The practice of sending e-mails to customers or potential customers of a legitimate Web site asking them to click a link in the e-mail is called ____.
A) spoofing
B) phishing
C) pharming
D) swishing
A) spoofing
B) phishing
C) pharming
D) swishing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
29
CD-ROMs are rewritable.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
30
Polycarbonate discs coated with a reflective metal on which data is recorded using laser technology as a trail of tiny pits or dark spots in the surface of the disc are ____ storage devices.
A) magnetic
B) optical
C) flash
D) USB
A) magnetic
B) optical
C) flash
D) USB

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
31
Antivirus software protects against which of the following types of malware?
A) Viruses
B) Trojan horses
C) Worms
D) all of the above
A) Viruses
B) Trojan horses
C) Worms
D) all of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
32
CMOS is often referred to as ____ memory.
A) permanent
B) semipermanent
C) volatile
D) none of the above
A) permanent
B) semipermanent
C) volatile
D) none of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
33
A parallel port is relatively slow, as it transmits data one bit at a time.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
34
The communication path between a microprocessor, RAM, and peripherals is called the data bus.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
35
An interface card could be plugged into an expansion slot on the main board of a computer.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
36
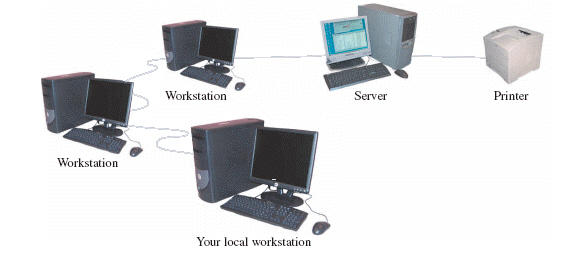 Each of the components connected by wires in the above figure is called a ____.
Each of the components connected by wires in the above figure is called a ____.A) client
B) node
C) workstation
D) server

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
37
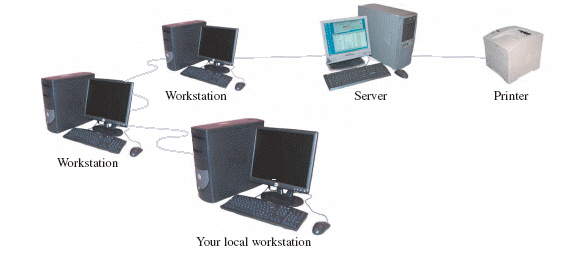 Each of the items labeled workstation in the above figure must have a network intercommunication card installed.
Each of the items labeled workstation in the above figure must have a network intercommunication card installed.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
38
____ allocate system resources, manage storage space, maintain security, detect equipment failure, and control basic input and output.
A) Operating systems
B) Utilities
C) Programming languages
D) Database management software
A) Operating systems
B) Utilities
C) Programming languages
D) Database management software

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
39
Protocols in data communication establish the countries with which data can be exchanged.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
40
A PC card slot could contain a hard disk drive.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
41
The operating system is the set of instructions that direct the computer to accomplish specific tasks such as document production and spreadsheet calculations.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
42
BASIC, Visual Basic, C, C++, and COBOL are all examples of computer programming ____________________.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
43
Antivirus software is a broad term that describes any program that is intended to cause harm or convey information to others without the owner's permission.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
44
 The integrated circuit, or chip, in the figure above is known as a(n) _________________________ and is responsible for executing instructions to process data.
The integrated circuit, or chip, in the figure above is known as a(n) _________________________ and is responsible for executing instructions to process data.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
45
____________________ instruct the computer on how to process data.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
46
Special high-speed memory built into the microprocessor for the microprocessor's use is called ____________________.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
47
A(n) ____________________ prevents other computers on the Internet from accessing a computer and prevents programs on a computer from accessing the Internet without the computer user's permission.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
48
Operating systems, utilities, device drivers, and programming languages are the four types of ____________________ software.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
49
If you type a paper for a class and save it on the hard drive, it is called an executable file .

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
50
A modem converts the digital signals your computer outputs to analog signals.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
51
Technical details about components on a computer are called architecture .

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
52
Explain the differences between RAM, ROM, CMOS, cache, and virtual memory.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
53
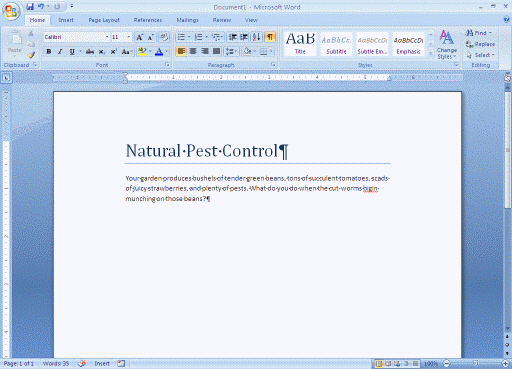 (a)
(a) 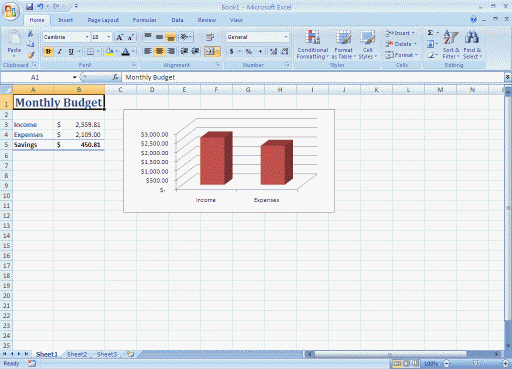 (b)
(b)  (c)
(c) 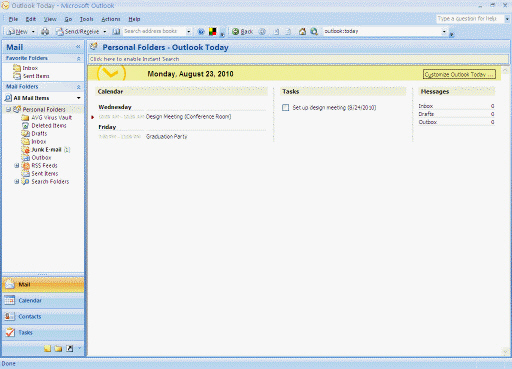 (d) Define system software and application software, and give a general example of each type, referring to the screens shown in the above figure as applicable.
(d) Define system software and application software, and give a general example of each type, referring to the screens shown in the above figure as applicable.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
54
Database management software allows you to create illustrations, diagrams, graphs, and charts that can be projected before a group, printed out for quick reference, or transmitted to remote computers.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
55
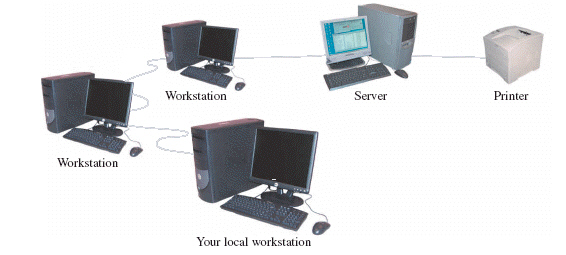 The printer in the above figure is considered a node.
The printer in the above figure is considered a node.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
56
A system resource is any part of the computer system, including memory, storage devices, and the microprocessor, that can be used by a computer program.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
57
Modifying data is referred to as ____________________.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
58
Explain the differences between mainframes and supercomputers.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
59
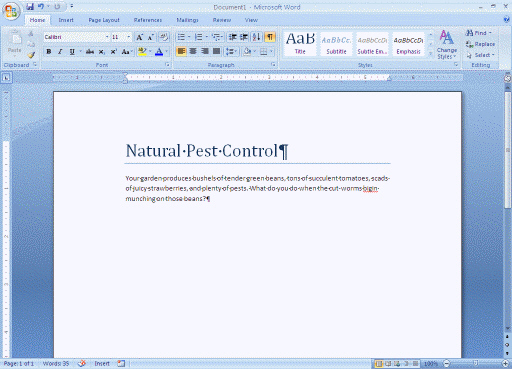 (a)
(a) 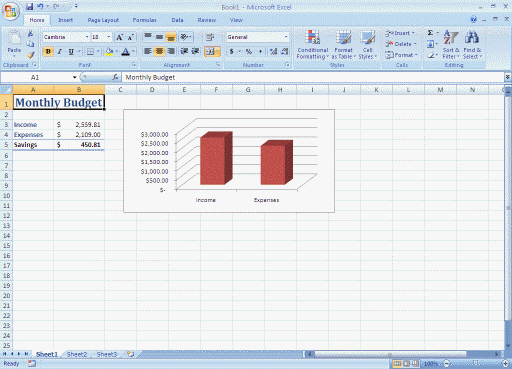 (b)
(b)  (c)
(c) 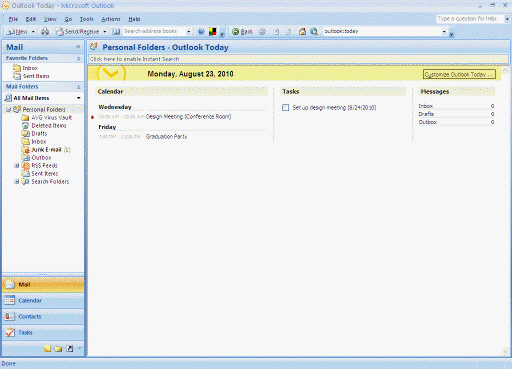 (d) The screens labeled (a), (b), and (d) in the above figure are examples of system software.
(d) The screens labeled (a), (b), and (d) in the above figure are examples of system software.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
60
____________________ memory is created and used by most computers when the amount of RAM needed exceeds the RAM available.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
61
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
62
What type of software should Mary Ann purchase to help her create and track budgets?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
63
You have been chosen to upgrade the computer system for your homeowner's association. You want to purchase a system that will be useful for several years. Because the spot where the computer will be located is somewhat cramped, what is the best type of monitor to purchase?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
64
You have been chosen to upgrade the computer system for your homeowner's association. You want to purchase a system that will be useful for several years. You want the computer to be able to perform quickly. What is the easiest way to make the computer run faster?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
65
Mary Ann Costello is a wedding planner in Austin, Texas. She decided to create a list of all the resources she uses--halls, florists, bands, etc.--when planning a wedding. She needs to purchase software to help her accomplish this. She also needs to track the total expenses for each wedding and needs software to help her do this as well. What type of software should Mary Ann purchase to create and manage her collection of data?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck
66
You have been chosen to upgrade the computer system for your homeowner's association. You want to purchase a system that will be useful for several years. You want to be able to allow members to copy certain files and carry them with them when they leave. What is a good choice for something that can store files, is transportable, and is small enough to fit in a member's pocket or on a key chain?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 66 في هذه المجموعة.
فتح الحزمة
k this deck








