Deck 11: Information Systems Analysis and Design
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/52
العب
ملء الشاشة (f)
Deck 11: Information Systems Analysis and Design
1
A(n)  development tool is essentially a software construction kit containing building blocks that can be assembled into the software for an information system.
development tool is essentially a software construction kit containing building blocks that can be assembled into the software for an information system.
 development tool is essentially a software construction kit containing building blocks that can be assembled into the software for an information system.
development tool is essentially a software construction kit containing building blocks that can be assembled into the software for an information system.Tool that contains building blocks that assembled into software of an information system
For developing an information system, project teams decides which approach should be taken like modifying some information system, create a new information system or using any tool. Software construction kit has a tool called application development tool which creates a software product by assembling building blocks. Database management systems and expert system shells are included in application development tools.
Therefore, the appropriate word to fill in the blank is application.
For developing an information system, project teams decides which approach should be taken like modifying some information system, create a new information system or using any tool. Software construction kit has a tool called application development tool which creates a software product by assembling building blocks. Database management systems and expert system shells are included in application development tools.
Therefore, the appropriate word to fill in the blank is application.
2
Application  describe the way an application should interact with users, store data, process data, and format reports.
describe the way an application should interact with users, store data, process data, and format reports.
 describe the way an application should interact with users, store data, process data, and format reports.
describe the way an application should interact with users, store data, process data, and format reports.Describing the way in which application should interact with users, process data, store data and format reports
In system design phase, when a solution is selected, application specifications is created by the system analysts. This application specification describes the specification of the information system like interaction with users, format reports, processing and storing of data. These application specifications are used as a blueprint and also for ensuring whether the development processes are proceeding efficiently or not.
Therefore, the appropriate word to fill in the blank is specification.
In system design phase, when a solution is selected, application specifications is created by the system analysts. This application specification describes the specification of the information system like interaction with users, format reports, processing and storing of data. These application specifications are used as a blueprint and also for ensuring whether the development processes are proceeding efficiently or not.
Therefore, the appropriate word to fill in the blank is specification.
3
List and briefly describe three tools used for project scheduling, and then list and describe four documentation tools used in the analysis phase of the SDLC. Draw a DFD showing the flow of data (ingredients) when you make a grilled cheese sandwich.
Project scheduling
Project scheduling concerns with the techniques that has to be employed for managing, the activities that has to be undertaken in the process of development of the project.
Project scheduling tools:
1. PERT chart ( Program evaluation and review technique)
2. WBS( work breakdown structure)
3. Gantt chart
PERT Chart: Pert chart is a project scheduling tool which is used for scheduling, organizing and coordinating tasks within a project. Program evolution and review technique (PERT) is a technique which is used for analyzing the time that is needed in completing ach project task. It also helps in identifying the minimum time required for completing a project. The elements of PERT chart are arranged in a way so that they can show which tasks should be completed before starting dependent tasks.
WBS: Work breakdown structure is used for breaking a complex task into a number of subtasks in a hierarchical structure. The work breakdown structure can be activity oriented for listing all the tasks and it is deliverable oriented for listing the milestones.
The elements of WBS can be service, data or product. It is used for providing the estimated cost details.
Gantt chart: Gantt chart is used for indicating the duration of each task. It is in the form of bar chart. It also shows the milestones and compares actual completion dates to the planned completion date. Gantt chart is used for illustrating the start and finish dates of a project.
Development tools: A variety of developments tool are used by the project team for diagram the produced documentation and the current system. Object oriented methodology and the structured methodology uses different types of tools.
Development tools are:
1. Data flow diagram
2. Use case diagram
3. Class diagram
4. Sequence diagram
Data flow diagram : DFD are used for graphically illustrating how the data in an information system moves. In DFD, external entity can be an organization, person or any device which is outside the information system that receives or originates data. Tape and disks that can hold data are data stores. A process is something done computerized or manually that can update information or changes data by performing some calculation etc. Arrow is used for symbolizing the data flow. In a DFD arrows help in showing path of data to and from the data stores external entities and processes.
Use case diagram : Use case diagram is used for documenting the users to the information system and the function performed by them. Peoples who are using the system are called actors. The task performed by actors is called use case.
Class diagram: A class diagram is used for providing names to each object and listing attributes of each object. It is also used for providing list of methods. An attribute is the data element which is stored as a part of the object. Method is the task that an object can perform
Sequence diagram: It is used for showing that how processes will operate with each other and by which order.
Data flow diagram for making a grilled cheese sandwich:
Consider the following figure for making grilled cheese sandwich: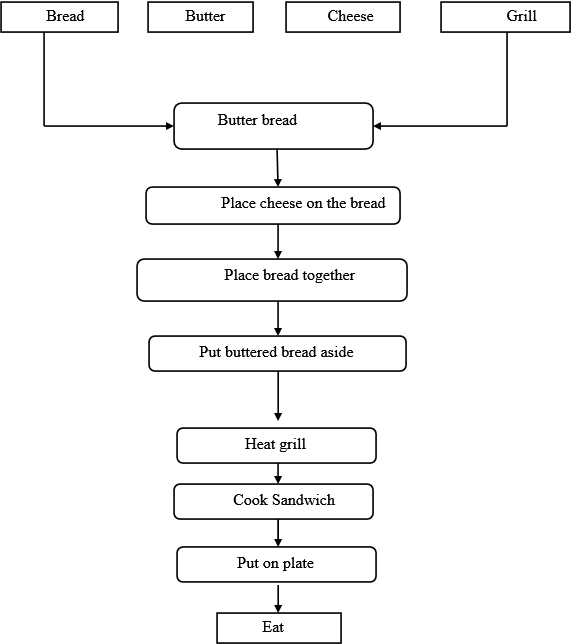
 The above figure describes the process for making a grilled cheese sandwich.
The above figure describes the process for making a grilled cheese sandwich.
Project scheduling concerns with the techniques that has to be employed for managing, the activities that has to be undertaken in the process of development of the project.
Project scheduling tools:
1. PERT chart ( Program evaluation and review technique)
2. WBS( work breakdown structure)
3. Gantt chart
PERT Chart: Pert chart is a project scheduling tool which is used for scheduling, organizing and coordinating tasks within a project. Program evolution and review technique (PERT) is a technique which is used for analyzing the time that is needed in completing ach project task. It also helps in identifying the minimum time required for completing a project. The elements of PERT chart are arranged in a way so that they can show which tasks should be completed before starting dependent tasks.
WBS: Work breakdown structure is used for breaking a complex task into a number of subtasks in a hierarchical structure. The work breakdown structure can be activity oriented for listing all the tasks and it is deliverable oriented for listing the milestones.
The elements of WBS can be service, data or product. It is used for providing the estimated cost details.
Gantt chart: Gantt chart is used for indicating the duration of each task. It is in the form of bar chart. It also shows the milestones and compares actual completion dates to the planned completion date. Gantt chart is used for illustrating the start and finish dates of a project.
Development tools: A variety of developments tool are used by the project team for diagram the produced documentation and the current system. Object oriented methodology and the structured methodology uses different types of tools.
Development tools are:
1. Data flow diagram
2. Use case diagram
3. Class diagram
4. Sequence diagram
Data flow diagram : DFD are used for graphically illustrating how the data in an information system moves. In DFD, external entity can be an organization, person or any device which is outside the information system that receives or originates data. Tape and disks that can hold data are data stores. A process is something done computerized or manually that can update information or changes data by performing some calculation etc. Arrow is used for symbolizing the data flow. In a DFD arrows help in showing path of data to and from the data stores external entities and processes.
Use case diagram : Use case diagram is used for documenting the users to the information system and the function performed by them. Peoples who are using the system are called actors. The task performed by actors is called use case.
Class diagram: A class diagram is used for providing names to each object and listing attributes of each object. It is also used for providing list of methods. An attribute is the data element which is stored as a part of the object. Method is the task that an object can perform
Sequence diagram: It is used for showing that how processes will operate with each other and by which order.
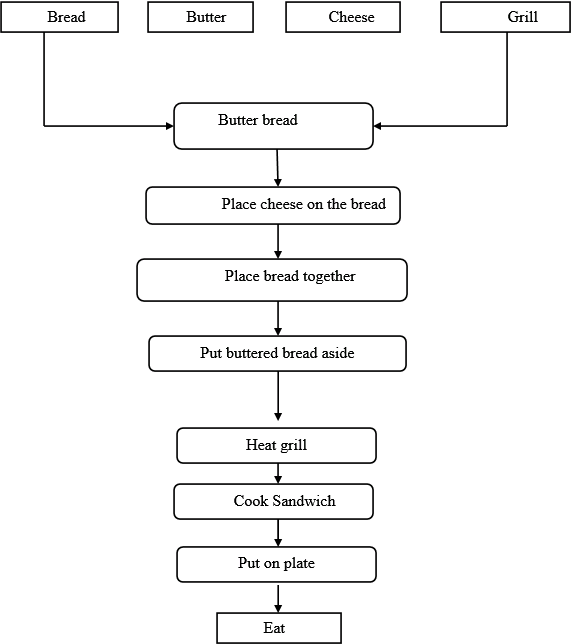
Data flow diagram for making a grilled cheese sandwich:
Consider the following figure for making grilled cheese sandwich:

 The above figure describes the process for making a grilled cheese sandwich.
The above figure describes the process for making a grilled cheese sandwich. 4
The target audience for  documentation is programmers, designers, and analysts.
documentation is programmers, designers, and analysts.
 documentation is programmers, designers, and analysts.
documentation is programmers, designers, and analysts.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
5
At the end of the implementation phase of the SDLC, users verify that the entire system works as specified, during a process called  testing.
testing.
 testing.
testing.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
6
Explain the advantages and disadvantages of centralized processing and distributed processing.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
7
A disaster  plan describes methods for securing data against disasters and sets guidelines for reconstructing lost data.
plan describes methods for securing data against disasters and sets guidelines for reconstructing lost data.
 plan describes methods for securing data against disasters and sets guidelines for reconstructing lost data.
plan describes methods for securing data against disasters and sets guidelines for reconstructing lost data.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
8
Some of the most secure  centers are located underground in old military bunkers and abandoned mines.
centers are located underground in old military bunkers and abandoned mines.
 centers are located underground in old military bunkers and abandoned mines.
centers are located underground in old military bunkers and abandoned mines.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
9
List and describe four software alternatives that systems analysts might consider for a new information system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
10
Do you think online voters would disproportionately vote for Republicans?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
11
Your county provides online access to property records. You simply enter the address of the property or the owner's name. However, each search seems to take longer than one minute. According to the PIECES framework, this delay would be classified as a(n)  problem.
problem.
 problem.
problem.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
12
Describe the five types of testing used during the implementation phase.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
13
Suppose that you own a small bookstore located in a mall. Business seems to be declining, and you suspect that many of your former customers are now shopping at online bookstores. What can you do about declining sales? You realize that this problem falls into the category of a(n)  problem, and you might not be able to solve it using the data supplied by your MIS.
problem, and you might not be able to solve it using the data supplied by your MIS.
 problem, and you might not be able to solve it using the data supplied by your MIS.
problem, and you might not be able to solve it using the data supplied by your MIS.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
14
An article in your local newspaper describes a new airport security system as "a sophisticated facial-recognition system powered by advanced computer technology that learns on its own." This technology sounds like a(n)  network.
network.
 network.
network.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
15
Using your own examples, discuss the ways in which an organization can respond to opportunities and threats.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
16
Use your own words to describe the advantages and disadvantages of direct, parallel, phased, and pilot conversions.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
17
List ten information systems that you've used.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
18
Explain the differences between strategic, tactical, and operational planning. Provide an example of how a computer system might be used for each type of planning.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
19
A(n)  system uses an inference engine to process rules and produce a diagnosis, recommendation, or decision.
system uses an inference engine to process rules and produce a diagnosis, recommendation, or decision.
 system uses an inference engine to process rules and produce a diagnosis, recommendation, or decision.
system uses an inference engine to process rules and produce a diagnosis, recommendation, or decision.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
20
List and define at least four quality-of-service metrics.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
21
Effective  systems are designed to support goals that help an organization carry out its mission statement.
systems are designed to support goals that help an organization carry out its mission statement.
 systems are designed to support goals that help an organization carry out its mission statement.
systems are designed to support goals that help an organization carry out its mission statement.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
22
 processing holds a group of transactions for later processing, whereas
processing holds a group of transactions for later processing, whereas  processing handles each transaction as it is entered.
processing handles each transaction as it is entered.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
23
Data  diagrams are used with structured methodology, whereas object-oriented methodology uses tools such as use case, class, and sequence diagrams.
diagrams are used with structured methodology, whereas object-oriented methodology uses tools such as use case, class, and sequence diagrams.
 diagrams are used with structured methodology, whereas object-oriented methodology uses tools such as use case, class, and sequence diagrams.
diagrams are used with structured methodology, whereas object-oriented methodology uses tools such as use case, class, and sequence diagrams.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
24
List and describe eight threats that could cause information systems to fail.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
25
In the planning phase, one of the main goals is to produce a Project  Plan.
Plan.
 Plan.
Plan.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
26
A(n)  diagram shows the time needed to complete each project task and the critical path for the entire project. (Hint: Use the acronym.)
diagram shows the time needed to complete each project task and the critical path for the entire project. (Hint: Use the acronym.)
 diagram shows the time needed to complete each project task and the critical path for the entire project. (Hint: Use the acronym.)
diagram shows the time needed to complete each project task and the critical path for the entire project. (Hint: Use the acronym.)
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
27
System development can get sidetracked by feature  .
.
 .
.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
28
Explain how organizations can protect the data stored on their information systems.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
29
In the  phase of the SDLC, a project team identifies several potential solutions and then selects the one that offers the most benefits at the lowest cost.
phase of the SDLC, a project team identifies several potential solutions and then selects the one that offers the most benefits at the lowest cost.
 phase of the SDLC, a project team identifies several potential solutions and then selects the one that offers the most benefits at the lowest cost.
phase of the SDLC, a project team identifies several potential solutions and then selects the one that offers the most benefits at the lowest cost.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
30
The project team can develop and send out a(n)  to ask vendors for prices on specific equipment and software. (Hint: Use the acronym.)
to ask vendors for prices on specific equipment and software. (Hint: Use the acronym.)
 to ask vendors for prices on specific equipment and software. (Hint: Use the acronym.)
to ask vendors for prices on specific equipment and software. (Hint: Use the acronym.)
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
31
During the maintenance phase, three key concepts ensure good  of service: reliability, availability, and serviceability.
of service: reliability, availability, and serviceability.
 of service: reliability, availability, and serviceability.
of service: reliability, availability, and serviceability.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
32
 testing ensures that a software module operates reliably and correctly, whereas
testing ensures that a software module operates reliably and correctly, whereas  testing checks to make sure all the modules work with each other.
testing checks to make sure all the modules work with each other.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
33
A direct  is risky because if the new system does not work correctly, it might need to be deactivated to undergo further development and testing.
is risky because if the new system does not work correctly, it might need to be deactivated to undergo further development and testing.
 is risky because if the new system does not work correctly, it might need to be deactivated to undergo further development and testing.
is risky because if the new system does not work correctly, it might need to be deactivated to undergo further development and testing.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
34
Corporate identity theft has become a major security concern because of increasing numbers of  scams and fake Web sites.
scams and fake Web sites.
 scams and fake Web sites.
scams and fake Web sites.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
35
A(n)  rating of 125,000 hours means that, on average, a device could function for 125,000 hours before failing. (Hint: Use the acronym.)
rating of 125,000 hours means that, on average, a device could function for 125,000 hours before failing. (Hint: Use the acronym.)
 rating of 125,000 hours means that, on average, a device could function for 125,000 hours before failing. (Hint: Use the acronym.)
rating of 125,000 hours means that, on average, a device could function for 125,000 hours before failing. (Hint: Use the acronym.)
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
36
 procedures, such as data backups, can reduce the effect of a virus that spreads throughout corporate computers.
procedures, such as data backups, can reduce the effect of a virus that spreads throughout corporate computers.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
37
Your roommate works in the Data Entry department for a large corporation and has been asked to participate in a JAD session. When asked about it, you explain to your roommate that JAD stands for  application design, and this probably means the corporation is working on a new information system.
application design, and this probably means the corporation is working on a new information system.
 application design, and this probably means the corporation is working on a new information system.
application design, and this probably means the corporation is working on a new information system.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
38
Would you prefer online voting to voting at a polling place?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
39
Should online voting be available only to specific groups, such as elderly voters and military personnel stationed abroad, who currently have trouble reaching polling places?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
40
Contrast and compare the characteristics of transaction processing systems, management information systems, decision support systems, and expert systems.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
41
Your friend just graduated and started work in a local pharmacy. She tells you about the pharmacy's computer system that warns of dangerous drug interactions by examining the patient's prescription record and sometimes asking the pharmacist to enter age and allergy information. The system that she has been describing sounds like a(n)  system.
system.
 system.
system.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
42
As a member of the IT staff at a large corporation, you often hear about problems with the current information system. One recently discovered problem is that when an employee quits (or gets fired), sometimes the network manager is not notified, and the former employee continues to have access to company data over the Internet. Using the PIECES framework, you would classify this as a(n)  problem.
problem.
 problem.
problem.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
43
You just started working in the IT department for a very small company that's developing a new information system. Your coworkers are trying to track down a discrepancy that resulted from a change in the name of a data field. Although you don't say it, you realize that such a problem would not have occurred if the project team had used  tools. (Hint: Use the acronym.)
tools. (Hint: Use the acronym.)
 tools. (Hint: Use the acronym.)
tools. (Hint: Use the acronym.)
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
44
Describe how information systems help organizations fulfill their missions, deal with threats, and take advantage of opportunities.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
45
Explain the differences between structured, semi-structured, and unstructured problems. Provide an example of each type, and describe how an information system might contribute to solving the problems.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
46
List the phases of the SDLC and the tasks that occur in each phase. Identify three development methodologies that systems analysts might use to complete the SDLC.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
47
Executive managers typically engage in  planning, whereas mid-level managers are responsible for
planning, whereas mid-level managers are responsible for  planning.
planning.
 planning, whereas mid-level managers are responsible for
planning, whereas mid-level managers are responsible for  planning.
planning.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
48
A(n)  collects data from a TPS and uses it to create scheduled and ad hoc reports. (Hint: Use the acronym.)
collects data from a TPS and uses it to create scheduled and ad hoc reports. (Hint: Use the acronym.)
 collects data from a TPS and uses it to create scheduled and ad hoc reports. (Hint: Use the acronym.)
collects data from a TPS and uses it to create scheduled and ad hoc reports. (Hint: Use the acronym.)
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
49
On your last job, you worked as an admitting clerk in a hospital. One day you were told to begin using the hospital's new information system. The next day, you were told to go back to using the old system until further notice. You suspect that these events occurred as a result of a failed attempt at a(n)  conversion.
conversion.
 conversion.
conversion.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
50
In Wetherbe's PIECES framework, the "S" represents a(n)  problem that means the system is too difficult or inconvenient to use.
problem that means the system is too difficult or inconvenient to use.
 problem that means the system is too difficult or inconvenient to use.
problem that means the system is too difficult or inconvenient to use.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
51
To fulfill the main objective of the  phase, the project team produces a System Requirements Report for a new or revised information system.
phase, the project team produces a System Requirements Report for a new or revised information system.
 phase, the project team produces a System Requirements Report for a new or revised information system.
phase, the project team produces a System Requirements Report for a new or revised information system.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck
52
For each letter of the PIECES framework, create your own example of a problem that a systems analyst might discover in an obsolete information system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 52 في هذه المجموعة.
فتح الحزمة
k this deck








