Deck 24: Network Fundamentals
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
Match between columns
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/46
العب
ملء الشاشة (f)
Deck 24: Network Fundamentals
1
An extranet is similar to a(n) server but it allows specific users outside of the organization to access internal information systems.
False
2
A wide area network (WAN) connects personal computers, workstations, and other devices in a limited geographical area.
False
3
Client/server networks are easier to set up and manage than peer-to-peer networks.
False
4
Networks are divided into four main types.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
5
Server operating systems are high-end programs designed to provide network control and include special functions for connecting computers and other devices into a network.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
6
To connect wirelessly requires different equipment than that used for a wired connection.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
7
What types of phones are supported through the Public Switched Telephone Network (PSTN)?
A) Digital
B) Mobile
C) Standard
D) All of the above
A) Digital
B) Mobile
C) Standard
D) All of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
8
A standalone computer system is vulnerable to the same kinds of risks as a network.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
9
Which of the following network benefit do companies take advantage of when they purchase a site license?
A) Enhanced communication
B) Hardware sharing
C) Software sharing
D) Collaborative environment
A) Enhanced communication
B) Hardware sharing
C) Software sharing
D) Collaborative environment

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
10
The term client/server network describes a software architectural model.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
11
A network is simply a group of two or more computers linked together.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
12
Which of the following can contain communication links across metropolitan, regional, or national boundaries?
A) LAN
B) Wireless LAN
C) WAN
D) Intranet
A) LAN
B) Wireless LAN
C) WAN
D) Intranet

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
13
Electronic identification cards are used to gain access to certain areas within a building or department.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
14
Which of the following is true about e-mail?
A) The cost depends on the size of the message
B) Delivery is almost instantaneous
C) It is private
D) It cannot be sabotaged
A) The cost depends on the size of the message
B) Delivery is almost instantaneous
C) It is private
D) It cannot be sabotaged

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
15
The communication area of a LAN might be as large as a state, country, or even the world.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
16
The Internet is the biggest network of all.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
17
The best plan for a company that handles secure information is to handle security breaches as they occur.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
18
In a client/server network, all computers are equal.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
19
Biometric security measures are usually applied when high-level security is required.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
20
In a client/server network, which of the following would be considered the client?
A) Microsoft Windows
B) Internet Explorer
C) Printer
D) Desktop computer
A) Microsoft Windows
B) Internet Explorer
C) Printer
D) Desktop computer

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
21
Handbooks, employee manuals, and employment forms would most likely be found on ____.
A) an intranet
B) an extranet
C) the Internet
D) a hub
A) an intranet
B) an extranet
C) the Internet
D) a hub

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
22
Case 24-1 Javier has decided to upgrade his communication hardware and get a faster Internet connection. After considering all the options, he has decided to use a wireless Internet service provider. The speeds Javier will get with his new wireless connection will be more than ____ times faster than his old dial-up connection.
A) 2
B) 7
C) 30
D) 384
A) 2
B) 7
C) 30
D) 384

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
23
Which of the following uses coaxial cable to send and receive data?
A) Modem
B) Cable modem
C) Digital subscriber line (DSL)
D) T-1 line
A) Modem
B) Cable modem
C) Digital subscriber line (DSL)
D) T-1 line

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
24
Case 24-1 Javier has decided to upgrade his communication hardware and get a faster Internet connection. After considering all the options, he has decided to use a wireless Internet service provider. To connect his laptop wirelessly to the Internet, Javier will need a(n) ____.
A) hub
B) router
C) T-1 line
D) adapter
A) hub
B) router
C) T-1 line
D) adapter

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
25
A cache is a(n) ____.
A) place to store something temporarily
B) special type of password
C) external wireless adapter
D) dedicated connection to the Internet
A) place to store something temporarily
B) special type of password
C) external wireless adapter
D) dedicated connection to the Internet

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
26
In a client/server network, the ____ manages network resources.
A) client
B) server
C) node
D) router
A) client
B) server
C) node
D) router

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
27
A(n) ____ is a type of fiber-optic telephone line that can transmit up to 1.544 megabits per second.
A) DSL
B) HDSL
C) VDSL
D) T-1 line
A) DSL
B) HDSL
C) VDSL
D) T-1 line

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
28
Computer information is stored digitally, but information sent over the telephone lines is transmitted in the form of ____.
A) analog waves
B) bridges
C) air waves
D) fiber optics
A) analog waves
B) bridges
C) air waves
D) fiber optics

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
29
The word modem is an acronym for ____.
A) mo dern dem arcation
B) mo st dem and
C) mo dulate dem odulate
D) mo dification dem onstration
A) mo dern dem arcation
B) mo st dem and
C) mo dulate dem odulate
D) mo dification dem onstration

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
30
Case 24-2 Bryah owns a small business and travels frequently. She is concerned about the security of the data on her laptop, which includes valuable information and trade secrets. When Bryah creates a password to restrict access to her computer, she should ____.
A) change it frequently
B) use all lowercase letters
C) write it down
D) use the same one as her Internet account
A) change it frequently
B) use all lowercase letters
C) write it down
D) use the same one as her Internet account

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
31
FIGURE 24-1 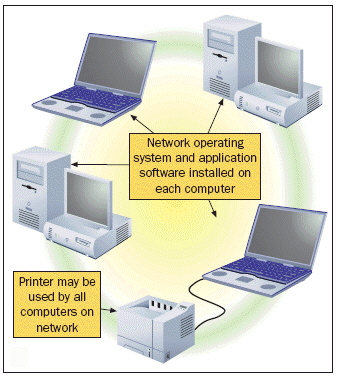 Figure 24-1 above shows an example of ____.
Figure 24-1 above shows an example of ____.
A) a communication channel
B) a client/server network
C) a peer-to-peer network
D) T-1 lines
 Figure 24-1 above shows an example of ____.
Figure 24-1 above shows an example of ____.A) a communication channel
B) a client/server network
C) a peer-to-peer network
D) T-1 lines

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
32
Case 24-2 Bryah owns a small business and travels frequently. She is concerned about the security of the data on her laptop, which includes valuable information and trade secrets. When Bryah is traveling, accidental association would be a concern when she is ____.
A) connecting wirelessly to the Internet
B) employing biometric security measures
C) screening potential employees
D) backing up data
A) connecting wirelessly to the Internet
B) employing biometric security measures
C) screening potential employees
D) backing up data

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
33
FIGURE 24-2 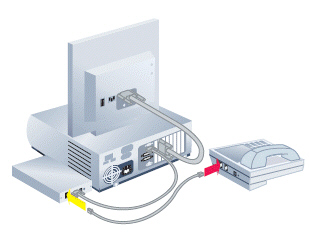 Figure 24-2 above shows a computer with a ____ attached.
Figure 24-2 above shows a computer with a ____ attached.
A) dial-up modem
B) wireless router
C) hub
D) T-1 line
 Figure 24-2 above shows a computer with a ____ attached.
Figure 24-2 above shows a computer with a ____ attached.A) dial-up modem
B) wireless router
C) hub
D) T-1 line

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
34
Antivirus software should ____.
A) be run when you suspect a problem
B) be run weekly
C) be run monthly
D) always be running
A) be run when you suspect a problem
B) be run weekly
C) be run monthly
D) always be running

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
35
A(n) ____ acts like a switchboard through a firewall.
A) Web server
B) FTP server
C) proxy server
D) database server
A) Web server
B) FTP server
C) proxy server
D) database server

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
36
Biometric security measures examine any of the following, except ____.
A) fingerprints
B) blood type
C) voice pattern
D) retina of the eye
A) fingerprints
B) blood type
C) voice pattern
D) retina of the eye

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
37
"Sniffer" software is used to ____.
A) prevent hackers from accessing your computer
B) locate wireless hot spots
C) transmit voice data over telephone lines
D) set up and manage a peer-to-peer network
A) prevent hackers from accessing your computer
B) locate wireless hot spots
C) transmit voice data over telephone lines
D) set up and manage a peer-to-peer network

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
38
____________________ are people who break into computer systems to steal services and information.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
39
Companies handling sensitive information should back up data regularly and store it ____.
A) on the same computer
B) on the network server
C) on CDs
D) off site
A) on the same computer
B) on the network server
C) on CDs
D) off site

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
40
The ____ determines the amount of data that can be sent at one time.
A) router
B) hub
C) node
D) bandwidth
A) router
B) hub
C) node
D) bandwidth

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
41
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
42
____________________ consist of special hardware and software to protect individual companies' networks from external networks.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
43
What are some of the changes that have occurred in our society because of the Internet? What are some disadvantages of being so dependent on the Internet?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
44
The ____________________ is a worldwide system composed of thousands of smaller networks.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
45
____________________ is a recent wireless technology that can deliver maximum speeds of up to 7 Mbps to your cell phone, home computer, or car.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
46
A(n) ____________________ is designed for the exclusive use of people within an organization.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck








