Deck 14: User Datagram Protocol Udp
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/10
العب
ملء الشاشة (f)
Deck 14: User Datagram Protocol Udp
1
In cases where reliability is not of primary importance, UDP would make a good transport protocol. Give examples of specific cases.
UPD:
• It is an unreliable, connectionless transport layer protocol.
• The sender sends the data packets to the receiver while receiver does not send acknowledgement to the sender. That's why it is unreliable protocol.
• It provides process to process delivery/communication instead of host to host communication.
• In comparison of TCP, UDP takes very less interaction among the sender and receiver.
• User datagram is the UDP packet, it contains 8 bytes of header and data which is sending to the receiver side.
There are several ports numbers are used by the UDP:
1. Echo uses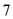 ports and it received the coming datagram from the server or receiver.
ports and it received the coming datagram from the server or receiver.
2. Discard uses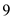 ports and discards datagram which is already received.
ports and discards datagram which is already received.
3. Users uses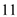 port number and it uses to now the active users.
port number and it uses to now the active users.
4. Daytime uses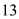 port number and it used to get date and time details.
port number and it used to get date and time details.
5. Domain uses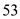 port number to know the domain name system details.
port number to know the domain name system details.
6. Bootps uses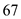 port number to know the bootstrap downloading information at server port.
port number to know the bootstrap downloading information at server port.
7. Bootpc uses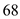 port number to know the bootstrap downloading information at client port.
port number to know the bootstrap downloading information at client port.
8. TFTP uses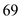 port number to transfer files.
port number to transfer files.
9. SNMP uses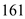 port number and it is a Simple Network Management Protocol.
port number and it is a Simple Network Management Protocol.
10. SNMP uses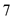 port number and it is a Simple Network Management Protocol (trap).
port number and it is a Simple Network Management Protocol (trap).
Reliability is not of primary importance if the user wants to send small message and user does not care about the reliability then UPD is the best choice to send messages.
• So, UDP would make good transport protocol.
• There is some example of applications such as daytime, bootp, echo, SNMP and TFTP, where reliability is not primary importance
• It is an unreliable, connectionless transport layer protocol.
• The sender sends the data packets to the receiver while receiver does not send acknowledgement to the sender. That's why it is unreliable protocol.
• It provides process to process delivery/communication instead of host to host communication.
• In comparison of TCP, UDP takes very less interaction among the sender and receiver.
• User datagram is the UDP packet, it contains 8 bytes of header and data which is sending to the receiver side.
There are several ports numbers are used by the UDP:
1. Echo uses
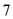 ports and it received the coming datagram from the server or receiver.
ports and it received the coming datagram from the server or receiver.2. Discard uses
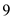 ports and discards datagram which is already received.
ports and discards datagram which is already received.3. Users uses
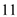 port number and it uses to now the active users.
port number and it uses to now the active users.4. Daytime uses
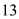 port number and it used to get date and time details.
port number and it used to get date and time details.5. Domain uses
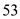 port number to know the domain name system details.
port number to know the domain name system details.6. Bootps uses
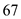 port number to know the bootstrap downloading information at server port.
port number to know the bootstrap downloading information at server port.7. Bootpc uses
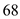 port number to know the bootstrap downloading information at client port.
port number to know the bootstrap downloading information at client port.8. TFTP uses
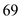 port number to transfer files.
port number to transfer files.9. SNMP uses
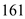 port number and it is a Simple Network Management Protocol.
port number and it is a Simple Network Management Protocol.10. SNMP uses
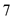 port number and it is a Simple Network Management Protocol (trap).
port number and it is a Simple Network Management Protocol (trap).Reliability is not of primary importance if the user wants to send small message and user does not care about the reliability then UPD is the best choice to send messages.
• So, UDP would make good transport protocol.
• There is some example of applications such as daytime, bootp, echo, SNMP and TFTP, where reliability is not primary importance
2
Are both UDP and IP unreliable to the same degree? Why or why not?
UDP:
• It is an unreliable, connectionless transport layer protocol.
• The sender sends the data packets to the receiver while receiver does not send acknowledgement to the sender. That's why it is unreliable protocol.
• It provides process to process delivery/communication instead of host to host communication.
• When the user wants to send small message and user does not care about the reliability then UDP is the best choice to send messages.
• In comparison of TCP, UDP takes very less interaction among the sender and receiver.
Internet protocol (IP) is a network layer protocol which is responsible to host to host communication between sender and receiver.
• Whenever IP data binds with UDP packet than transmission must be connectionless and unreliable.
• Whenever IP data binds with TCP packet than transmission must be connection oriented and reliable.
User datagram is the UDP packet, it contains 8 bytes of header and data which is sending to the receiver side.
• The total length of UDP packet is from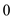 to 65535 bytes.
to 65535 bytes.
• UDP packets are encapsulated with IP datagram with length 65535 bytes. IP fields consist header length and total length.
• At the receiver side, to calculate the UDP length of the data from provided information of UDP user datagram.
Yes, both UDP and IP are unreliable to the same degree because:
• UDP is a transport layer protocol while IP is a network layer protocol.
• But when the UDP packets encapsulated with IP datagrams then the data packets will send to the receiver and receiver does not send acknowledgement to the sender.
• It is an unreliable, connectionless transport layer protocol.
• The sender sends the data packets to the receiver while receiver does not send acknowledgement to the sender. That's why it is unreliable protocol.
• It provides process to process delivery/communication instead of host to host communication.
• When the user wants to send small message and user does not care about the reliability then UDP is the best choice to send messages.
• In comparison of TCP, UDP takes very less interaction among the sender and receiver.
Internet protocol (IP) is a network layer protocol which is responsible to host to host communication between sender and receiver.
• Whenever IP data binds with UDP packet than transmission must be connectionless and unreliable.
• Whenever IP data binds with TCP packet than transmission must be connection oriented and reliable.
User datagram is the UDP packet, it contains 8 bytes of header and data which is sending to the receiver side.
• The total length of UDP packet is from
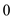 to 65535 bytes.
to 65535 bytes.• UDP packets are encapsulated with IP datagram with length 65535 bytes. IP fields consist header length and total length.
• At the receiver side, to calculate the UDP length of the data from provided information of UDP user datagram.
Yes, both UDP and IP are unreliable to the same degree because:
• UDP is a transport layer protocol while IP is a network layer protocol.
• But when the UDP packets encapsulated with IP datagrams then the data packets will send to the receiver and receiver does not send acknowledgement to the sender.
3
Show the entries for the header of a UDP user datagram that carries a message from a TFTP client to a TFTP server. Fill the checksum field with 0s. Choose an appropriate ephemeral port number and the correct well-known port number. The length of data is 40 bytes. Show the UDP packet using the format in Figure 14.2.
Figure 14.2 User datagram format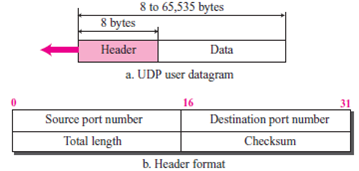
Figure 14.2 User datagram format

Consider the following data:
• The header of a UDP datagram carries a message from TFTP client to TFTP server.
• The checksum field is filled with 0's.
• Length of the data = 40 bytes
The UDP datagram format along with the header is as follows: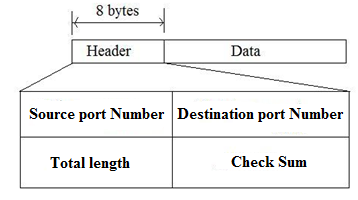 The port number for the client sending the request is called an ephemeral port number. The port number for the server sending the response is called a well-known port number.
The port number for the client sending the request is called an ephemeral port number. The port number for the server sending the response is called a well-known port number.
Here, the message is transmitted from TFTP client to TFTP server.
• So, the source is TFTP client. So, the port number is requested by the process running on source host and is chosen by the UDP software. So, the source port number is 52010.
• The destination is TFTP server. So, TFTP server consists of a well-known port number. The well-known port number for TFTP with UDP is 69. So, the destination port number is 69.
• The total length is the length of the data plus the header length. So, the total length is 40+8=48 bytes.
• The checksum field contains 0's.
So, the UDP datagram along with port numbers of source and destination is as follows: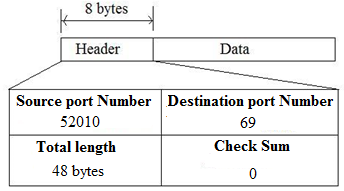
• The header of a UDP datagram carries a message from TFTP client to TFTP server.
• The checksum field is filled with 0's.
• Length of the data = 40 bytes
The UDP datagram format along with the header is as follows:
 The port number for the client sending the request is called an ephemeral port number. The port number for the server sending the response is called a well-known port number.
The port number for the client sending the request is called an ephemeral port number. The port number for the server sending the response is called a well-known port number.Here, the message is transmitted from TFTP client to TFTP server.
• So, the source is TFTP client. So, the port number is requested by the process running on source host and is chosen by the UDP software. So, the source port number is 52010.
• The destination is TFTP server. So, TFTP server consists of a well-known port number. The well-known port number for TFTP with UDP is 69. So, the destination port number is 69.
• The total length is the length of the data plus the header length. So, the total length is 40+8=48 bytes.
• The checksum field contains 0's.
So, the UDP datagram along with port numbers of source and destination is as follows:

4
An SNMP client residing on a host with IP address 122.45.12.7 sends a message to an SNMP server residing on a host with IP address 200.112.45.90. What is the pair of sockets used in this communication?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 10 في هذه المجموعة.
فتح الحزمة
k this deck
5
A TFTP server residing on a host with IP address 130.45.12.7 sends a message to a TFTP client residing on a host with IP address 14.90.90.33. What is the pair of sockets used in this communication?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 10 في هذه المجموعة.
فتح الحزمة
k this deck
6
Answer the following questions:
a. What is the minimum size of a UDP datagram?
b. What is the maximum size of a UDP datagram?
c. What is the minimum size of the process data that can be encapsulated in a UDP datagram?
d. What is the maximum size of the process data that can be encapsulated in a UDP datagram?
a. What is the minimum size of a UDP datagram?
b. What is the maximum size of a UDP datagram?
c. What is the minimum size of the process data that can be encapsulated in a UDP datagram?
d. What is the maximum size of the process data that can be encapsulated in a UDP datagram?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 10 في هذه المجموعة.
فتح الحزمة
k this deck
7
A client uses UDP to send data to a server. The data length is 16 bytes. Calculate the efficiency of this transmission at the UDP level (ratio of useful bytes to total bytes).

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 10 في هذه المجموعة.
فتح الحزمة
k this deck
8
Redo Exercise 7, calculating the efficiency of transmission at the IP level. Assume no options for the IP header.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 10 في هذه المجموعة.
فتح الحزمة
k this deck
9
Redo Exercise 7, calculating the efficiency of transmission at the data link layer. Assume no options for the IP header and use Ethernet at the data link layer.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 10 في هذه المجموعة.
فتح الحزمة
k this deck
10
The following is a dump of a UDP header in hexadecimal format. 
a. What is the source port number?
b. What is the destination port number?
c. What is the total length of the user datagram?
d. What is the length of the data?
e. Is the packet directed from a client to a server or vice versa?
f. What is the client process?

a. What is the source port number?
b. What is the destination port number?
c. What is the total length of the user datagram?
d. What is the length of the data?
e. Is the packet directed from a client to a server or vice versa?
f. What is the client process?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 10 في هذه المجموعة.
فتح الحزمة
k this deck








