Deck 9: Data Design
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/80
العب
ملء الشاشة (f)
Deck 9: Data Design
1
The three normal forms constitute a progression in which second normal form represents the best design.
False
2
To resolve potential database connectivity and access problems,companies use ODBC-compliant software that enables communication among various systems and DBMSs.
True
3
Field X is functionally dependent on field Y if the value of field X depends on the value of field Y.
True
4
Systems that interact with a DBMS are relatively independent of how the physical data is maintained.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
5
In a table or file,each column represents a record and each row represents a field.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
6
Web-based designs are dependent on a specific combination of hardware and software.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
7
A common field is an attribute that appears in only one entity.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
8
Cipher codes distinguish items by using a series of subgroups of digits.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
9
Web-based systems are popular because they offer ease of access,cost-effectiveness,and worldwide connectivity.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
10
Most magazine subscription codes are action codes.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
11
Like a primary key,a foreign key must be unique.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
12
The basic elements of logical storage are alphabetic or numeric characters,such as the letter A or the number 9.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
13
Three main types of relationships can exist between entities: a one-to-one relationship,abbreviated 1:1;a one-to-many relationship,abbreviated 1:M;and a many-to-many relationship,abbreviated M:N.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
14
A web-based data design requires users to have powerful workstations.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
15
Migrating a traditional database design to the web can require design modification,additional software,and some added expense.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
16
A subschema is a view of the database used by one or more systems or users.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
17
A primary key is composed of exactly two fields.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
18
Audit log files,which record details of all accesses and changes to a file or database,can be used to recover changes made since the last backup.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
19
A table design is in third normal form (3NF)if it is in 2NF and if all nonkey fields are dependent on one another.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
20
A repeating group is a set of one or more fields that can occur only once in a single record,with each occurrence having the same value.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
21
A 3NF design avoids redundancy and data integrity problems that still can exist in 2NF designs.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
22
A _____ controls database operations,including storing,retrieving,updating,and deleting data.
A) data manipulation language
B) data device language
C) data definition language
D) data query language
A) data manipulation language
B) data device language
C) data definition language
D) data query language

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
23
The complete definition of a database,including descriptions of all fields,tables,and relationships,is called a _____.
A) viewport
B) schema
C) framework
D) cell
A) viewport
B) schema
C) framework
D) cell

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
24
_____ means that a system can be expanded,modified,or downsized easily to meet the rapidly changing needs of a business enterprise.
A) Scalability
B) Compatibility
C) Cardinality
D) Functionality
A) Scalability
B) Compatibility
C) Cardinality
D) Functionality

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
25
Encryption is the process of creating table designs by assigning specific fields or attributes to each table in the database.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
26
A logical record is a set of field values that describes a single person,place,thing,or event.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
27
Mainframe storage refers to data that a user can view,understand,and access,regardless of how or where that information actually is organized or stored.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
28
A schema is a set of letters or numbers that represents a data item.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
29
College course numbers usually are assigned using a block sequence code.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
30
The inherent efficiency of high-volume processing on larger computers is called _____.
A) monopoly
B) economy of scope
C) cardinality
D) economy of scale
A) monopoly
B) economy of scope
C) cardinality
D) economy of scale

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
31
A _____,which is a framework for organizing,storing,and managing data,consists of files or tables that interact in various ways.
A) data structure
B) data roster
C) data object
D) data log
A) data structure
B) data roster
C) data object
D) data log

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
32
_____ is an industry-standard protocol that makes it possible for software from different vendors to interact and exchange data.
A) ActiveX data object (ADO)
B) Java virtual connector (JVC)
C) Open database connectivity (ODBC)
D) Open embedded connectivity (OEC)
A) ActiveX data object (ADO)
B) Java virtual connector (JVC)
C) Open database connectivity (ODBC)
D) Open embedded connectivity (OEC)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
33
An M:N relationship is different from 1:1 or 1:M relationships because the event or transaction that links the two entities is actually a third entity,called an associative entity,that has its own characteristics.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
34
The database and the Internet speak the same language.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
35
With a _____,users provide an example of the data requested.
A) query language
B) data table
C) query by example language
D) data frame
A) query language
B) data table
C) query by example language
D) data frame

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
36
A secondary key is a field in one table that must match a primary key value in another table in order to establish the relationship between the two tables.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
37
A(n)_____ is a collection of tools,features,and interfaces that enables users to add,update,manage,access,and analyze data.
A) data logger framework
B) database management system
C) integrated development environment
D) advanced host controller system
A) data logger framework
B) database management system
C) integrated development environment
D) advanced host controller system

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
38
A(n)_____ allows a user to specify a task without specifying how the task will be accomplished.
A) procedural language
B) query by example language
C) query language
D) imperative language
A) procedural language
B) query by example language
C) query language
D) imperative language

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
39
Common fields can be used to link entities in various types of relationships.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
40
Typically,a database management system is managed by a person called a _____,who assesses overall requirements and maintains the database for the benefit of an entire organization rather than a single department or user.
A) database administrator
B) business intelligence analyst
C) database consumer
D) big data analyst
A) database administrator
B) business intelligence analyst
C) database consumer
D) big data analyst

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
41
If a primary key combines two or more fields,then it is called a _____.
A) foreign key
B) composite key
C) dedicated key
D) candidate key
A) foreign key
B) composite key
C) dedicated key
D) candidate key

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
42
A common method of cardinality notation is called _____ because of the shapes,which include circles,bars,and symbols that indicate various possibilities.
A) big O notation
B) dark resistor's notation
C) crow's foot notation
D) hash topology notation
A) big O notation
B) dark resistor's notation
C) crow's foot notation
D) hash topology notation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
43
Designing tables is easier if a _____ is used to show a table's structure,fields,and primary key.
A) distinct notation format
B) multifaceted notation format
C) viewport notation format
D) standard notation format
A) distinct notation format
B) multifaceted notation format
C) viewport notation format
D) standard notation format

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
44
A table is in _____ if it is in first normal form and if all fields that are not part of the primary key are functionally dependent on the entire primary key.
A) second normal form
B) zeroth normal form
C) third normal form
D) fourth normal form
A) second normal form
B) zeroth normal form
C) third normal form
D) fourth normal form

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
45
A _____,which is not unique,is a field or combination of fields that can be used to access or retrieve records.
A) no-frills key
B) super key
C) secondary key
D) foreign key
A) no-frills key
B) super key
C) secondary key
D) foreign key

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
46
A table is in _____ if it does not contain a repeating group.
A) second normal form
B) first normal form
C) third normal form
D) fourth normal form
A) second normal form
B) first normal form
C) third normal form
D) fourth normal form

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
47
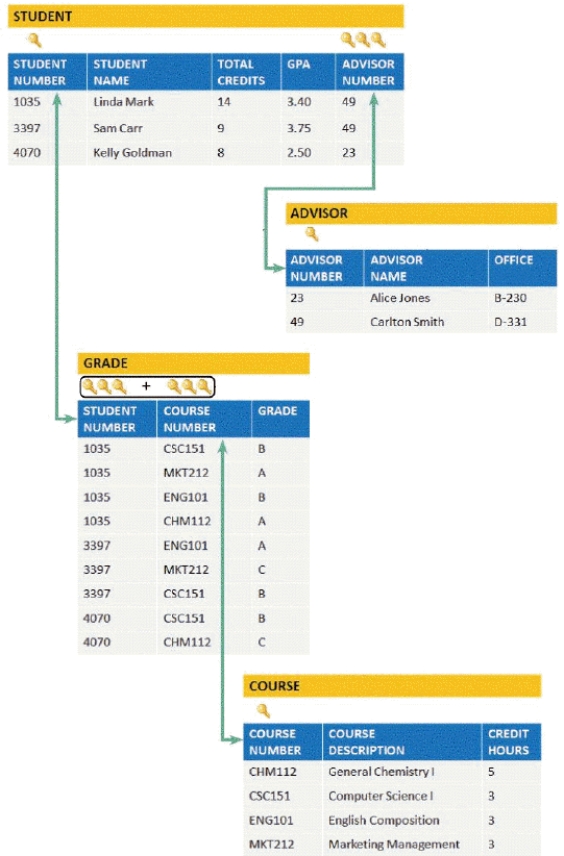
In the accompanying figure,a _____ is a field or combination of fields that uniquely and minimally identifies a particular member of an entity.
A) primary key
B) secondary key
C) candidate key
D) foreign key

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
48

In the accompanying figure,any field that serves as a primary key is called a _____.
A) candidate key
B) secondary key
C) combination key
D) foreign key

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
49
During the systems design phase,_____ are used to organize,access,and maintain data structures.
A) glossary fields
B) common fields
C) content fields
D) key fields
A) glossary fields
B) common fields
C) content fields
D) key fields

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
50
_____ enables Java applications to exchange data with any database that uses SQL statements and is compliant with its standard.
A) Java runtime environment (JRE)
B) Java eclipse framework connectivity (JEFC)
C) Java virtual machine (JVM)
D) Java database connectivity (JDBC)
A) Java runtime environment (JRE)
B) Java eclipse framework connectivity (JEFC)
C) Java virtual machine (JVM)
D) Java database connectivity (JDBC)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
51
_____ describes the numeric relationship between two entities and shows how instances of one entity relate to instances of another entity.
A) Scalability
B) Compatibility
C) Cardinality
D) Functionality
A) Scalability
B) Compatibility
C) Cardinality
D) Functionality

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
52
To bridge the gap between a database and the Internet,it is necessary to use _____,which is software that integrates different applications and allows them to exchange data.
A) middleware
B) a stack
C) a server
D) firmware
A) middleware
B) a stack
C) a server
D) firmware

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
53
A(n)_____ is a graphical model of an information system that depicts the logical relationships and interaction among system entities.
A) entity-relationship diagram (ERD)
B) illustration flow chart
C) query relationship diagram (QRD)
D) data chart
A) entity-relationship diagram (ERD)
B) illustration flow chart
C) query relationship diagram (QRD)
D) data chart

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
54
A table design that contains a repeating group is called _____.
A) normalized
B) unnormalized
C) unsynchronized
D) synchronized
A) normalized
B) unnormalized
C) unsynchronized
D) synchronized

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
55
One type of validity check,called _____,is a set of rules that avoids data inconsistency and quality problems.
A) candidate integrity
B) foreign integrity
C) referential integrity
D) combinatorial integrity
A) candidate integrity
B) foreign integrity
C) referential integrity
D) combinatorial integrity

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
56

In the accompanying figure,a _____ is a field in one table that must match a primary key value in another table in order to establish the relationship between the two tables.
A) secondary key
B) candidate key
C) combination key
D) foreign key

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
57
In an entity-relationship diagram,entities are commonly represented as _____.
A) triangles
B) circles
C) rectangles
D) hexagons
A) triangles
B) circles
C) rectangles
D) hexagons

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
58
_____ is the process of creating table designs by assigning specific fields or attributes to each table in a database.
A) Encapsulation
B) Normalization
C) Abstraction
D) Encryption
A) Encapsulation
B) Normalization
C) Abstraction
D) Encryption

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
59
A _____ specifies the fields and identifies the primary key in a particular file.
A) frame design
B) table design
C) viewport
D) window
A) frame design
B) table design
C) viewport
D) window

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
60
Any field that is not a primary key or a candidate key is called a _____.
A) no-frills field
B) nonkey field
C) secondary field
D) foreign field
A) no-frills field
B) nonkey field
C) secondary field
D) foreign field

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
61
A _____ is a set of letters or numbers that represents a data item.
A) business glossary
B) data dictionary
C) mnemonic
D) code
A) business glossary
B) data dictionary
C) mnemonic
D) code

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
62
A long integer format uses _____ bits to represent the number 1,234,567,890 in binary form.
A) 12
B) 24
C) 30
D) 32
A) 12
B) 24
C) 30
D) 32

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
63
The data mining technique that relies on association rule learning is often called _____.
A) simulated analysis
B) virtual storage analysis
C) strategy-oriented analysis
D) market basket analysis
A) simulated analysis
B) virtual storage analysis
C) strategy-oriented analysis
D) market basket analysis

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
64
_____ are numbers or letters assigned in a specific order.
A) Sequence codes
B) Category codes
C) Significant digit codes
D) Derivation codes
A) Sequence codes
B) Category codes
C) Significant digit codes
D) Derivation codes

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
65
_____ use a keyword to encode a number.
A) Cipher codes
B) Identifier codes
C) Action codes
D) Associative codes
A) Cipher codes
B) Identifier codes
C) Action codes
D) Associative codes

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
66
Eamon plans to operate three warehouses,in different cities,to support his business.To find the exact location of a product,he wants to establish a code that identifies a product's warehouse location,floor number,section number,aisle number,and bin number.By doing this,he can ship the ordered products faster.Which of the following codes would you suggest that Eamon use?
A) Significant digit code
B) Block sequence code
C) Sequence code
D) Action code
A) Significant digit code
B) Block sequence code
C) Sequence code
D) Action code

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
67
Eamon wants to provide a discount to premium buyers who order in large quantities.He wants to create a code for each price and share it with them.Also,he wants to ensure that only the premium buyers can decipher the code shared.In this scenario,which of the following codes would you suggest that Eamon use?
A) Cipher code
B) Mnemonic code
C) Action code
D) Derivation code
A) Cipher code
B) Mnemonic code
C) Action code
D) Derivation code

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
68
_____,a coding method that uses one byte per character,is used on mainframe computers and high-capacity servers.
A) ASCII (American Standard Code for Information Interchange)
B) EBCDIC (Extended Binary Coded Decimal Interchange Code)
C) Unicode
D) ISO (International Organization for Standardization)
A) ASCII (American Standard Code for Information Interchange)
B) EBCDIC (Extended Binary Coded Decimal Interchange Code)
C) Unicode
D) ISO (International Organization for Standardization)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
69
_____ is strictly hardware related because it involves the process of reading and writing binary data to physical media,such as a hard drive,CD/DVD,or network-based storage device.
A) Logical storage
B) Virtual storage
C) Simulated storage
D) Physical storage
A) Logical storage
B) Virtual storage
C) Simulated storage
D) Physical storage

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
70
_____ is the process of converting readable data into unreadable characters to prevent unauthorized access to the data.
A) Encapsulation
B) Normalization
C) Standardization
D) Encryption
A) Encapsulation
B) Normalization
C) Standardization
D) Encryption

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
71
_____ is an integrated collection of data that can include seemingly unrelated information,no matter where it is stored in the company.
A) A data warehouse
B) A data frame
C) Pseudo-data
D) Metadata
A) A data warehouse
B) A data frame
C) Pseudo-data
D) Metadata

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
72
_____ is designed to serve the needs of a specific department,such as sales,marketing,or finance.
A) A data mart
B) A data frame
C) Pseudo-data
D) Metadata
A) A data mart
B) A data frame
C) Pseudo-data
D) Metadata

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
73
Explain the importance and process of system file backup.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
74
List and discuss at least five specific database management system (DBMS)advantages.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
75
Some abbreviation codes are called _____ codes because they use a specific combination of letters that are easy to remember.
A) harmonic
B) sequence
C) mnemonic
D) rhapsodic
A) harmonic
B) sequence
C) mnemonic
D) rhapsodic

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
76
_____ combine data from different item attributes,or characteristics,to build a code.
A) Sequence codes
B) Category codes
C) Significant digit codes
D) Derivation codes
A) Sequence codes
B) Category codes
C) Significant digit codes
D) Derivation codes

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
77
Explain why large firms use data warehouses.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
78
Binary digits have only _____ possible value(s).
A) one
B) two
C) three
D) four
A) one
B) two
C) three
D) four

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
79
Briefly describe the seven coding methods used by companies with examples.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
80
Describe how middleware is used.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck








